信息网络安全 ›› 2024, Vol. 24 ›› Issue (8): 1220-1230.doi: 10.3969/j.issn.1671-1122.2024.08.008
基于无证书签名的5G系统广播消息身份认证协议
- 1.中国科学院信息工程研究所,北京 100093
2.中国科学院大学网络空间安全学院,北京 100049
-
收稿日期:2024-04-25出版日期:2024-08-10发布日期:2024-08-22 -
通讯作者:彭诚pengcheng@iie.ac.cn -
作者简介:孙中岫(1999—),男,山东,硕士研究生,主要研究方向为网络空间安全、移动通信安全、通信协议分析|彭诚(1994—),男,北京,工程师,博士,主要研究方向为移动通信安全、通信协议分析、微弱信号检测与识别|范伟(1984—),男,北京,高级工程师,博士,CCF会员,主要研究方向为无线通信网络空间安全、区块链安全、微弱信号检测与识别、移动通信信号处理 -
基金资助:国家重点研发计划(2021YFB2700603)
System Broadcast Information Authentication Protocol Based on Certificateless Signature for 5G Network
SUN Zhongxiu1,2, PENG Cheng1,2( ), FAN Wei1,2
), FAN Wei1,2
- 1. Institute of Information Engineering, Chinese Academy of Sciences, Beijing 100093, China
