信息网络安全 ›› 2024, Vol. 24 ›› Issue (4): 614-625.doi: 10.3969/j.issn.1671-1122.2024.04.011
EFIS数据源防御部署优化的非合作博弈模型
- 1.中国民航大学信息安全测评中心,天津 300300
2.中国民航大学计算机科学与技术学院,天津 300300
3.中国民航大学航空工程学院,天津 300300
-
收稿日期:2024-01-29出版日期:2024-04-10发布日期:2024-05-16 -
通讯作者:隋翯hsui@cauc.edu.cn -
作者简介:顾兆军(1966—),男,山东,教授,博士,主要研究方向为网络与信息安全|张一诺(1999—),女,甘肃,硕士研究生,主要研究方向为航空电子系统安全|扬雪影(1999—),女,宁夏,硕士研究生,主要研究方向为民航信息系统|隋翯(1987—),男,吉林,讲师,博士,CCF会员,主要研究方向为网络与信息安全、航空电子系统 -
基金资助:国家自然科学基金(U2333201)
A Non-Cooperative Game Model for Optimizing EFIS Data Source Defense Deployment
GU Zhaojun1, ZHANG Yinuo1,2, YANG Xueying1,2, SUI He3( )
)
- 1. Information Security Evaluation Center, Civil Aviation University of China, Tianjin 300300, China
2. College of Computer Science and Technology, Civil Aviation University of China, Tianjin 300300, China
3. College of Aeronautical Engineering, Civil Aviation University of China, Tianjin 300300, China
-
Received:2024-01-29Online:2024-04-10Published:2024-05-16
摘要:
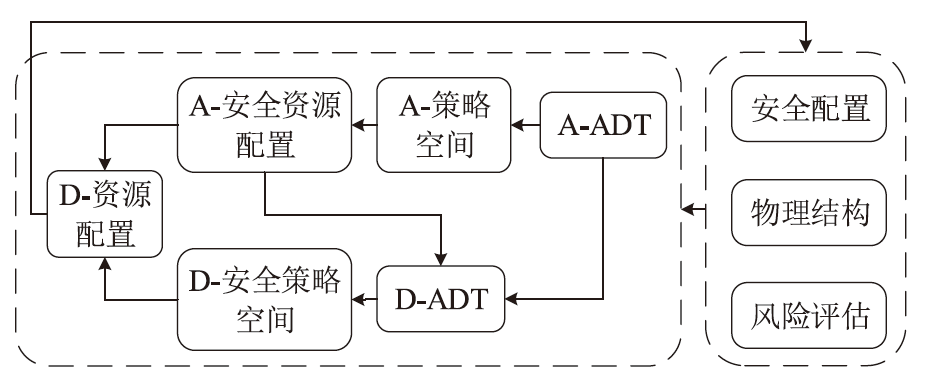
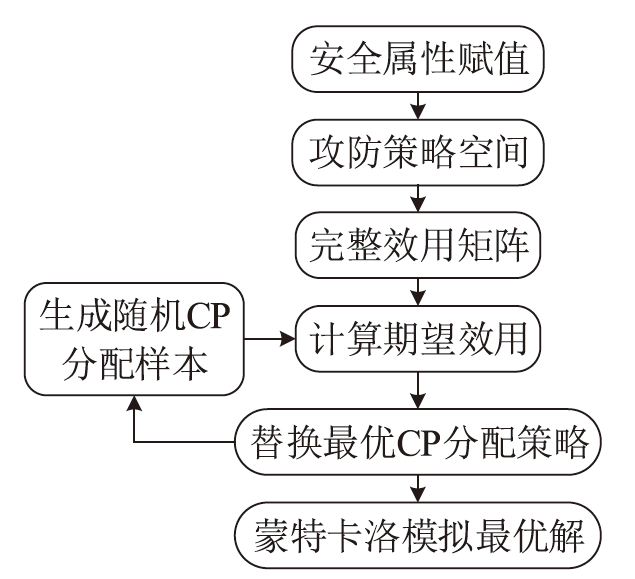
