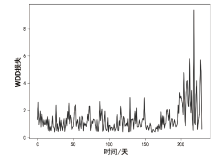
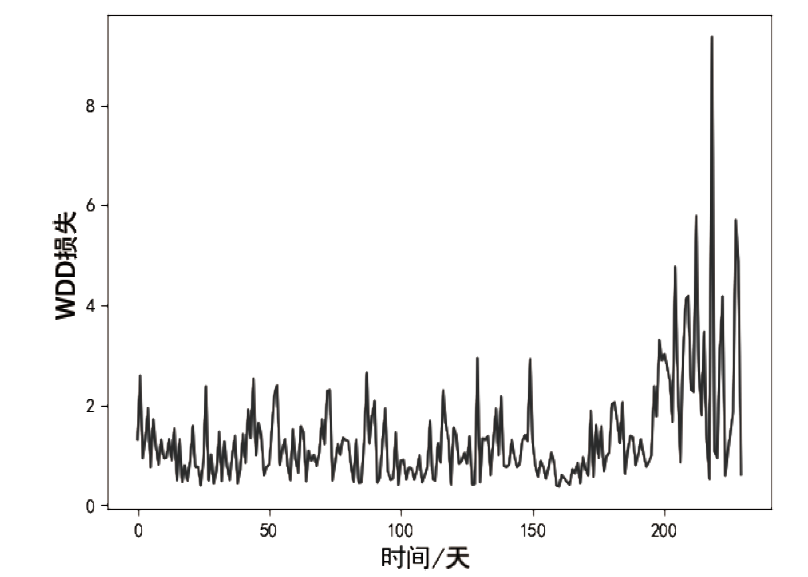
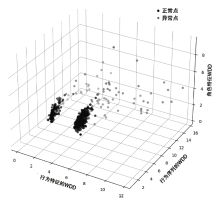
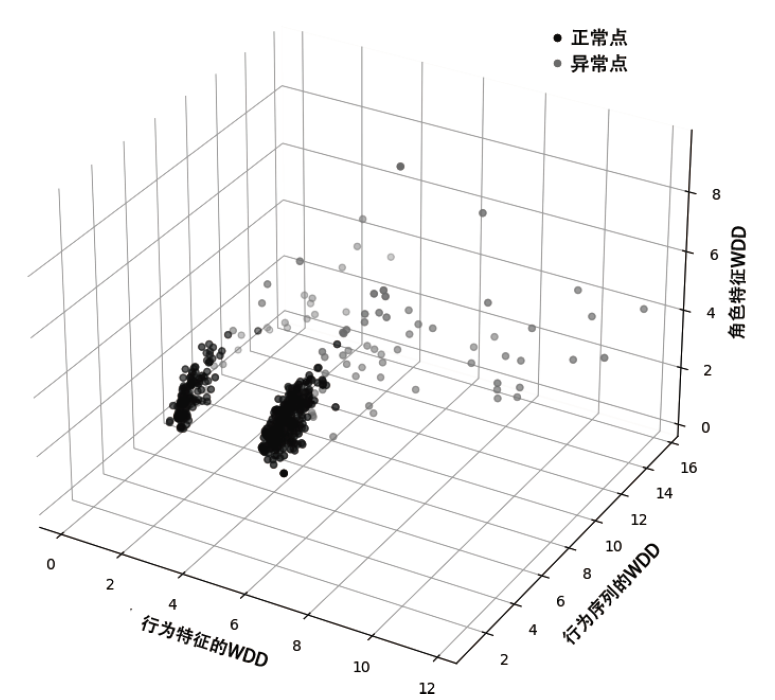
信息网络安全 ›› 2022, Vol. 22 ›› Issue (2): 1-10.doi: 10.3969/j.issn.1671-1122.2022.02.001
基于LSTM-Attention的内部威胁检测模型
- 1.西安电子科技大学网络与信息安全学院,西安 710071
2.河北科技大学信息科学与工程学院,石家庄 050018
-
收稿日期:2021-08-04出版日期:2022-02-10发布日期:2022-02-16 -
通讯作者:张冬雯 E-mail:zdwwtx@163.com -
作者简介:张光华(1979—),男,河北,教授,博士,主要研究方向为网络与信息安全|闫风如(1997—),女,河北,硕士研究生,主要研究方向为网络与信息安全|张冬雯(1964—),女,河北,教授,博士,主要研究方向为网络与信息安全|刘雪峰(1985—),男,安徽,副教授,博士,主要研究方向为隐私保护 -
