信息网络安全 ›› 2024, Vol. 24 ›› Issue (7): 1129-1137.doi: 10.3969/j.issn.1671-1122.2024.07.014
隐私保护体系下网络威胁情报共享的研究现状和方案设计
- 北京市公安局关键信息基础设施保护中心,北京 100029
-
收稿日期:2023-12-25出版日期:2024-07-10发布日期:2024-08-02 -
通讯作者:刘钦菊15611529581@163.com -
作者简介:问闻(1980—),男,河南,硕士,主要研究方向为网络空间安全执法技术|刘钦菊(1993—),女,山东,博士,主要研究方向为密码学、隐私计算技术|邝琳(1980—),女,北京,硕士,主要研究方向为网络空间安全|任雪静(1999—),女,北京,主要研究方向为网络空间安全。
Research and Scheme Design of Cyber Threat Intelligence Sharing under Privacy Protection System
WEN Wen, LIU Qinju( ), KUANG Lin, REN Xuejing
), KUANG Lin, REN Xuejing
- Beijing Municipal Public Security Bureau Critical Information Infrastructre Protection Center, Beijing 100029, China
-
Received:2023-12-25Online:2024-07-10Published:2024-08-02
摘要:
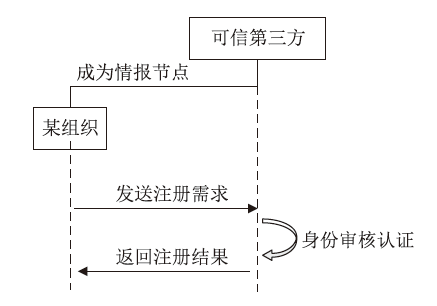
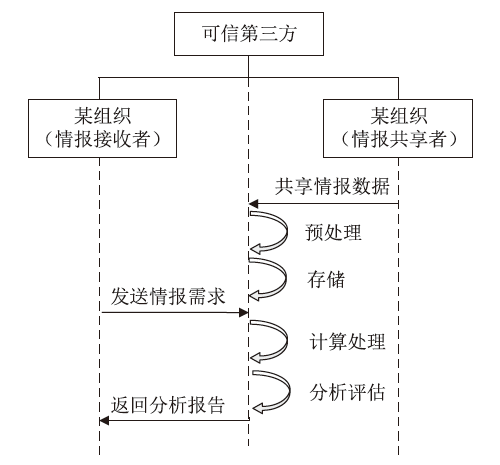
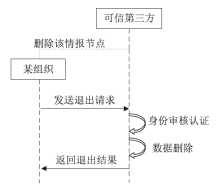
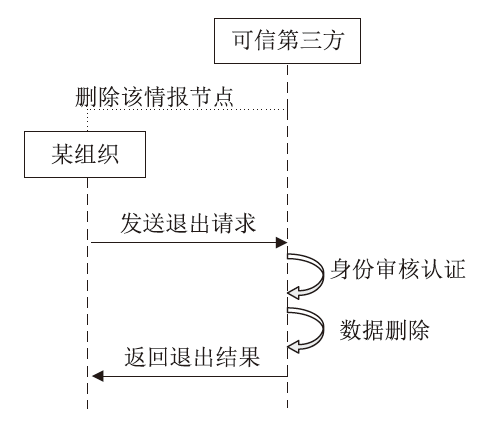
网络威胁情报共享有利于实现网络安全态势感知以应对网络威胁,但网络威胁情报高度敏感,处理不当极易导致共享者利益受损或暴露安全防护弱点等严重后果。因此,网络威胁情报共享的前提是保证数据安全和用户隐私。文章聚焦隐私保护体系下的网络威胁情报共享研究,首先对网络威胁情报、网络威胁情报共享、隐私计算技术等相关内容进行总结分析;然后从网络威胁情报共享面临的安全隐私问题出发,对近年的网络威胁情报共享技术路径和研究现状进行梳理和分析;最后设计一个基于隐私计算技术的网络威胁情报共享平台方案。
中图分类号:
引用本文
问闻, 刘钦菊, 邝琳, 任雪静. 隐私保护体系下网络威胁情报共享的研究现状和方案设计[J]. 信息网络安全, 2024, 24(7): 1129-1137.
