信息网络安全 ›› 2022, Vol. 22 ›› Issue (3): 1-9.doi: 10.3969/j.issn.1671-1122.2022.03.001
智能电网中抗主次合谋攻击的群智频谱感知加固方案
- 1. 西安邮电大学无线网络安全技术国家工程实验室,西安 710121
2. 西安邮电大学网络空间安全学院,西安 710121
-
收稿日期:2021-11-20出版日期:2022-03-10发布日期:2022-03-28 -
通讯作者:冯景瑜 E-mail:fengjy@xupt.edu.cn -
作者简介:冯景瑜(1985—),男,甘肃,副教授,博士,主要研究方向为物联网安全|时翌飞(1996—),男,陕西,硕士研究生,主要研究方向为信息系统安全|王腾(1996—),女,陕西,讲师,博士,主要研究方向为隐私保护 -
基金资助:国家自然科学基金青年科学基金(62102311);国家电网有限公司科技项目(J2021206)
Crowd Spectrum Sensing Reinforcement Scheme Against Primary-secondary Collusive Attack in Smart Grid
FENG Jingyu1,2( ), SHI Yifei1,2, WANG Teng1,2
), SHI Yifei1,2, WANG Teng1,2
- 1. National Engineering Laboratory for Wireless Security, Xi’an University of Posts and Telecommunications, Xi’an 710121, China;
2. School of Cyberspace Security, Xi’an University of Posts and Telecommunications, Xi’an 710121, China;
-
Received:2021-11-20Online:2022-03-10Published:2022-03-28 -
Contact:FENG Jingyu E-mail:fengjy@xupt.edu.cn
摘要:
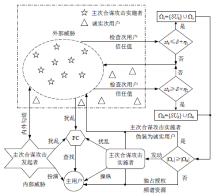
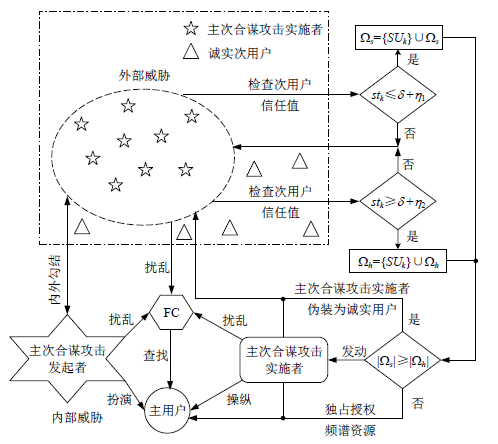
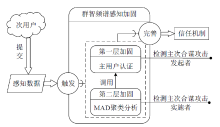
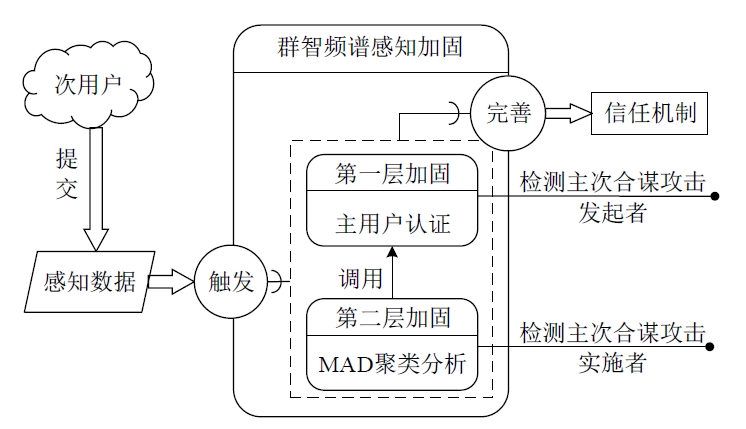
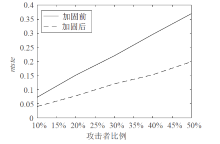
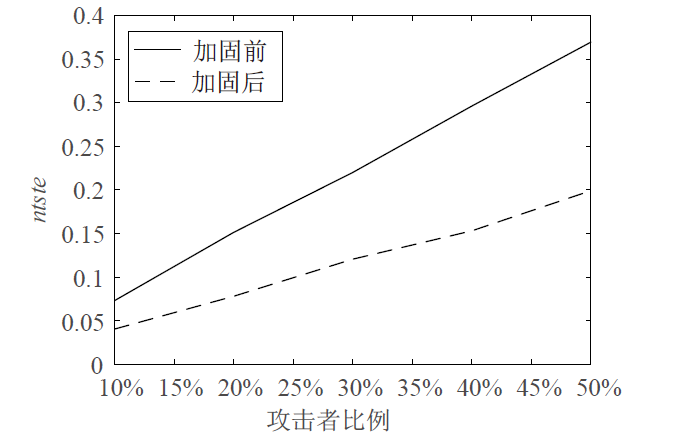
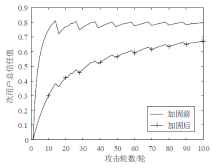
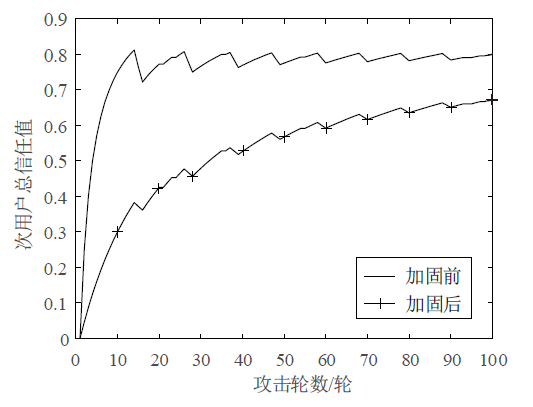
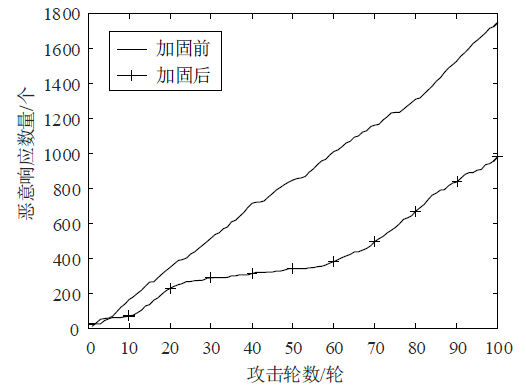
针对智能电网中群智频谱感知易受虚假数据注入攻击的问题,文章提出一种抗主次合谋攻击的群智频谱感知加固方案。该方案首先通过主用户认证构建第一层防御加固,设计基于身份密码的签名方案防止攻击者冒充主用户,引入主用户信任值检测主次合谋发起者;然后设计MAD聚类分析算法,构建第二层防御加固,由关联主用户进行次用户信任计算,使次用户信任由单值演化为多值,形成次用户信任向量,以信任向量距离为识别依据,基于聚类分析检测主次合谋攻击实施者。实验结果表明,该方案可以提高次用户信任评估的准确性,有效降低主次合谋攻击的恶意响应数量。
中图分类号:
引用本文
冯景瑜, 时翌飞, 王腾. 智能电网中抗主次合谋攻击的群智频谱感知加固方案[J]. 信息网络安全, 2022, 22(3): 1-9.
FENG Jingyu, SHI Yifei, WANG Teng. Crowd Spectrum Sensing Reinforcement Scheme Against Primary-secondary Collusive Attack in Smart Grid[J]. Netinfo Security, 2022, 22(3): 1-9.
| [1] | PANG Chuanjun, ZHANG Bo, YU Jianming. Short-term Power Load Forecasting Based on LSTM Recurrent Neural Network[J]. Electric Power Engineering Technology, 2021, 40(1):175-180. |
| 庞传军, 张波, 余建明. 基于LSTM循环神经网络的短期电力负荷预测[J]. 电力工程技术, 2021, 40(1):175-180. | |
