信息网络安全 ›› 2024, Vol. 24 ›› Issue (4): 520-533.doi: 10.3969/j.issn.1671-1122.2024.04.003
恶意流量检测模型设计与实现
- 1.郑州警察学院网络安全与智慧警务学院,郑州 450053
2.北京铁路公安局天津公安处,天津 300100
-
收稿日期:2023-12-07出版日期:2024-04-10发布日期:2024-05-16 -
通讯作者:张传浩zhangchuanhao@rpc.edu.cn -
作者简介:屠晓涵(1991—),女,河南,讲师,博士,CCF会员,主要研究方向为人工智能和网络安全|张传浩(1979—),男,河南,副教授,博士,CCF会员,主要研究方向为网络信息安全和智慧警务|刘孟然(2001—),男,天津,本科,主要研究方向为网络安全 -
基金资助:中央高校基本科研业务费(2022TJJBKY002);中央高校基本科研业务费(2023TJJBKY012);中央高校基本科研业务费(2022TJJBKY009);河南省重点研发与推广专项(222102210302);河南省重点研发与推广专项(232102210022);河南省高等学校重点科研项目(23A520042)
Design and Implementation of Malicious Traffic Detection Model
TU Xiaohan1, ZHANG Chuanhao1( ), LIU Mengran2
), LIU Mengran2
- 1. Department of Cybersecurity and Smart Police, Zhengzhou Police University, Zhengzhou 450053, China
