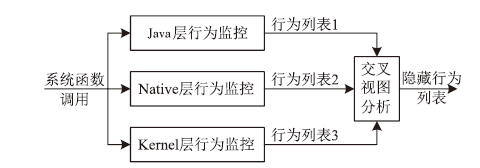
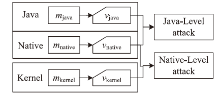
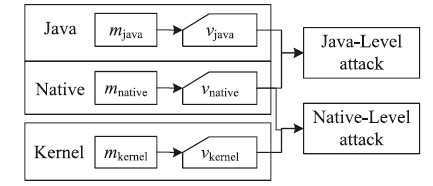
| [1] |
AVL移动安全. 2014年Android恶意代码发展报告[EB/OL]. .
|
| [2] |
360互联网安全中心. 2015年第二季度中国手机安全状况报告[EB/OL]. .
|
| [3] |
BURGUERA I, ZURUTUZA U, NADJM-TEHRANI S.Crowdroid: Behavior-based Malware Detection System for Android[C]//ACM. 1st ACM Workshop on Security and Privacy in Smartphones and Mobile Devices, October 17-21, 2011, Chicago, USA. New York: ACM, 2011: 15-25.
|
| [4] |
RUSSELLO G, JIMENEZ A B, NADERI H, et al.FireDroid: Hardening Security in Almost-stock Android[C]//ACM. 29th Annual Computer Security Applications Conference, December 9-13, 2013, Louisiana, USA. New York: ACM, 2013: 319-328.
|
| [5] |
ENCK W, GIBERT P, HAN S, et al.TaintDroid: An Information-Flow Tracking System for Realtime Privacy Monitoring on Smartphones[J]. ACM Transactions on Computer Systems, 2014, 32(2): 393-407.
|
| [6] |
DAVIS B, SANDERS B, KHODAVERDIAN A, et al. I-ARM-Droid: A Rewriting Framework for In-App Reference Monitors for Android Applications[EB/OL]. .
|
| [7] |
XU Rubin, SAÏDI H, ANDERSON R. Aurasium: Practical Policy Enforcement for Android Applications[C]//USENIX. 21st USENIX Conference on Security Symposium, August 8-10, 2012, Bellevue, Washington, USA. New York: ACM, 2012: 27.
|
| [8] |
PENG Guojun, SHAO Yuru, WANG Taige, et al.Research on Android Malware Detection and Interception Based on Behavior Monitoring[J]. Wuhan University Journal of Natural Sciences, 2012, 17(5): 421-427.
|
| [9] |
QIU Lingzhi, ZHANG Zixiong, SHEN Ziyi, et al.AppTrace: Dynamic Trace on Android Devices[C]//IEEE. 2015 IEEE International Conference on Communications (ICC), June 8-12, 2015, London, UK. New Jersey: IEEE, 2015: 7145-7150.
|
| [10] |
JEONG Y, LEE H T, CHO S J, et al.A Kernel-based Monitoring Approach for Analyzing Malicious Behavior on Android[C]//ACM. 29th Annual ACM Symposium on Applied Computing, March 24-28, 2014.New York: ACM, 2014: 1737-1738.
|
| [11] |
PAN Xuerui, ZHONGYANG Yibin, XIN Zhi, et al.Defensor: Lightweight and Efficient Security-enhanced Framework for Android[C]//IEEE. 2014 IEEE 13th International Conference on Trust, Security and Privacy in Computing and Communications, September 24-26, 2014, Beijing, China. New Jersey: IEEE, 2015: 260-267.
|
| [12] |
YAN L K, YIN Heng.DroidScope: Seamlessly Reconstructing the OS and Dalvik Semantic Views for Dynamic Android Malware Analysis[C]// USENIX. 21st USENIX Conference on Security Symposium, August 8-10, 2012, Bellevue, Washington, USA. New York: ACM, 2012: 29.
|
| [13] |
YD/T 2439-2012,移动互联网恶意程序描述格式[S]D/T 2439-2012, 移动互联网恶意程序描述格式[S]. 北京:人民邮电出版社,2012.
|
| [14] |
ZHOU Yajian, JIANG Xuxian.Dissecting Android Malware: Characterization and Evolution[C]//IEEE. 2012 IEEE Symposium on Security and Privacy, May 20-23, 2012, San Francisco, USA. New Jersey: IEEE, 2012: 95-109.
|
| [15] |
贾同彬,蔡阳,王跃武,等. 一种面向普通用户的Android APP安全性动态分析方法研究[J]. 信息网络安全,2015(9):1-5.
|
| [16] |
Google. UI/Application Exerciser Monkey[EB/OL]. .
|
| [17] |
朱筱赟,胡爱群,邢月秀,等.基于Android平台的移动办公安全方案综述[J]. 信息网络安全,2015(1):76-83.
|