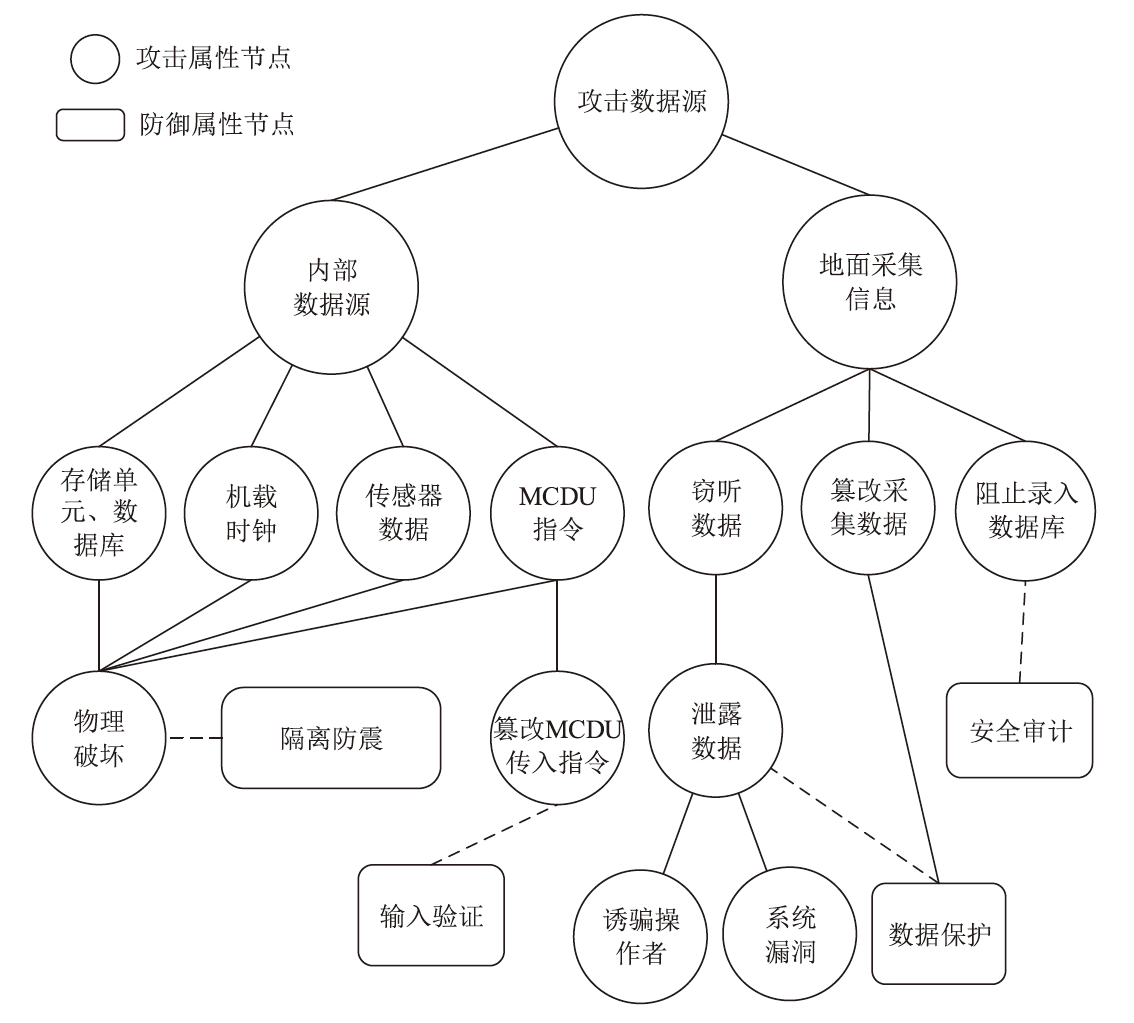
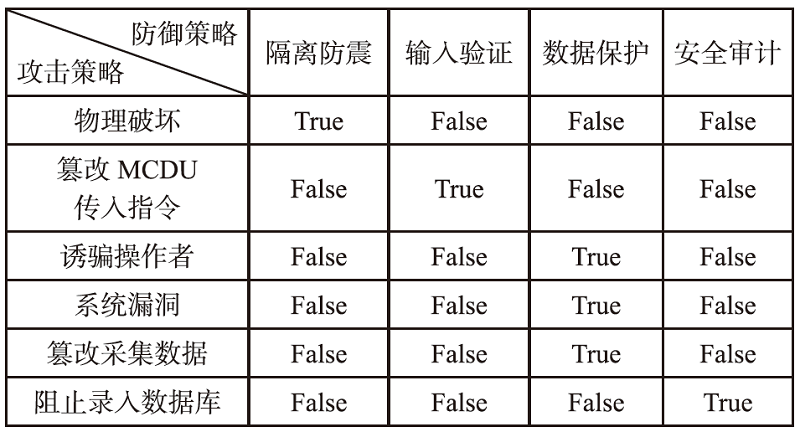
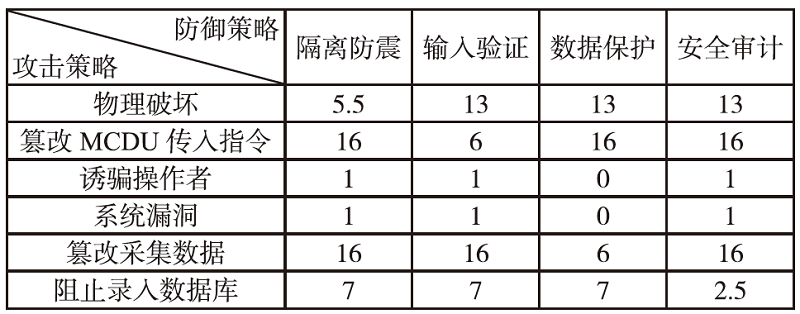
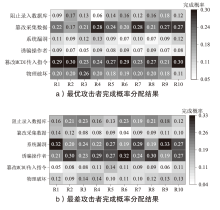
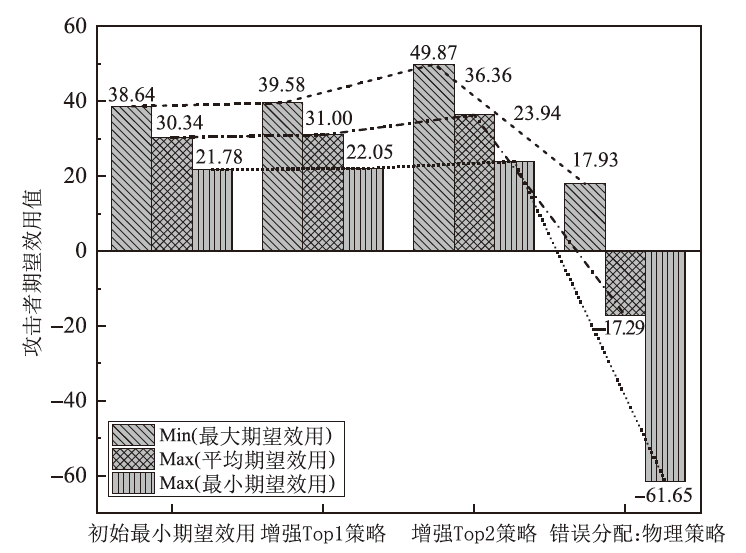
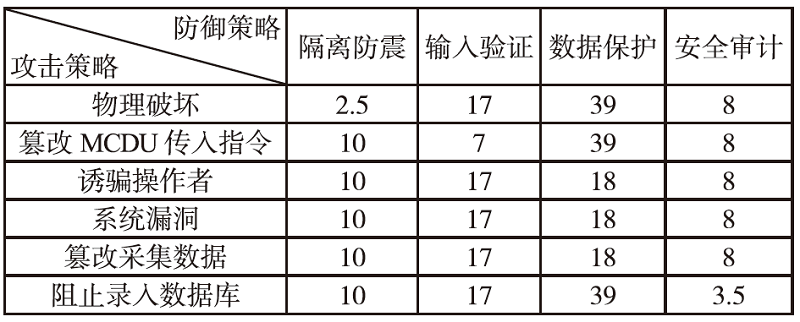
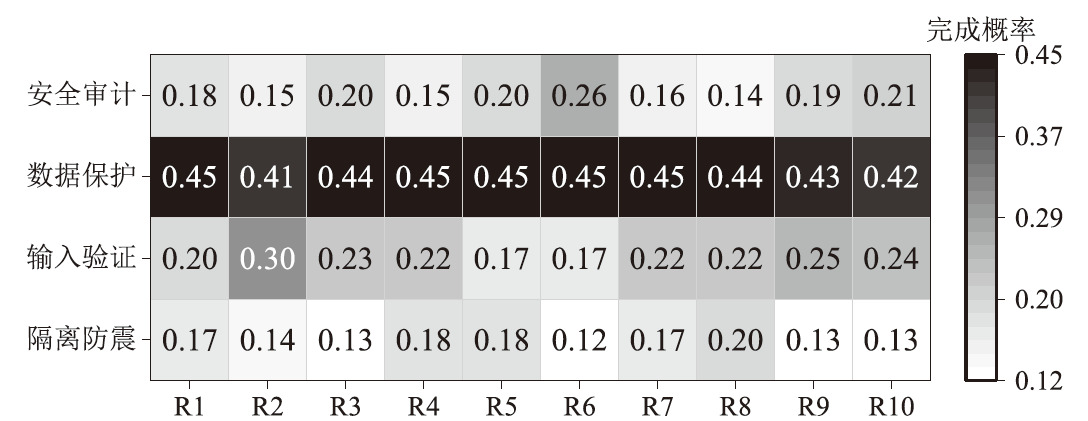
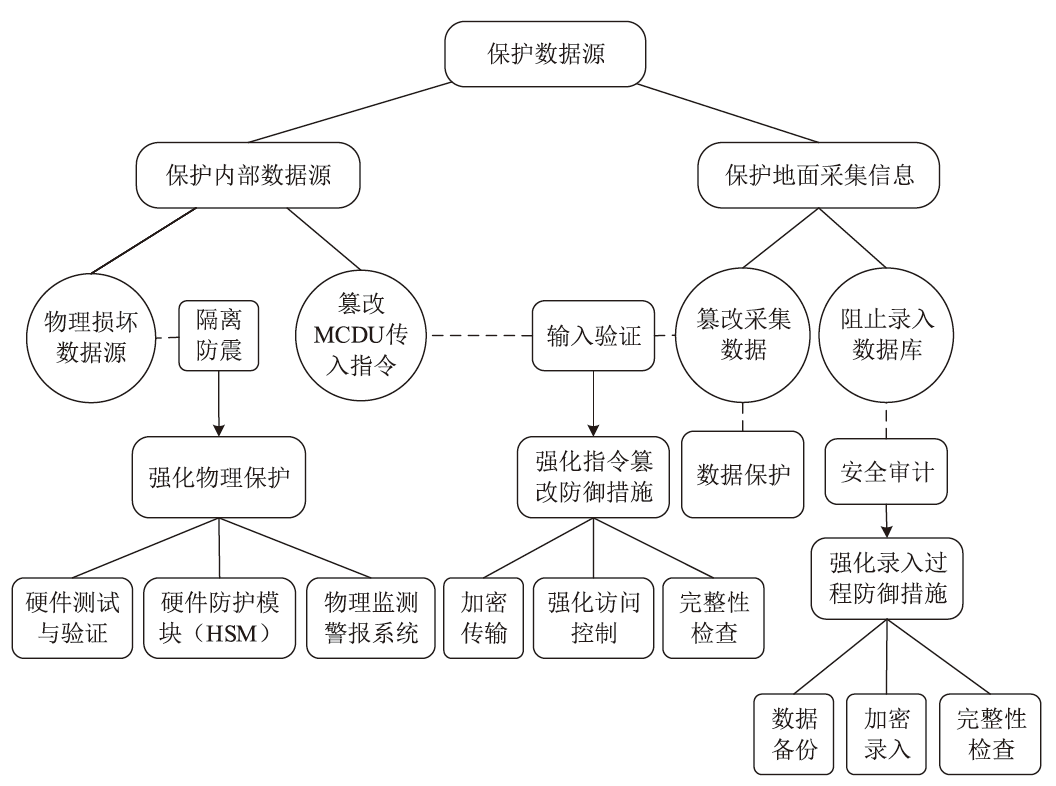
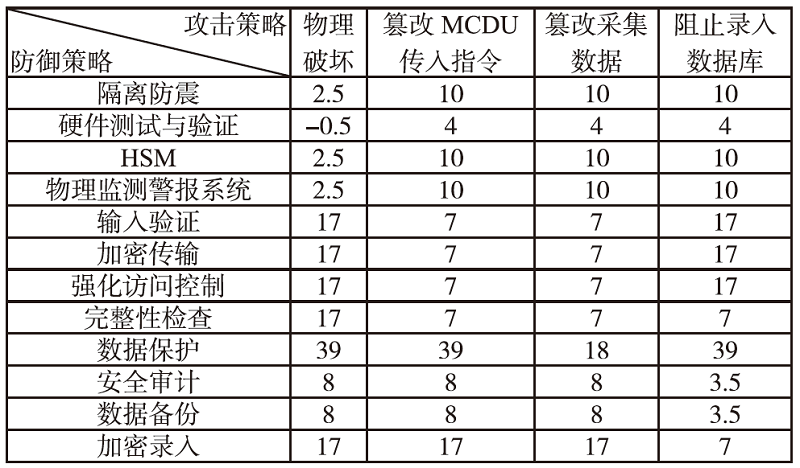
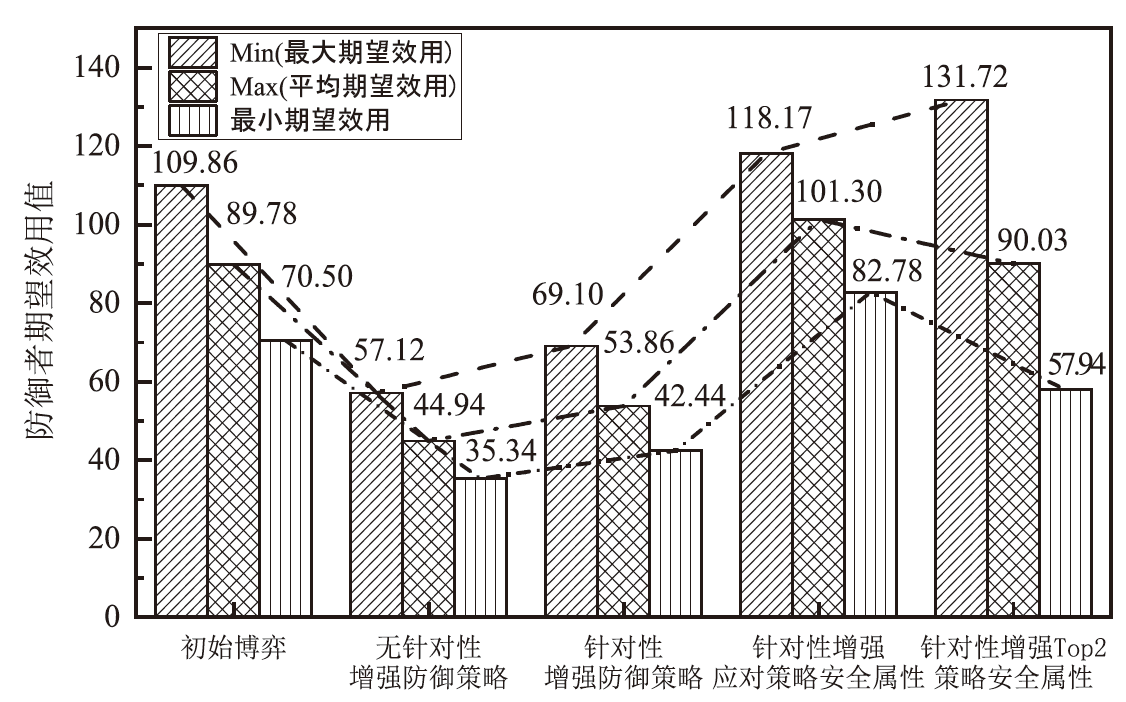
电子飞行仪表系统(Electronic Flight Instrument System,EFIS)具有高安全性要求,其运行环境极端,可供分配的防御策略资源严重受限,缺乏合理性的防御策略部署会影响系统整体安全。