信息网络安全 ›› 2022, Vol. 22 ›› Issue (11): 36-46.doi: 10.3969/j.issn.1671-1122.2022.11.005
SD-IoT中基于设备地址的移动目标防御机制研究
- 1. 天津理工大学计算机科学与工程学院,天津 300384
2. 天津工业大学软件学院,天津 300387
-
收稿日期:2022-07-12出版日期:2022-11-10发布日期:2022-11-16 -
通讯作者:孙士民 E-mail:sunshimin@tiangong.edu.cn -
作者简介:韩俐(1983—),女,内蒙古,副教授,博士,主要研究方向为软件定义安全、软件定义网络、网络空间安全|宋吉祥(1996—),男,河南,硕士研究生,主要研究方向为网络信息安全、移动目标防御|孙士民(1983—),男,山东,副教授,博士,主要研究方向为软件定义网络、网络空间安全、QoS优化算法 -
基金资助:国家自然科学基金(61802281);国家自然科学基金(61702366);国家自然科学基金(61972456);天津市自然科学基金(19JCYBJC15800);专用集成电路与系统国家重点实验室(复旦大学)
Moving Target Defense Mechanism Research Based on Device Address in SD-IoT
HAN Li1, SONG Jixiang1, SUN Shimin2( )
)
- 1. School of Computer Science and Engineering, Tianjin University of Technology, Tianjin 300384, China
2. School of Software, Tiangong University, Tianjin 300387, China
-
Received:2022-07-12Online:2022-11-10Published:2022-11-16 -
Contact:SUN Shimin E-mail:sunshimin@tiangong.edu.cn
摘要:
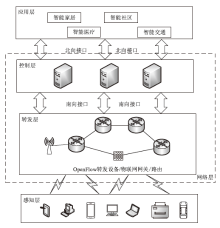
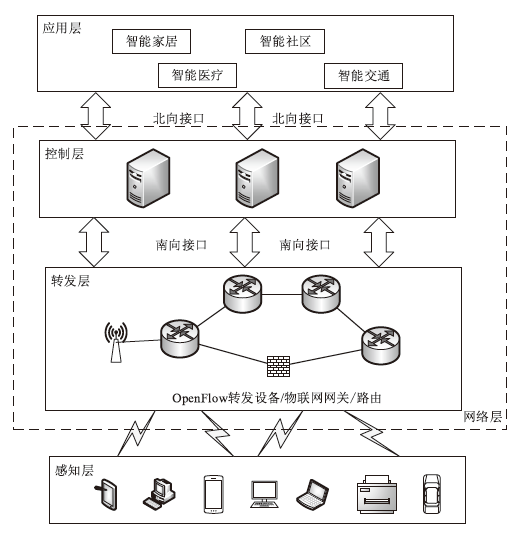
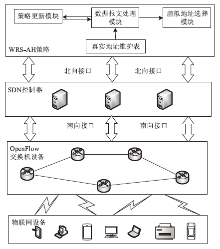
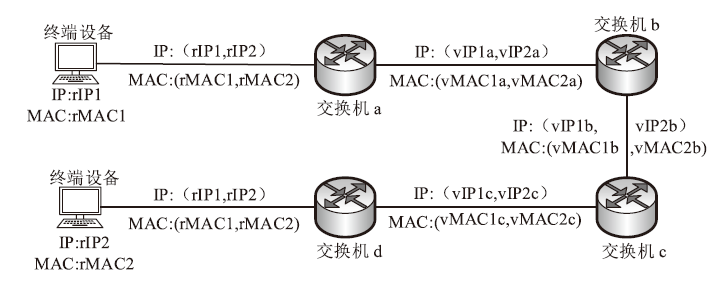
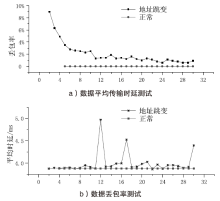
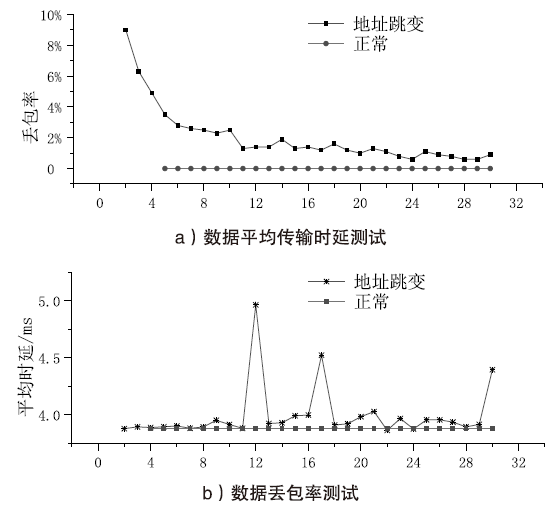
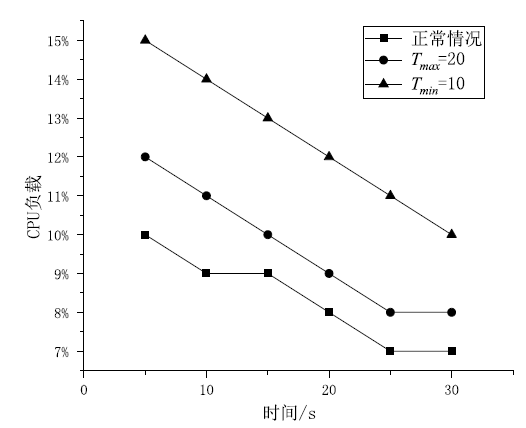
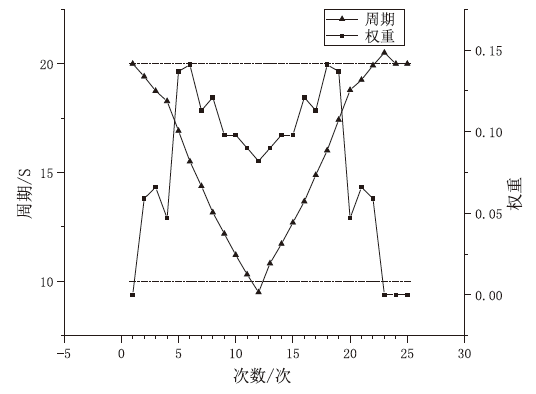
