信息网络安全 ›› 2019, Vol. 19 ›› Issue (2): 36-42.doi: 10.3969/j.issn.1671-1122.2019.02.005
多源网络编码同态环签名方案研究
- 青海师范大学计算机学院,青海西宁 810082
-
收稿日期:2018-05-15出版日期:2019-02-10发布日期:2020-05-11 -
作者简介:作者简介:俞惠芳(1972—),女,青海,教授,博士,主要研究方向为密码学与信息安全;高新哲(1990—), 男, 山西, 硕士研究生, 主要研究方向为密码学与信息安全。
-
基金资助:国家自然科学基金[61363080];青海省基础研究计划[2016-ZJ-776]
Homomorphic Ring Signature Scheme Technology for Multi-source Network Coding
- School of Computer, Qinghai Normal University, Xining Qinghai 810082, China
-
Received:2018-05-15Online:2019-02-10Published:2020-05-11
摘要:
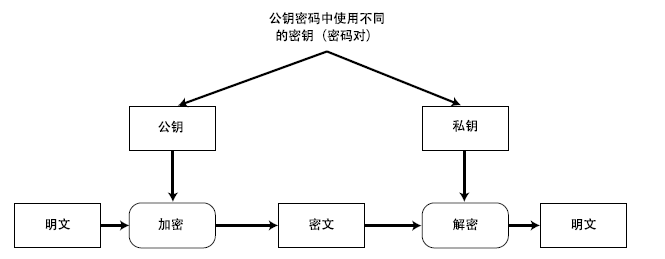
网络编码做为一种新的网络传输机制,相较于传统的网络技术,有着吞吐量大,鲁棒性好和速度快的优点,缺点是其更容易遭受污染攻击的破坏。由于传统的签名技术不能适用于多源网络编码。为此,文章采用Schnorr签名机制和同态加密算法构造了一个适用于多源网络编码的环签名方案,其安全性依赖于离散对数(DL)问题和计算Diffie-Hellman(CDH)问题的难解性。该方案中每个源节点用自己的私钥对消息签名,信宿节点用公钥验证;而且在环签名中引入时间概念,使方案能够同时抵抗污染攻击和重放攻击。
中图分类号:
引用本文
俞惠芳, 高新哲. 多源网络编码同态环签名方案研究[J]. 信息网络安全, 2019, 19(2): 36-42.
Huifang YU, Xinzhe GAO. Homomorphic Ring Signature Scheme Technology for Multi-source Network Coding[J]. Netinfo Security, 2019, 19(2): 36-42.
| [1] | YUN A, CHEON J H, KIM Y.On Homomorphic Signatures for Network Coding[J]. IEEE Transactions on Computers, 2010, 59(9):1295-1296. |
| [2] | ZHAO F,KALKER T,MEDARED M.Signature for Content Distribution with Network Coding[C]//IEEE.Symposium on Information Theory,November 12-15, 2006, Washington.New York:IEEE,2007:556-560. |
| [3] | ZHOU Xiuyuan, WANG Caifen, LUO Hai.Multi-source Network Coding Signature Scheme Based on RSA[J]. Computer Engineering and Design, 2012, 33(5): 1752-1756. |
| 周秀媛,王彩芬,罗海. 基于RSA的多源网络编码签名方案[J]. 计算机工程与设计,2012,33(5):1752-1756. | |
| [4] | NIU ShuFen, WANG CaiFen.Homomorphic Signature Algorithm for Multi-source Linear Network Coding[J]. Computer Engineering, 2012, 38(2): 126-128. |
| 牛淑芬,王彩芬. 多源线性网络编码的同态签名算法[J]. 计算机工程,2012,38(2):126-128. | |
| [5] | LIU Guangjun, WANG Bin.A Secure Network Coding Scheme Against Internal/External Pollution Attacks[J]. China Communications, 2013, 10(8): 100-110. |
| 刘光军,王斌. 抗代内/外污染攻击的安全网络编码方案[J]. 中国通信,2013,10(8):100-110. | |
| [6] | LUO Q, YANG G, SHE K, et al.Quantum Homomorphic Signature Using Coherent States[C]// IEEE. 2016 2nd IEEE International Conference on Computer and Communications (ICCC). October 14-17, 2016. Chengdu, China.New York:IEEE, 2017:1052-1055. |
| [7] | PEI Hengli, SHANG Tao, LIU Jianwei.A Secure Network Coding Method Based on Time Stamp and Homomorphic Signature[J]. Journal of Computation, 2013, 34(4): 28-35. |
| 裴恒利,尚涛,刘建伟. 融合时间戳和同态签名的安全网络编码方法[J]. 通信学报,2013,34(4):28-35. | |
| [8] | MENG Yunfan, SUN Guangbiao, XING Jie, et al.Wireless Body Area Network Security Signature Scheme Based on Network Coding and ECC[J]. Telecommunications Technology, 2015, 55(6): 605-610. |
