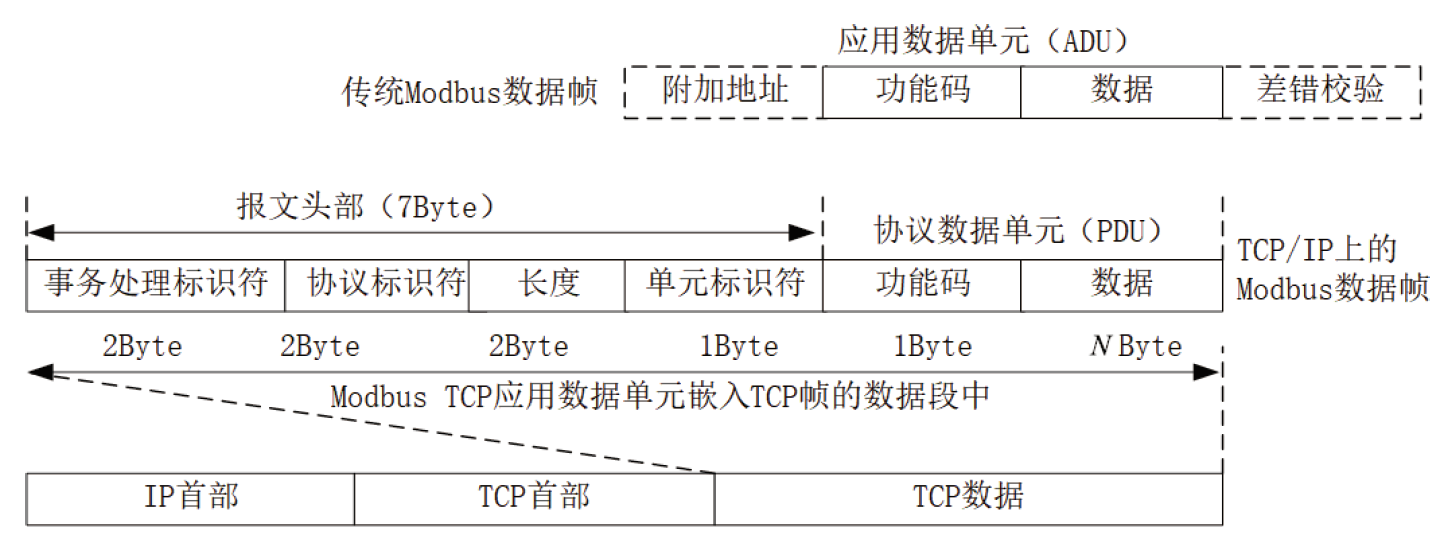
信息网络安全 ›› 2024, Vol. 24 ›› Issue (11): 1710-1720.doi: 10.3969/j.issn.1671-1122.2024.11.010
Modbus TCP协议安全风险分析及对策研究
- 江苏警官学院计算机信息与网络安全系,南京 210031
-
收稿日期:2024-07-03出版日期:2024-11-10发布日期:2024-11-21 -
通讯作者:马如坡mrpjet@163.com -
作者简介:马如坡(1980—),男,河南,讲师,博士,主要研究方向为工业互联网安全、安全防范技术|王群(1971—),男,甘肃,教授,博士,CCF杰出会员,主要研究方向为网络空间安全|尹强(2001—),男,江苏,本科,主要研究方向为工业互联网安全|高谷刚(1974—),男,江苏,高级实验师,博士,主要研究方向为智慧警务、人工智能 -
基金资助:“十四五”江苏省重点学科“网络空间安全”建设项目;江苏本科高校卓越工程师教育培养计划2.0专业项目(安全防范工程专业)
Analysis of Security Risks and Countermeasures for Modbus TCP Protocol
MA Rupo( ), WANG Qun, YIN Qiang, GAO Gugang
), WANG Qun, YIN Qiang, GAO Gugang
- Department of Computer Information and Cyber Security, Jiangsu Police Institute, Nanjing 210031, China
-
Received:2024-07-03Online:2024-11-10Published:2024-11-21
摘要:
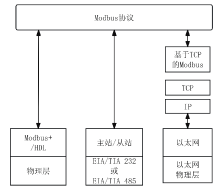
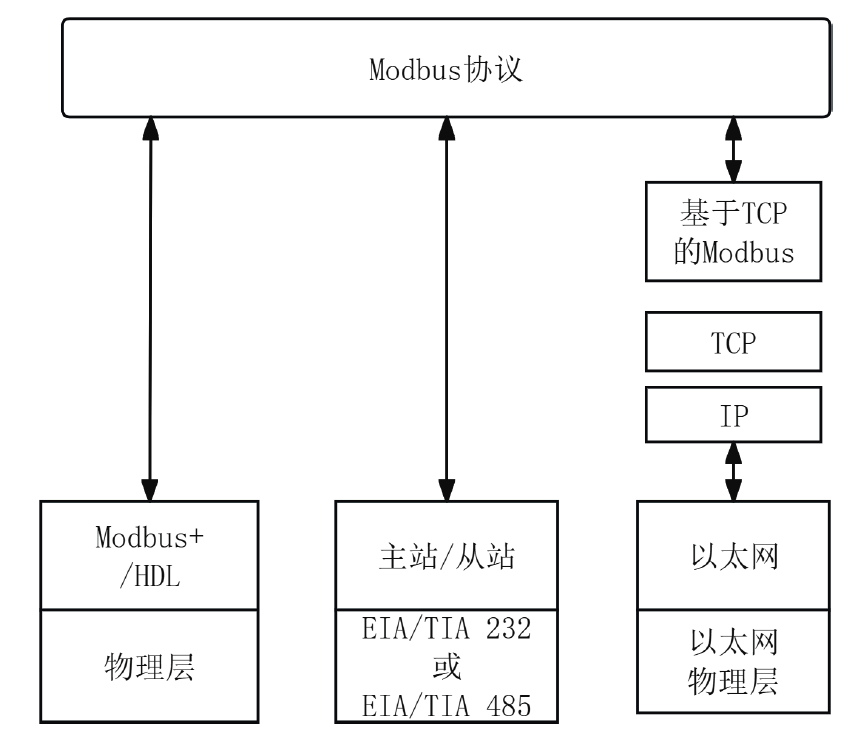
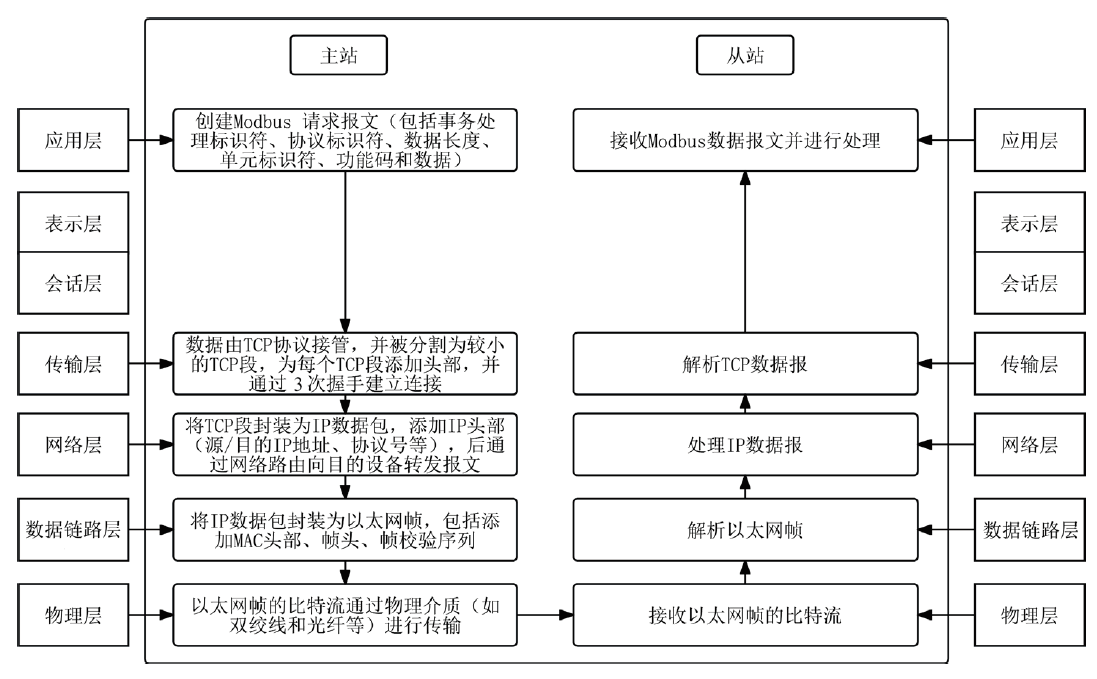
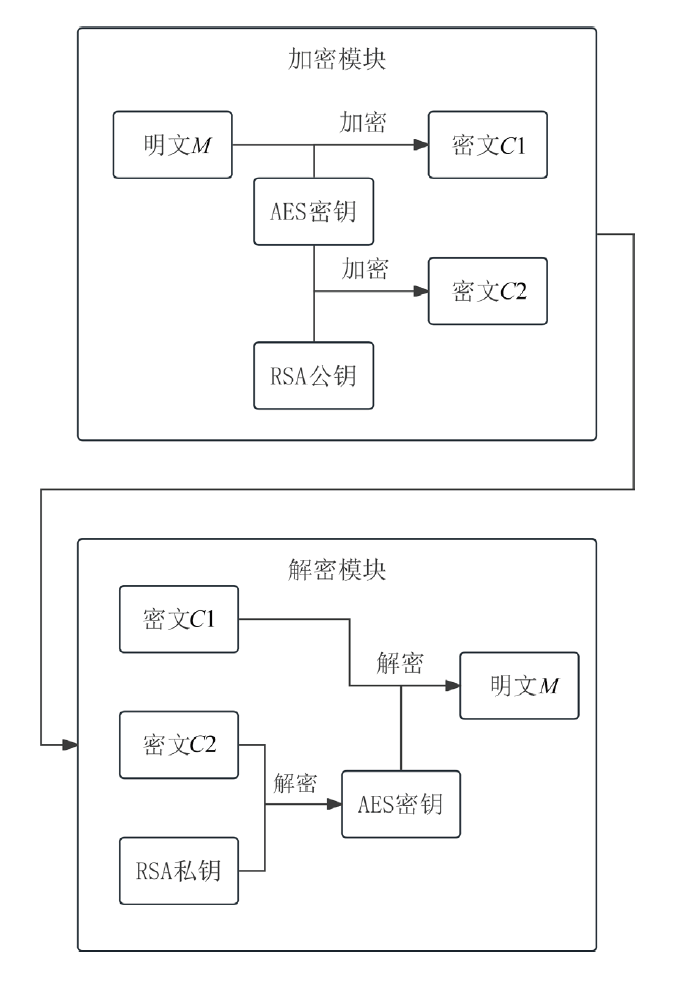
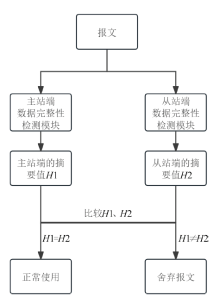