基金资助:国家自然科学基金(62072239);国家重点研发计划(2018YFB0804701);河北省科技厅科技计划(20377725D)
Insider Threat Detection Model Based on LSTM-Attention
ZHANG Guanghua1,2, YAN Fengru2, ZHANG Dongwen2( ), LIU Xuefeng1
), LIU Xuefeng1
- 1. School of Cyber Engineering, Xidian University, Xi’an 710071, China
2. School of Information Science and Engineering, Hebei University of Science Technology, Shijiazhuang 050018, China
-
Received:2021-08-04Online:2022-02-10Published:2022-02-16 -
Contact:ZHANG Dongwen E-mail:zdwwtx@163.com
摘要:
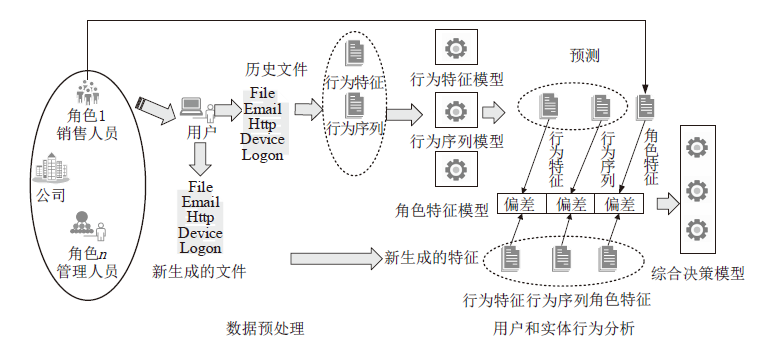
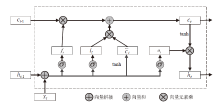
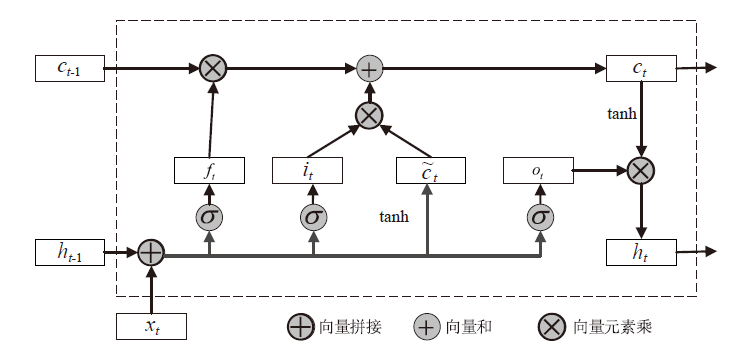
