信息网络安全 ›› 2016, Vol. 16 ›› Issue (1): 11-17.doi: 10.3969/j.issn.1671-1122.2016.01.003
硬件木马威胁与识别技术综述
- 1.中国电子科技集团公司第五十八研究所,江苏无锡 214072
2.中国电子科学研究院 北京 100041
3.西安电子科技大学微电子学院,陕西西安 710071
-
收稿日期:2015-11-19出版日期:2016-01-01发布日期:2020-05-13 -
作者简介:作者简介: 周昱(1983-),男,江苏,博士研究生,主要研究方向为芯片安全性测试、芯片防伪仿篡改设计;于宗光(1964-),男,山东,研究员,博士,主要研究方向为集成电路设计开发。
Threat Analysis and Detection Techniques of Hardware Trojans
- 1. No. 58 Research Institute, China Electronic Technology Group Corporation, Wuxi Jiangsu 214072, China
2. China Academy of Electronics and Information Technology, Beijing 100041, China
3. School of Microelectornics, Xidian University, Xi'an Shaanxi 710071, China
-
Received:2015-11-19Online:2016-01-01Published:2020-05-13
摘要:
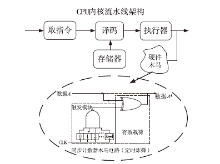
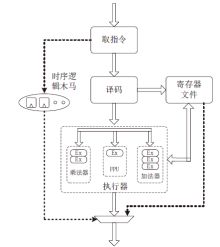
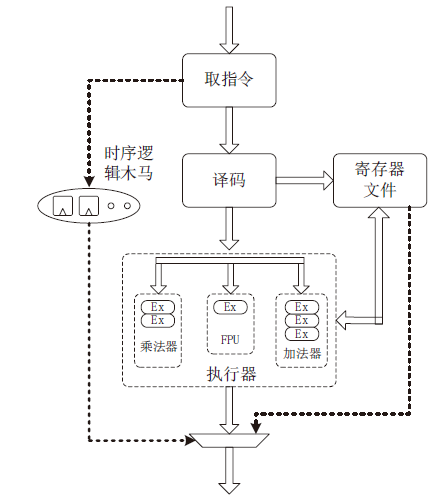
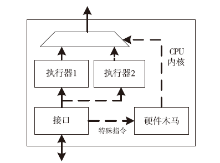
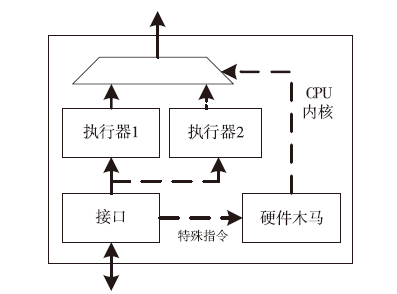
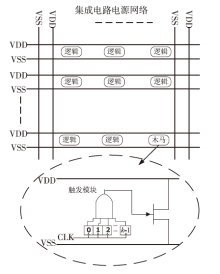
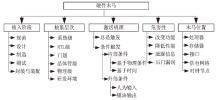
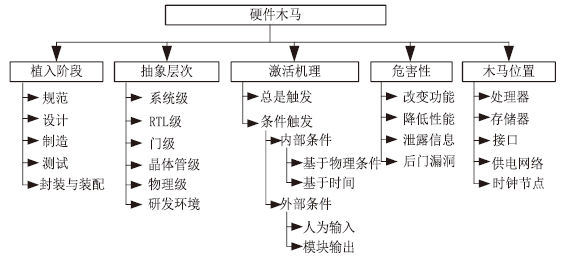
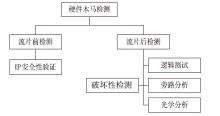
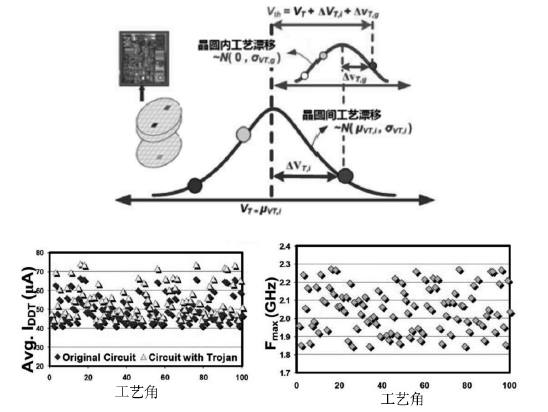
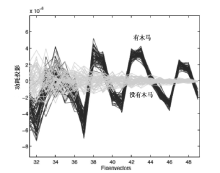
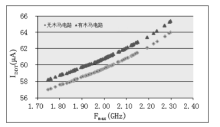
软件木马曾被认为是计算机系统的唯一安全威胁,计算机系统内的硬件即集成电路被普遍认为是安全可信的。但随着硬件木马这一针对集成电路及其应用的新的安全威胁的出现,打破了硬件安全可信的传统观点。硬件木马是集成电路在设计与制造过程中遭到人为恶意篡改而形成的影响电路功能、性能等参数的各种逻辑后门与漏洞。硬件木马的攻击模型有很多种,有的会改变电路的逻辑功能;有的会泄露电路内部的机密信息;还有的既不改变电路的功能,也不泄露电路内的机密信息,但能协助软件木马来攻击整个系统。随着集成电路设计的日益复杂,制造成本日趋高昂,集成电路产业正朝着全球合作的方向发展,集成电路在其产业链各环节受到硬件木马攻击的威胁将会越来越大,因此发展硬件木马的识别技术来保证集成电路的安全性已迫在眉睫。文章主要分析硬件木马造成的威胁,包括各种攻击模型及其分类,介绍当前硬件木马识别技术的最新研究进展,阐述未来该领域的研究热点。
中图分类号:
引用本文
周昱, 于宗光. 硬件木马威胁与识别技术综述[J]. 信息网络安全, 2016, 16(1): 11-17.