| 蒙云番,孙光昊,邢杰,等. 基于网络编码和ECC的无线体域网安全签名方案[J]. 电讯技术,2015,55(6): 605-610. | |
| [9] | LUO Peng, YANG Xiaoyuan.Multi-PKG Identity-based Encryption Scheme Based on Ring Signature[J]. Journal of Shandong Uuiversity(Natural Sciences), 2017, 52(6): 64-68. |
| 罗鹏,杨晓元. 基于环签名的支持多PKG身份基加密方案[J]. 山东大学学报(理学版) ,2017,52(6):64-68. | |
| [10] | LIU G J,LIU B Y,LIU X M, et al.Low-Complexity Secure Network Coding Against Wiretapping Using Intra/Inter-generation Coding[J]. China Communications,2015, 12(6):116-125. |
| [11] | LEE S H, MARIO G, HUGO K, et al.Performance Evaluation of Secure Network Coding Using Homomorphic Signature[C]//IEEE. 2011 International Symposium on Networking Coding, July 25-27, 2011,Beijing, China.New York: IEEE, 2011:1-6. |
| [12] | HE M, CHEN L, WANG H,et al.Survey on Secure Transmission of Network Coding in Wireless Networks[C]//IEEE. 2012 International Conference on Computer Science and Service System, August 11-13, 2012, Nanjing, China.New York:IEEE,2012:1216-1219. |
| [13] | PENG Yong, CHEN Yuqiang, YAN Wenjie.A Secure Multi-source Network Coding Signature Algorithm[J]. Computer Engineering and Applications, 2012, 48(30): 135-139. |
| 彭勇,陈愈强,严文杰. 一种安全的多源网络编码签名算法[J]. 计算机工程与应用,2012,48(30):135-139. | |
| [14] | PENG Tianli, SHANG Tao, LIU Jianwei.Network Coded Signature Scheme for Anti-generation Pollution Attack[J]. Beijing Aerospace Journal, 2015, 41(4): 721-726. |
| 彭天丽,尚涛,刘建伟. 抗代间污染攻击的网络编码签名方案[J]. 北京航空航天大报,2015,41(4):721-726. | |
| [15] | ZHOU Zhaobin, XU Li.Anti-pollution Network Coding Scheme Based on Digital Signature[J]. Journal of Computer Systems, 2016, 25(6): 185-190. |
| 周赵斌,许力. 基于数字签名的防污染网络编码方案[J]. 计算机系统应用,2016,25(6):185-190. | |
| [16] | FAN C I, SUN W Z, HUANG V S.Provably Secure Randomized Blind Signature Scheme Based on Bilinear Pairing[J]. Computers and Mathematics with Applications,2010,60(2): 285-293. |
| [17] | WANG Wenqiang, CHEN Shaozhen.An Identity-based Efficient Ring Signature Scheme[J]. Journal of Computer Applications, 2009, 29(11): 2990-2992. |
| 王文强,陈少真. 一种基于身份的高效环签名方案[J]. 计算机应用,2009,29(11):2990-2992. | |
| [18] | PENG Yong, YAN Wenjie, CHEN Yuqiang.A Multi-source Network Coded Homomorphic Signature Algorithm[J]. Journal of Hefei University of Technology(Natural Science), 2014, 37(3): 310-313. |
| 彭勇,严文杰,陈俞强. 一种多源网络编码同态签名算法[J]. 合肥工业大学学报(自然科学版) ,2014,37(3):310-313. | |
| [19] | LI Jianmin, YU Huifang, ZHAO Chen.Self-certified Blind Signcryption Protocol for UC Security[J]. Journal of Frontiers of Computer Science and Technology, 2017, 11(6): 932-940. |
| 李建民,俞惠芳,赵晨. UC安全的自认证盲签密协议[J]. 计算机科学与探索, 2017,11(6):932-940. |
| [1] | 陈福臻, 程久军, 廖竞学, 邵剑雨. 基于网络编码的同态HASH抗污染攻击系统研究[J]. 信息网络安全, 2015, 15(6): 33-40. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||