信息网络安全 ›› 2024, Vol. 24 ›› Issue (9): 1317-1327.doi: 10.3969/j.issn.1671-1122.2024.09.002
基于身份的可验证定时格签名方案
陈辉焱1( ), 王庆楠1, 谭舜聪1, 谢惠琴1, 姚云飞1,2
), 王庆楠1, 谭舜聪1, 谢惠琴1, 姚云飞1,2
- 1.北京电子科技学院,北京 100070
2.北京邮电大学网络空间安全学院,北京 100876
-
收稿日期:2024-06-07出版日期:2024-09-10发布日期:2024-09-27 -
通讯作者:陈辉焱hychen2001@126.com -
作者简介:陈辉焱(1968—),男,山东,正高级工程师,博士,主要研究方向为后量子密码、公钥密码|王庆楠(2000—),男,广东,硕士研究生,主要研究方向为格密码理论应用与分析|谭舜聪(2000—),男,重庆,硕士研究生,主要研究方向为格密码理论应用与分析|谢惠琴(1992—),女,福建,讲师,博士,主要研究方向为量子密码|姚云飞(1991—),女,山西,博士研究生,主要研究方向为后量子密码学、属性加密、网络空间安全 -
基金资助:北京市自然科学基金(4234084)
Identity-Based Verifiable Timed Signature Scheme on Lattices
CHEN Huiyan1( ), WANG Qingnan1, TAN Shuncong1, XIE Huiqin1, YAO Yunfei1,2
), WANG Qingnan1, TAN Shuncong1, XIE Huiqin1, YAO Yunfei1,2
- 1. Beijing Electronic Science and Technology Institute, Beijing 100070, China
2. School of Cyberspace Security, Beijing University of Posts and Telecommunications, Beijing 100876, China
-
Received:2024-06-07Online:2024-09-10Published:2024-09-27
摘要:
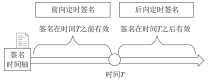
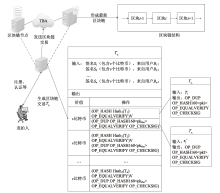
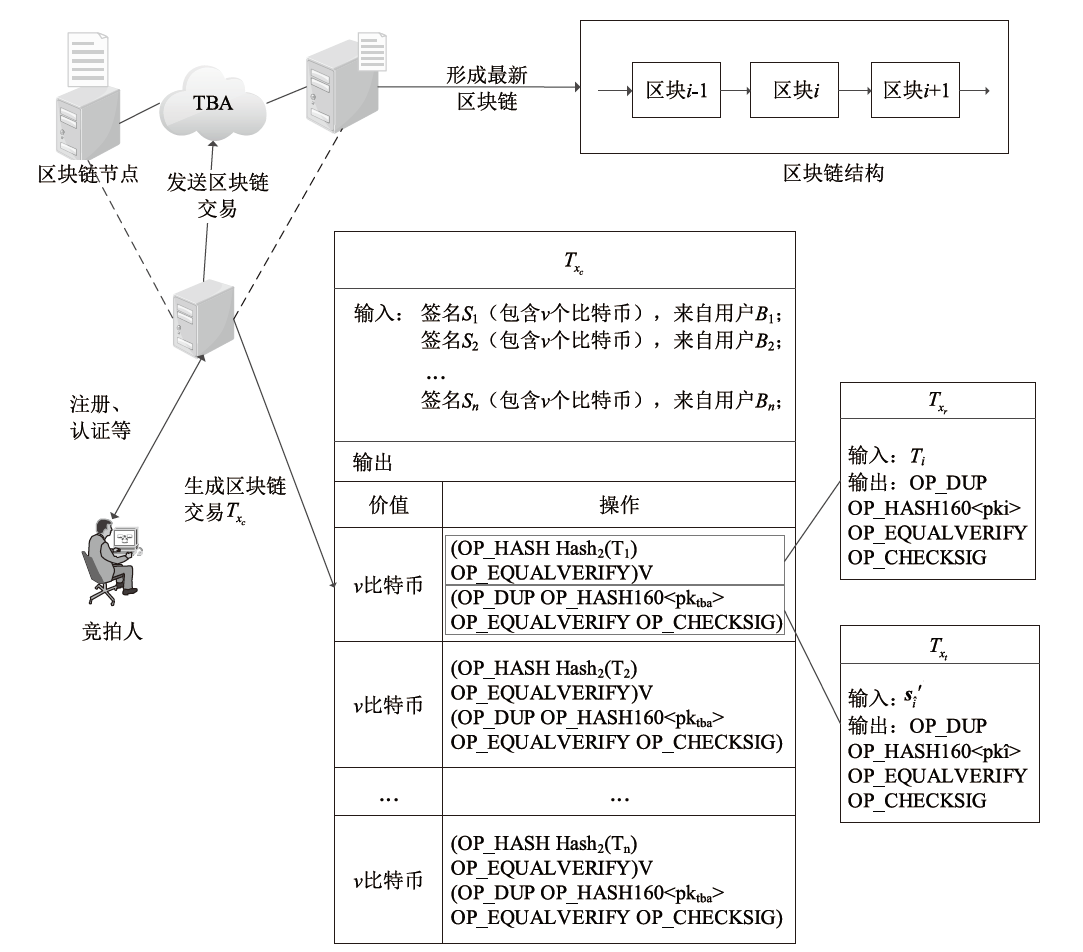
针对现有的可验证定时签名方案无法有效抵抗量子攻击的威胁和无法批处理时间锁谜题的缺陷,文章结合非交互门限秘密共享、批处理时间锁谜题和简洁非交互零知识证明等抗量子组件,基于环上小整数解问题构造了一种基于身份的可验证定时格签名方案。该方案能够实现选择身份攻击下存在性不可伪造性和隐私性,同时避免了传统数字签名繁琐的证书颁发流程,且具备后量子安全和抵抗流氓谜题攻击的能力。文章还基于该方案设计了一个电子拍卖协议,提出一种链上隐私保护惩罚机制,拓展了方案的实用性。文章通过功能性分析和仿真实验展示了方案的实际性能。
中图分类号:
引用本文
陈辉焱, 王庆楠, 谭舜聪, 谢惠琴, 姚云飞. 基于身份的可验证定时格签名方案[J]. 信息网络安全, 2024, 24(9): 1317-1327.
CHEN Huiyan, WANG Qingnan, TAN Shuncong, XIE Huiqin, YAO Yunfei. Identity-Based Verifiable Timed Signature Scheme on Lattices[J]. Netinfo Security, 2024, 24(9): 1317-1327.
表1
系统参数
| 符号 | 含义 |
|---|---|
| 竞拍人 | |
| 证书 | |
| 注册截止时间 | |
| 竞拍截止时间 | |
| OP_DUP | 将堆栈顶部的元素复制到堆栈顶部 |
