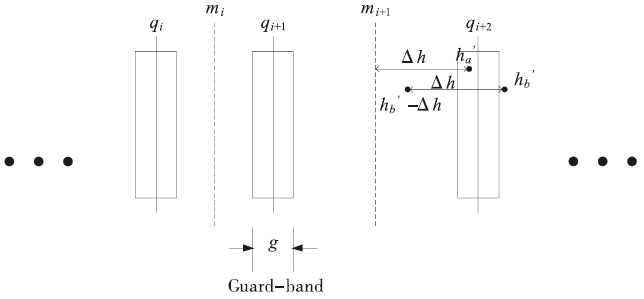
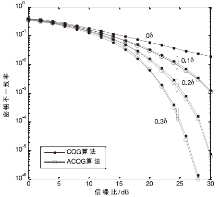
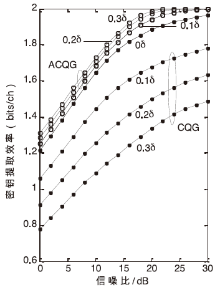
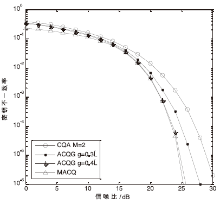
| [1] |
MAURER U.M. Secret Key Agreement by Public Discussion from Common Information[J]. IEEE Transactions on Information Theory, 1993, 39(3): 733-742.
|
| [2] |
AHLSWEDE R, CSISZAR I.Common Randomness in Information Theory and Cryptography. I. Secret Sharing[J]. IEEE Transactions on Information Theory, 1993, 39(4): 1121-1132.
|
| [3] |
HERSHEY J E, HASSAN A, YARLAGADDA R.Unconventional Cryptographic Keying Variable Management[J]. IEEE Transactions on Communications, 1995, 43(1): 3-6.
|
| [4] |
MATHUR S, WADE T, NARAYAN M, et al.Radio-telepathy: Extracting a Secret Key from an Unauthenticated Wireless Channel[C]//ACM. 14th ACM International Conference on Mobile Computing and Networking, September 14-19, 2008, San Francisco, California, USA. New York: ACM, 2008: 128-139.
|
| [5] |
ZHU X, XU F, NOVAK E, et al.Using Wireless Link Dynamics to Extract a Secret Key in Vehicular Scenarios[J]. IEEE Transactions on Mobile Computing, 2016(99):1.
|
| [6] |
SUMAN J, SRIRAM N P, MIKE C, et al.On the Effectiveness of Secret Key Extraction from Wireless Signal Strength in Real Environments[C]//ACM. 15th Annual ACM International Conference on Mobile Computing and Networking, September 20-25, 2009, Beijing, China. New York: ACM, 2009: 321-332.
|
| [7] |
SAYEED A, PERRIG A.Secure Wireless Communications: Secret Keys through Multipath[C]// IEEE. IEEE International Conference on Acoustics, Speech and Signal Processing, March 30-April 4, 2008, Las Vegas, NV. New York: IEEE, 2008: 3013-3016.
|
| [8] |
WALLACE J W, SHARMA R K.Automatic Secret Keys from Reciprocal MIMO Wireless Channels: Measurement and Analysis[J]. IEEE Transactions on Information Forensics and Security, 2010, 5(3): 381-392.
|
| [9] |
JESSICA C, NEAL P, SNEHA K.Robust Uncorrelated Bit Extraction Methodologies for Wireless Sensors[C]//ACM/IEEE. 9th ACM/IEEE International Conference on Information Processing in Sensor Networks, April 12-16, 2010, Stockholm, Sweden. New York: ACM, 2010: 70-81.
|
| [10] |
GOPINATH S, GUILLAUME R, DUPLYS P, et al.Reciprocity Enhancement and Decorrelation Schemes for PHY-based Key Generation[C]//IEEE. 2014 IEEE Globe Communications Conference, December 8-12, 2014, Austin, TX. New York: IEEE, 2014: 1367-1372.
|
| [11] |
AMBEKAR M, HASSAN H, SCHOTTEN D.Improving Channel Reciprocity for Effective Key Management Systems[C]//URSI. 2012 International Symposium on Signals, Systems, and Electronics, October 3-5, 2012, Potsdam, Germany. New York: IEEE, 2012: 1-4.
|
| [12] |
LIU H, WANG Y, WANG J, et al.Fast and Practical Secret Key Extraction by Exploiting Channel Response[C]//IEEE. 32nd IEEE INFOCOM Conference, April 14-19, 2013, Turin, Italy. New York: IEEE, 2013: 3048-3056.
|
| [13] |
蔡方博,何泾沙,张玉强,等. 无线传感器节点实时同步安全方法研究[J].信息网络安全,2016(8):12-17.
|
| [14] |
CHENG L, LI W, MA D, et al.Moving Window Scheme for Extracting Secret Keys in Stationary Environments[J]. IET Communications, 2016, 10(16): 2206-2214.
|
| [15] |
张涛,刘樵,李晖. 多天线系统中物理层安全问题研究综述[J].信息网络安全,2016(5):9-14.
|
| [16] |
HONG Y W P, HUANG L M, LI H T. Vector Quantization and Clustered Key Mapping for Channel-Based Secret Key Generation[J]. IEEE Transactions on Information Forensics and Security, 2017, 12(5): 1170-1181.
|
| [17] |
田森平,基于接收信号强度的传感网组密钥生成协议的研究[D].西安:西安电子科技大学,2014.
|
| [18] |
ZHENG Y R, XIAO Chengshan.Simulation Models with Correct Statistical Properties for Rayleigh Fading Channels[J]. IEEE Transactions on Communications, 2003, 51(6): 920-928.
|