物联网终端设备资源受限与静态配置的特性会导致嗅探攻击对设备地址(IP地址或MAC地址)的窃取或篡改,地址跳变策略通过动态随机化网络设备的地址来抵御攻击者的入侵。文章在软件定义物联网环境下提出一种加权随机选择的设备地址跳变方法,通过对跳变过程中虚拟地址的选择添加重复约束条件,以增强设备地址跳变过程中的不可预测性,抵御嗅探行为的发生;同时,利用SDN控制器集中控制的特性,对物联网终端设备进行检测,以确保地址跳变策略的正常部署;并根据检测结果动态调整地址跳变周期,以提高网络的服务能力与安全性。仿真实验表明,在系统负载5%范围内,该方法能够增强设备地址的不可预测性,并抵御物联网中嗅探与欺骗行为的发生。
中图分类号:
引用本文
韩俐, 宋吉祥, 孙士民. SD-IoT中基于设备地址的移动目标防御机制研究[J]. 信息网络安全, 2022, 22(11): 36-46.
HAN Li, SONG Jixiang, SUN Shimin. Moving Target Defense Mechanism Research Based on Device Address in SD-IoT[J]. Netinfo Security, 2022, 22(11): 36-46.
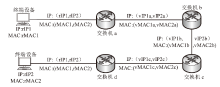
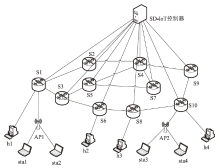
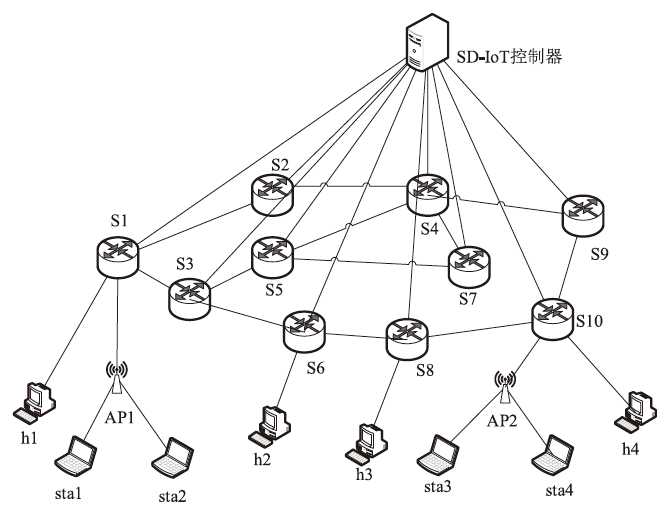
表1
嗅探攻击者获取的链路地址信息
| 链路 | 地址信息 |
|---|---|
| S1→S3 | 源IP:10.0.0.56 源MAC:00:00:00:88:c1:e4 目的IP:10.0.0.65 目的MAC:00:00:00:57:ca:fb |
| S3→S5 | 源IP:10.0.0.108 源MAC:00:00:00:4c:53:ca 目的IP:10.0.0.57 目的MAC:00:00:00:28:91:72 |
| S5→S7 | 源IP:10.0.0.92 源MAC:00:00:00:a8:2b:0e 目的IP:10.0.0.50 目的MAC:00:00:00:64:e0:43 |
| S7→S4 | 源IP:10.0.0.73 源MAC:00:00:00:c4:d0:87 目的IP:10.0.0.15 目的MAC:00:00:00:99:2a:80 |
| S4→S9 | 源IP:10.0.0.54 源MAC:00:00:00:cc:41:a3 目的IP:10.0.0.152 目的MAC:00:00:00:eb:74:9a |
| S9→S10 | 源IP:10.0.0.25 源MAC:00:00:00:d8:e8:c2 目的IP:10.0.0.146 目的MAC:00:00:00:49:dc:47 |
| [1] |
GUBBI J, BUYYA R, MARUSIC S, et al. Internet of Things (IoT): A Vision Architectural Elements and Future Directions[J]. Future Generation Computer Systems, 2013, 29(7): 1645-1660.