| OP_EQUALVERIFY | 检查堆栈顶部的两个元素是否相等 |
| 担保交易 | |
| 赎回交易 | |
| Obj | 拍卖物 |
| TBA | 可信拍卖中心 |
| 承诺截止时间 | |
| T | 解谜时间 |
| OP_HASH160 | 将栈顶元素散列到HASH160 |
| OP_CHECKSIG | 验证交易签名 |
| 惩罚交易 | |
| 哈希函数 |
表3
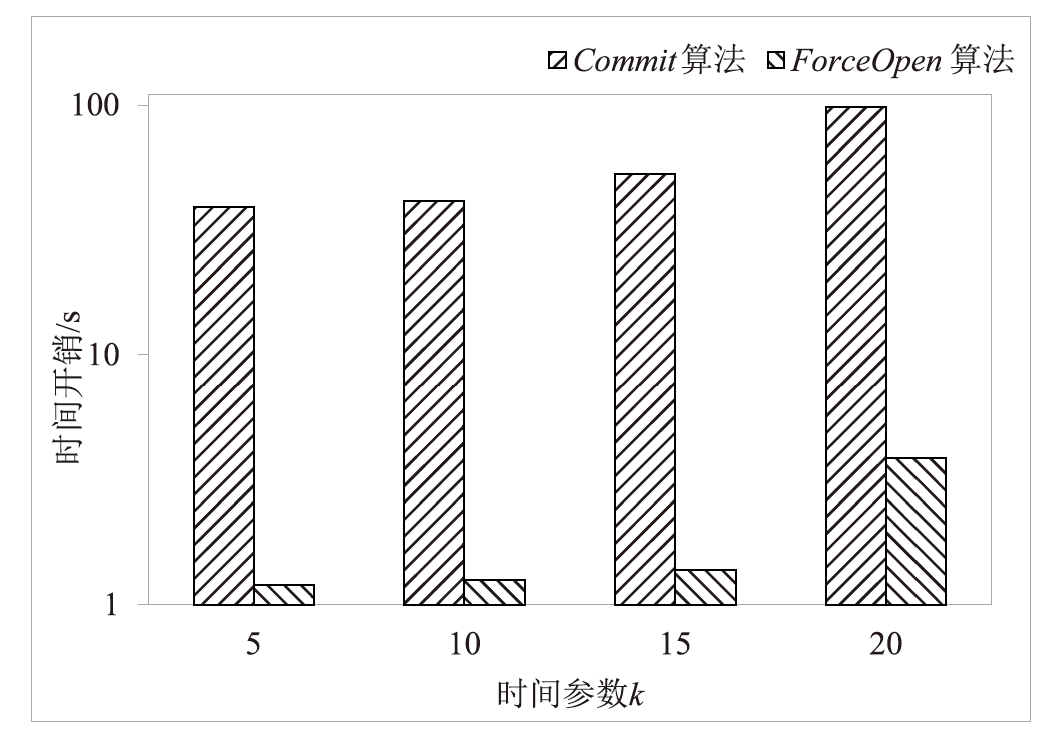
签名算法时间开销和安全等级
| n | B | 生成密钥时间/ms | 签名时间 /ms | 验证时间 /ms | k | k' | ||
|---|---|---|---|---|---|---|---|---|
| 512 | 3 | 95 | 1.00949 | 10 | 173.22 | 378.11 | 27.74 | 25.18 |
| 5 | 122 | 1.00836 | 4 | 175.86 | 390.63 | 35.62 | 32.33 | |
| 7 | 140 | 1.00775 | 4 | 195.78 | 386.80 | 40.88 | 37.10 | |
| 1024 | 3 | 345 | 1.00441 | 4 | 373.95 | 740.80 | 100.70 | 91.43 |
| 5 | 415 | 1.00388 | 8 | 356.66 | 766.12 | 121.20 | 109.90 | |
| 7 | 470 | 1.00356 | 4 | 368.60 | 751.37 | 137.20 | 124.60 | |
| 2048 | 3 | 1000 | 1.00204 | 18 | 764.83 | 1502.00 | 292.00 | 265.00 |
| 5 | 1200 | 1.00177 | 10 | 739.85 | 1504.57 | 350.40 | 318.00 | |
| 7 | 1380 | 1.00160 | 7 | 736.49 | 1501.81 | 403.00 | 365.70 |
| [1] | RIVEST R L, SHAMIR A, WAGNER D A. Time-Lock Puzzles and Timed-Release Crypto[EB/OL]. (2023-03-29)[2024-05-22]. https://dspace.mit.edu/handle/1721.1/149822?show=full. |
| [2] | MALAVOLTA G, THYAGARAJAN S A K. Homomorphic Time-Lock Puzzles and Applications[C]// Springer. 39th Annual International Cryptology Conference. Heidelberg: Springer, 2019: 620-649. |
| [3] | LIU Yi, WANG Qi, YIU S M. Towards Practical Homomorphic Time-Lock Puzzles: Applicability and Verifiability[C]// Springer. 27th European Symposium on Research in Computer Security. Heidelberg: Springer, 2022: 424-443. |
| [4] | DUJMOVIC J, GARG R, MALAVOLTA G. Time-Lock Puzzles with Efficient Batch Solving[C]// Springer. 43th Annual International Conference. Heidelberg: Springer, 2024: 311-341. |
