信息网络安全 ›› 2023, Vol. 23 ›› Issue (11): 48-57.doi: 10.3969/j.issn.1671-1122.2023.11.006
一种基于国密算法的音视频选择性加密方案
- 北京电子科技学院,北京 102627
-
收稿日期:2023-06-13出版日期:2023-11-10发布日期:2023-11-10 -
通讯作者:邓烨dyaipai@163.com -
作者简介:许盛伟(1976—),男,江西,教授,博士,CCF会员,主要研究方向为密码应用、大数据安全|邓烨(1999—),男,安徽,硕士研究生,主要研究方向为密码应用|刘昌赫(1999—),男,山东,硕士研究生,主要研究方向为密码算法|谭莉(1999—),女,湖南,硕士研究生,主要研究方向为密钥管理 -
基金资助:国家重点研发计划(2022YFB3104402);中央高校基本科研业务费专项资金(328202221)
A Selective Encryption Scheme for Audio and Video Based on the National Cryptographic Algorithm
XU Shengwei, DENG Ye( ), LIU Changhe, TAN Li
), LIU Changhe, TAN Li
- Beijing Electronic Science and Technology Institute, Beijing 102627, China
-
Received:2023-06-13Online:2023-11-10Published:2023-11-10
摘要:
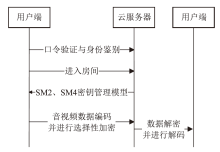
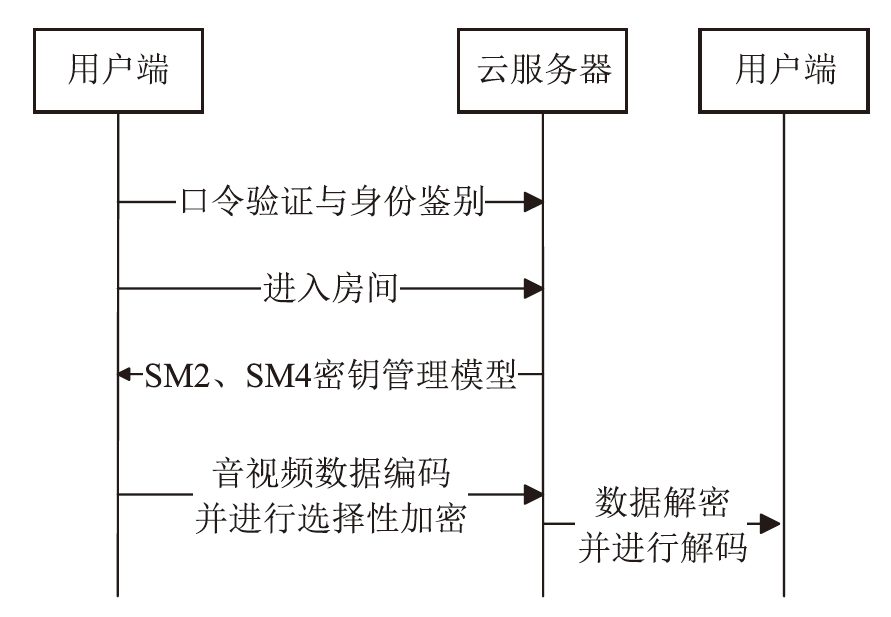
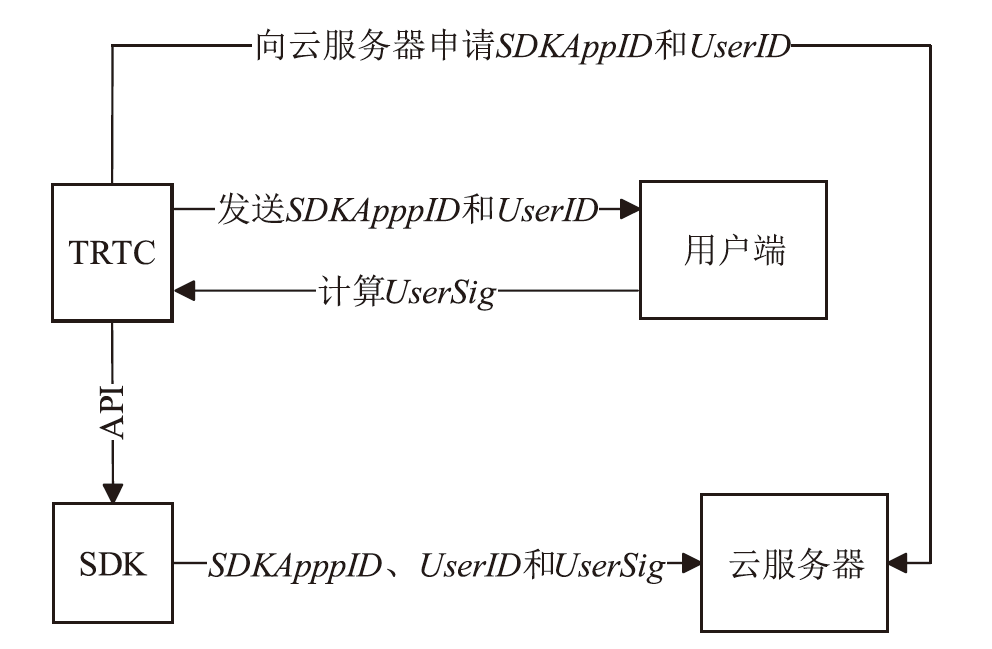