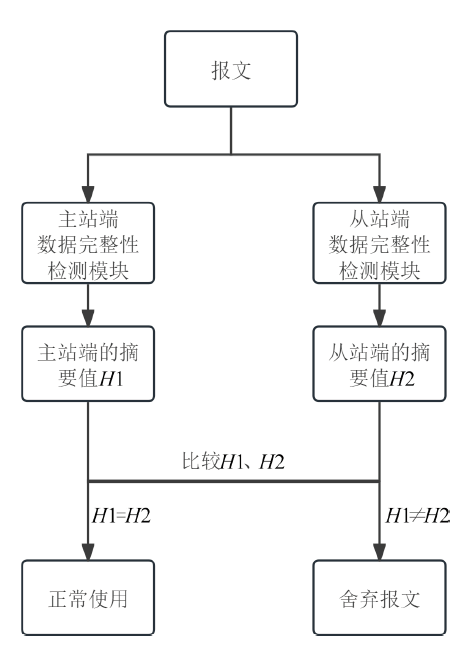
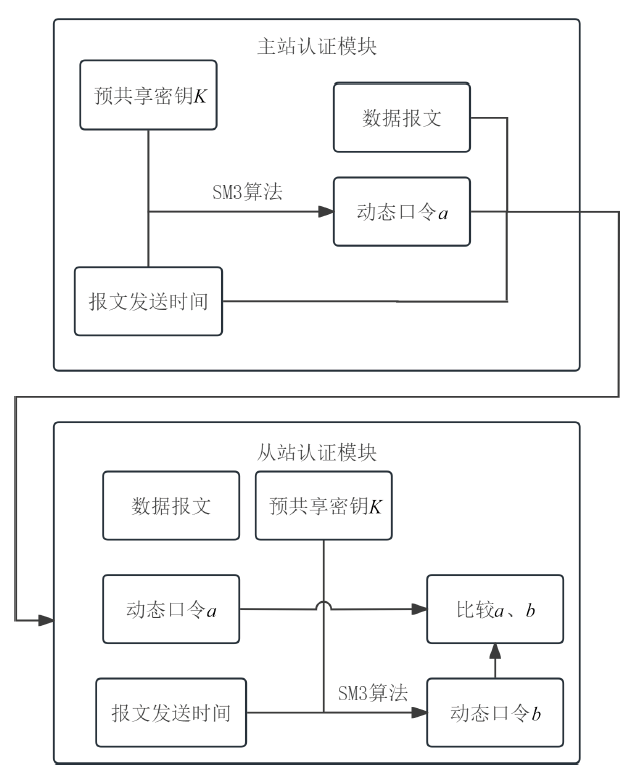
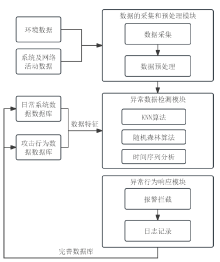
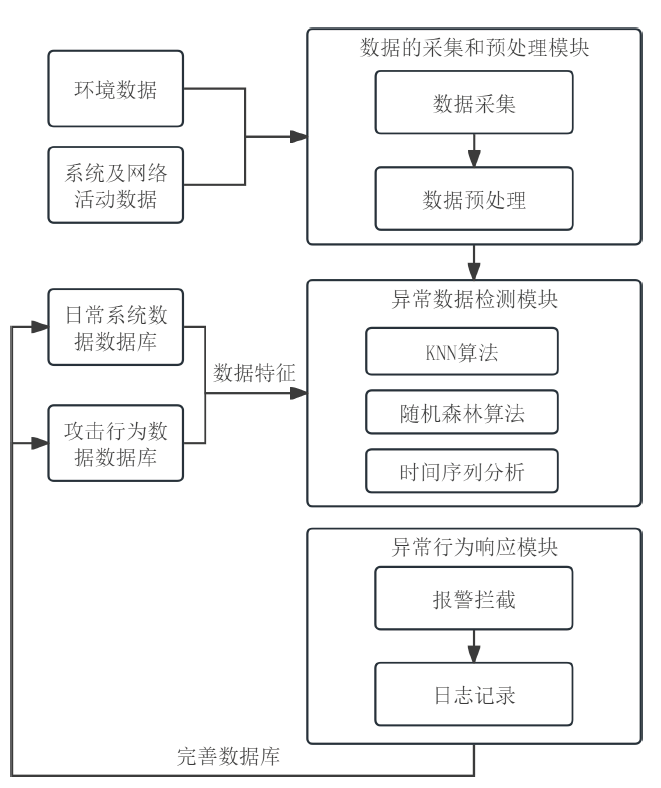
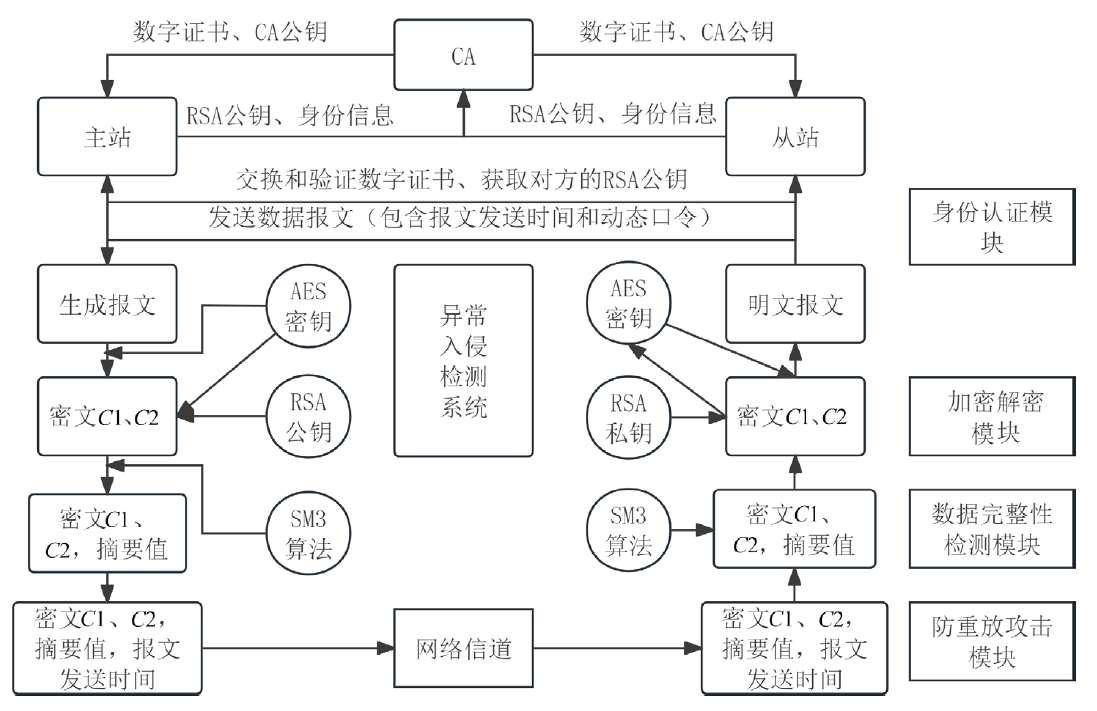
工业互联网作为新一代信息技术与工业系统深度融合的产物,正推动着工业生产方式的变革。然而,工控网络协议在设计之初因注重效率提升和功能实现忽视了一些安全性问题,加之应用中的安全漏洞和异常行为,导致其存在严峻的安全隐患。文章介绍了工业互联网的发展背景、趋势和工控网络协议特点,分析了当前应用最广泛的典型工控网络协议Modbus TCP的安全风险,研究了数据加密、数据完整性检测、身份认证及异常入侵检测等安全对策,提出一套Modbus TCP协议安全方案。该方案包含采用AES算法和RSA算法的数据加密和解密模块、采用SM3算法的数据完整性检测模块、采用动态口令认证技术的身份认证模块和基于数据特征的异常入侵检测系统,同时引入PKI进一步加强工控系统的安全性,为其他工控网络协议的安全防范提供借鉴和参考。
中图分类号:
引用本文
马如坡, 王群, 尹强, 高谷刚. Modbus TCP协议安全风险分析及对策研究[J]. 信息网络安全, 2024, 24(11): 1710-1720.