2. Tianjin Public Security Division, Beijing Railway Public Security Bureau, Tianjin 300100, China
-
Received:2023-12-07Online:2024-04-10Published:2024-05-16
摘要:
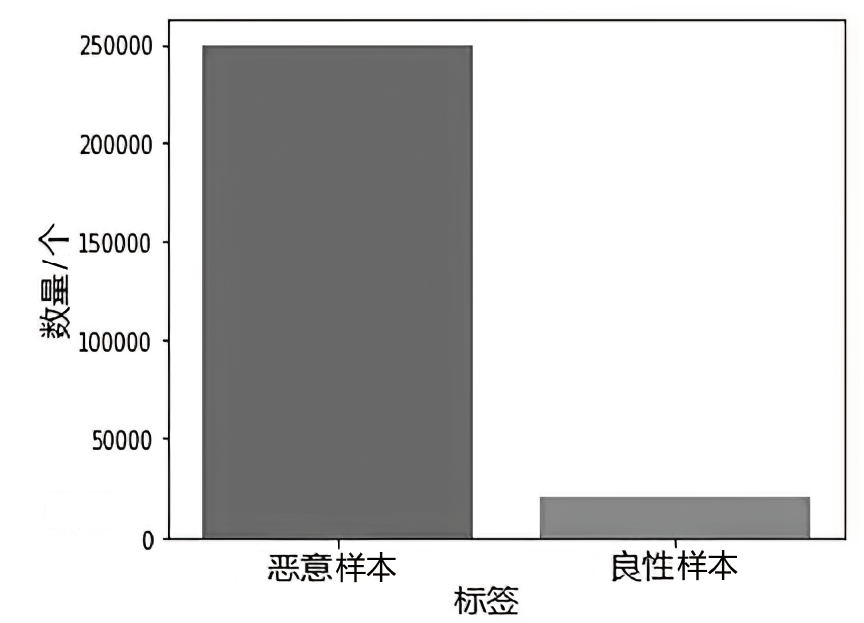
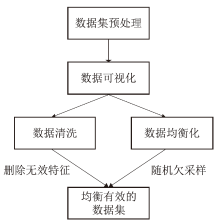
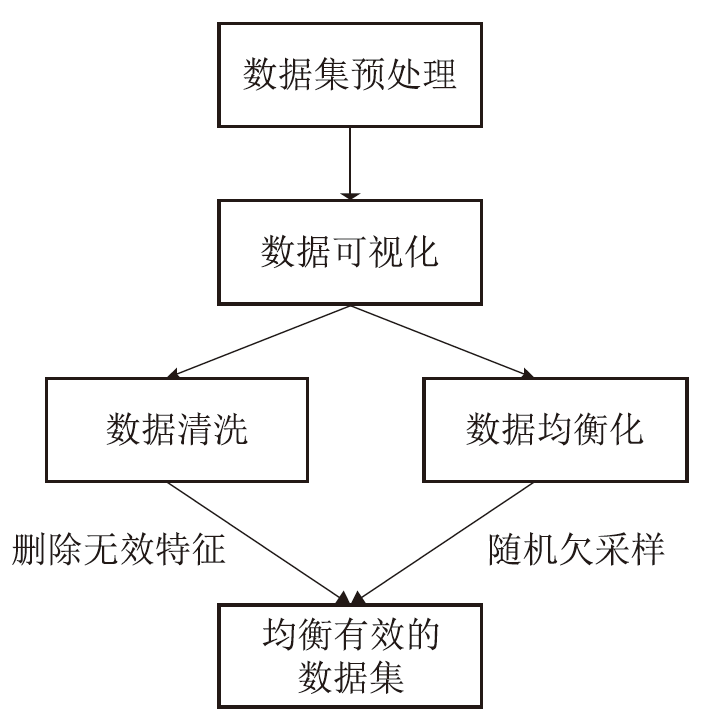
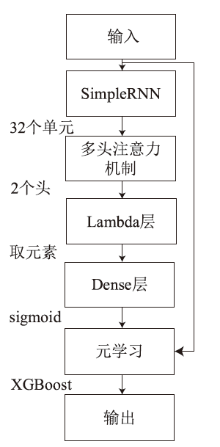
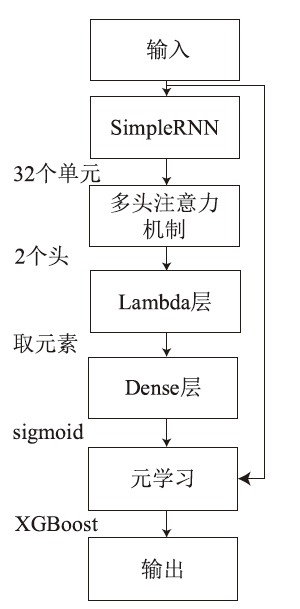