2. School of Cyber Security, University of Chinese Academy of Sciences, Beijing 100049, China
-
Received:2024-04-25Online:2024-08-10Published:2024-08-22
摘要:
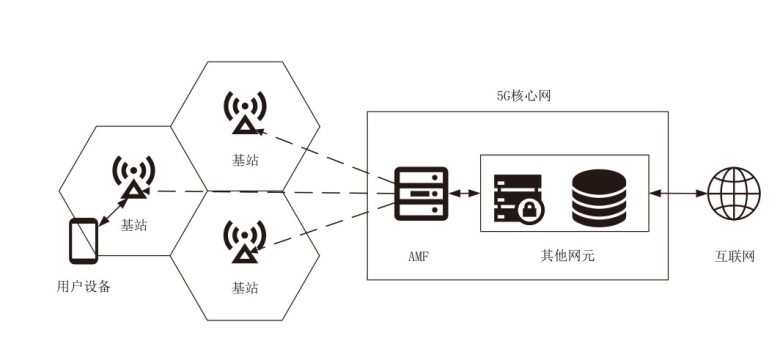
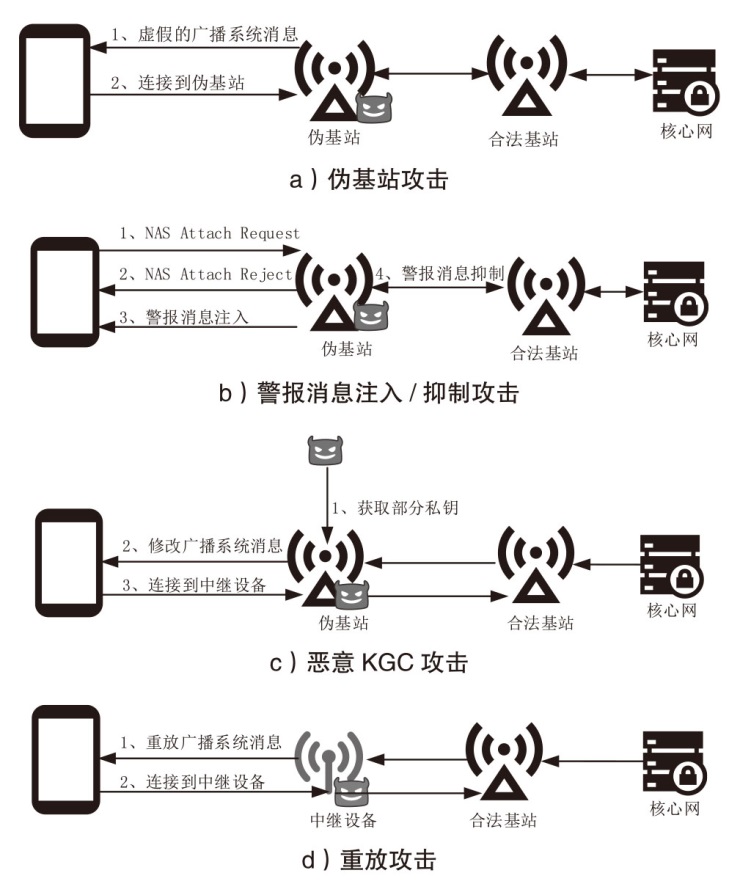
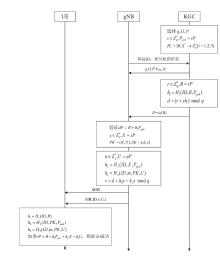
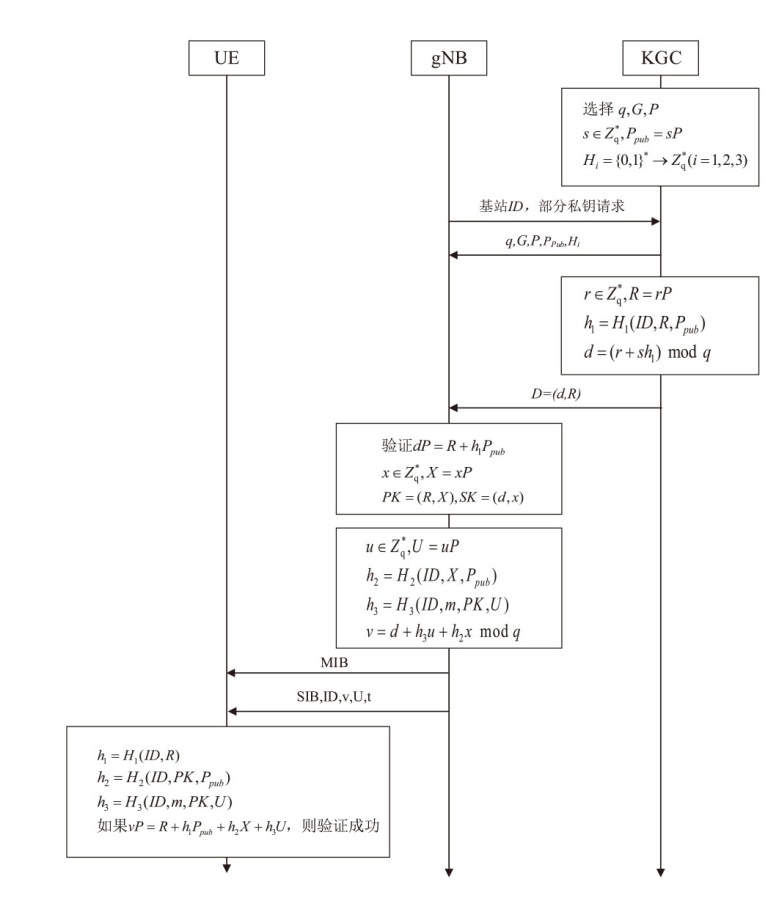
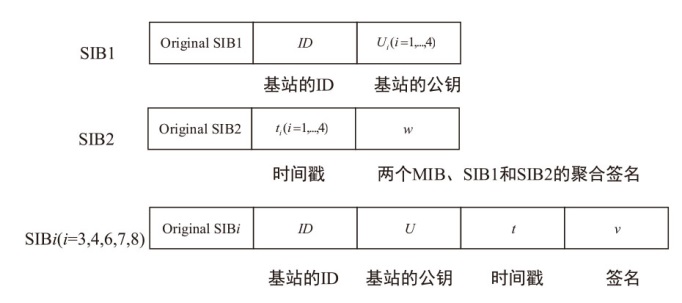
5G技术的普及促进了各行业生产力的发展,但5G网络的安全性问题也逐渐凸显,基站作为连接用户设备和核心网的枢纽,其安全性备受关注。由于基站通过广播发送的系统消息缺乏真实性和完整性的保护,攻击者可以通过修改系统消息,吸引用户设备在初始接入或者在小区重选时连接到伪基站,从而发起多种后续攻击。针对这一问题,文章提出了一种基于无证书签名的基站身份认证协议,为用户设备提供了一种验证基站广播系统消息合法性的方法,并从签名消息的选择、签名和验证的开销、抵御重放攻击几个方面进行了优化。仿真实验表明,该协议引入的计算开销是基站和用户设备可以接受的,与现有的基站身份认证协议相比,该协议提高了安全性,实现了更小的签名长度。
中图分类号:
引用本文
孙中岫, 彭诚, 范伟. 基于无证书签名的5G系统广播消息身份认证协议[J]. 信息网络安全, 2024, 24(8): 1220-1230.