MA Rupo, WANG Qun, YIN Qiang, GAO Gugang. Analysis of Security Risks and Countermeasures for Modbus TCP Protocol[J]. Netinfo Security, 2024, 24(11): 1710-1720.
| [1] | YANG Ting, ZHANG Jiayuan, HUANG Zaiqi, et al. Survey of Industrial Control Systems Security[J]. Journal of Computer Research and Development, 2022, 59(5): 1035-1053. |
| 杨婷, 张嘉元, 黄在起, 等. 工业控制系统安全综述[J]. 计算机研究与发展, 2022, 59(5): 1035-1053. | |
| [2] | WANG Chonghua, LI Jun, CHEN Xuehong. Research on Industrial Internet Platform Security Protection[J]. Netinfo Security, 2019, 19(9): 6-10. |
| 王冲华, 李俊, 陈雪鸿. 工业互联网平台安全防护体系研究[J]. 信息网络安全, 2019, 19(9): 6-10. | |
| [3] |
HUANG Tao, WANG Zhiwei, LIU Jiachi, et al. Survey of Industrial Control Protocol Security Research[J]. Journal on Communications, 2024, 45(6): 60-74.
doi: 10.11959/j.issn.1000-436x.2024104 |
|
黄涛, 王郅伟, 刘家池, 等. 工控协议安全研究综述[J]. 通信学报, 2024, 45(6): 60-74.
doi: 10.11959/j.issn.1000-436x.2024104 |
|
| [4] | LAI Yingxu, YANG Kaixiang, LIU Jing, et al. Vulnerability Mining Method for Industrial Control Network Protocol Based on Fuzz Testing[J]. Computer Integrated Manufacturing Systems, 2019, 25(9): 2265-2279. |
| 赖英旭, 杨凯翔, 刘静, 等. 基于模糊测试的工控网络协议漏洞挖掘方法[J]. 计算机集成制造系, 2019, 25(9): 2265-2279. | |
| [5] | EREZ N, WOOL A. Control Variable Classification, Modeling and Anomaly Detection in Modbus/TCP SCADA Systems[J]. International Journal of Critical Infrastructure Protection, 2015, 10: 59-70. |
| [6] | HOLASOVA E, KUCHAR K, FUJDIAK R, et al. Security Modules for Securing Industrial Networks[C]// IEEE. 2021 2nd International Conference on Electronics, Communications and Information Technology (CECIT). New York: IEEE, 2021: 1125-1132. |
| [7] | FU Jingqi, CAO Yifan, YI Mubai. Research on Fuzzing Test Case Generation Method Based on Gaussian Mixture Model[C]// IEEE. 2019 Chinese Control and Decision Conference (CCDC). New York: IEEE, 2019: 2674-2678. |
| [8] | SHANG Wenling, LI Lin, WAN Min, et al. Security Defense Model of Modbus TCP Communication Based on Zone/Border Rules[EB/OL]. (2015-07-06)[2024-05-08]. https://api.semanticscholar.org/CorpusID:53410515. |
| [9] | WEI Yiyin, CHAI Xudong. Industrial Internet Technology and Practice[M]. Beijing: Publishing House of Electronics Industry, 2021. |
| 魏毅寅, 柴旭东. 工业互联网技术与实践[M]. 北京: 电子工业出版社, 2021. | |
| [10] | YAO Yu, ZHU Liehuang, WU Chuankun. Industraial Control Network Security Technology and Practice[M]. Beijing: China Machine Press, 2017. |
| 姚羽, 祝烈煌, 武传坤. 工业控制网络安全技术与实践[M]. 北京: 机械工业出版社, 2017. | |
| [11] | ROSA M, OREY D C. A Trivium Curriculum for Mathematics Based on Literacy, Matheracy, and Technoracy: An Ethnomathematics Perspective[J]. ZDM, 2015, 47(4): 587-598. |