文章从攻防决策视角转换和非合作博弈理论出发,在融合安全视角下提出一种伴随EFIS周期性检修的有限防御策略部署优化模型。首先通过建立双属性的攻击防御树(Attack Defense Tree,ADT)构建攻防策略空间;然后运用决策视角转换思想,从攻击者的角度进行非合作博弈分析,揭示攻击者意图降低系统安全性的攻击策略分配;最后基于攻击者博弈结果对防御策略进行博弈分析,并通过验证提高防御者策略安全属性的可行性,为安全资源分配提供可靠的理论基础。该模型基于蒙特卡洛模拟成功求解了非合作博弈下的防御策略部署问题,得到期望效用最大化时的防御策略优化部署方案,避免了防御措施的冗余添加,同时有效提高了系统整体的安全性。
中图分类号:
引用本文
顾兆军, 张一诺, 扬雪影, 隋翯. EFIS数据源防御部署优化的非合作博弈模型[J]. 信息网络安全, 2024, 24(4): 614-625.
GU Zhaojun, ZHANG Yinuo, YANG Xueying, SUI He. A Non-Cooperative Game Model for Optimizing EFIS Data Source Defense Deployment[J]. Netinfo Security, 2024, 24(4): 614-625.
| [1] | BARON C, LOUIS V. Towards a Continuous Certification of Safety-Critical Avionics Software[EB/OL]. (2021-01-03)[2023-12-22]. https://www.sciencedirect.com/science/article/pii/S0166361520306163. |
| [2] | VILLEGAS J, FORTES S, ESCAÑO V, et al. Verification and Validation Framework for AFDX Avionics Networks[J]. IEEE Access, 2022, 10: 66743-66756. |
| [3] | SUTHAPUTCHAKUN C, SUN Zhili, KAVADIAS C, et al. Performance Analysis of AFDX Switch for Space Onboard Data Networks[J]. IEEE Transactions on Aerospace and Electronic Systems, 2016, 52(4): 1714-1727. |
| [4] | MATTI E, JOHNS O, KHAN S, et al. Aviation Scenarios for 5G and Beyond[C]// IEEE. In 2020 AIAA/IEEE 39th Digital Avionics Systems Conference(DASC). New York: IEEE, 2020: 1-10. |
| [5] |
ZHAO Changxiao, WANG Kenian, ZHANG Wei, et al. Integrated Analysis Method of Functional Safety and Cyber Security of Avionics System for Civil Aircraft[J]. China Safety Science Journal, 2022, 32(9): 49-56.