| [5] | CHVOJKA P, JAGER T, SLAMANIG D, et al. Versatile and Sustainable Timed-Release Encryption and Sequential Time-Lock Puzzles[C]// Springer. 26th European Symposium on Research in Computer Security. Heidelberg: Springer, 2021: 64-85. |
| [6] | LOE A, MEDLEY L, O’CONNELL C, et al. Applications of Timed-Release Encryption with Implicit Authentication[C]// Springer. 14th International Conference on Cryptology in Africa. Heidelberg: Springer, 2023: 490-515. |
| [7] | BONEH D, NAOR M. Timed Commitments[C]// Springer. 20th Annual International Cryptology Conference. Heidelberg: Springer, 2000: 236-254. |
| [8] | KATZ J, LOSS J, XU Jiayu. On the Security of Time-Lock Puzzles and Timed Commitments[C]// Springer. Theory of Cryptography:18th International Conference. Heidelberg: Springer, 2020: 390-413. |
| [9] | ARUN A, BONNEAU J, CLARK J. Short-Lived Zero-Knowledge Proofs and Signatures[C]// Springer. 28th International Conference on the Theory and Application of Cryptology and Information Security. Heidelberg: Springer, 2022: 487-516. |
| [10] | THYAGARAJAN S A K, BHAT A, MALAVOLTA G, et al. Verifiable Timed Signatures Made Practical[C]// ACM. 2020 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2020: 1733-1750. |
| [11] | MALAVOLTA G, MORENO-SANCHEZ P, KATE A, et al. Concurrency and Privacy with Payment-Channel Networks[C]// ACM. 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 455-471. |
| [12] | BONEH D, DRIJVERS M, NEVEN G. Compact Multi-Signatures for Smaller Blockchains[C]// Springer. 24th International Conference on the Theory and Application of Cryptology and Information Security. Heidelberg: Springer, 2018: 435-464. |
| [13] | BENTOV I, KUMARESAN R. How to Use Bitcoin to Design Fair Protocols[C]// Springer. 34th Annual Cryptology Conference. Heidelberg: Springer, 2014: 421-439. |