doi: 10.1016/j.future.2013.01.010 URL |
| [2] | VAILSHERY L S. IoT and Non-IoT Connections Worldwide 2010-2025[EB/OL]. (2021-03-08)[2022-06-10]. . |
| [3] | JIAN M S, WU J M T. Hybrid Internet of Things (IoT) Data Transmission Security Corresponding to Device Verification[EB/OL]. (2021-03-30)[2022-06-10]. . |
| [4] |
ANTHI E, AHMAD S, RANA O, et al. EclipseIoT: A Secure and Adaptive Hub for the Internet of Things[J]. Computers & Security, 2018, 78: 477-490.
doi: 10.1016/j.cose.2018.07.016 URL |
| [5] |
IQBAL W, ABBAS H, DANESHMAND M, et al. An In-Depth Analysis of IoT Security Requirements, Challenges, and their Countermeasures via Software-Defined Security[J]. IEEE Internet of Things Journal, 2020, 7(10): 10250-10276.
doi: 10.1109/JIOT.2020.2997651 URL |
| [6] |
LIU Gang, QUAN Wei, CHENG Nan, et al. Softwarized IoT Network Immunity Against Eavesdropping with Programmable Data Planes[J]. IEEE Internet of Things Journal, 2021, 8(8): 6578-6590.
doi: 10.1109/JIOT.2020.3048842 URL |
| [7] |
TAN S Y, YEOW K W, HWANG S O. Enhancement of a Lightweight Attribute-Based Encryption Scheme for the Internet of Things[J]. IEEE Internet of Things Journal, 2019, 6(4): 6384-6395.
doi: 10.1109/JIOT.2019.2900631 URL |
| [8] | ZHANG Yuntong, XU Jingye, WANG Zhiwei, et al. Efficient and Intelligent Attack Detection in Software Defined IoT Networks[C]// IEEE. 2020 IEEE International Conference on Embedded Software and Systems (ICESS). New York:IEEE, 2020: 1-9. |
| [9] |
ESKANDARI M, JANJUA Z H, VECCHIO M, et al. Passban IDS: An Intelligent Anomaly-Based Intrusion Detection System for IoT Edge Devices[J]. IEEE Internet of Things Journal, 2020, 7(8): 6882-6897.
doi: 10.1109/JIOT.2020.2970501 URL |
| [10] | ZHOU Yuyang, CHENG Guang, GUO Chunsheng, et al. Survey on Attack Surface Dynamic Transfer Technology Based on Moving Target Defense[J]. Journal of Software, 2018, 29(9): 2799-2820. |
| 周余阳, 程光, 郭春生, 等. 移动目标防御的攻击面动态转移技术研究综述[J]. 软件学报, 2018, 29(9):2799-2820. | |
| [11] | ZHANG Chaokun, CUI Yong, TANG Heyi, et al. State-of-the-Art Survey on Software-Defined Networking (SDN)[ J]. Journal of Software, 2015, 26(1): 62-81. |
| 张朝昆, 崔勇, 唐翯祎, 等. 软件定义网络(SDN)研究进展[J]. 软件学报, 2015, 26(1):62-81. | |
| [12] |
CHEN Liang, LI Feng, REN Baoquan, et al. Software-Defined Internet of Things: A Survey[J]. Acta Electronica Sinica, 2021, 49(5): 1019-1032.
doi: 10.12263/DZXB.20200561 |
|
陈亮, 李峰, 任保全, 等. 软件定义物联网研究综述[J]. 电子学报, 2021, 49(5):1019-1032.
doi: 10.12263/DZXB.20200561 |
|
| [13] | OJO M, ADAMI D, GIORDANO S. A SDN-IoT Architecture with NFV Implementation[C]// IEEE.2016 IEEE Globecom Workshops (GC Wkshps). New York:IEEE, 2016: 1-6. |
| [14] |
LIU Xiangju, LIU Pengcheng, XU Hui, et al. Distributed Denial of Service Attack Detection Method Based on Software Defined Internet of Things[J]. Journal of Computer Applications, 2020, 40(3): 753-759.