| [2] | TAN Xin, HUANG Qiyi, TONG Lin, et al. Comprehensive Benefit Evaluation of the Transnational Power Grid Interconnection Project Based on Improved Matter-element Extension Model[J]. Electric Power Engineering Technology, 2020, 39(6):199-206. |
| 谭鑫, 黄其昱, 仝琳, 等. 基于改进物元可拓法的跨国联网工程综合效益评价[J]. 电力工程技术, 2020, 39(6):199-206. | |
| [3] | YUAN Mingzhe, ZOU Jingxin, WANG Gen, et al. Fault Diagnosis Method for Secondary System of Smart Substation Based on PSO-SVM[J]. Electric Power Engineering Technology, 2020, 39(6):172-176. |
| 袁明哲, 邹经鑫, 汪艮, 等. 基于PSO-SVM的智能变电站二次系统故障诊断方法[J]. 电力工程技术, 2020, 39(6):172-176. | |
| [4] | AMRUTHA V, KARTHIKEYAN K V. Spectrum Sensing Methodologies in Cognitive Radio Networks: A Survey [C]//IEEE. 2017 International Conference on Innovations in Electrical, Electronics, Instrumentation and Media Technology(ICEEIMT), February 3-4, 2017, Coimbatore, India. New Jersey: IEEE, 2017: 306-310. |
| [5] | RAO Xuli, LIN Hui, TIAN Youliang, et al. Research on a Trusted Collaborative Second Users Selection Strategy in Distributed Cognitive Radio Networks[J]. Netinfo Security, 2018, 18(10):37-44. |
| 饶绪黎, 林晖, 田有亮, 等. 分布式认知无线电网络中的一种可信协作次用户选取策略研究[J]. 信息网络安全, 2018, 18(10):37-44. | |
| [6] | ZHANG Damin, WANG Yirou, XU Hang, et al. Spectrum Allocation Strategy Based on Energy Efficiency Optimization in Cognitive Smart Grid[J]. Control and Decision, 2021, 36(8):1901-1910. |
| 张达敏, 王依柔, 徐航, 等. 认知智能电网中基于能效优化的频谱分配策略[J]. 控制与决策, 2021, 36(8):1901-1910. | |
| [7] | LIU Boyang, MA Jie, LI Wei, et al. POMDP Based Resource Allocation for Single-user Cognitive Mobile Edge Computing Networks[J]. Journal of Xi’an University of Posts and Telecommunications, 2021, 26(4):26-33. |
| 刘伯阳, 马杰, 李伟, 等. 基于POMDP的单用户认知移动边缘计算资源分配[J]. 西安邮电大学学报, 2021, 26(4):26-33. | |
| [8] | KHAN A A, REHMANI M H, REISSLEIN M. Cognitive Radio for Smart Grids: Survey of Architectures, Spectrum Sensing Mechanisms, and Networking Protocols[J]. IEEE Communications Surveys & Tutorials, 2016, 18(1):860-898. |