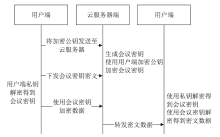
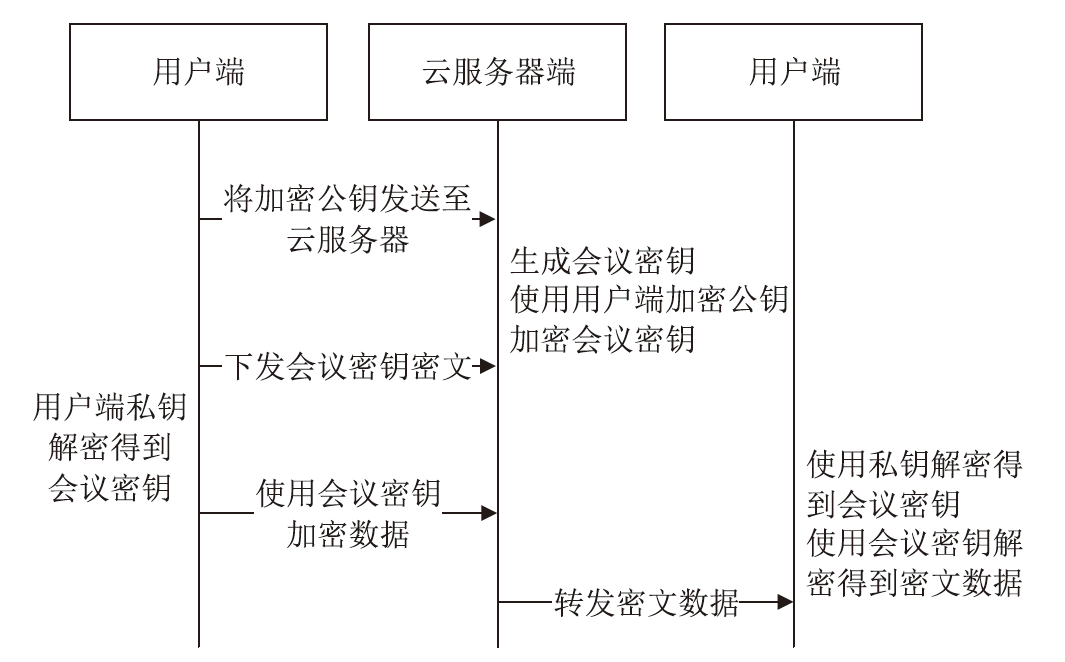
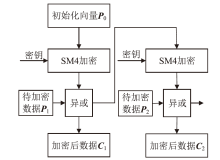
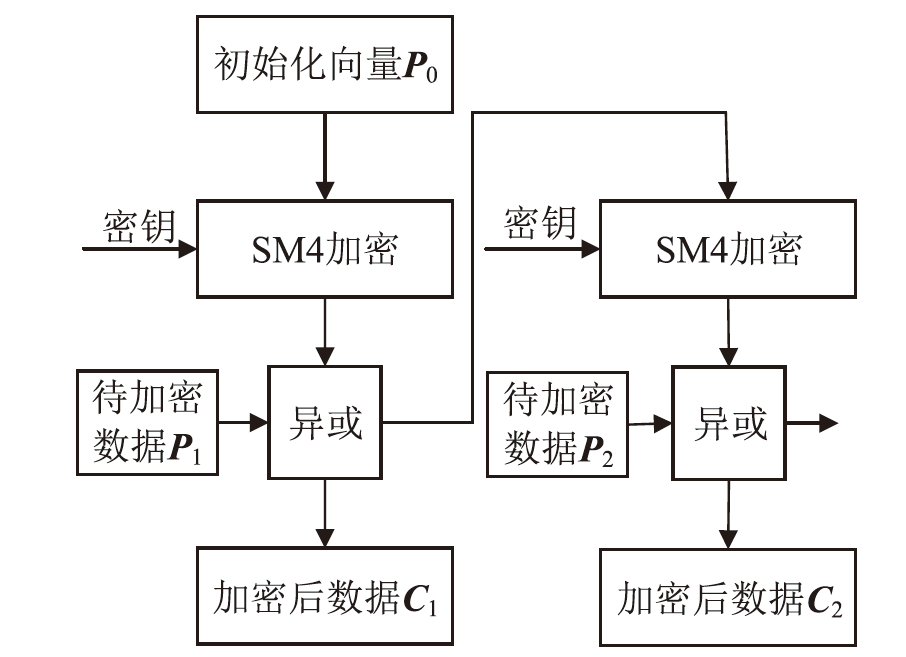
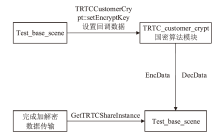
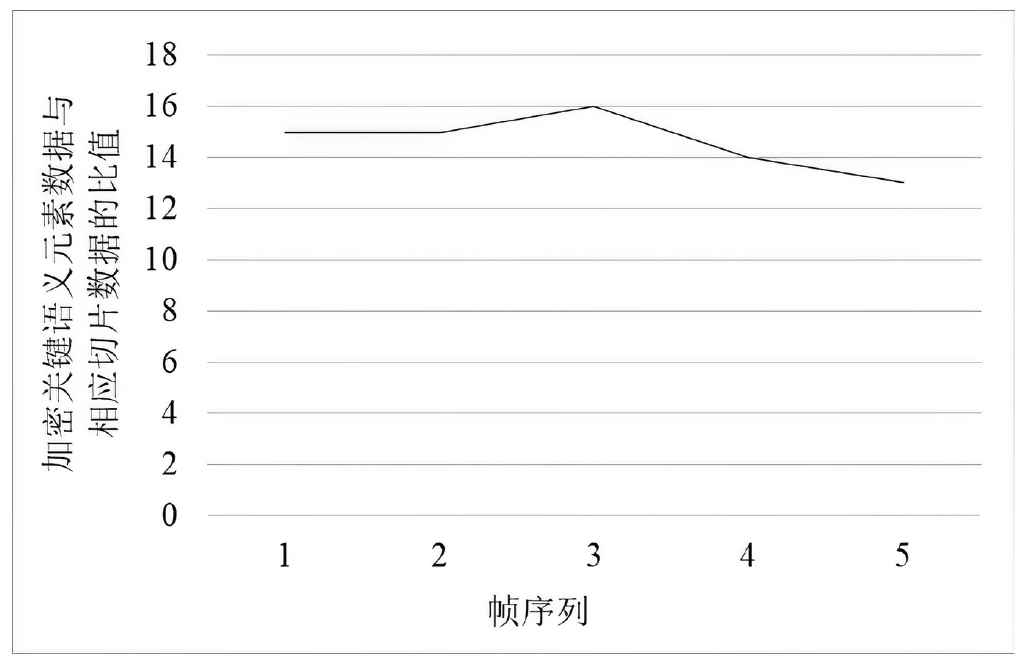
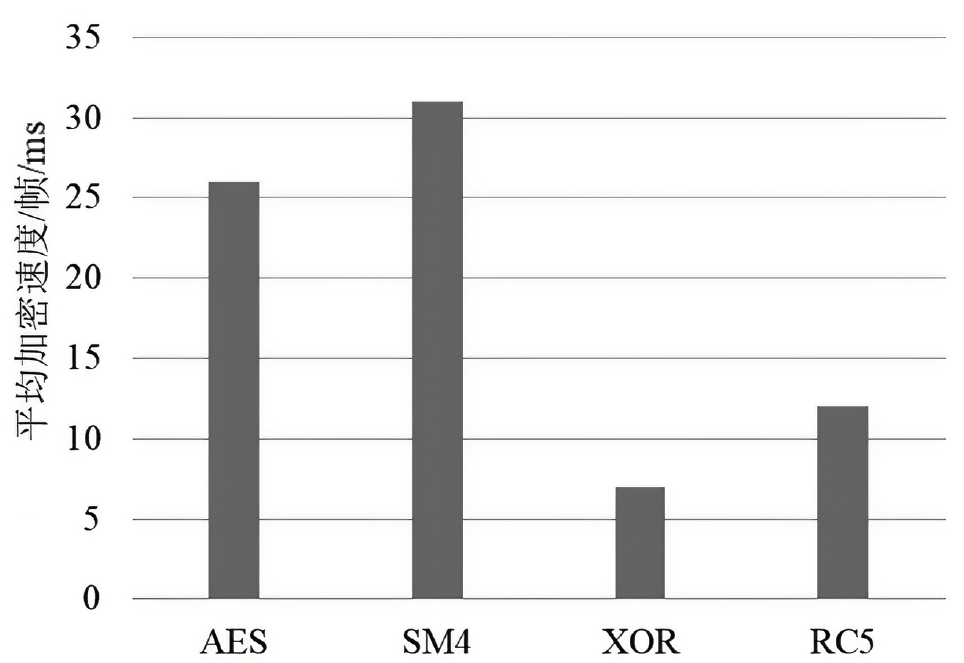
针对目前以国密算法为基础的音视频数据加密方案不完善、加密效率与安全性难以权衡的问题,文章在腾讯实时音视频(Tencent Real-Time Communication,TRTC)架构下设计了一种基于国密算法的音视频选择性加密方案。根据音视频应用的特点与需求提出口令认证与协同签名相结合的身份认证方案,通过分析SM4算法与H.264编码方式的特点,使用SM4-CFB模式对编码后帧内关键语法元素IPM、MVD和RC进行加密,实现了高效的音视频数据选择性加密。实验证明,该方案有效降低了加密数据量,提高了加密速度,并且具有较高的密码安全性和感知安全性。
中图分类号:
引用本文
许盛伟, 邓烨, 刘昌赫, 谭莉. 一种基于国密算法的音视频选择性加密方案[J]. 信息网络安全, 2023, 23(11): 48-57.
XU Shengwei, DENG Ye, LIU Changhe, TAN Li. A Selective Encryption Scheme for Audio and Video Based on the National Cryptographic Algorithm[J]. Netinfo Security, 2023, 23(11): 48-57.