| [12] | MAXIMOV A, BIRYUKOV A. Two Trivial Attacks on TRIVIUM[C]// Springer. Proceedings of the 14th International Conference on Selected Areas in Cryptography: LNCS 4876. Heidelberg: Springer, 2007: 36-55. |
| [13] | XU Rongmao. Research and Implementation of Key Technologies for Security Reinforcement of Modbus TCP/IP Protocol[D]. Xi’an: Xidian University, 2017. |
| 徐荣茂. Modbus TCP/IP协议安全加固关键技术研究与实现[D]. 西安: 西安电子科技大学, 2017. | |
| [14] | WU Yihao. Research on Data Integrity Protection Method in Industrial Control System[D]. Beijing: North China Electric Power University, 2021. |
| 吴屹浩. 工控系统中的数据完整性保护方法研究[D]. 北京: 华北电力大学, 2021. | |
| [15] | STEVENS M, LENSTRA A, WEGER B. Chosen-Prefix Collisions for MD5 and Colliding X. 509 Certificates for Different Identities[C]// Springer. International Cryptology Conference. Heidelberg: Springer, 2007: 1-22. |
| [16] | WANG Xiaoyun, YIN Y L, YU Hongbo. Finding Collisions in the Full SHA-1[C]// Springer. Annual International Cryptology Conference. Heidelberg: Springer, 2005: 17-36. |
| [17] | STEVENS M, BURSZTEIN E, KARPMAN P, et al. The First Collision for Full SHA-1[C]// Springer. Annual International Cryptology Conference. Heidelberg: Springer, 2017: 570-596. |
| [18] | DONG Qiao. Research on Information Security Protection Technology Based on Modbus/TCP Protocol[D]. Xi’an: Xi’an Polytechnic University, 2018. |
| 董巧. 基于Modbus/TCP协议的信息安全防护技术研究[D]. 西安: 西安工程大学, 2018. | |
| [19] | BENADDI H, IBRAHIMI K, BENSLIMANE A. Improving the Intrusion Detection System for NSL-KDD Dataset Based on PCA-Fuzzy Clustering-KNN[C]// IEEE. 2018 6th International Conference on Wireless Networks and Mobile Communications (WINCOM). New York: IEEE, 2018: 1-6. |
| [20] | ZHANG Hao, CHEN Long, WEI Zhiqiang. Abnormal Traffic Detection Technology Based on Data Augmentation and Model Update[J]. Netinfo Security, 2020, 20(2): 66-74. |
| 张浩, 陈龙, 魏志强. 基于数据增强和模型更新的异常流量检测技术[J]. 信息网络安全, 2020, 20(2): 66-74. | |
| [21] | YAN Wei, ZHANG Jun. Network Traffic Anomaly Detection Based on Time Series Analysis[J]. Journal of Jilin University (Science Edition), 2017, 55(5): 1249-1254. |
| 闫伟, 张军. 基于时间序列分析的网络流量异常检测[J]. 吉林大学学报(理学版), 2017, 55(5): 1249-1254. |
| [1] | 浦珺妍, 李亚辉, 周纯杰. 基于概率攻击图的工控系统跨域动态安全风险分析方法[J]. 信息网络安全, 2023, 23(9): 85-94. |
| [2] | 沈也明, 李贝贝, 刘晓洁, 欧阳远凯. 基于主动学习的工业互联网入侵检测研究[J]. 信息网络安全, 2021, 21(1): 80-87. |
| [3] | 余果, 王冲华, 陈雪鸿, 李俊. 认证视角下的工业互联网标识解析安全[J]. 信息网络安全, 2020, 20(9): 77-81. |
| [4] | 王冲华, 李俊, 陈雪鸿. 工业互联网平台安全防护体系研究[J]. 信息网络安全, 2019, 19(9): 6-10. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||