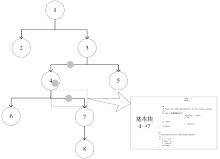
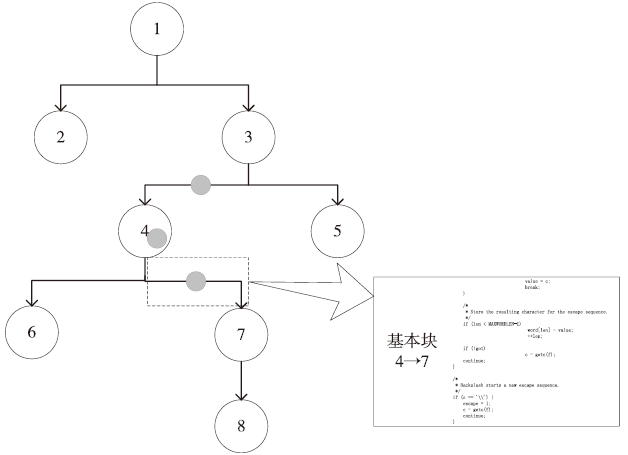
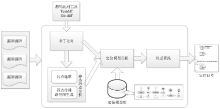
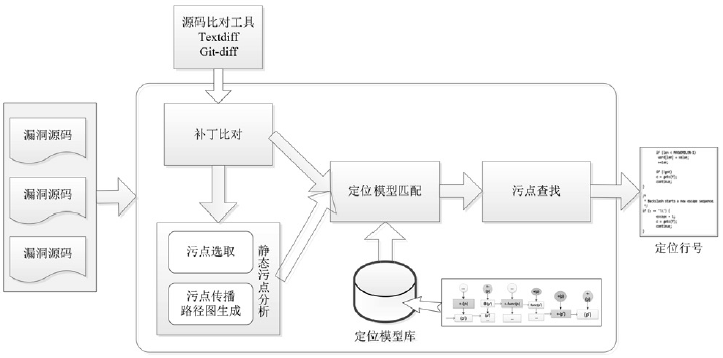
| [1] |
微软安全技术中心. Microsoft 安全公告 MS17-010 - 严重[EB/OL].https://technet.microsoft.com/zh-cn/library/security/MS17-010, 2016-5-10.
|
| [2] |
GAO Fengjuan, WANG Linzhang, LI Xuandong.BovInspector: Automatic Inspection and Repair of Buffer Overflow Vulnerabilities[C]//ACM.Proceedings of the 31st IEEE/ACM International Conference on Automated Software Engineering, September 3-7, 2016. Singapore. New York: ACM, 2016: 786-791.
|
| [3] |
PADMANABHUNI B M, TAN H B K. Light-weight Rule-based Test Case Generation for Detecting Buffer Overflow Vulnerabilities[C]//IEEE.Automation of Software Test (AST), 2015 IEEE/ACM 10th International Workshop on, May 23-24, 2015. Florence, Italy. NJ: IEEE, 2015: 48-52.
|
| [4] |
DIETZ W, LI Peng, REGEHR J, et al.Understanding Integer Overflow in C/C++[C]//IEEE. Software Engineering (ICSE), 2012 34th International Conference on, June 2-9, 2012. Zurich, Switzerland.NJ:IEEE,2015: 2.
|
| [5] |
LAGUNA I, SCHULZ M.Pinpointing Scale-dependent Integer Overflow Bugs in Large-scale Parallel Applications[C]//IEEE.Proceedings of the International Conference for High Performance Computing, Networking, Storage and Analysis, November 13-18, 2016. Salt Lake City, Utah. NJ: IEEE, 2016: 216-227.
|
| [6] |
董鹏程, 舒辉, 康绯, 等. 基于动态二进制平台的缓冲区溢出过程分析[J]. 计算机工程, 2012, 38(6): 66-68.
|
| [7] |
SONG Yang, ZHANG Yuqing, SUN Yingfei.Automatic Vulnerability Locating in Binary Patches[C]// IEEE.International Conference on Computational Intelligence and Security, December 11-14, 2009. Beijing, China. NJ: IEEE, 2009:474-477.
|
| [8] |
黄克振, 连一峰, 陈恺, 等. 基于标志位差异分析的整数溢出漏洞溢出点定位方法[J]. 计算机科学, 2014, 41(12): 19-23.
|
| [9] |
肖海, 陈平, 茅兵, 等. 基于运行时类型分析的整形漏洞二进制检测和定位系统[J]. 计算机科学, 2011, 38(1): 140-144.
|
| [10] |
YAMAGUCHI F, MAIER A, GASCON H, et al.Automatic Inference of Search Patterns for Taint-style Vulnerabilities[C]//IEEE.Security and Privacy (SP), 2015 IEEE Symposium on. May 17-21, 2015.San Jose, CA,USA. NJ: IEEE, 2015: 797-812.
|
| [11] |
SHAHRIAR H, HADDAD H M, VAIDYA I.Buffer Overflow Patching for C and C++ Programs: Rule-based Approach[J]. ACM SIGAPP Applied Computing Review, 2013, 13(2): 8-19.
|
| [12] |
The MITRE Corporation. CWE[EB/OL]. , 2017-5-19.
|
| [13] |
王蕾, 李丰, 李炼, 等.污点分析技术的原理和实践应用[J].软件学报, 2017, 28(4):860-882.
|
| [14] |
WANG Xuefei, MA Hengtai, JING Lisha.A Dynamic Marking Method for Implicit Information Flow in Dynamic Taint Analysis[C]//ACM.Proceedings of the 8th International Conference on Security of Information and Networks, September 8-10, 2015. Sochi, Russia. New York: ACM, 2015: 275-282.
|
| [15] |
宋铮, 王永剑, 金波, 等.二进制程序动态污点分析技术研究综述[J].信息网络安全, 2016(3):77-83.
|
 ), Limin MAO, Mingjie WU, Min GUO
), Limin MAO, Mingjie WU, Min GUO