| [9] | XIONG Jinbo, BI Renwan, TIAN Youliang, et al. Security and Privacy in Mobile Crowdsensing: Models, Progress, and Trends[J]. Chinese Journal of Computers, 2021, 44(9):1949-1966. |
| 熊金波, 毕仁万, 田有亮, 等. 移动群智感知安全与隐私:模型、进展与趋势[J]. 计算机学报, 2021, 44(9):1949-1966. | |
| [10] | MA Rong, CHEN Xiuhua, LIU Hui, et al. Research on User Privacy Measurement and Privacy Protection in Mobile Crowdsensing[J]. Netinfo Security, 2018, 18(8):64-72. |
| 马蓉, 陈秀华, 刘慧, 等. 移动群智感知中用户隐私度量与隐私保护研究[J]. 信息网络安全, 2018, 18(8):64-72. | |
| [11] | LI Xiaohui, ZHU Qi, WANG Ying. IRS-assisted Crowd Spectrum Sensing in B5G Cellular IoT Networks[C]//IEEE. 2020 International Conference on Wireless Communications and Signal Processing(WCSP), October 21, 2020, Nanjing, China. New Jersey: IEEE, 2020: 761-765. |
| [12] |
ANSERE J A, HAN Guangjie, WANG Hao, et al. A Reliable Energy Efficient Dynamic Spectrum Sensing for Cognitive Radio IoT Networks[J]. IEEE Internet of Things Journal, 2019, 6(4):6748-6759.
doi: 10.1109/JIoT.6488907 URL |
| [13] |
LUO Tie, HUANG Jianwei, KANHERE S S, et al. Improving IoT Data Quality in Mobile Crowd Sensing: A Cross Validation Approach[J]. IEEE Internet of Things Journal, 2019, 6(3):5651-5664.
doi: 10.1109/JIOT.2019.2904704 |
| [14] |
NAYAK N, RAJ V, KALYANI S. Leveraging Online Learning for CSS in Frugal IoT Network[J]. IEEE Transactions on Cognitive Communications and Networking, 2020, 6(4):1350-1364.
doi: 10.1109/TCCN.6687307 URL |
| [15] | JIANG Jinfang, HAN Guangjie. Survey of Trust Management Mechanism in Wireless Sensor Network[J]. Netinfo Security, 2020, 20(4):12-20. |
| 江金芳, 韩光洁. 无线传感器网络中信任管理机制研究综述[J]. 信息网络安全, 2020, 20(4):12-20. | |
| [16] | GALEAZZI A, BADIA L, CHANG S C, et al. Reputation-based Spectrum Data Fusion Against Falsification Attacks in Cognitive Networks [C]//IEEE. 19th Mediterranean Communication and Computer Networking Conference(MedComNet), June 15-17, 2021, Ibiza, Spain. New Jersey: IEEE, 2021: 1-8. |
| [17] |
FU Yuanhua, HE Zhiming. Bayesian-inference-based Sliding Window Trust Model Against Probabilistic SSDF Attack in Cognitive Radio Networks[J]. IEEE Systems Journal, 2020, 14(2):1764-1775.
