信息网络安全 ›› 2025, Vol. 25 ›› Issue (4): 654-663.doi: 10.3969/j.issn.1671-1122.2025.04.013
一种面向固件网络应用的高效灰盒模糊测试方法
- 北京理工大学网络空间安全学院,北京 100081
-
收稿日期:2024-09-29出版日期:2025-04-10发布日期:2025-04-25 -
通讯作者:谭毓安tan2008@bit.edu.cn -
作者简介:常振轩(2003—),男,河北,博士研究生,主要研究方向为固件安全、模糊测试|郑之涵(2000—),男,山西,博士研究生,主要研究方向为固件安全、UEFI安全、模糊测试|梅傲寒(2002—),男,湖北,硕士研究生,主要研究方向为固件安全、系统安全|谭毓安(1972—),男,重庆,教授,博士,主要研究方向为固件安全、数据安全。 -
基金资助:国家自然科学基金(U2336201)
An Efficient Gray-Box Fuzzing Approach for Firmware Network Applications
CHANG Zhenxuan, ZHENG Zhihan, MEI Aohan, TAN Yu’an( )
)
- School of Cyberspace Science and Technology, Beijing Institute of Technology, Beijing 100081, China
-
Received:2024-09-29Online:2025-04-10Published:2025-04-25
摘要:
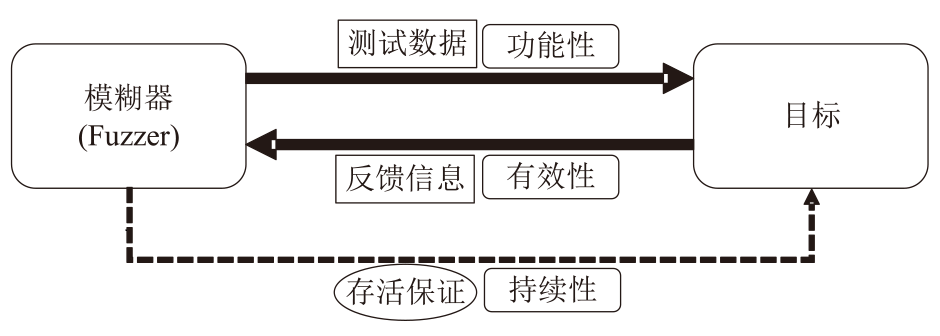
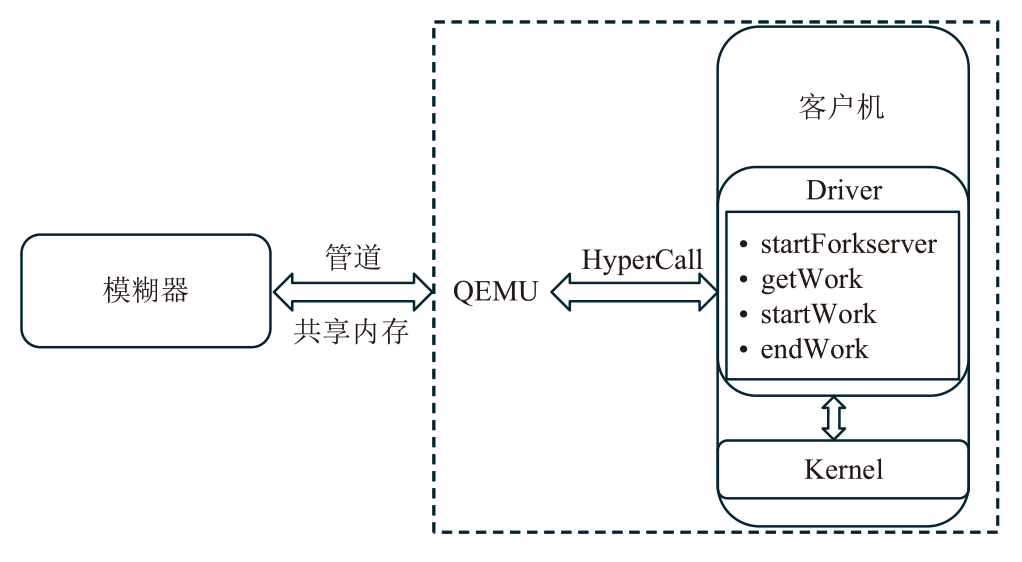
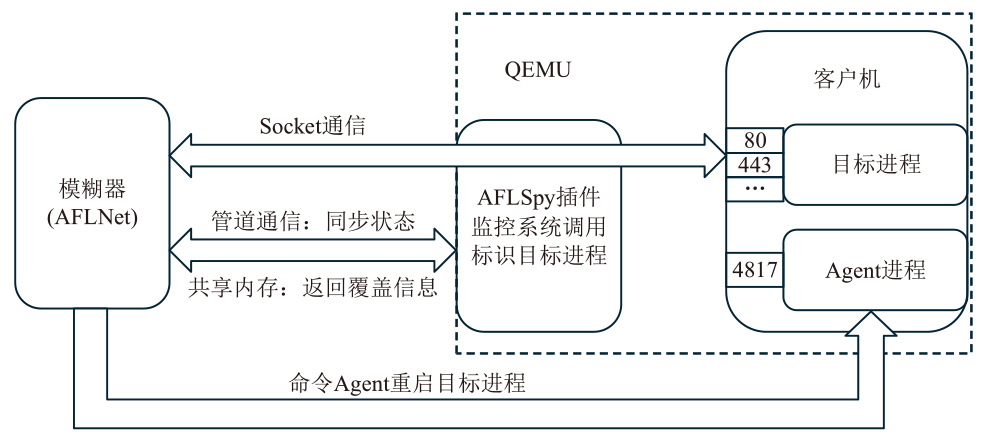
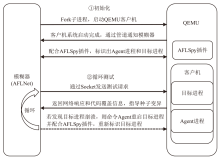
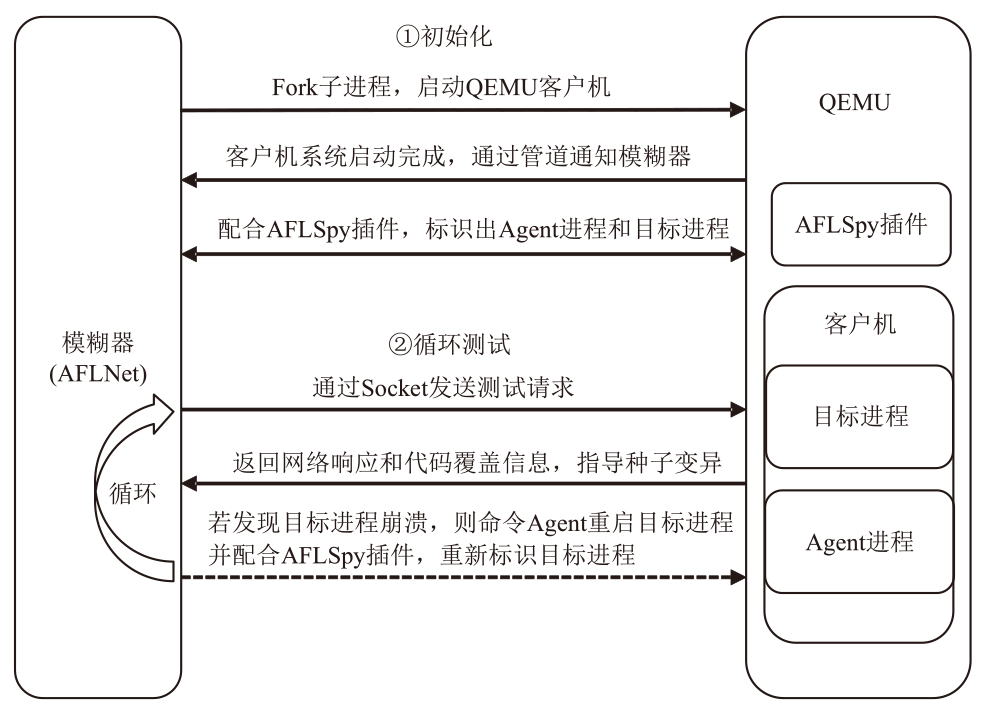
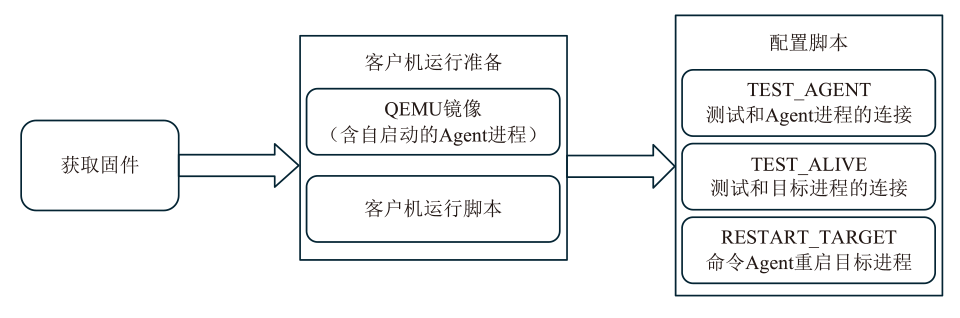