WEN Wen, LIU Qinju, KUANG Lin, REN Xuejing. Research and Scheme Design of Cyber Threat Intelligence Sharing under Privacy Protection System[J]. Netinfo Security, 2024, 24(7): 1129-1137.
| [1] | FU Jing. Exploration and Practice of Security Protection of Critical Information Infrastructure of Water Conservancy[J]. Netinfo Security, 2023, 23(8): 121-127. |
| 付静. 水利关键信息基础设施安全保护探索与实践[J]. 信息网络安全, 2023, 23(8):121-127. | |
| [2] | TOUNSI W, RAIS H. A Survey on Technical Threat Intelligence in the Age of Sophisticated Cyber Attacks[J]. Computers & Security, 2018, 72: 212-233. |
| [3] | MCMILLAN R, PRATAP K. Market Guide for Security Threat Intelligence Services[EB/OL]. (2014-10-14)[2023-11-12]. https://www.gartner.com/en/documents/2874317?ref=ddisp. |
| [4] | LIN Yue, LIU Peng, WANG He, et al. Overview of Threat Intelligence Sharing and Exchange in Cybersecurity[J]. Journal of Computer Research and Development, 2020, 57(10): 2052-2065. |
| 林玥, 刘鹏, 王鹤, 等. 网络安全威胁情报共享与交换研究综述[J]. 计算机研究与发展, 2020, 57(10):2052-2065. | |
| [5] | National Industrial Information Security Development Research Center. Cyber Security Threat Intelligence Industry Development Report(2021)[R]. China: National Industrial Information Security Development Research Center, 2021-dc-24, 2021. |
| 国家工业信息安全发展研究中心. 网络安全威胁情报行业发展报告(2021)[R]. 中国: 国家工业信息安全发展研究中心,2021-dc-24,2021. | |
| [6] | WAGNER T D, MAHBUB K, PALOMAR E, et al. Cyber Threat Intelligence Sharing: Survey and Research Directions[EB/OL]. (2018-08-06)[2023-11-12]. https://doi.org/10.1016/j.cose.2019.101589. |
| [7] |
LI Fenghua, LI Hui, JIA Yan, et al. Privacy Computing: Concept, Connotation and Its Research Trend[J]. Journal on Communications, 2016, 37(4): 1-11.
doi: 10.11959/j.issn.1000-436x.2016078 |
|
李凤华, 李晖, 贾焰, 等. 隐私计算研究范畴及发展趋势[J]. 通信学报, 2016, 37(4):1-11.
doi: 10.11959/j.issn.1000-436x.2016078 |
|
| [8] | HUO Wei, YU Yu, YANG Kang, et al. Privacy-Preserving Cryptographic Algorithms and Protocols: A Survey on Designs and Applications[J]. Scientia Sinica(Informationis), 2023, 53(9): 1688-1733. |
| 霍炜, 郁昱, 杨糠, 等. 隐私保护计算密码技术研究进展与应用[J]. 中国科学:信息科学, 2023, 53(9):1688-1733. | |
| [9] | YAO A C C. How to Generate and Exchange Secrets[C]// IEEE. 27th Annual Symposium on Foundations of Computer Science. New York: IEEE, 1986: 162-167. |
| [10] | DEMMLER D, SCHNEIDER T, ZOHNER M. ABY-A Framework for Efficient Mixed-Protocol Secure Two-Party Computation[EB/OL]. (2015-02-01)[2023-11-14]. https://www.semanticscholar.org/paper/ABY-A-Framework-for-Efficient-Mixed-Protocol-Secure-Demmler-Schneider/20b5b5c25e2b56693b38fe7f69caddca78872085?p2df. |