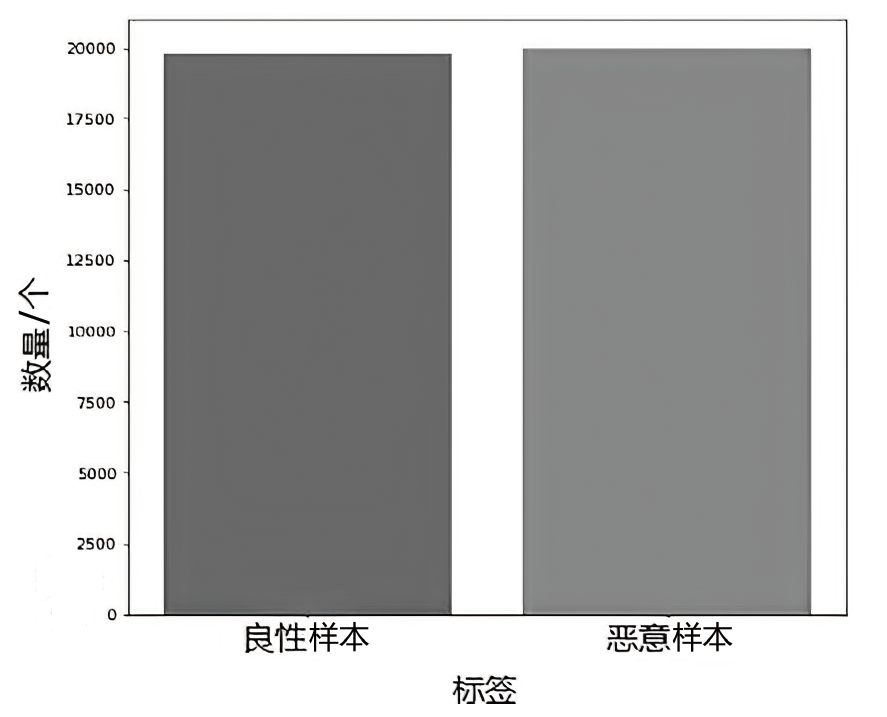
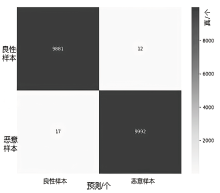
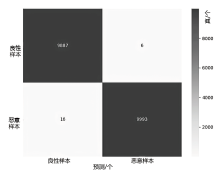
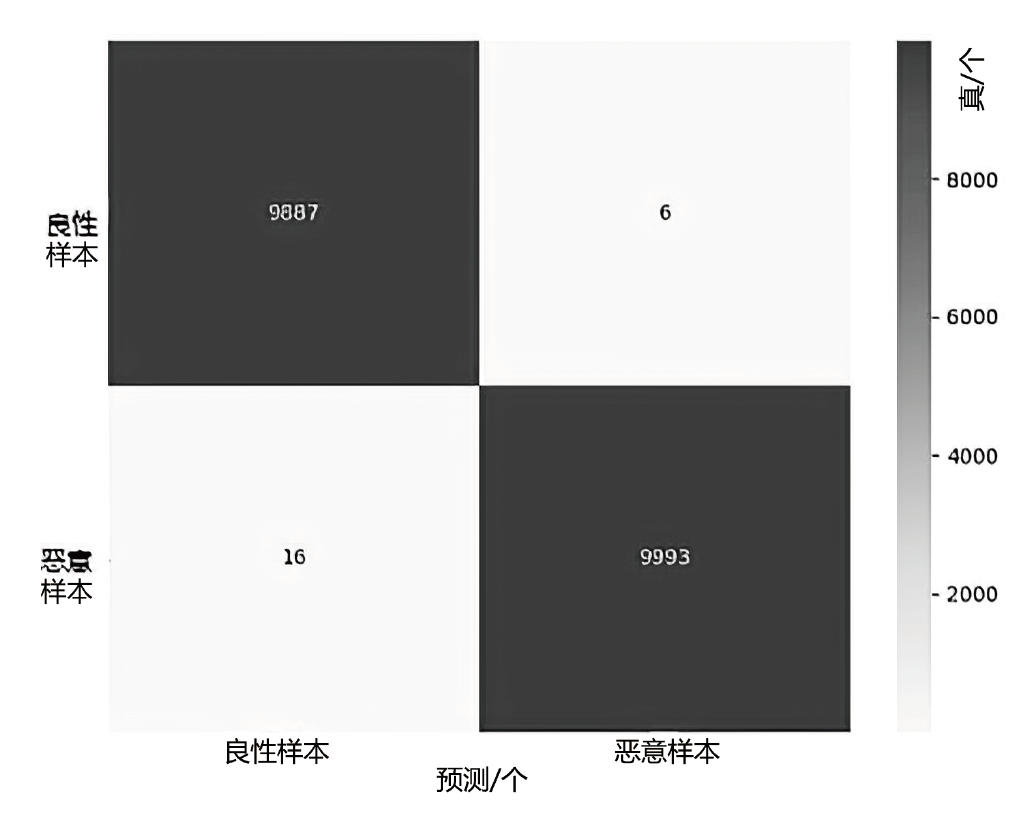
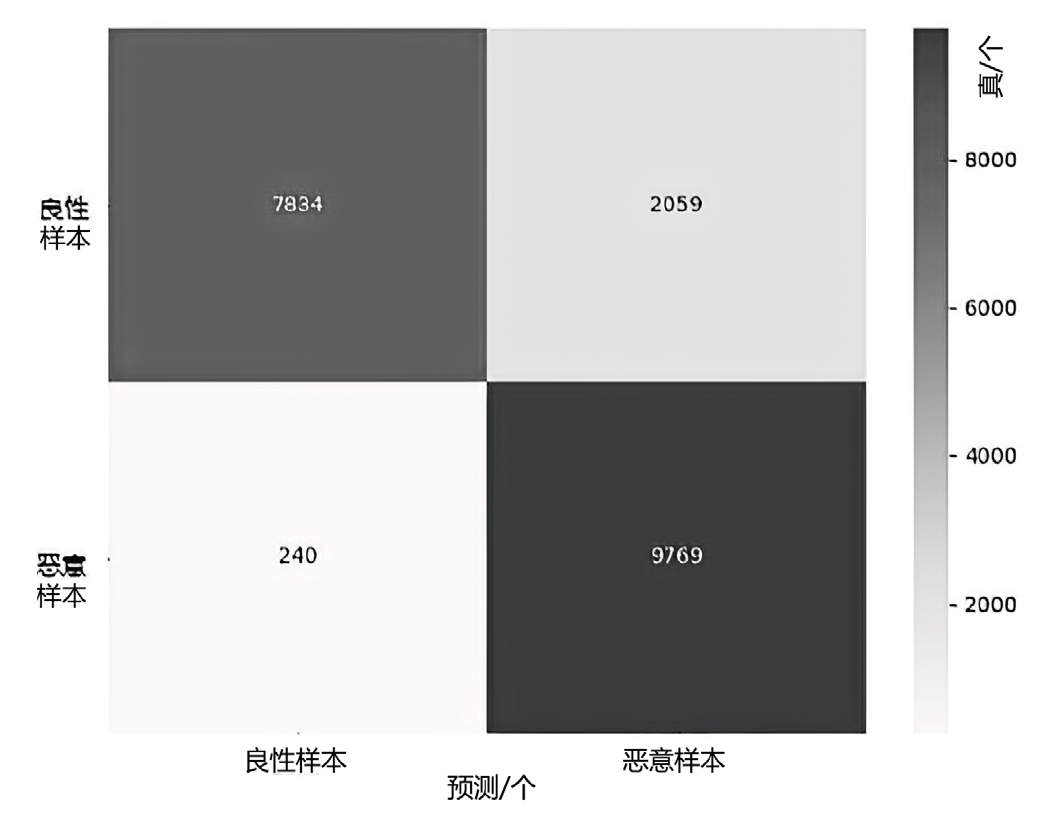
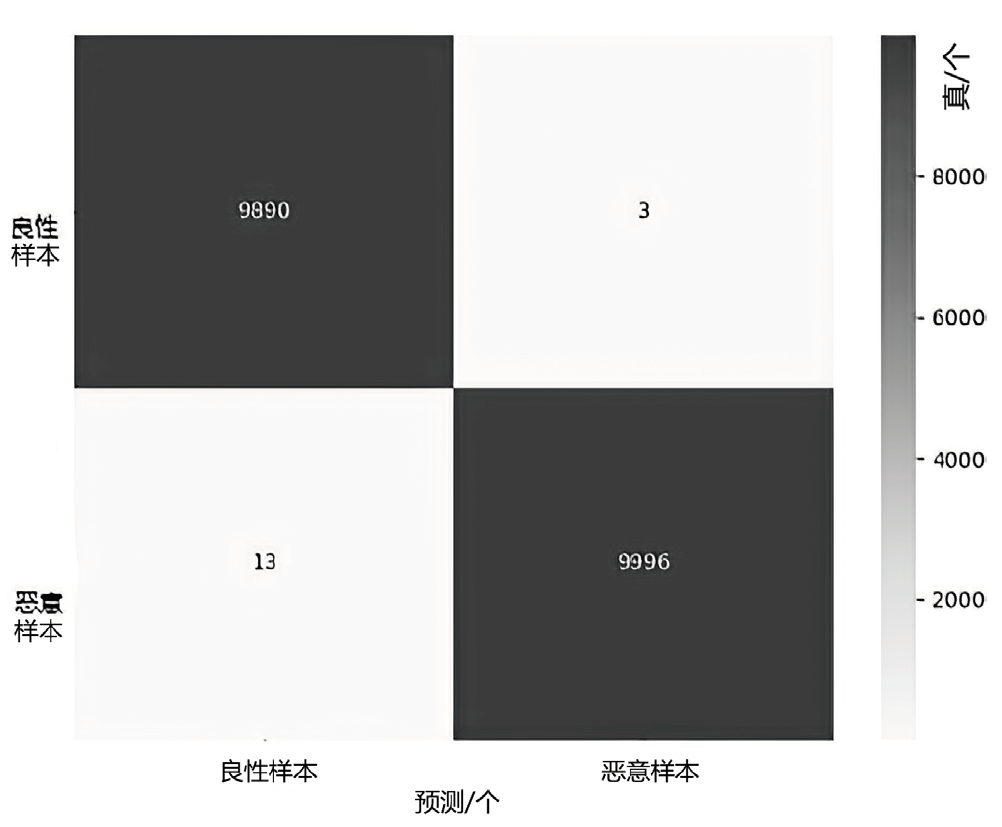
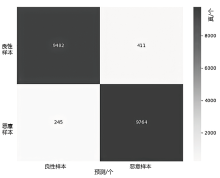
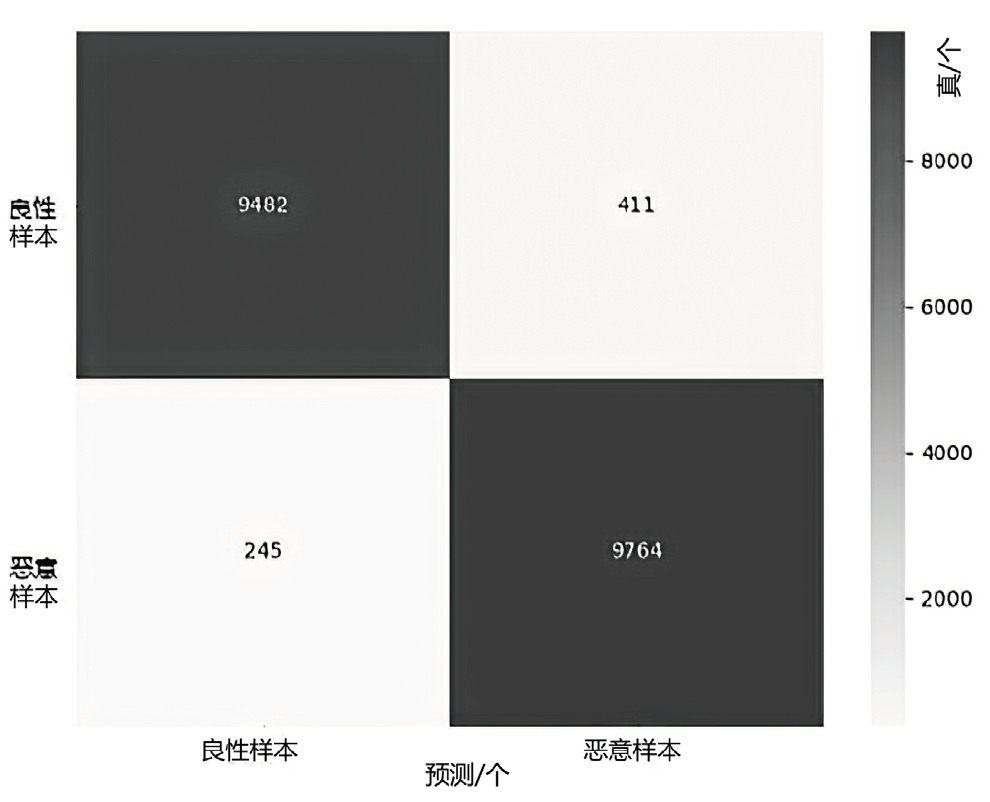
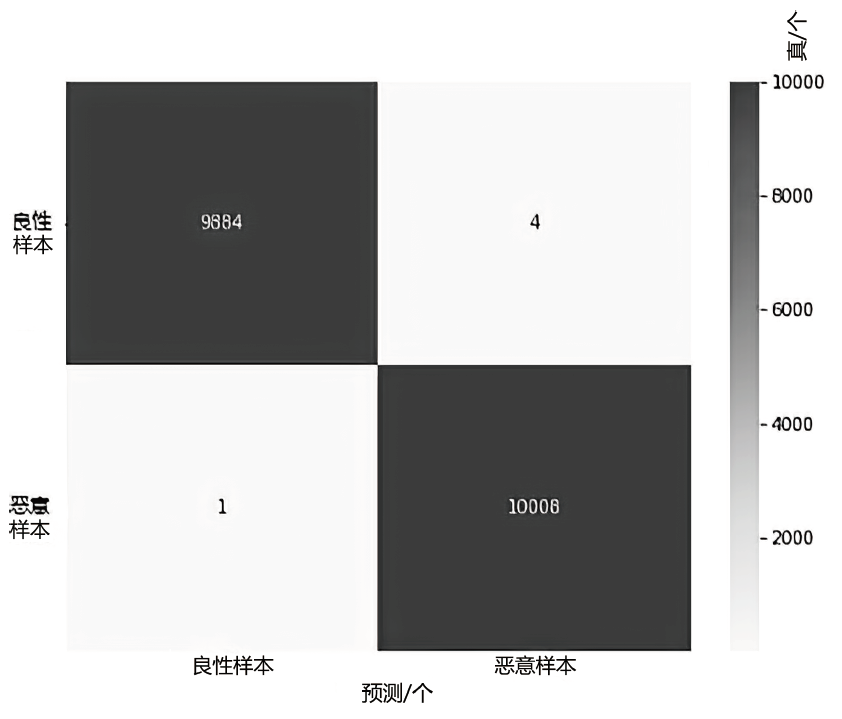
随着网络攻击手段的日益精进和多样化,传统安全防护面临准确识别恶意流量困难的挑战。文章针对恶意流量检测中常见的无效特征众多、数据不平衡以及攻击手段复杂化等问题,开发了一种较高效的检测方法。首先,文章提出一种数据清洗和均衡化方法,能够提升流量特征数据的质量和有效性;然后,文章结合简单循环神经网络(Recurrent Neural Network,RNN)与多头注意力机制,使检测模型能够更精确处理序列数据,有效捕捉和识别各类信息及其依赖关系,大幅提升特征提取的准确度;最后,文章利用集成学习、深度学习和机器学习的优势,使检测模型能够在有限的样本上高效学习,并快速适应不同的网络特征。实验结果表明,该方法在多个公共数据集上展现了较好的检测性能。
中图分类号:
引用本文
屠晓涵, 张传浩, 刘孟然. 恶意流量检测模型设计与实现[J]. 信息网络安全, 2024, 24(4): 520-533.