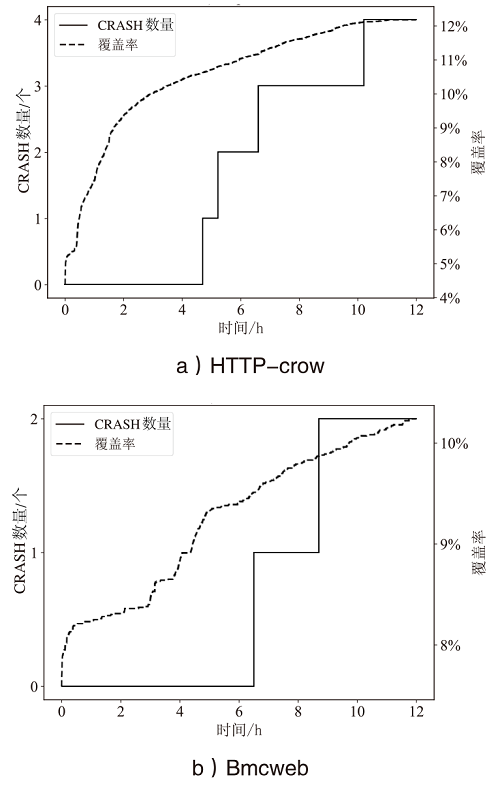
灰盒模糊测试是针对通用软件程序进行脆弱性分析和漏洞挖掘的有效方式,但无法直接应用于固件设备。文章首先从功能性、有效性和持续性三个方面对灰盒模糊测试的基本技术要求进行系统梳理,指出现有的固件灰盒模糊测试方法存在配置复杂、通用性差、虚拟机内省系统开销大等不足之处。随后提出一种面向固件网络应用的高效灰盒模糊测试方法,通过对客户机网络相关的系统调用进行监测,利用页目录地址来标识目标进程进而收集代码覆盖信息。该方法不需要复杂的虚拟机内省系统支持即可满足灰盒模糊测试的三项基本技术要求。基于该方法,作者开发出支持多种网络协议的原型系统FAN(FirmAFLNet),并使用该系统对两种固件网络应用进行测试。相较于使用虚拟机内省系统,该方法引入的时间开销从12%下降到4%左右,实验结果证明了该方法的有效性。
中图分类号:
引用本文
常振轩, 郑之涵, 梅傲寒, 谭毓安. 一种面向固件网络应用的高效灰盒模糊测试方法[J]. 信息网络安全, 2025, 25(4): 654-663.