表3
Intra_16×16对应码字
| Mb_type | 类型名称 | 帧内16×16预测模式 | 码字 |
|---|---|---|---|
| 1 | I_16×16_0_0_0 | 0 | 010 |
| 2 | I_16×16_1_0_0 | 1 | 011 |
| 3 | I_16×16_2_0_0 | 2 | 00100 |
| 4 | I_16×16_3_0_0 | 3 | 00101 |
| 5 | I_16×16_0_1_0 | 0 | 00110 |
| 6 | I_16×16_1_1_0 | 1 | 00111 |
| 7 | I_16×16_2_1_0 | 2 | 0001000 |
| 8 | I_16×16_3_1_0 | 3 | 0001001 |
| 9 | I_16×16_0_2_0 | 0 | 0001010 |
| 10 | I_16×16_1_2_0 | 1 | 0001011 |
| 11 | I_16×16_2_2_0 | 2 | 0001100 |
| 12 | I_16×16_3_2_0 | 3 | 0001101 |
| 13 | I_16×16_0_0_1 | 0 | 0001110 |
| 14 | I_16×16_1_0_1 | 1 | 0001111 |
| 15 | I_16×16_2_0_1 | 2 | 000010000 |
| 16 | I_16×16_3_0_1 | 3 | 000010001 |
| 17 | I_16×16_0_1_1 | 0 | 000010010 |
| 18 | I_16×16_1_1_1 | 1 | 000010011 |
| 19 | I_16×16_2_1_1 | 2 | 000010100 |
| 20 | I_16×16_3_1_1 | 3 | 000010101 |
| 21 | I_16×16_0_2_1 | 0 | 000010110 |
| 22 | I_16×16_1_2_1 | 1 | 000010111 |
| 23 | I_16×16_2_2_1 | 2 | 000011000 |
| 24 | I_16×16_3_2_1 | 3 | 000011001 |
| [1] | Shanghai Airui Market Consulting Company Limited. China Real-Time Audio and Video Industry Research Report[EB/OL]. (2022-10-13)[2023-04-23]. https://baijiahao.baidu.com/s?id=1742238707272155025&wfr=spider&for=pc. |
| 上海艾瑞市场咨询股份有限公司. 中国实时音视频行业研究报告[EB/OL]. (2022-10-13)[2023-04-13]. https://baijiahao.baidu.com/s?id=1742238707272155025&wfr=spider&for=pc. | |
| [2] | LIAN Shiguo, SUN Jinsheng, WANG Zhiquan. Video Encryption and Its Development[J]. Information and Control, 2004, 33(5): 560-566. |
| 廉士国, 孙金生, 王执铨. 视频加密算法及其发展现状[J]. 信息与控制, 2004, 33(5):560-566. | |
| [3] | SPANOS G A, MAPLES T B. Performance Study of a Selective Encryption Scheme for the Security of Networked, Real-Time Video[C]// IEEE. International Conference on IEEE Computer Society. New York: IEEE, 1995: 2-10. |
| [4] | QIAO Lintian, NAHRSTEDT K. A New Algorithm for MPEG Video Encryption[C]// Oscillations and Chaos. 1st International Conference on Imaging Science System and Technology. Saint Petersburg: CiteSeer, 1997: 21-29. |
| [5] | YUAN Zhimin, ZHU Chunlei, LYU Chengdu. Selective Video Encryption Algorithm Based on SM4[J]. Communications Technology, 2019, 52(8): 1962-1966. |
| 袁志民, 朱春磊, 吕成都. 基于SM4的选择性视频加密算法[J]. 通信技术, 2019, 52(8):1962-1966. | |
| [6] | ZHANG Shuli, SHI Yuanbing, REN Xubin, et al. Research on Video Conference Encryption Technology[J]. Communications Technology, 2020, 53(10): 2520-2527. |
| 张舒黎, 石元兵, 任旭斌, 等. 视频会议加密技术研究[J]. 通信技术, 2020, 53(10):2520-2527. | |
| [7] | MA Jianping, CHEN Bo, MA Shijia, et al. Adaptive Video Realtime Stream Transmission for Digital Terminals[J]. Journal of Chinese Computer Systems, 2010, 31(6): 1231-1235. |
| 马建平, 陈渤, 马识佳, 等. 数字终端音视频实时自适应流式传输方法[J]. 小型微型计算机系统, 2010, 31(6):1231-1235. | |
| [8] | YU Bo, LI Xuanshan, WANG Wei, et al. Research and Application of Real-Time Communication Optimization Based on QUIC[J]. Journal of Chinese Computer Systems, 2021, 42(8): 1753-1757. |
| 于波, 李炫杉, 王卫, 等. 基于QUIC的实时通信优化研究与应用[J]. 小型微型计算机系统, 2021, 42(8):1753-1757. | |
| [9] | HU Jingxiu, YANG Yang, XIONG Lu, et al. SM Algorithm Analysis and Software Performance Research[J]. Netinfo Security, 2021, 21(10): 8-16. |
| 胡景秀, 杨阳, 熊璐, 等. 国密算法分析与软件性能研究[J]. 信息网络安全, 2021, 21(10):8-16. | |
| [10] | ZUO Liming, XIA Pingping, CHEN Zuosong. Protection Technology of Network Camera Based on SM2 Digital Signature[J]. Netinfo Security, 2018, 18(5): 32-40. |
| 左黎明, 夏萍萍, 陈祚松. 基于国密SM2数字签名的网络摄像头保护技术[J]. 信息网络安全, 2018, 18(5):32-40. | |
| [11] | XU Shengwei, DENG Ye, TIAN Yu. Design and Application of a Cloud Bilateral Collaborative Signature Scheme Based on SM2[J]. Journal of Beijing Electronic Science and Technology Institute, 2023, 31(1): 1-8. |
| 许盛伟, 邓烨, 田宇. 基于SM2的云服务器端双方协同签名方案设计与应用[J]. 北京电子科技学院学报, 2023, 31(1):1-8. | |
| [12] |
XU Dawen, WANG Rangding, SHI Yunqing. Data Hiding in Encrypted H.264/AVC Video Streams by Codeword Substitution[J]. IEEE Transactions on Information Forensics and Security, 2014, 9(4): 596-606.