TU Xiaohan, ZHANG Chuanhao, LIU Mengran. Design and Implementation of Malicious Traffic Detection Model[J]. Netinfo Security, 2024, 24(4): 520-533.
| [1] | MONTAZERISHATOORI M, DAVIDSON L, KAUR G, et al. Detection of DoH Tunnels Using Time-Series Classification of Encrypted Traffic[C]// IEEE. 2020 IEEE Intl Conf on Dependable, Autonomic and Secure Computing, Intl Conf on Pervasive Intelligence and Computing, Intl Conf on Cloud and Big Data Computing, Intl Conf on Cyber Science and Technology Congress (DASC/PiCom/CBDCom/CyberSciTech). NewYork: IEEE, 2020: 63-70. |
| [2] | MITSUHASHI R, JIN Yong, IIDA K, et al. Malicious DNS Tunnel Tool Recognition Using Persistent DoH Traffic Analysis[J]. IEEE Transactions on Network and Service Management, 2022, 20(2): 2086-2095. |
| [3] | TU Xiaohan, XU Cheng, LIU Siping, et al. Efficient Monocular Depth Estimation for Edge Devices in Internet of Things[J]. IEEE Transactions on Industrial Informatics, 2021, 17(4): 2821-2832. |
| [4] | LIN Kunda, XU Xiaolong, XIAO Fu. MFFusion: A Multi-Level Features Fusion Model for Malicious Traffic Detection Based on Deep Learning[J]. Computer Networks, 2022, 202: 108658-108667. |
| [5] | HONG Yueping, LI Qi, YANG Yanqing, et al. Graph Based Encrypted Malicious Traffic Detection with Hybrid Analysis of Multi-View Features[J]. Information Sciences, 2023, 185: 119229-119236. |
| [6] | TU Xiaohan, ZHANG Chuanhao, LIU Siping, et al. Point Cloud Segmentation of Overhead Contact Systems with Deep Learning in High-Speed Rails[J]. Journal of Network and Computer Applications, 2023, 23: 103671-103688. |
| [7] | ZHANG Pei, HE Fangzhou, ZHANG Han, et al. Real-Time Malicious Traffic Detection with Online Isolation Forest over SD-WAN[J]. IEEE Transactions on Information Forensics and Security, 2023, 18: 2076-2090. |
| [8] | KISHOR K, SINGH P, VASHISHTA R. Develop Model for Malicious Traffic Detection Using Deep Learning[J]. Micro-Electronics and Telecommunication Engineering: Proceedings of 6th ICMETE 2022. Singapore: Springer Nature Singapore, 2023: 83-91. |
| [9] | SHIN D H, AN K K, CHOI S C, et al. Malicious Traffic Detection Using K-Means[J]. The Journal of Korean Institute of Communications and Information Sciences, 2016, 41(2): 277-284. |
| [10] | NAEEM H, CHENG Xiaochun, ULLAH F, et al. A Deep Convolutional Neural Network Stacked Ensemble for Malware Threat Classification in Internet of Things[EB/OL]. (2022-07-18)[2023-11-25]. https://www.worldscientific.com/doi/10.1142/S0218126622503029. |
| [11] | NAEEM H, DONG Shi, FALANA O J, et al. DEVELOPMENT of a Deep Stacked Ensemble with Process Based Volatile Memory Forensics for Platform Independent Malware Detection and Classification[EB/OL]. (2023-08-18)[2023-11-25]. https://www.nstl.gov.cn/paper_detail.html?id=d829128c2b7c4b8caca5389d2553aba7. |
| [12] | SHU Longhui, DONG Shi, SU Huadong, et al. Android Malware Detection Methods Based on Convolutional Neural Network: A Survey[J]. IEEE Transactions on Emerging Topics in Computational Intelligence, 2023, 7(5): 1330-1350. |
| [13] |
LUO Yantian, SUN Hancun, CHEN Xu, et al. Detecting While Accessing: A Semi-Supervised Learning-Based Approach for Malicious Traffic Detection in Internet of Things[J]. China Communications, 2023, 20(4): 302-314.