CHANG Zhenxuan, ZHENG Zhihan, MEI Aohan, TAN Yu’an. An Efficient Gray-Box Fuzzing Approach for Firmware Network Applications[J]. Netinfo Security, 2025, 25(4): 654-663.
| [1] | SINHA S. State of IoT 2023[EB/OL]. (2023-09-03)[2024-03-25]. https://iot-analytics.com/number-connected-iot-devices. |
| [2] | ZALEWSKI M. American Fuzzy Lop[EB/OL]. (2021-06-08)[2024-03-25]. https://github.com/google/AFL. |
| [3] | BHME M, PHAM V T, ROYCHOUDHURY A. Coverage-Based Greybox Fuzzing as Markov Chain[C]// ACM. 2016 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2016: 1032-1043. |
| [4] | SCHUMILO S, ASCHERMANN C, GAWLIK R, et al. kAFL: Hardware-Assisted Feedback Fuzzing for OS Kernels[C]// USENIX. 26th USENIX Security Symposium (USENIX Security 17). Berkeley: USENIX, 2017: 167-182. |
| [5] | BOHME M, PHAM V T, NGUYEN M D, et al. Directed Greybox Fuzzing[C]// ACM. 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 2329-2344. |
| [6] | LYU Chenyang, JI S, ZHANG C, et al. MOPT: Optimized Mutation Dcheduling for Fuzzers[C]// USENIX. 28th USENIX Security Symposium (USENIX Security 19). Berkeley: USENIX, 2019: 1949-1966. |
| [7] | FIORALDI A, MAIER D, EIFELDT H, et al. AFL++: Combining Incremental Steps of Fuzzing Research[C]// USENIX. 14th USENIX Workshop on Offensive Technologies (WOOT 20). Berkeley: USENIX, 2020: 1-12. |
| [8] | LI Hangyu, FANG Haoran, QU Yanwen, et al. ADFuzz: Using Anomaly Detection to Filter Rare Paths for Efficient Fuzzing[J]. Journal of Computer Research and Development, 2023, 60(8): 1912-1924. |
| 李航宇, 方浩然, 曲彦文, 等. ADFuzz: 使用异常检测筛选低频路径高效模糊测试[J]. 计算机研究与发展, 2023, 60(8): 1912-1924. | |
| [9] | XIA C S, PALTENGHI M, TIAN J L, et al. Fuzz4ALL: Universal Fuzzing with Large Language Models[C]// ACM. 46th International Conference on Software Engineering(ICSE 24). New York: ACM, 2024: 1-13. |
| [10] | PHAM V T, BHME M, ROYCHOUDHURY A. AFLNET: A Greybox Fuzzer for Network Protocols[C]// IEEE. 13th International Conference on Software Testing, Validation and Verification (ICST 20). New York: IEEE, 2020: 460-465. |
| [11] | BELLARD F. QEMU, A Fast and Portable Dynamic Translator[C]// USENIX. USENIX Annual Technical Conference, FREENIX Track. Berkeley: USENIX, 2005: 10-50. |
| [12] | HERTZ J, NEWSHAM T. Project Triforce: Run AFL on Everything[EB/OL]. (2018-09-09)[2024-03-25]. https://github.com/nccgroup/TriforceAFL. |
| [13] | HERTZ J, NEWSHAM T. Triforce Linux Syscall Fuzzer[EB/OL]. (2017-01-05)[2024-03-25]. https://github.com/nccgroup/TriforceLinuxSyscallFuzzer. |
| [14] | ZHENG Yaowen, DAVANIAN A, YIN H, et al. FIRM-AFL: High-Throughput Greybox Fuzzing of IoT Firmware via Augmented Process Emulation[C]// USENIX. 28th USENIX Security Symposium (USENIX Security 19). Berkeley: USENIX, 2019: 1099-1114. |