| [14] | THYAGARAJAN S A K, MALAVOLTA G, SCHMID F, et al. Verifiable Timed Linkable Ring Signatures for Scalable Payments for Monero[C]// Springer. 27th European Symposium on Research in Computer Security. Heidelberg: Springer, 2022: 467-486. |
| [15] | ZHOU Xiaotong, HE Debiao, NING Jianting, et al. Efficient Construction of Verifiable timed Signatures and Its Application in Scalable Payments[J]. IEEE Transactions on Information Forensics and Security, 2023, 18: 5345-5358. |
| [16] | HOU Huiying, NING Jianting, HUANG Xinyi, et al. Verifiable Attribute-Based Timed Signatures and Its Applications[J]. Journal of Software, 2023, 34(5): 2465-2481. |
| 侯慧莹, 宁建廷, 黄欣沂, 等. 可验证的属性基定时签名方案及其应用[J]. 软件学报, 2023, 34(5):2465-2481. | |
| [17] | BAO Zijian, HE Debiao, FENG Qi, et al. Constant-Size Verifiable Timed Signatures from RSA Group for Bitcoin-Based Voting Protocols[J]. IEEE Transactions on Services Computing, 2024, 17(4): 1414-1425. |
| [18] | GOLDREICH O, GOLDWASSER S, HALEVI S. Public-Key Cryptosystems from Lattice Reduction Problems[C]// Springer. 17th Annual International Cryptology Conference. Heidelberg: Springer, 1997: 112-131. |
| [19] | NIST. NIST Announces First Four Quantum-Resistant Cryptographic Algorithms[EB/OL]. (2022-07-05)[2024-05-20]. https://www.nist.gov/news-events/news/2022/07/nist-announces-first-four-quantum-resistant-cryptographic-algorithms. |
| [20] | SHAMIR A. Identity-Based Cryptosystems and Signature Schemes[C]// Springer. Annual International Cryptology Conference. Heidelberg: Springer, 1985: 47-53. |
| [21] |
RAJABI B, ESLAMI Z. A Verifiable Threshold Secret Sharing Scheme Based on Lattices[J]. Information Sciences, 2019, 501: 655-661.