doi: 10.1109/TIFS.2014.2302899 URL |
| [13] | QIN Lele, ZHANG Guojuan, LI You. Application of CSK Encryption Algorithm in Video Synergic Command Systems[J]. Journal of Organizational and End User Computing(JOEUC), 2022, 34(2): 1-18. |
| [14] | ABOMHARA M, ZAKARIA O, KHALIFA O O, et al. Enhancing Selective Encryption for H.264/AVC Using Advanced Encryption Standard[J]. International Journal of Computer and Electrical Engineering, 2022, 10(1): 339-341. |
| [15] | KHALIL M I. Real-Time Encryption/Decryption of Audio Signal[J]. International Journal of Computer Network and Information Security, 2016, 8(2): 25-31. |
| [16] | LI Shanxi, CHEN Wenbo, SHANG Zhihao. Research on the Performance of Encryption Techniques for High-Bandwidth Multicast Video Streaming[C]// University of Western Australia. 1st International Workshop on Cloud Computing and Information Security. Brisbane: Atlantis Press, 2013: 492-496. |
| [17] | ABOMHARA M, ZAKARIA O, KHALIFA O O. An Overview of Video Encryption Techniques[J]. International Journal of Computer Theory and Engineering, 2010, 2(1): 1793-1801. |
| [18] |
CHENG Shuli, WANG Liejun, AO Naixiang, et al. A Selective Video Encryption Scheme Based on Coding Characteristics[J]. Symmetry, 2020, 12(3): 332-340.
doi: 10.3390/sym12030332 URL |
| [19] | MAO Niansheng, ZHUO Li, ZHANG Jing, et al. Fast Compression Domain Video Encryption Scheme for H.264/AVC Streaming[C]// IEEE. 14th International Conference on Advanced Communication Technology(ICACT). New York: IEEE, 2012: 425-429. |
| [20] |
SALLAM A I, FARAGALLAH O S, EL-RABAIE E S M. HEVC Selective Encryption Using RC6 Block Cipher Technique[J]. IEEE Transactions on Multimedia, 2017, 20(7): 1636-1644.
doi: 10.1109/TMM.2017.2777470 URL |
| [21] |
WANG Xingyuan, SU Yining. An Audio Encryption Algorithm Based on DNA Coding and Chaotic System[J]. IEEE Access, 2020, 8: 9260-9270.
doi: 10.1109/Access.6287639 URL |
| [1] | 王晶宇, 马兆丰, 徐单恒, 段鹏飞. 支持国密算法的区块链交易数据隐私保护方案[J]. 信息网络安全, 2023, 23(3): 84-95. |
| [2] | 王开轩, 滕亚均, 王琼霄, 王伟. 隐式证书的国密算法应用研究[J]. 信息网络安全, 2021, 21(5): 74-81. |
| [3] | 胡景秀, 杨阳, 熊璐, 吴金坛. 国密算法分析与软件性能研究[J]. 信息网络安全, 2021, 21(10): 8-16. |
| [4] | 吴志红, 赵建宁, 朱元, 陆科. 国密算法和国际密码算法在车载单片机上应用的对比研究[J]. 信息网络安全, 2019, 19(8): 68-75. |
| [5] | 李兆斌, 刘丹丹, 黄鑫, 曹浩. 基于国密算法的安全接入设备设计与实现[J]. 信息网络安全, 2016, 16(11): 19-27. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||