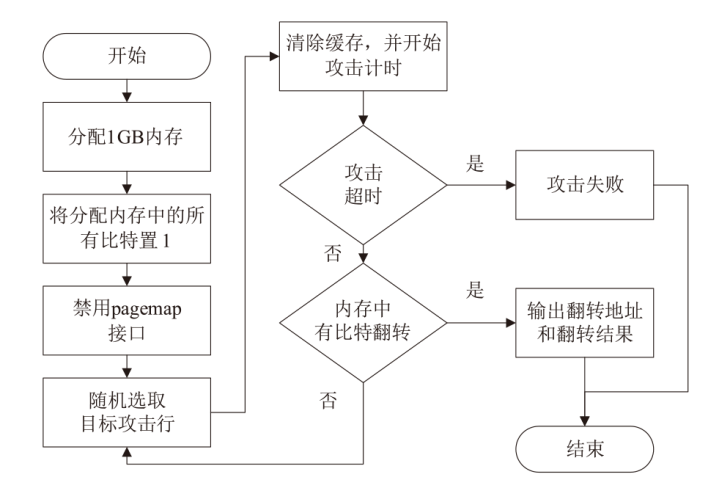
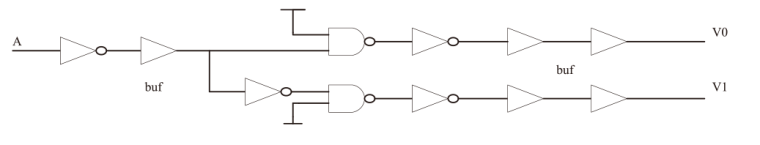
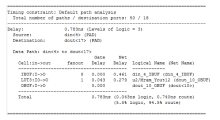
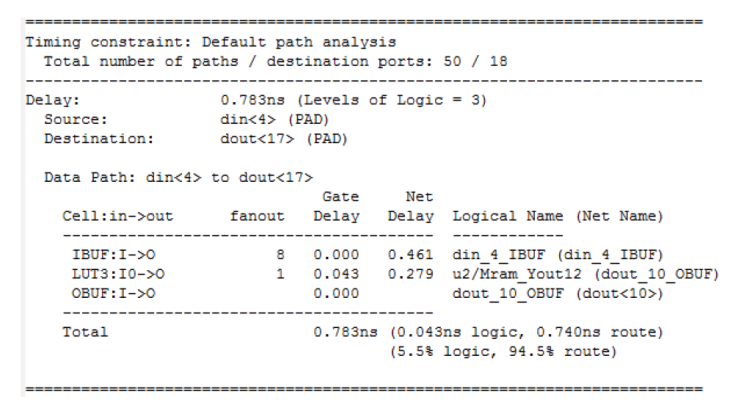
| [1] |
KIM Y, DALY R, KIM J, et al. Flipping Bits in Memory Without Accessing Them: An Experimental Study of DRAM Disturbance Errors[C]// ACM. The 41st International Symposium on Computer Architecture (ISCA). New York: ACM, 2014: 361-372.
|
| [2] |
LEE M, KWAK J. Detection Technique of Software-Induced Rowhammer Attacks[J]. Computers, Materials & Continua, 2021, 67(1): 349-367.
|
| [3] |
GAO Bo, CHEN Lin, YAN Yingjian. Research on Side Channel Attack Based on CNN-MGU[J]. Netinfo Security, 2022, 22(8): 55-63.
|
|
高博, 陈琳, 严迎建. 基于CNN-MGU的侧信道攻击研究[J]. 信息网络安全, 2022, 22(8):55-63.
|
| [4] |
MA Yuepeng, LIU Jiqiang, WANG Jian. A Pretreatment of DPI System Based on the Cache Hit[J]. Netinfo Security, 2016, 16(10): 69-75.
|
|
马跃鹏, 刘吉强, 王健. 基于缓存命中的DPI系统预处理方法[J]. 信息网络安全, 2016, 16(10):69-75.