doi: 10.16265/j.cnki.issn1003-3033.2022.09.2126 |
| 赵长啸, 汪克念, 张伟, 等. 民机航电系统功能安全-信息安全一体化分析方法[J]. 中国安全科学学报, 2022, 32(32):49-56. | |
| [6] | ZIMMER L, YVARS P A, LAFAYE M. Models of Requirements for Avionics Architecture Synthesis: Safety, Capacity and Security[EB/OL]. (2020-12-01)[2023-12-22]. https://hal.science/hal-03957544/. |
| [7] | ATHAVALE J, MARIANI R, PAULITSCH M. Flight Safety Certification Implications for Complex Multi-Core Processor Based Avionics Systems[C]// IEEE. In 2019 IEEE International Reliability Physics Symposium(IRPS). New York: IEEE, 2019: 1-6. |
| [8] | SMITH M, STROHMEIER M, HARMAN J, et al. Safety vs. Security: Attacking Avionic Systems with Humans in the Loop[EB/OL]. (2019-05-20)[2023-12-22]. https://www.researchgate.net/publication/333233094_Safety_vs_Security_Attacking_Avionic_Systems_with_Humans_in_the_Loop. |
| [9] | BEEK M H T, LEGAY A, LAFUENTE AL, et al. Quantitative Security Risk Modeling and Analysis with RisQFLan[EB/OL]. (2021-10-01)[2023-12-22]. https://doi.org/10.1016/j.cose.2021.102381. |
| [10] | JHAWAR R, MAUW S, ZAKIUDDIN I. Automating Cyber Defence Responses Using Attack-Defence Trees and Game Theory[EB/OL]. (2016-01-01)[2023-12-22]. https://research.utwente.nl/en/publications/automating-cyber-defence-responses-using-attack-defence-trees-and. |
| [11] | HUANG Bo, QIN Yuhai, LIU Yang, et al. Research of Vulnerability Assessment and Risk ProbabilityBase on General Attack Tree[J]. Netinfo Security, 2022, 22(10): 39-44. |
| 黄波, 秦玉海, 刘旸, 等. 基于通用攻击树的脆弱性评估与风险概率研究[J]. 信息网络安全, 2022, 22(10):39-44. | |
| [12] | CHEHIDA S, BAOUYA A, BOZGA M, et al. Exploration of Impactful Countermeasures on IoT Attacks[C]// IEEE. 9th Mediterranean Conference on Embedded Computing(MECO). New York: IEEE, 2020: 1-4. |
| [13] | ARIAS J, BUDDE C E, PENCZEK W, et al. Hackers vs. Security: Attack-Defence Trees as Asynchronous Multi-Agent Systems[C]// Springer. In International Conference on Formal Engineering Methods. Heidelberg: Springer, 2020: 3-19 |
| [14] | RIOS E, REGO A, ITURBE E, et al. Continuous Quantitative Risk Management in Smart Grids Using Attack Defense Trees[EB/OL]. (2020-08-07)[2023-12-22]. https://www.mdpi.com/1424-8220/20/16/4404. |
| [15] | PETRUCCI L, KNAPIK M, PENCZEK W, et al. Squeezing State Spaces of (Attack-Defence) Trees[C]// IEEE. 24th International Conference on Engineering of Complex Computer Systems(ICECCS). New York: IEEE, 2019: 71-80. |