doi: 10.1016/j.ins.2018.11.004 |
| [22] | ISHAI Y, SU Hang, WU D J. Shorter and Faster Post-Quantum Designated-Verifier zkSNARKs from Lattices[C]// ACM. 2021 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2021: 212-234. |
| [23] | DUCAS L, DURMUS A, LEPOINT T, et al. Lattice Signatures and Bimodal Gaussians[C]// Springer. 33rd Annual Cryptology Conference. Heidelberg: Springer, 2013: 40-56. |
| [24] | BERT P, FOUQUE P A, ROUX-LANGLOIS A, et al. Practical Implementation of Ring-SIS/LWE Based Signature and IBE[C]// Springer. Post-Quantum Cryptography:9th International Conference. Heidelberg: Springer, 2018: 271-291. |
| [25] | BELLARE M, NEVEN G. Multi-Signatures in the Plain Public-Key Model and a General Forking Lemma[C]// ACM. 13th ACM Conference on Computer and Communications Security. New York: ACM, 2006: 390-399. |
| [26] | GENTRY C, PEIKERT C, VAIKUNTANATHAN V. How to Use a Short Basis: Trapdoors for Hard Lattices and New Cryptographic Constructions[C]// ACM. The 40th Annual ACM Symposium on Theory of Computing. New York: ACM, 2008: 197-206. |
| [27] | GENISE N, LI Baiyu. Gadget-Based iNTRU Lattice Trapdoors[C]// Springer. 21st International Conference on Cryptology in India. Heidelberg: Springer, 2020: 601-623. |
| [1] | 李增鹏, 王思旸, 王梅. 隐私保护近邻检测研究[J]. 信息网络安全, 2024, 24(6): 817-830. |
| [2] | 杜育松, 江思维, 沈静, 张家豪. 一种抵御计时攻击的指数Bernoulli精确采样算法[J]. 信息网络安全, 2024, 24(6): 855-862. |
| [3] | 叶清, 何俊霏, 杨智超. 基于格的可搜索公钥加密研究进展[J]. 信息网络安全, 2024, 24(6): 903-916. |
| [4] | 刘芹, 王卓冰, 余纯武, 王张宜. 面向云安全的基于格的高效属性基加密方案[J]. 信息网络安全, 2023, 23(9): 25-36. |
| [5] | 俞惠芳, 乔一凡, 孟茹. 面向区块链金融的抗量子属性基门限环签密方案[J]. 信息网络安全, 2023, 23(7): 44-52. |
| [6] | 李增鹏, 王梅, 陈梦佳. 新形态伪随机函数研究[J]. 信息网络安全, 2023, 23(5): 11-21. |
| [7] | 杨婉霞, 陈帅, 管磊, 杨忠良. 宋词自动生成的信息隐藏算法[J]. 信息网络安全, 2022, 22(7): 46-54. |
| [8] | 王子恒, 吴涵, 解建国, 陈小明. 基于VLAN的超晶格密钥分发跨网实现[J]. 信息网络安全, 2022, 22(4): 49-57. |
| [9] | 余发江, 贾耀民. 对DSA和ECDSA的一种改进格攻击[J]. 信息网络安全, 2022, 22(2): 11-20. |
| [10] | 张郅, 李欣, 叶乃夫, 胡凯茜. 融合多重风格迁移和对抗样本技术的验证码安全性增强方法[J]. 信息网络安全, 2022, 22(10): 129-135. |
| [11] | 陶云亭, 孔凡玉, 于佳, 徐秋亮. 抗量子格密码体制的快速数论变换算法研究综述[J]. 信息网络安全, 2021, 21(9): 46-51. |
| [12] | 顾兆军, 蔡畅, 王明. 基于改进保留格式加密的民航旅客数据脱敏方法[J]. 信息网络安全, 2021, 21(5): 39-47. |
| [13] | 周艺华, 董松寿, 杨宇光. 标准模型下基于格的身份代理部分盲签名方案[J]. 信息网络安全, 2021, 21(3): 37-43. |
| [14] | 王耀杰, 杨晓元, 刘文超. 基于数字化卡登格的生成图像隐写方案[J]. 信息网络安全, 2021, 21(2): 70-77. |
| [15] | 郎为民, 张汉, 赵毅丰, 姚晋芳. 一种基于区块链的物联网行为监控和活动管理方案[J]. 信息网络安全, 2020, 20(2): 22-29. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||