Yu ZHOU, Zongguang YU. Threat Analysis and Detection Techniques of Hardware Trojans[J]. Netinfo Security, 2016, 16(1): 11-17.
| [1] | DEFENSE SIENCE BOARD.Report of the Defense Science Board Task Force on High Performance Microchip Supply [R]. Washington DC: Defense Science Board, Feb 2005. |
| [2] | LIEBERMAN J.White Paper: National Security Aspects of the Global Migration of the U.S. Semiconductor Industry[R]. Airland Subcommittee, US Senate Armed Services Committee, June 2003. |
| [3] | ADEE S.The Hunt for the Kill Switch[J]. IEEE Spectrum, 2008, 45(5): 34-39. |
| [4] | MUTSCHLER A S.SEMI:Semi Equipment Industry Stands to Lose up to $4B Annually due to IP Infringements[J]. Electronic News, 2008,54(18):17-22. |
| [5] | DEAN COLLINS.Trust in Integrated Circuits and 3rd Party IP[C]//IEEE. International Workshop on Hardware-Oriented Trust Security,2008, Anaheim, CA. New York:IEEE. 2008:19-30. |
| [6] | AGRAWAL D, BAKTIR S, KARAKOYUNLU D, et al.Trojan Detection Using IC Fingerprinting[C]//IEEE. Symposium on Security and Privacy, 2007, Berkeley, California. New York: IEEE, 2007:296-310. |
| [7] | ABRAMOVICI M, BRADLEY P.Integrated Circuit Security New Threats and Solutions[C]//ACM. 5th Annual Workshop on Cyber Security Information Intellengence Research,2009. Oak Ridge,USA. New York:ACM, 2009:25-27. |
| [8] | CHAKRABORTY R S.Hardware Trojan: Threats and Emerging Solutions[C//IEEE. International High Level Design Validation Test Workshop,2009, San Francisco, CA. New York:IEEE, 2009:166-171. |
| [9] | LIN L, BURLESON W, PARR C.MOLES: Malicious Off-Chip Leakage Enabled by Side-Channels[C]//IEEE. International Conference on Computer-Aided Design, 2009, San Jose, CA. New York: IEEE, 2009:117-122. |
| [10] | KING S.Designing and Implementing Malicious Hardware[C]//USENIX. 1st Usenix Workshop on Large-Scale Exploits and Emergent Threats, 2008, San Francisco, CA. Berkeley: USENIX Association,2008:1-8. |
| [11] | Tehranipoor M, Koushanfar F.A survey of Hardware Trojan Taxonomy and Detection[J]. IEEE Design Test Comput., 2010, 27(1) : 10-25. |
| [12] | RAJENDRAN J.Towards a Comprehensive and Systematic Classification of Hardware Trojans[C]//IEEE. International Symposium on Circuits and Systems,2010, Pairs. New York: IEEE, 2010:1871-1874. |
| [13] | KARRI R, RAJENDRAN J, ROSENFELD K, et al.Trustworthy Hardware: Identifying and Classifying Hardware Trojans[J]. IEEE Computer, 2011, 43(10):39-46. |
| [14] | BANGA M, HSIAO M.Trusted RTL: Trojan Detection Methodology in Pre-silicon Designs[C]//IEEE. International Workshop on Hardware-Oriented Trust Security,2010, Anaheim,CA. New York: IEEE.2010:56-59. |
| [15] | SMITH S, DI J.Detecting Malicious Logic through Structural Checking[C]//IEEE. Region 5 Technical Conference, 2007, Fayetteville, AR. New York:IEEE, 2007:217-222. |
| [16] | ACHARYYA D, PLUSQUELLIC J.Calibrating Power Supply Signal Measurements for Process and Probe Card Variations[C]//IEEE. International Workshop on Current Defect Based Test,2004, Napa Valley, CA. New York:IEEE, 2004:23-30. |