| [11] | Github. MP-SPDZ[EB/OL]. (2023-12-14)[2023-12-18]. https://github.com/data61/MP-SPDZ. |
| [12] | IMPAGLIAZZO R, RUDICH S. Limits on the Provable Consequences of One-Way Permutations[C]// ACM. The Twenty-First Annual ACM symposium on Theory of Computing. New York: ACM, 1989: 44-61. |
| [13] | GOLDREICH O, MICALI S, WIGDERSON A. How to Play any Mental Game, or a Completeness Theorem for Protocols with Honest Majority[M]. New York: ACM, 2019. |
| [14] | MCMAHAN H B, MOORE E, RAMAGE D, et al. Communication-Efficient Learning of Deep Networks from Decentralized Data[EB/OL]. (2016-02-17)[2023-11-12]. https://www.semanticscholar.org/paper/Communication-Efficient-Learning-of-Deep-Networks-McMahan-Moore/d1dbf643447405984eeef098b1b320dee0b3b8a7?p2df. |
| [15] | YANG Qiang, LIU Yang, CHEN Tianjian, et al. Federated Machine Learning: Concept and Applications[J]. ACM Transactions on Intelligent Systems and Technology, 2019, 10(2): 1-19. |
| [16] | KAIROUZ P, MCMAHAN H B, AVENT B, et al. Advances and Open Problems in Federated Learning[J]. Foundations and Trends in Machine Learning, 2021, 14(1-2): 1-21. |
| [17] | SABT M, ACHEMLAL M, BOUABDALLAH A. Trusted Execution Environment:What It is, and What It Is Not[C]// IEEE. 2015 IEEE Trustcom/BigDataSE/ISPA. New York: IEEE, 2015: 57-64. |
| [18] | ARFAOUI G, GHAROUT S, TRAORÉ J. Trusted Execution Environments: A Look under the Hood[C]// IEEE. 2014 2nd IEEE International Conference on Mobile Cloud Computing, Services, and Engineering. New York: IEEE, 2014: 259-266. |
| [19] | NAKAMOTO S. Bitcoin: A Peer-to-Peer Electronic Cash System[EB/OL]. [2023-11-12]. https://www.semanticscholar.org/paper/Bitcoin%3A-A-Peer-to-Peer-Electronic-Cash-System-Hunt/4e9ec92a90c5d571d2f1d496f8df01f0a8f38596?p2df. |
| [20] | ZHENG Zibin, XIE Shaoan, DAI Hongning, et al. Blockchain Challenges and Opportunities: A Survey[J]. International Journal of Web and Grid Services, 2018, 14(4): 352-375. |
| [21] | SADIQUE F, BAKHSHALIYEV K, SPRINGER J, et al. A System Architecture of Cybersecurity Information Exchange with Privacy(CYBEX-P)[C]// IEEE. 2019 IEEE 9th Annual Computing and Communication Workshop and Conference. New York: IEEE, 2019: 493-498. |
| [22] | HOMAN D, SHIEL I, THORPE C. A New Network Model for Cyber Threat Intelligence Sharing Using Blockchain Technology[C]// IEEE. 2019 10th IFIP International Conference on New Technologies, Mobility and Security. New York: IEEE, 2019: 1-6. |
| [23] | BARNUM S. Standardizing Cyber Threat Intelligence Information with the Structured Threat Information Expression(STIXTM)[ EB/OL]. [2023-11-12]. https://www.mitre.org/sites/default/files/publications/stix.pdf. |