| [16] | LIU Guiyun, PENG Baihao, ZHONG Xiaojing. Epidemic Analysis of Wireless Rechargeable Sensor Networks Based on an Attack-Defense Game Model[EB/OL]. (2021-01-15)[2023-12-22]. https://www.mdpi.com/1424-8220/21/2/594. |
| [17] | LIU Guiyun, PENG Baihao, ZHONG Xiaojing, et al. Attack-Defense Game between Malicious Programs and Energy-Harvesting Wireless Sensor Networks Based on Epidemic Modeling[J]. Complexity, 2020(1): 1-9. |
| [18] | ZHOU Haiping, SHEN Shigen, LIU Jianhua. Malware Propagation Model in Wireless Sensor Networks under Attack-Defense Confrontation[J]. Computer Communications, 2020, 162: 51-58. |
| [19] | WU Yingfu, KANG Bingyi, WU Hao. Strategies of Attack-Defense Game for Wireless Sensor Networks Considering the Effect of Confidence Level in Fuzzy Environment[EB/OL]. (2021-04-12)[2023-12-22]. https://www.sciencedirect.com/science/article/pii/S0952197621000853. |
| [20] | ZHANG Zhimei, HUANG Shaowei, CHEN Ying, et al. Cyber-Physical Coordinated Risk Mitigation in Smart Grids Based on Attack-Defense Game[J]. IEEE Transactions on Power Systems, 2021, 37(1): 530-542. |
| [21] | PENG Rui, WU Di, SUN Mengyao, et al. An Attack-Defense Game on Interdependent Networks[J]. Journal of the Operational Research Society, 2021, 72(10): 2331-2341. |
| [1] | 张浩, 谢大智, 胡云晟, 叶骏威. 基于半监督学习的网络异常检测研究综述[J]. 信息网络安全, 2024, 24(4): 491-508. |
| [2] | 王健, 陈琳, 王凯崙, 刘吉强. 基于时空图神经网络的应用层DDoS攻击检测方法[J]. 信息网络安全, 2024, 24(4): 509-519. |
| [3] | 屠晓涵, 张传浩, 刘孟然. 恶意流量检测模型设计与实现[J]. 信息网络安全, 2024, 24(4): 520-533. |
| [4] | 刘斯诺, 阮树骅, 陈兴蜀, 郑涛. 基于eBPF的云上威胁观测系统[J]. 信息网络安全, 2024, 24(4): 534-544. |
| [5] | 张光华, 刘亦纯, 王鹤, 胡勃宁. 基于JSMA对抗攻击的去除深度神经网络后门防御方案[J]. 信息网络安全, 2024, 24(4): 545-554. |
| [6] | 张雪锋, 陈婷婷, 苗美霞, 程叶霞. 基于SM9的多接收者混沌密钥生成方案[J]. 信息网络安全, 2024, 24(4): 555-563. |
| [7] | 张艳硕, 袁煜淇, 李丽秋, 杨亚涛, 秦晓宏. 基于SM2的周期性可否认环签名方案[J]. 信息网络安全, 2024, 24(4): 564-573. |
| [8] | 孙隽丰, 李成海, 宋亚飞. ACCQPSO:一种改进的量子粒子群优化算法及其应用[J]. 信息网络安全, 2024, 24(4): 574-586. |
| [9] | 石润华, 杨婧怡, 王鹏博, 刘华伟. V2G中基于区块链的在线/离线跨域身份认证方案[J]. 信息网络安全, 2024, 24(4): 587-601. |
| [10] | 尹春勇, 贾续康. 基于策略图的三维位置隐私发布算法研究[J]. 信息网络安全, 2024, 24(4): 602-613. |
| [11] | 胡海洋, 刘畅, 王栋, 魏旭. 基于区块链的清洁能源数据溯源机制[J]. 信息网络安全, 2024, 24(4): 626-639. |
| [12] | 徐子荣, 郭焱平, 闫巧. 基于特征恶意度排序的恶意软件对抗防御模型[J]. 信息网络安全, 2024, 24(4): 640-649. |
| [13] | 薛茗竹, 胡亮, 王明, 王峰. 基于联邦学习和区块链技术的TAP规则处理系统[J]. 信息网络安全, 2024, 24(3): 473-485. |
| [14] | 张强, 何俊江, 李汶珊, 李涛. 基于深度度量学习的异常流量检测方法[J]. 信息网络安全, 2024, 24(3): 462-472. |
| [15] | 傅彦铭, 陆盛林, 陈嘉元, 覃华. 基于深度强化学习和隐私保护的群智感知动态任务分配策略[J]. 信息网络安全, 2024, 24(3): 449-461. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||