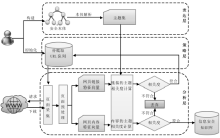
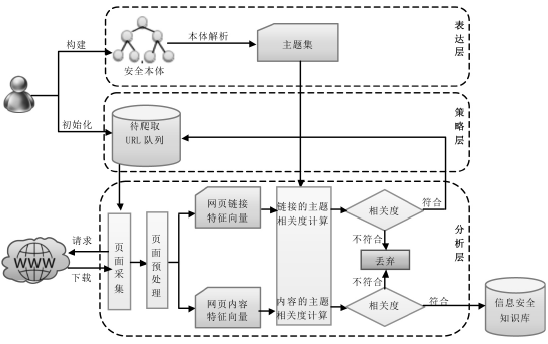
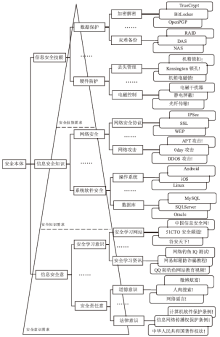
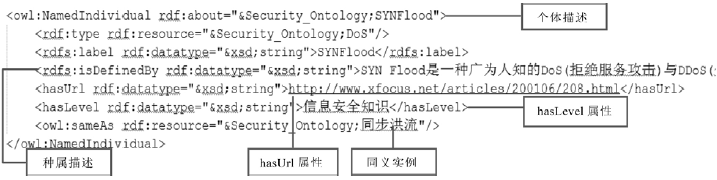
| [1] |
AL AWAWDEH S, TUBAISHAT A.An Information Security Awareness Program to Address Common Security Concerns in IT Unit[C] //IEEE. 2014 Eleventh International Conference on Information Technology: New Generations, April 7-9, 2014, Las Vegas, USA. New York: IEEE, 2014:273-278.
|
| [2] |
ABAWAJY J.User Preference of Cyber Security Awareness Delivery Methods[J]. Behaviour & Information Technology, 2014, 33(3):237-248.
|
| [3] |
KEARNEY W D, KRUGER H A.Can Perceptual Differences Account for Enigmatic Information Security Behaviour in an Organization?[J]. Computers & Security, 2016(61): 46-58.
|
| [4] |
朱燕丽. 基于RSS的用户信息安全意识教育系统设计与实现[D]. 南京:南京师范大学, 2014.
|
| [5] |
朱汉. 适应用户需求及其演进的信息安全素养教育系统设计与实现[D]. 南京:南京师范大学, 2016.
|
| [6] |
丁雪, 张玉峰. 基于本体的智能数字图书馆个性化推荐用户本体研究[J]. 现代情报, 2009, 29(12): 61-65,7.
|
| [7] |
徐德斌. 基于领域本体的知识整合浅析[J]. 现代情报, 2011, 31(12): 27-29,3.
|
| [8] |
刘启华. 泛在商务环境下的信息聚合与推荐[M].上海;复旦大学出版社,2014.
|
| [9] |
钟杰,王海舟,王文贤. 基于话题的微博信息传播拓扑结构研究[J].信息网络安全,2016(3):64-70.
|
| [10] |
RASKIN V, HEMPELMANN C F, Triezenberg K.E., et al. Ontology in Information Security: a Useful Theoretical Foundation and Methodological Tool[C] // ACM. 2001 Workshop on New Security Paradigms, September 10-13, 2001, Cloudcroft, USA. New York: ACM, 2001:53-59.
|
| [11] |
DONNER M.Toward a Security Ontology[J]. IEEE Security & Privacy, 2003, 1(3): 6-7.
|
| [12] |
PEREIRA T, SANTOS H.An Ontology Based Approach to Information Security[C] // Springer. Third International Conference on Metadata and Semantic Research, October 1-2, 2009, Milan, Italy. Heidelberg: Springer-Verlag Berlin, 2009: 183-192.
|
| [13] |
LIU F H.Constructing Enterprise Information Network Security Risk Management Mechanism by Using Ontology[C] // IEEE. 21st International Conference on Advanced Information Networking and Applications, May 21-23, 2007, Niagara Falls, Canada. New York: IEEE, 2007:929-934.
|
| [14] |
LICCARDO L, RAK M, DI MODICA G, et al.Ontology-based Negotiation of Security Requirements in Cloud[C] //IEEE. Fourth International Conference on Computational Aspects of Social Networks, November 21-23, 2012, Sao Carlos, USA. New York: IEEE, 2012:192-197.
|
| [15] |
TAKAHASHI T, FUJIWARA H, KADOBAYASHI Y.Building Ontology of Cybersecurity Operational Information[C] // ACM. Sixth Annual Workshop on Cyber Security and Information Intelligence, April 21-23, 2010, Oak Ridge, USA. New York: ACM, 2010:87-91.
|
| [16] |
YAO Y, WANG X, MENG X, et al.ISEK: An Information Security Knowledge Graph for CISP Knowledge System[C] // IEEE. 5th International Conference on IT Convergence and Security, August 24-27, Kuala Lumpur, Malaysia. New York: IEEE, 2015:1-4.
|
| [17] |
罗力. 国民信息安全素养评价指标体系构建研究[J]. 图书情报工作, 2012, 56(6):25-28.
|
| [18] |
陈腾, 袁小群, 曾元祥. 领域本体的作用及构建实例[J]. 出版科学, 2013, 21(5):79-84.
|
| [19] |
陈华山,皮兰,刘峰,等. 网络空间安全科学基础的研究前沿及发展趋势[J].信息网络安全,2015(3):1-5.
|
| [20] |
郑健珍, 林坤辉, 周昌乐,等. 基于本体语义的定题爬虫[J]. 山东大学学报:理学版, 2006, 41(3):106-110.
|
 ), Bo CHEN2
), Bo CHEN2