doi: 10.11772/j.issn.1001-9081.2019091611 |
|
刘向举, 刘鹏程, 徐辉, 等. 基于软件定义物联网的分布式拒绝服务攻击检测方法[J]. 计算机应用, 2020, 40(3):753-759.
doi: 10.11772/j.issn.1001-9081.2019091611 |
|
| [15] |
NAVAS R E, CUPPENS F, CUPPENS N B, et al. MTD, Where Art Thou? A Systematic Review of Moving Target Defense Techniques for IoT[J]. IEEE Internet of Things Journal, 2021, 8(10): 7818-7832.
doi: 10.1109/JIOT.2020.3040358 URL |
| [16] |
KARMAKAR K K, VARADHARAJAN V, NEPAL S, et al. SDN-Enabled Secure IoT Architecture[J]. IEEE Internet of Things Journal, 2021, 8(8): 6549-6564.
doi: 10.1109/JIOT.2020.3043740 URL |
| [17] |
MERCADO-VELÁZQUEZ A A, ESCAMILLA-AMBROSIO P J, ORTIZ-RODRÍGUEZ F. A Moving Target Defense Strategy for Internet of Things Cybersecurity[J]. IEEE Access, 2021, 9: 118406-118418.
doi: 10.1109/ACCESS.2021.3107403 URL |
| [18] |
NIZZI F, PECORELLA T, ESPOSITO F, et al. IoT Security via Address Shuffling: The Easy Way[J]. IEEE Internet of Things Journal, 2019, 6(2): 3764-3774.
doi: 10.1109/JIOT.2019.2892003 |
| [19] | ALMOHAIMEED A, GAMPA S, SINGH G. Privacy-Preserving IoT Devices[C]// IEEE. 2019 IEEE Long Island Systems, Applications and Technology Conference (LISAT). New York:IEEE, 2019: 1-5. |
| [20] | PAPPA A C, ASHOK A, GOVINDARASU M. Moving Target Defense for Securing Smart Grid Communications: Architecture, Implementation & Evaluation[C]// IEEE. 2017 IEEE Power & Energy Society Innovative Smart Grid Technologies Conference (ISGT). New York:IEEE, 2017: 1-5. |
| [21] |
HE Yun, ZHANG Min, YANG Xiaolong, et al. The Intelligent Offense and Defense Mechanism of Internet of Vehicles Based on the Differential Game-IP Hopping[J]. IEEE Access, 2020, 8: 115217-115227.
doi: 10.1109/ACCESS.2020.3004255 URL |
| [22] | LI Zhaoyang, TAN Jinglei, HU Ruiqin, et al. Moving Target Defense Method Based on Double Address Hopping[J]. Netinfo Security, 2021, 21(2): 24-33. |
| 李朝阳, 谭晶磊, 胡瑞钦, 等. 基于双重地址跳变的移动目标防御方法[J]. 信息网络安全, 2021, 21(2):24-33. | |
| [23] | HU Ruiqin, TAN Jinglei, PENG Xinhe, et al. Dynamic Hopping Technology of Double Virtual IP Address for SDN Data Layer[J]. Netinfo Security, 2022, 22(2): 76-85. |
| 胡瑞钦, 谭晶磊, 彭心荷, 等. 面向SDN数据层的双虚假IP地址动态跳变技术[J]. 信息网络安全, 2022, 22(2):76-85. | |
| [24] | SANABRIA-RUSSO L, ALONSO-ZARATE J, VERIKOUKIS C. SDN-Based Pro-Active Flow Installation Mechanism for Delay Reduction in IoT[C]// IEEE. 2018 IEEE Global Communications Conference (GLOBECOM). New York:IEEE, 2018: 1-6. |
| [25] | FONTES R R, AFZAL S, BRITO S H B, et al. Mininet-WiFi: Emulating Software-Defined Wireless Networks[C]// IEEE. 2015 11th International Conference on Network and Service Management (CNSM). New York:IEEE, 2015: 384-389. |
| [26] | LI Zhenyu, DING Yong, YUAN Fang, et al. An Integrated Protection Method of Moving Target Defense and Access Control Based on IPv6 Network[J]. Journal of Computer Research and Development, 2022, 59(5): 1105-1119. |
| 李振宇, 丁勇, 袁方, 等. 基于IPv6网络的移动目标防御与访问控制融合防护方法[J]. 计算机研究与发展, 2022, 59(5):1105-1119. |
| [1] | 胡瑞钦, 谭晶磊, 彭心荷, 张红旗. 面向SDN数据层的双虚假IP地址动态跳变技术[J]. 信息网络安全, 2022, 22(2): 76-85. |
| [2] | 左黎明, 夏萍萍, 陈祚松. 基于国密SM2数字签名的网络摄像头保护技术[J]. 信息网络安全, 2018, 18(5): 32-40. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||