doi: 10.23919/JCC.fa.2022-0783.202304 |
| [14] | LU Gang, GUO Ronghua, ZHOU Ying, et al. Review of Malicious Traffic Feature Extraction[J]. Netinfo Security, 2018, 18(9): 9-22. |
| 鲁刚, 郭荣华, 周颖, 等. 恶意流量特征提取综述[J]. 信息网络安全, 2018, 18(9): 9-22. | |
| [15] | ZOU Futai, YU Tangda, XU Wenliang. Encrypted Malicious Traffic Detection Based on Hidden Markov Mode[J]. Journal of Software, 2022, 33(7): 2683-2698. |
| 邹福泰, 俞汤达, 许文亮. 基于隐马尔可夫模型的加密恶意流量检测[J]. 软件学报, 2022, 33(7): 2683-2698. | |
| [16] |
LI Daoquan, LU Xiaofu, YANG Qianqian. Malicious Traffic Detection Method Based on Siamese Neural Network[J]. Computer Engineering and Applications, 2022, 58(14): 89-95.
doi: 10.3778/j.issn.1002-8331.2104-0159 |
|
李道全, 鲁晓夫, 杨乾乾. 基于孪生神经网络的恶意流量检测方法[J]. 计算机工程与应用, 2022, 58(14): 89-95.
doi: 10.3778/j.issn.1002-8331.2104-0159 |
|
| [17] | LI Hongwu, FU Xingyu, ZHU Yujia, et al. MetaIoT: Few Shot Malicious Traffic Detection in Internet of Things Networks Based on HIN[C]// IEEE. 2023 IFIP Networking Conference (IFIP Networking). New York: IEEE, 2023: 1-9. |
| [18] | HONG Jiarong, DING Mingfeng. A New Algorithm of Decision Tree Induction[J]. Chinese Journal of Computers, 1995, 18(6): 470-474. |
| 洪家荣, 丁明峰. 一种新的决策树归纳学习算法[J]. 计算机学报, 1995, 18(6): 470-474. | |
| [19] | HOU Jian, LU Hui, LIU Fangai, et al. Detection and Countermeasure of Encrypted Malicious Traffic: A Survey[J]. Journal of Software, 2024, 35(1): 333-355. |
| 侯剑, 鲁辉, 刘方爱, 等. 加密恶意流量检测及对抗综述[J]. 软件学报, 2024, 35(1): 333-355. | |
| [20] | ZHOU Chang. Research on Mining Algorithm for Web Threat Intelligence Based on Deep Learning[D]. Shanghai: Shanghai Jiao Tong University, 2018. |
| 周畅. 基于深度学习的Web威胁情报挖掘算法研究[D]. 上海: 上海交通大学, 2018. | |
| [21] | LI Zeyi, WANG Pan. Unsupervised Network Abnormal Traffie Detection Method Based on Improved KNN[J]. Journal of Nanjing University of Posts and Telecommunications (Natural Science Edition), 2022, 42(2): 560-568. |
| 李泽一, 王攀. 基于代价敏感度的改进型K近邻异常流量检测算法[J]. 南京邮电大学学报(自然科学版), 2022, 42(2): 560-568. | |
| [22] | BAO Wenbo, SHA Letian, CAO Xiaomei. Malicious Encrypted Traffic Identification Based on Feature Fusion[J]. Computer Systems and Applications, 2023, 32(1): 358-367. |
| 包文博, 沙乐天, 曹晓梅. 基于特征融合的恶意加密流量识别[J]. 计算机系统应用, 2023, 32(1): 358-367. | |
| [23] | GAO Yuanchen, XU Guosheng. Research on Network Malicious Traffic Detection Technology Based on Ensemble Learning Strategy[J]. Journal of Information Security Research, 2023, 9(8): 730-738. |
| 高源辰, 徐国胜. 基于集成学习策略的网络恶意流量检测技术研究[J]. 信息安全研究, 2023, 9(8): 730-738. | |
| [24] | TU Xiaohan, XU Cheng, LIU Siping, et al. Learning Depth for Scene Reconstruction Using an Encoder-Decoder Model[J]. IEEE Access, 2020, 99: 1-11. |