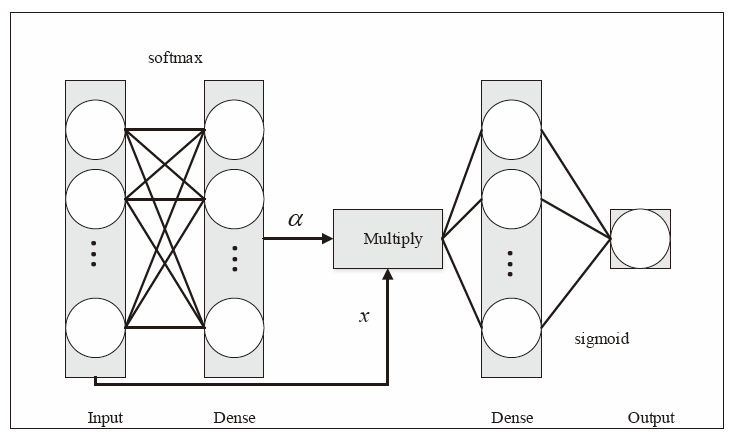
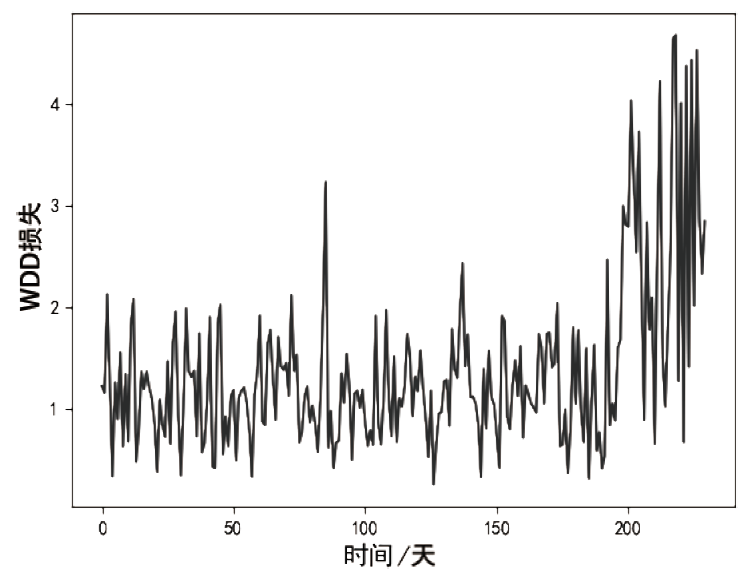
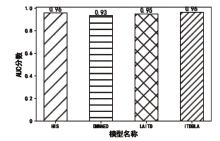
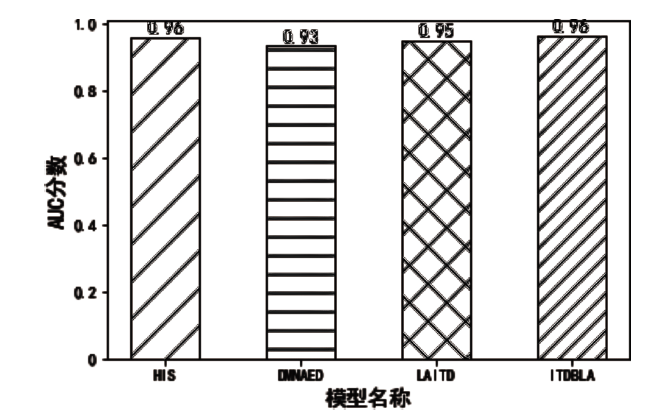
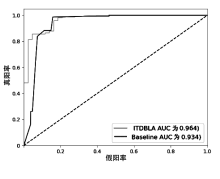
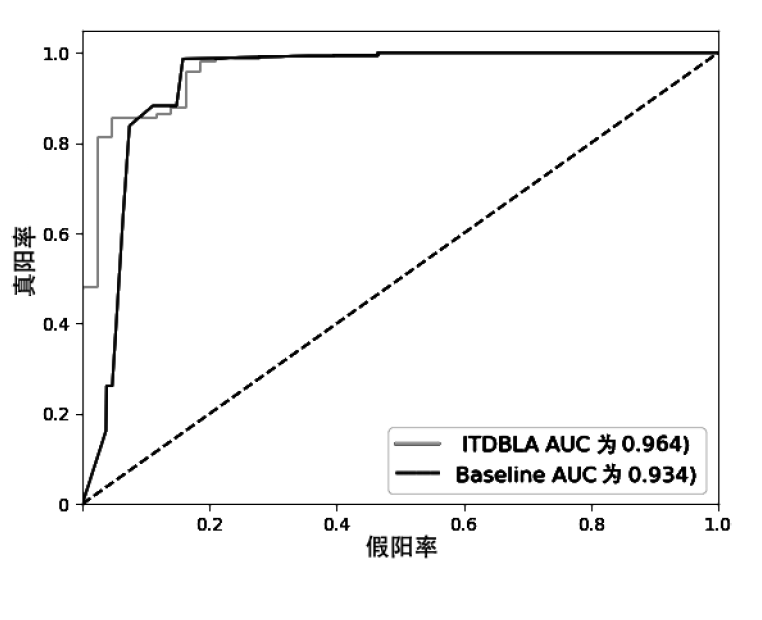
信息被内部人员非法泄露、复制、篡改,会给政府、企业造成巨大的经济损失。为了防止信息被内部人员非法窃取,文章提出一种基于LSTM-Attention的内部威胁检测模型ITDBLA。首先,提取用户的行为序列、用户行为特征、角色行为特征和心理数据描述用户的日常活动;其次,使用长短期记忆网络和注意力机制学习用户的行为模式,并计算真实行为与预测行为之间的偏差;最后,使用多层感知机根据该偏差进行综合决策,从而识别异常行为。在CERT内部威胁数据集上进行实验,实验结果表明,ITDBLA模型的AUC分数达0.964,具有较强的学习用户活动模式和检测异常行为的能力。
中图分类号:
引用本文
张光华, 闫风如, 张冬雯, 刘雪峰. 基于LSTM-Attention的内部威胁检测模型[J]. 信息网络安全, 2022, 22(2): 1-10.