doi: 10.1109/JSYST.4267003 URL |
| [18] |
XU Zhenyu, SUN Zhiguo, GUO Lili. Throughput Maximization of Collaborative Spectrum Sensing Under SSDF Attacks[J]. IEEE Transactions on Vehicular Technology, 2021, 70(8):8378-8383.
doi: 10.1109/TVT.2021.3095541 URL |
| [19] | MOROZOV M Y, PERFILOV O Y, MALYAVINA N V, et al. Combined Approach to SSDF-attacks Mitigation in Cognitive Radio Networks [C]//IEEE. 2020 Systems of Signals Generating and Processing in the Field of on Board Communications, March 19-20, 2020, Moscow, Russia. New Jersey: IEEE, 2020: 1-4. |
| [20] | LIU Jia, FU Hongchuan, CHEN Yunhua, et al. A Trust-based Message Passing Algorithm against Persistent SSDF [C]//IEEE. 2020 IEEE 20th International Conference on Communication Technology(ICCT), October 28-31, 2020, Nanning, China. New Jersey: IEEE, 2020: 1112-1115. |
| [21] | SHAMIR A. Identity-based Cryptography[EB/OL]. http://en.wikipedia.org/wiki/ID-based cryptography, 2022-01-12. |
| [22] | JONSSON J, KALISKI B. Public-key Cryptography Standards #1: RSA Cryptography Specifications Version 2.1. Technical Report RFC 3447[EB/OL]. http://wattle.apnic.net/ietf/rfc/PDF/rfc5208.pdf, 2022-01-12. |
| [23] | CHA J C, CHEON J H. An Identity-based Signature from Gap Diffie Hellman Groups [C]//Springer. 6th International Workshop on Practice and Theory in Public Key Cryptography, January 6-8, 2003, Miami, FL, USA. Heidelberg: Springer, 2003: 18-30. |
| [1] | 金志刚, 刘凯, 武晓栋. 智能电网AMI领域IDS研究综述[J]. 信息网络安全, 2023, 23(1): 1-8. |
| [2] | 夏喆, 罗宾, 徐桂彬, 肖新秀. 智能电网中支持细粒度访问控制的隐私保护数据聚合方案[J]. 信息网络安全, 2021, 21(11): 28-39. |
| [3] | 李坤昌, 石润华, 李恩. 智能电网中数据聚合与用户查询隐私保护研究[J]. 信息网络安全, 2021, 21(11): 65-74. |
| [4] | 董威, 李永刚. 基于复杂网络的智能电网网络攻击影响分析研究[J]. 信息网络安全, 2020, 20(1): 52-60. |
| [5] | 刘玉岭, 唐云善, 张琦, 李枫. 电力调度自动化软件安全态势评估方法[J]. 信息网络安全, 2019, 19(8): 15-21. |
| [6] | 周权, 许舒美, 杨宁滨. 一种基于ABGS的智能电网隐私保护方案[J]. 信息网络安全, 2019, 19(7): 25-30. |
| [7] | 黎妹红, 齐小晨, 吴倩倩. 基于动态密钥的智能电网无线通信数据加密传输方案[J]. 信息网络安全, 2019, 19(12): 10-21. |
| [8] | 田秀霞, 陈希, 田福粮. 基于区块链的社区分布式电能安全交易平台方案[J]. 信息网络安全, 2019, 19(1): 51-58. |
| [9] | 陈阳, 王勇. 移动Ad Hoc网络中一种安全的AODV路由协议及性能优化[J]. 信息网络安全, 2018, 18(2): 40-47. |
| [10] | 李梁, 张应辉, 邓恺鑫, 张甜甜. 5G智能电网中具有隐私保护的电力注入系统[J]. 信息网络安全, 2018, 18(12): 87-92. |
| [11] | 陈阳, 王勇, 孙伟. 基于YARN规范的智能电网大数据异常检测[J]. 信息网络安全, 2017, 17(7): 11-17. |
| [12] | 陈颖聪, 陈广清, 陈智明, 万能. 面向智能电网SDN的二进制代码分析漏洞扫描方法研究[J]. 信息网络安全, 2016, 16(7): 35-39. |
| [13] | 刘家男, 翁健. 智能电网安全研究综述[J]. 信息网络安全, 2016, 16(5): 78-84. |
| [14] | 李增鹏, 邹岩, 张磊, 马春光. 一种基于全同态加密的智能电网数据交换隐私保护方案[J]. 信息网络安全, 2016, 16(3): 1-7. |
| [15] | 郑生军, 郭龙华, 陈建, 南淑君. 基于虚拟执行技术的高级恶意软件攻击在线检测系统[J]. 信息网络安全, 2016, 16(1): 29-33. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||