| [24] | FUENTES J M, GONZÁLEZ-MANZANO L, TAPIADOR J, et al. PRACIS: Privacy-Preserving and Aggregatable Cybersecurity Information Sharing[J]. Computers & Security, 2017, 69: 127-141. |
| [25] | BADSHA S, VAKILINIA I, SENGUPTA S. Privacy Preserving Cyber Threat Information Sharing and Learning for Cyber Defense[C]// IEEE. 2019 IEEE 9th Annual Computing and Communication Workshop and Conference (CCWC). New York: IEEE, 2019: 708-714. |
| [26] | SARHAN M, LAYEGHY S, MOUSTAFA N, et al. Cyber Threat Intelligence Sharing Scheme Based on Federated Learning for Network Intrusion Detection[EB/OL]. (2022-10-07)[2023-11-12]. https://link.springer.com/article/10.1007/s10922-022-09691-3?utm_source=xmol&utm_content=meta. |
| [27] | NGUYEN K, PAL S, JADIDI Z, et al. A Blockchain-Enabled Incentivised Framework for Cyber Threat Intelligence Sharing in ICS[C]// IEEE. 2022 IEEE International Conference on Pervasive Computing and Communications Workshops and other Affiliated Events(PerCom Workshops). New York: IEEE, 2022: 261-266. |
| [28] | BANDARA E, SHETTY S, MUKKAMALA R, et al. LUUNU-Blockchain, Model Cards and Federated Learning Enabled Cyber Threat Intelligence Sharing Platform[C]// IEEE. 2022 Annual Modeling and Simulation Conference(ANNSIM). New York: IEEE, 2022: 235-245. |
| [1] | 张长琳, 仝鑫, 佟晖, 杨莹. 面向网络安全领域的大语言模型技术综述[J]. 信息网络安全, 2024, 24(5): 778-793. |
| [2] | 杨志鹏, 刘代东, 袁军翼, 魏松杰. 基于自注意力机制的网络局域安全态势融合方法研究[J]. 信息网络安全, 2024, 24(3): 398-410. |
| [3] | 付静. 水利关键信息基础设施安全保护探索与实践[J]. 信息网络安全, 2023, 23(8): 121-127. |
| [4] | 孙珵珵. 网络安全治理对策研究[J]. 信息网络安全, 2023, 23(6): 104-110. |
| [5] | 王晓狄, 黄诚, 刘嘉勇. 面向网络安全开源情报的知识图谱研究综述[J]. 信息网络安全, 2023, 23(6): 11-21. |
| [6] | 李冬, 于俊清, 文瑞彬, 谢一丁. 基于IPv6的容器云内生安全机制[J]. 信息网络安全, 2023, 23(12): 21-28. |
| [7] | 金志刚, 刘凯, 武晓栋. 智能电网AMI领域IDS研究综述[J]. 信息网络安全, 2023, 23(1): 1-8. |
| [8] | 孙鹏宇, 谭晶磊, 李晨蔚, 张恒巍. 基于时间微分博弈的网络安全防御决策方法[J]. 信息网络安全, 2022, 22(5): 64-74. |
| [9] | 金波, 唐前进, 唐前临. CCF计算机安全专业委员会2022年网络安全十大发展趋势解读[J]. 信息网络安全, 2022, 22(4): 1-6. |
| [10] | 陈妍, 韦湘, 陆臻. 云计算环境下网络安全产品检测方法研究[J]. 信息网络安全, 2022, 22(12): 1-6. |
| [11] | 刘忻, 王家寅, 杨浩睿, 张瑞生. 一种基于区块链和secGear框架的车联网认证协议[J]. 信息网络安全, 2022, 22(1): 27-36. |
| [12] | 白宏鹏, 邓东旭, 许光全, 周德祥. 基于联邦学习的入侵检测机制研究[J]. 信息网络安全, 2022, 22(1): 46-54. |
| [13] | 顾兆军, 姚峰, 丁磊, 隋翯. 基于半实物的机场供油自控系统网络安全测试[J]. 信息网络安全, 2021, 21(9): 16-24. |
| [14] | 蔡满春, 王腾飞, 岳婷, 芦天亮. 基于ARF的Tor网站指纹识别技术[J]. 信息网络安全, 2021, 21(4): 39-48. |
| [15] | 赵小林, 赵斌, 赵晶晶, 薛静锋. 基于攻击识别的网络安全度量方法研究[J]. 信息网络安全, 2021, 21(11): 17-27. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||