ZHANG Guanghua, YAN Fengru, ZHANG Dongwen, LIU Xuefeng. Insider Threat Detection Model Based on LSTM-Attention[J]. Netinfo Security, 2022, 22(2): 1-10.
| [1] | LAN Caihui, LI Haifeng, YIN Shoulin, et al. A New Security Cloud Storage Data Encryption Scheme Based on Identity Proxy Re-encryption[J]. International Journal of Network Security, 2017, 19(5):804-810. |
| [2] |
KABIR E, HU Jiankun, WANG Hua, et al. A Novel Statistical Technique for Intrusion Detection Systems[J]. Future Generation Computer Systems, 2018, 79(1):303-318.
doi: 10.1016/j.future.2017.01.029 URL |
| [3] | WU Chi, SHUAI Junlan, LONG Tao, et al. Research on Detection Method of User Abnormal Operation Based on Linux Shell Commands[J]. Netinfo Security, 2021, 21(5):31-38. |
| 吴驰, 帅俊岚, 龙涛, 等. 基于Linux Shell命令的用户异常操作检测方法研究[J]. 信息网络安全, 2021, 21(5):31-38. | |
| [4] | YAO Hailong, WANG Caifen, XU Qinbai, et al. A Distributed Biometric Authentication Protocol Based on Homomorphic Encryption[J]. Journal of Computer Research and Development, 2019, 56(11):2375-2383. |
| 姚海龙, 王彩芬, 许钦百, 等. 一种基于同态加密的分布式生物特征认证协议[J]. 计算机研究与发展, 2019, 56(11):2375-2383. | |
| [5] |
YE Xiaoyun, HONG S S, HAN M M. Feature Engineering Method Using Double-layer Hidden Markov Model for Insider Threat Detection[J]. International Journal of Fuzzy Logic and Intelligent Systems, 2020, 20(1):17-25.
doi: 10.5391/IJFIS.2020.20.1.17 URL |
| [6] | TIAN Zhihong, LUO Chaochao, LU Hui, et al. User and Entity Behavior Analysis under Urban Big Data[J]. ACM Transactions on Data Science, 2020, 1(3):1-19. |
| [7] | GORKA S, JONATHAN C, NEIL M, et al. 2019 Market Guide for User and Entity Behavior Analytics[R]. USA: Gartner, G00349450, 2019. |
| [8] | DU Min, LI Feifei, ZHENG Guineng, et al. DeepLog: Anomaly Detection and Diagnosis from System Logs through Deep Learning[C]//ACM. 2017 ACM SIGSAC Conference on Computer and Communications Security, October 30-November 3, 2017, New York, USA. New York: ACM, 2017: 1285-1298. |
| [9] | GUO Yuanbo, LIU Chunhui, KONG Jing, et al. Study on User Behavior Profiling in Insider Threat Detection[J]. Journal on Communications, 2018, 39(12):141-150. |
| 郭渊博, 刘春辉, 孔菁, 等. 内部威胁检测中用户行为模式画像方法研究[J]. 通信学报, 2018, 39(12):141-150. | |
| [10] | PAUL S, MISHRA S. LAC: LSTM Autoencoder with Community for Insider Threat Detection[C]//ACM. The 4th International Conference on Big Data Research (ICBDR’20), November 27-29, 2020, Tokyo, Japan. New York: ACM, 2020: 71-77. |
| [11] | BAO Haiyong, LU Rongxing, LI Beibei, et al. BLITHE: Behavior Rule-based Insider Threat Detection for Smart Grid[J]. IEEE Internet of Things Journal, 2015, 3(2):190-205. |
| [12] | MAVROEIDIS V, VISHI K, JOSANG A. A Framework for Data-driven Physical Security and Insider Threat Detection[C]//IEEE. 2018 IEEE/ACM International Conference on Advances in Social Networks Analysis and Mining (ASONAM), August 28-31, 2018, Barcelona, Spain. Piscataway: IEEE, 2018: 1108-1115. |
| [13] |
LEGG P A, BUCKLEY O, GOLDSMITH M, et al. Automated Insider Threat Detection System Using User and Role-based Profile Assessment[J]. IEEE Systems Journal, 2017, 11(2):503-512.