| [17] | JIN Y, MAKRIS Y.Hardware Trojan Detection Using Path Delay Fingerprint[C]//IEEE. International Workshop on Hardware-Oriented Trust Security, 2008, Anaheim,CA. New York:IEEE, 2008:51-57. |
| [18] | ALKABANI Y, KOUSHANFAR F.Consistency-based Characterization for IC Trojan Detection[C]//IEEE. International Conference on Comput-aided Design, 2009, San Jose, CA. New York:IEEE, 2009:123-127. |
| [19] | POTKONJAK M, NAHAPETIAN A, NELSON M, et al.Hardware Trojan Horse Detection Using Gate-level Characterization[C]//IEEE. Proc. Design Automation Conference, 2009.San Francisco, CA. New York:IEEE, 2009:688-693. |
| [20] | RAI D, LACH J.Performance of Delay-Based Trojan Detection Techniques under Parameter Variations[C]//IEEE. IEEE International Workshop on Hardware-Oriented Security Trust,2009, Francisco, CA. New York:IEEE, 2009:58-65. |
| [21] | AARESTAD J, ACHARYYA D, RAD R, et al.Detecting Trojans though Leakage Current Analysis Using Multiple Supply Pad IDDQs[J]. IEEE Transaction on Information Forensics Security, 2010, 5(4): 893-904. |
| [22] | LAMECH C, RAD R M, Tehranipoor M, et al. An experimental Analysis of Power and Delay Signal-to-noise Requirements for Detecting Trojans and Methods for Achieving the Required Detection Sensitivities[J]. IEEE Transaction on Information. Forensics Security, 2011,6(3), pt. 2 : 1170-1179. |
| [23] | NARASIMHAN S.Hardware Trojan Detection by Multiple-parameter Side-channel Analysis[J]. IEEE Transaction on Computers. 2013,62(10): 2183-2195. |
| [24] | CHAKRABORTY RS, WOLFF F, PAUL S, PAPACHRISTOU C, et al.A Statistical Approach for Hardware Trojan Detection[C]//Springer. Workshop on Cryptographic. Hardware Embedded System, 2009, Lausanne. Berling:Springer 2009:396-410. |
| [25] | SALMANI H, TEHRANIPOOR M, PLUSQUELLIC J.A novel Technique for Improving Hardware Trojan Detection and Reducing Trojan Activation Time[J]. IEEE Transaction on Very Large Scale Integrated System, 2011, 20(1): 112-125. |
| [26] | ELENA DUBROVA.Keyed Logic BIST for Trojan Detection in SoC[C]//IEEE. International Symposium on System-on-Chip, 2014, Tampere. New York:IEEE, 2014:1-4. |
| [27] | BHUNIA S.Protection Against Hardware Trojan Attacks: Towards A Comprehensive Solution[J]. IEEE Design and Test of Computers, 2013, 30(3) : 6-17. |
| [28] | SONG P.Malicious Alteration Recognition and Verification by Emission of Light[C]//IEEE. International Symposium on Hardware-Oriented Security and Trust, 2011, San Diego, CA. New York:IEEE, 2011:117-121. |
| [29] | STELLARI F.Testing and Diagnostics of CMOS Circuits Using Light Emission from Off-state Leakage Current[J]. IEEE Transaction on Electron Devices, 2004, 51(9): 1455-1462. |
| [30] | STELLARI F.Verification of Untrusted Chips Using Trusted Layout and Emission Measurements[C]//IEEE. International Symposium on Hardware-Oriented Security and Trust, 2014, Arlington, VA. New York:IEEE, 2014:19-24. |
| [1] | 苏静, 路文玲, 赵毅强, 史艳翠. 基于支持向量机的硬件木马检测建模与优化[J]. 信息网络安全, 2017, 17(8): 33-38. |
| [2] | 苏静, 赵毅强, 张中伟, 谢艳芳. 基于侧信道分析的硬件木马检测方法[J]. 信息网络安全, 2017, 17(11): 19-24. |
| [3] | . 扫描电压对硬件木马检测影响分析[J]. , 2014, 14(7): 7-. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||