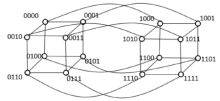
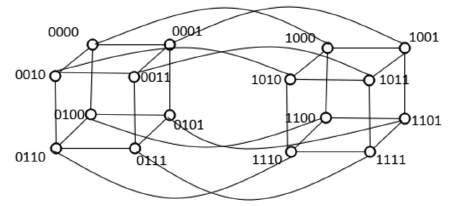
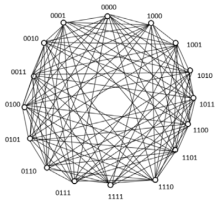
| [1] |
蔡方博,何泾沙,张玉强,等. 无线传感器节点实时同步安全方法研究[J]. 信息网络安全,2016(8):12-17.
|
| [2] |
ESCHENAUER L, GLIGOR V.A Key Management Scheme for Distributed Sensor Networks[D]. 福州:福建师范大学, 2002.
|
| [3] |
CHAN Haowen, PERRIG A, SONG D.Random Key Predistribution Schemes for Sensor Networks[C]//IEEE. 2003 Symposium on Security and Privacy, May 11-14. 2003. Berkeley, CA, USA.NJ:IEEE, 2003: 197-213.
|
| [4] |
DENG Hongmei, MUKHERJEE A, AGRAWAL D P.Threshold and Identity-based Key Management and Authentication for Wireless ad Hoc Networks[C]//IEEE. International Conference on Information Technology: Coding and Computing, April 5-7, 2004. Las Vegas, NV, USA. NJ:IEEE,2004:107-111 .
|
| [5] |
DELGOSHA F, FEKRI F.Threshold Key-establishment in Distributed Sensor Networks Using a Multivariate Scheme[C]//IEEE. 25th IEEE International Conference on Computer Communications, April 23-29,2006. Barcelona, Spain.NJ:IEEE, 2006:1-12.
|
| [6] |
LIU Donggang, NING Peng, LI Rongfang.Establishing Pairwise Keys in Distributed Sensor Networks[J]. ACM Transactions on Information and System Security,2005,8(1):41-77.
|
| [7] |
YAGAN O. Random Graph Modeling of Key Distribution Schemesin Wireless Sensor Networks[EB/OL]. ,2017-7-15.
|
| [8] |
ZHAO Jun, Ya˘Gan O, GLIGOR V. k-Connectivity in Random Key Graphs with Unreliable Links[J]. IEEE Transactions on Information Theory, 2015,61(7):3810-3836.
|
| [9] |
矢敏,叶伟伟,欧庆于.不需双线性对的基于身份的认证密钥协商协议[J].信息网络安全,2016(10):21-27.
|
| [10] |
ZHAO J, GOVINDAN R.Understanding Packet Delivery Performance in Dense Wireless Sensor Networks[C]//ACM. The 1st International Conference on Embedded Networked Sensor Systems (SenSys), November 5 - 7, 2003. Los Angeles, California, USA. New York:ACM,2003:1-13.
|
| [11] |
王沂,韩广国,李慧智.无线网络中可证安全的移动用户密钥交换协议[J].信息网络安全,2015(3):54-58.
|
| [12] |
许力,章红艳,沈金波.分簇传感器网络中基于横截设计的对密钥建立方案[J].电子与信息学报,2009,31(7) :1600-1605.
|
| [13] |
ZHANG Yuexin, XU Li, HUANG Xinyi.Polynomial-based Key Predistribution Scheme in Wireless Mesh Networks[J]. Journal of Computational Information System,2012. 8(6):2539-2549.
|
| [14] |
苏彬庭,方禾,许力.基于Q-Learing的无线传感器网络生命周期平衡路由[J].信息网络安全,2015(4):74-77.
|
 ), Limei LIN3
), Limei LIN3