|
| [5] |
SEABORN M, DULLIEN T. Exploiting the DRAM Rowhammer Bug to Gain Kernel Privileges[EB/OL]. (2015-08-11)[2024-09-03]. https://www.cs.umd.e-du/class/fall2019/cmsc818O/papers/rowhammer-kernel.pdf.
|
| [6] |
GRUSS D, MAURICE C, MANGARD S. Rowhammer. js: A Remote Software-Induced Fault Attack in JavaScript[C]// Springer. Detection of Intrusions and Malware, and Vulnerability Assessment. Heidelberg: Springer, 2016: 300-321.
|
| [7] |
FRIGO P, GIUFFRIDA C, BOS H, et al. Grand Pwning Unit: Accelerating Microarchitectural Attacks with the GPU[C]// IEEE. 2018 IEEE Symposium on Security and Privacy. New York: IEEE, 2018: 195-210.
|
| [8] |
JATTKE P, WIPFLI M, SOLT F, et al. Zenhammer: Rowhammer Attacks on AMD Zen-Based Platforms[C]// USENIX. 33rd USENIX Security Symposium (USENIX Security 2024). Philadelphia: USENIX, 2024: 1615-1633.
|
| [9] |
DING Liping, LIU Xuehua, CHEN Guangxuan, et al. Overview of Digital Forensics Technologies of RAM in Android Devices[J]. Netinfo Security, 2019, 19(2): 10-17.
|
|
丁丽萍, 刘雪花, 陈光宣, 等. Android智能手机动态内存取证技术综述[J]. 信息网络安全, 2019, 19(2):10-17.
|
| [10] |
XIAO Chaoen, HUANG Song, WANG Jianxin, et al. Review on Research Progress of Rowhammer[J]. Journal of Beijing Electronic Science and Technology Institute, 2020, 28(1): 30-41.
|
|
肖超恩, 黄松, 王建新, 等. Rowhammer漏洞研究进展[J]. 北京电子科技学院学报, 2020, 28(1):30-41.
|
| [11] |
LOU Xiaoxuan. The Implementation Security of Block Ciphers against Side Channel Attacks Based on Memory System[D]. Hangzhou: Zhejiang University, 2020.
|
|
楼潇轩. 基于存储系统旁路攻击的分组密码实现安全性研究[D]. 杭州: 浙江大学, 2020.
|
| [12] |
YANG Yingying, HOU Rui. Overview of Memory RowHammer Attacks and Defense Technology[J]. Journal of Guangzhou University(Natural Science Edition), 2021, 20(3): 30-43.
|
|
杨莹莹, 侯锐. 内存RowHammer攻击与防御综述[J]. 广州大学学报(自然科学版), 2021, 20(3):30-43.
|
| [13] |
HONG Sheng, LI Lei, YUAN Yidong, et al. Research on Cooperative Security Technology of Side Channel in Processor Microarchitecture Storage System[J]. Netinfo Security, 2022, 22(6): 26-37.
|
|
洪晟, 李雷, 原义栋, 等. 处理器微架构存储体系侧信道协同安全技术研究[J]. 信息网络安全, 2022, 22(6):26-37.
|
| [14] |
WANG Jianxin, XU Hongke, XIAO Chaoen, et al. Research and Implementation of Rowhammer Attack Method Based on Domestic NeoKylin Operating System[C]// IEEE. 2022 4th International Conference on Frontiers Technology of Information and Computer (ICFTIC). New York: IEEE, 2022: 663-668.
|
| [15] |
COJOCAR L, RAZAVI K, GIUFFRIDA C. Exploiting Correcting Codes: On the Effectiveness of ECC Memory Against Rowhammer Attacks[C]// IEEE. 2019 IEEE Symposium on Security and Privacy. New York: IEEE, 2019: 55-71.
|
| [16] |
MAO Ting. Analysis of Storage Structure on Linux Operating System[D]. Changsha: Central South University of Forestry & Technology, 2017.
|
|
毛婷. Linux存储结构分析[D]. 长沙: 中南林业科技大学, 2017.
|
 ), XIAO Chaoen1, ZHANG Lei1
), XIAO Chaoen1, ZHANG Lei1