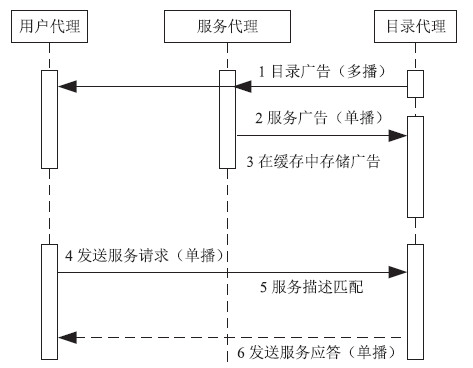
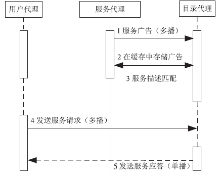
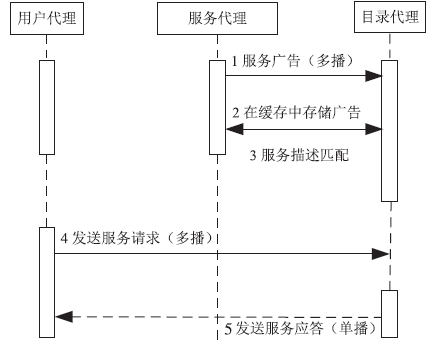
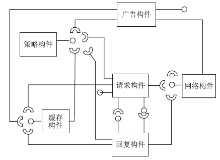
| [1] |
JUBIN J, TORNOW J D.The DARPA packet radio network protocols[J]. IEEE - PIEEE, 1987, 75(1): 21-32.
|
| [2] |
Beyer D A.Accomplishments of the DARPA Survivable Adaptive Networks SURAN Program[C]//IEEE Military Communications Conference (MILCOM), 1990: 855-862.
|
| [3] |
LEINER B M, RUTH R J, SASTRY A R.Sastry. Goals and Challenges of the DARPA GloMo Program[J]. Personal Communications, IEEE, 1996, 3(6):34-43.
|
| [4] |
IEEE. IEEE 802.11TM WIRELESS LOCAL AREA NETWORKS[EB/OL]. , 2015-05-11.
|
| [5] |
IETF. Mobile Ad-hoc Networks[EB/OL]. , 2015-05-13.
|
| [6] |
王勇,高诗梦,聂肖,等. 基于速度动态差异的位置服务匿名算法[J]. 信息网络安全,2015,(4):28-35.
|
| [7] |
GRACE P, BLAIR G S, SAMUEL S.ReMMoC: A Reflective Middleware to support Mobile Client Interoperability[C]//OTM Confederated International Conferences: CoopIS, DOA, and ODBASE Italy, 2003:1170-1187.
|
| [8] |
BROMBERG Y D, ISSARNY, V.INDISS: Interoperable Discovery System for Networked Services[C]//ACM/IFIP/USENIX 6th International Middleware Conference, Grenoble, France, 2005: 164-183.
|
| [9] |
HELAL S, DESAI N, VERMA V, et al.Konark - A Service Discovery and Delivery protocol for Ad-hoc Networks[C]//Third IEEE conference on Wireless Communication networks (WCNC), New Orleans, 2003: 2107-2113.
|
| [10] |
CAMPO C, GARCÍA C. PDP: A lightweight discovery protocol for local-scope interactions in wireless ad hoc networks[J]. Computer Networks, 2006, 50(17): 3264-3283.
|
| [11] |
RATSIMOR O, CHAKRABORTY D, JOSHI A, et al.Allia: Alliance-based Service Discovery for Ad-hoc Environments[C]//The 2nd ACM Mobile Commerce Workshop, 2002: 1-9.
|
| [12] |
HALKES G P, BAGGIO A, LANGENDOEN K G.A Simulation Study of Integrated Service Discovery[C]//First European Conference, EuroSSC 2006, 2006: 39-53.
|
| [13] |
宋弢,何建忠. 基于FSR协议的Ad-hoc网络服务发现策略[J]. 仪器仪表学报,2006,27(6):2048-2049.
|
| [14] |
吕文文. MANET服务发现协议研究[D]. 北京:北京邮电大学,2011.
|
| [15] |
熊梅,周安民. Kad网络协议研究与实验[J]. 信息网络安全,2015,(2):46-50.
|
| [16] |
戴勇谦,张明武,祝胜林,等. 一种节点自分布最优Ad Hoc多播树及其应用[J]. 电子学报,2015,43(7):1449-1456.
|
| [17] |
胡桃英,程运安,官骏鸣. Ad hoc网络中基于带宽的准入控制研究[J]. 计算机工程与应用,2014,(21):85-90.
|
| [18] |
晏威,肖明波,徐向南. Ad Hoc网络中联合速率与功率控制的跨层设计[J]. 信息网络安全,2015,(4):36-40.
|
| [19] |
郭晶晶,马建峰,李琦,等. 基于博弈论的移动自组织网络的信任管理方法[J]. 通信学报,2014,35(11):50-58.
|
| [20] |
刘超. 认知Ad-hoc无线网络的跨层结构设计[J]. 电子测量技术,2014,37(11):122-126.
|
| [21] |
王涛,胡爱群. 基于边界检测的IPSec VPN协议的一致性测试方法[J]. 信息网络安全,2014,(2):7-11.
|
 ), TANG Yi-hong2, QI Wei1, YANG Yi-xian3
), TANG Yi-hong2, QI Wei1, YANG Yi-xian3