doi: 10.1109/JSYST.2015.2438442 URL |
| [14] | JAGIELSKI M, OPREA A, BIGGIO B, et al. Manipulating Machine Learning: Poisoning Attacks and Countermeasures for Regression Learning[C]//IEEE. 2018 IEEE Symposium on Security and Privacy (SP), May 20-24, 2018, San Francisco, CA, USA. Piscataway: IEEE, 2018: 204-221. |
| [15] | LIU Fei, LIM E T, LI Hongxiu, et al. Disentangling Utilitarian and Hedonic Consumption Behavior in Online Shopping: An Expectation Disconfirmation Perspective[J]. Information & Management, 2020, 57(3):100-123. |
| [16] | WEN Yu, WANG Weiping, MENG Dan. Mining User Cross-domain Behavior Patterns for Insider Threat Detection[J]. Chinese Journal of Computers, 2016, 39(8):1555-1569. |
| 文雨, 王伟平, 孟丹. 面向内部威胁检测的用户跨域行为模式挖掘[J]. 计算机学报, 2016, 39(8):1555-1569. | |
| [17] | YU Hong, ZHANG Tiantian, CHEN Jiaxin, et al. Web Items Recommendation Based on Multi-view Clustering[C]//IEEE. 2018 IEEE 42nd Annual Computer Software and Applications Conference (COMPSAC), July 23-27, 2018, Tokyo, Japan. Piscataway: IEEE, 2018: 153-158. |
| [18] | LI Zhi, SONG Lipeng. Research on Internal Threat Detection Based on User Window Behavior[J]. Computer Engineering, 2020, 46(4):135-142, 150. |
| 李志, 宋礼鹏. 基于用户窗口行为的内部威胁检测研究[J]. 计算机工程, 2020, 46(4):135-142, 150. | |
| [19] | SHASHANKA M, SHEN Minyi, WANG Jisheng. User and Entity Behavior Analytics for Enterprise Security[C]//IEEE. 2016 IEEE International Conference on Big Data (Big Data), December 5-8, 2016, Washington, DC, USA. Piscataway: IEEE, 2016: 1867-1874. |
| [20] | TEODORA S B, CAGLAYAN B, HAYTHAM A. DeepAD: A Generic Framework Based on Deep Learning for Time Series Anomaly Detectio[M]. Berlin: Springer, 2018: 577-588. |
| [21] | YUAN Fangfang, CAO Yanan, SHANG Yanmin, et al. Insider Threat Detection with Deep Neural Network[C]//Springer. International Conferenceon Computational Science(ICCS), June 11-13, 2018, Wuxi, China. Heidelberg: Springer, 2018: 43-54. |
| [22] |
HOCHREITER S, SCHMIDHUBER J. Long Short-term Memory[J]. Neural Computation, 1997, 9(8):1735-1780.
doi: 10.1162/neco.1997.9.8.1735 URL |
| [23] | GLASSER J, LINDAUER B. Bridging the Gap: A Pragmatic Approach to Generating Insider Threat Data[C]//IEEE. 2013 IEEE Security and Privacy Workshops, May 23-24, 2013, San Francisco, CA, USA. Piscataway: IEEE, 2013: 98-104. |
| [24] | LE D C, ZINCIR-HEYWOOD A N. Evaluating Insider Threat Detection Workflow Using Supervised and Unsupervised Learning[C]//IEEE. 2018 IEEE Security and Privacy Workshops, May 24, 2018, San Francisco, CA, USA. Piscataway: IEEE, 2018: 270-275. |
| [1] | 代翔, 孙海春, 牛硕, 朱容辰. 融合互注意力机制与BERT的中文问答匹配技术研究[J]. 信息网络安全, 2021, 21(12): 102-108. |
| [2] | 黄娜, 何泾沙, 吴亚飚, 李建国. 基于LSTM回归模型的内部威胁检测方法[J]. 信息网络安全, 2020, 20(9): 17-21. |
| [3] | 冯胥睿瑞, 刘嘉勇, 程芃森. 基于特征提取的恶意软件行为及能力分析方法研究[J]. 信息网络安全, 2019, 19(12): 72-78. |
| [4] | GULKhanSafiQamas, 尹继泽, 潘丽敏, 罗森林. 基于深度神经网络的命名实体识别方法研究[J]. 信息网络安全, 2017, 17(10): 29-35. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||