SUN Zhongxiu, PENG Cheng, FAN Wei. System Broadcast Information Authentication Protocol Based on Certificateless Signature for 5G Network[J]. Netinfo Security, 2024, 24(8): 1220-1230.
| [1] | SHAIK A, BORGAONKAR R, ASOKAN N, et al. Practical Attacks against Privacy and Availability in 4G/LTE Mobile Communication Systems[EB/OL]. (2015-10-20)[2024-04-16]. https://ui.adsabs.harvard.edu/abs/2015arXiv151007563S/abstract. |
| [2] | 3GPP. Specification Number TR 33.809 Version 0.8.0, Study on 5G Security Enhancements against False Base Stations[EB/OL]. (2023-06-20)[2024-04-16]. https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3952. |
| [3] | SHAIK A, BORGAONKAR R, PARK S, et al. New Vulnerabilities in 4G and 5G Cellular Access Network Protocols: Exposing Device Capabilities[C]// ACM. Proceedings of the 12th Conference on Security and Privacy in Wireless and Mobile Networks. New York: ACM, 2019: 221-231. |
| [4] | BITSIKAS E, POPPER C. You Have Been Warned: Abusing 5G’s Warning and Emergency Systems[C]// ACM. Proceedings of the 38th Annual Computer Security Applications Conference. New York: ACM, 2022: 561-575. |
| [5] | 3GPP. 3GPP Specification Number TR 21.915 Version 15.0.0, Release Description; Release 15.[EB/OL]. (2018-03-20)[2024-04-06]. https://www.3gpp.org/ftp/Specs/archive/21_series/21.915/. |
| [6] | HA Man, CHEN Jing, LIU J K et al. Malicious KGC Attacks in Certificateless Cryptography[C]// ACM. Proceedings of the 2nd ACM Symposium on Information, Computer and Communications Security. New York: ACM, 2007: 302-311. |
| [7] | HUSSAIN S R, ECHEVERRIA M, CHOWDHURY O, et al. Privacy Attacks to the 4G and 5G Cellular Paging Protocols Using Side Channel Information[J]. Network and Distributed Systems Security (NDSS) Symposium, 2019(8): 1-12. |
| [8] | SHAIK A, BORGAONKAR R, PARK S, et al. On the Impact of Rogue Base Stations in 4G/LTE Self Organizing Networks[C]// ACM. Proceedings of the 11th ACM Conference on Security & Privacy in Wireless and Mobile Networks. New York: ACM, 2018: 75-86. |
| [9] | LEE G, LEE J. This is Your President Speaking: Spoofing Alerts in 4G LTE Networks[C]// ACM. Proceedings of the 17th Annual International Conference on Mobile Systems, Applications, and Services. New York: ACM, 2019: 404-416. |
| [10] | KIM M, PARK J G, MOON D S, et al. Long-Term Evolution Vulnerability Focusing on System Information Block Messages[C]// IEEE. 2020 International Conference on Information and Communication Technology Convergence (ICTC). New York: IEEE, 2020: 837-842. |
| [11] | JIN Jian, LIAN Changliang, XU Ming. Rogue Base Station Detection Using A Machine Learning Approach[C]// IEEE. 2019 28th Wireless and Optical Communications Conference (WOCC). New York: IEEE, 2019: 1-5. |
| [12] | SINGLA A, HUSSAIN S R, CHOWDHURY O, et al. Protecting the 4G and 5G Cellular Paging Protocols against Security and Privacy Attacks[J]. Proceedings on Privacy Enhancing Technologies, 2020(6): 1-9. |
| [13] | LOTTO A, SINGH V, RAMASUBRAMANIAN B, et al. Baron: Base-Station Authentication through Core Network for Mobility Management in 5G Networks[C]// ACM. Proceedings of the 16th ACM Conference on Security and Privacy in Wireless and Mobile Networks. New York: ACM, 2023: 133-144. |
| [14] | HUSSAIN S R, ECHEVERRIA M, SINGLA A, et al. Insecure Connection Bootstrapping in Cellular Networks: The Root of All Evil[C]// ACM. Proceedings of the 12th Conference on Security and Privacy in Wireless and Mobile Networks. New York: ACM, 2019: 1-11. |