| [15] | HENDERSON A, PRAKASH A, YAN L, et al. Make It Work, Make It Right, Make It Fast: Building A Platform-Neutral Whole-System Dynamic Binary Analysis Platform[C]// ACM. 23rd ACM SIGSOFT International Symposium on Software Testing and Analysis(ISSTA 2014). New York: ACM, 2014: 248-258. |
| [16] | CLEMENTS A A, GUSTAFSON E, SCHARNOWSKI T, et al. HALucinator: Firmware Re-Hosting Through Abstraction Layer Emulation[C]// USENIX. 29th USENIX Security Symposium (USENIX Security 20). Berkeley: USENIX, 2020: 1201-1218. |
| [17] | SCHARNOWSKIS T, BARS N, SCHLOEGEL M, et al. Fuzzware: Using Precise MMIO Modeling for Effective Firmware Fuzzing[C]// USENIX. 31st USENIX Security Symposium (USENIX Security 22). Berkeley: USENIX, 2022: 1239-1256. |
| [18] | SEIDEL L, MAIER D C, MUENCH M. Forming Faster Firmware Fuzzers[C]// USENIX. 32nd USENIX Security Symposium (USENIX Security 23. Berkeley:USENIX, 2023: 2903-2920. |
| [19] | LIN Xinkang, GU Kuangyu, ZHAO Lei. UEFI Fuzz Testing System and Method Based on Heuristic Reverse Analysis[J]. Journal of Software, 2024, 35(8): 3577-3590 |
| 林欣康, 顾匡愚, 赵磊. UEFI 固件的启发式逆向分析与模糊测试方法[J]. 软件学报, 2024, 35(8): 3577-3590. | |
| [20] | LU Haoliang, ZOU Yanyan, PENG Yue, et al. Feedback-Driven Fuzzing Technology Based on Partial Simulation of IoT Devices[J]. Journal of Cyber Security, 2023, 8(1): 78-92. |
| 卢昊良, 邹燕燕, 彭跃, 等. 基于物联网设备局部仿真的反馈式模糊测试技术[J]. 信息安全学报, 2023, 8(1): 78-92. | |
| [21] | CHESSER M, NEPAL S, RANASINGHE D C. Icicle: A Re-Designed Emulator for Grey-Box Firmware Fuzzing[C]// ACM. 32nd ACM SIGSOFT International Symposium on Software Testing and Analysis(ISSTA 2023). New York: ACM, 2023: 76-88. |
| [22] | MUENCH M, STIJOHANN J, KARGL F, et al. What You Corrupt is Not What You Crash: Challenges in Fuzzing Embedded Devices[C]// ISOC. Network and Distributed System Security Symposium(NDSS 2018). Reston: ISOC, 2018: 1-15. |
| [23] | JI Jiangan, JING Jing, WANG Yisen, et al. Survey of Fuzzing in Embedded Firmware[J]. Journal of Chinese Computer Systems, 2024, 45(5): 1173-1180. |
| 计江安, 井靖, 王奕森, 等. 嵌入式固件模糊测试研究综述[J]. 小型微型计算机系统, 2024, 45(5): 1173-1180. | |
| [24] | CHEN D D, WOO M, BRUMLEY D, et al. Towards Automated Dynamic Analysis for Linux-Based Embedded Firmware[C]// ISOC. 2016 Network and Distributed System Security Symposium (NDSS 2016). Reston: ISOC, 2016: 1-16. |
| [25] | KIM M, KIM D, KIM E, et al. Firmae: Towards Large-Scale Emulation of IoT Firmware for Dynamic Analysis[C]// IEEE. 36th Annual Computer Security Applications Conference(ACSAC 2020). New York: IEEE, 2020: 733-745. |
| [26] | LEVITTE R, CASWELL M, POLYAKOV A, et al. OpenSSL[EB/OL]. (2024-03-25)[2024-05-25]. https://github.com/openssl/openssl. |
| [1] | 文伟平, 郭荣华, 孟正, 柏皛. 信息安全风险评估关键技术研究与实现[J]. 信息网络安全, 2015, 15(2): 7-8. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||