| [25] | FATIMA R A, ABID M. A Review of Recent Advances, Challenges, and Opportunities in Malicious Insider Threat Detection Using Machine Learning Methods[J]. IEEE Access, 2024, 12: 30907-30927. |
| [26] | SHERSTINSKY A. Fundamentals of Recurrent Neural Network (RNN) and Long Short-Term Memory (LSTM) Network[J]. Physica D: Nonlinear Phenomena, 2020, 404(1): 1323-1329. |
| [27] | LIN Zhouhan, FENG Minwei, SANTOS C N, et al. A Structured Self-Attentive Sentence Embedding[EB/OL]. (2017-05-09)[2023-11-15]. https://doi.org/10.48550/arXiv.1703.03130. |
| [28] | LUO Gongzhi, HOU Ruoxian, CHEN Shengyu. Malicious DoH Traffic Warning of Extreme Learning Machine Based on Neighborhood Rough Sets[J]. Nanjing University of Posts and Telecommunications (Natural Science Edition). 2022, 42(6): 79-85. |
| 骆公志, 侯若娴, 陈圣瑜. 基于邻域粗糙集的极限学习机恶意DoH流量预警[J]. 南京邮电大学学报(自然科学版), 2022, 42(6): 79-85. | |
| [29] | CHEN Tianqi, HE Tong, BENESTY M, et al. XGBoost: eXtreme Gradient Boosting[J]. R Package Version, 2015, 1(4): 1-4. |
| [30] | ULLAH I, MAHMOUD Q H. Design and Development of RNN Anomaly Detection Model for IoT Networks[J]. IEEE Access, 2022, 10: 62722-62750. |
| [31] | ANITHA T, AANJANKUMAR S, POONKUNTRAN S, et al. A Novel Methodology for Malicious Traffic Detection in Smart Devices Using Bi-LSTM-CNN-Dependent Deep Learning Methodology[J]. Neural Computing and Applications, 2023, 35(27): 20319-20338. |
| [1] | 江荣, 刘海天, 刘聪. 基于集成学习的无监督网络入侵检测方法[J]. 信息网络安全, 2024, 24(3): 411-426. |
| [2] | 张玉臣, 张雅雯, 吴越, 李程. 基于时频图与改进E-GraphSAGE的网络流量特征提取方法[J]. 信息网络安全, 2023, 23(9): 12-24. |
| [3] | 赵小林, 王琪瑶, 赵斌, 薛静锋. 基于机器学习的匿名流量分类方法研究[J]. 信息网络安全, 2023, 23(5): 1-10. |
| [4] | 邢凌凯, 张健. 基于HPC的虚拟化平台异常检测技术研究与实现[J]. 信息网络安全, 2023, 23(10): 64-69. |
| [5] | 秦一方, 张健, 梁晨. 基于神经网络的电子病历数据特征提取技术研究[J]. 信息网络安全, 2023, 23(10): 70-76. |
| [6] | 赵欣荷, 谢永恒, 万月亮, 汪金苗. 基于多模态数据的博彩网站检测识别模型[J]. 信息网络安全, 2023, 23(10): 77-82. |
| [7] | 范明钰, 李珂. 一种基于RNN区分DDoS攻击类型的方法[J]. 信息网络安全, 2022, 22(7): 1-8. |
| [8] | 王浩洋, 李伟, 彭思维, 秦元庆. 一种基于集成学习的列车控制系统入侵检测方法[J]. 信息网络安全, 2022, 22(5): 46-53. |
| [9] | 曾颖明, 王斌, 郭敏. 基于群体智能的网络安全协同防御技术研究[J]. 信息网络安全, 2020, 20(9): 52-56. |
| [10] | 康健, 王杰, 李正旭, 张光妲. 物联网中一种基于多种特征提取策略的入侵检测模型[J]. 信息网络安全, 2019, 19(9): 21-25. |
| [11] | 马泽文, 刘洋, 徐洪平, 易航. 基于集成学习的DoS攻击流量检测技术[J]. 信息网络安全, 2019, 19(9): 115-119. |
| [12] | 李辉, 倪时策, 肖佳, 赵天忠. 面向互联网在线视频评论的情感分类技术[J]. 信息网络安全, 2019, 19(5): 61-68. |
| [13] | 王旭东, 余翔湛, 张宏莉. 面向未知协议的流量识别技术研究[J]. 信息网络安全, 2019, 19(10): 74-83. |
| [14] | 文伟平, 李经纬, 焦英楠, 李海林. 一种基于随机探测算法和信息聚合的漏洞检测方法[J]. 信息网络安全, 2019, 19(1): 1-7. |
| [15] | 鲁刚, 郭荣华, 周颖, 王军. 恶意流量特征提取综述[J]. 信息网络安全, 2018, 18(9): 1-9. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||