| [15] | SINGLA A, BEHNIA R, HUSSAIN S R, et al. Look Before You Leap: Secure Connection Bootstrapping for 5G Networks to Defend against Fake Base-Stations[C]// ACM. Proceedings of the 2021 ACM Asia Conference on Computer and Communications Security. New York: ACM, 2021: 501-515. |
| [16] | SHAMIR A. Identity-Based Cryptosystems and Signature Schemes[C]//Springer. Advances in Cryptology:Proceedings of CRYPTO. Heidelberg: Springer, 1985: 47-53. |
| [17] | AL-RIYAMI S S, PATERSON K G. Certificateless Public Key Cryptography[C]// Springer. International Conference on the Theory and Application of Cryptology and Information Security. Heidelberg: Springer, 2003: 452-473. |
| [18] | WANG Liangliang, CHEN Kefei, LONG Yu, et al. An Efficient Pairing-Free Certificateless Signature Scheme for Resource-Limited Systems[J]. Science China (Information Sciences), 2017, 60(11): 11-23. |
| [19] | THUMBUR G, RAO G S, REDDY P V, et al. Efficient Pairing-Free Certificateless Signature Scheme for Secure Communication in Resource-Constrained Devices[J]. IEEE Communications Letters, 2020, 24(8): 1641-1645. |
| [20] | XU Zhiyan, LUO Min, KHAN M K, et al. Analysis and Improvement of a Certificateless Signature Scheme for Resource-Constrained Scenarios[J]. IEEE Communications Letters, 2020, 25(4): 1074-1078. |
| [21] | KHAN M, ALHAKAMI H, ULLAH I, et al. A Resource-Friendly Certificateless Proxy Signcryption Scheme for Drones in Networks Beyond 5G[J]. Drones, 2023, 7(5): 321-332. |
| [22] | ALMAZROI A, ALDHAHRI E, AL-SHAREEDA M, et al. ECA-VFog: An Efficient Certificateless Authentication Scheme for 5G-Assisted Vehicular Fog Computing[J]. Plos One, 2023, 18(6): 87-91. |
| [23] | DOLEV D, YAO A. On the Security of Public Key Protocols[J]. IEEE Transactions on Information Theory, 1983, 29(2): 198-208. |
| [24] | 3GPP. Specification Number TS 38.104 Version 15.9.0, Base Station (BS) Radio Transmission and Reception[EB/OL]. (2020-04-09)[2024-04-16]. https://www.3gpp.org/ftp/Specs/archive/38_series/38.104/. |
| [25] | BONEH D, GENTRY C, LYNN B, et al. Aggregate and Verifiably Encrypted Signatures from Bilinear Maps[C]// Springer. Advances in Cryptology—EUROCRYPT 2003:International Conference on the Theory and Applications of Cryptographic Techniques. Heidelberg: Springer, 2003: 416-432. |
| [26] | ZHAO Yunlei. Aggregation of Gamma-Signatures and Applications to Bitcoin[EB/OL]. (2018-04-21)[2024-04-16]. https://eprint.iacr.org/2018/414.pdf. |
| [27] | SRS. SRSRAN_Project[EB/OL]. (2023-02-22)[2024-04-24]. https://github.com/srsran/srsRAN_Project. |
| [28] | NIST. NIST Report on Cryptographic Key Length and Cryptoperiod[EB/OL]. (2020-05-24)[2024-04-06]. https://www.keylength.com/en/4/. |
| [29] | YAVUZ A A, MUDGERIKAR A, SINGLA A, et al. Real-Time Digital Signatures for Time-Critical Networks[J]. IEEE Transactions on Information Forensics and Security, 2017, 12(11): 2627-2639. |
| [1] | 刘芹, 张标, 涂航. 基于twisted Edwards曲线的无证书盲签名方案[J]. 信息网络安全, 2022, 22(8): 19-25. |
| [2] | 张敏, 许春香, 黄闽英. 远程医疗环境下面向多服务器的轻量级多因子身份认证协议研究[J]. 信息网络安全, 2019, 19(10): 42-49. |
| [3] | 粟栗, 邵京, 杜海涛. 移动通信网2G/3G/4G互操作风险分析与防护方案[J]. 信息网络安全, 2017, 17(9): 69-72. |
| [4] | 严子军, 范明钰, 王光卫. 一种针对多旋翼无人机的取证方案研究[J]. 信息网络安全, 2017, 17(6): 75-82. |
| [5] | 王沂, 韩广国, 李慧智. 无线网络中可证安全的移动用户密钥交换协议[J]. 信息网络安全, 2015, 15(3): 54-58. |
| [6] | 李赓, 赵玉萍, 孙春来, 赵辉. 一种基于伪信令的伪基站抑制方法研究与分析[J]. 信息网络安全, 2014, 14(9): 12-16. |
| [7] | 芦天亮, 周运伟, 曹巍. 移动互联网攻击技术及违法犯罪手段分析[J]. 信息网络安全, 2014, 14(9): 176-179. |
| [8] | 周之童, 夏子焱, 邢佳帅, 李珍妮. 伪基站系统侦测识别及定位方法研究[J]. 信息网络安全, 2014, 14(9): 196-198. |
| [9] | 王璐;夏文博;卓为. 基于Win7凭据提供程序开发的安全登录界面[J]. , 2013, 13(2): 0-0. |
| [10] | 钟秀玉. 加密算法在身份验证中的应用[J]. , 2010, (5): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||