信息网络安全 ›› 2020, Vol. 20 ›› Issue (11): 15-21.doi: 10.3969/j.issn.1671-1122.2020.11.003
等级保护测评模拟环境设计与实践
- 公安部信息安全等级保护评估中心,北京 100142
Design and Practice of Simulation Environment for Cyber Security Classified Protection Evaluation
ZHENG Guogang( ), YIN Xiangpei, WANG Kui, HE Kunpeng
), YIN Xiangpei, WANG Kui, HE Kunpeng
- MPS Information Security Classified Protection Evaluation Center, Beijing 100142, China
摘要:
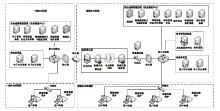
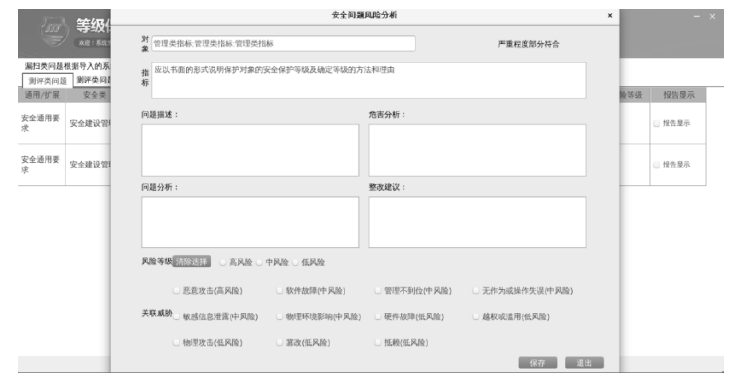
文章详细介绍了一个以办公自动化系统为原型,涵盖等级保护二级、三级区域的模拟环境和等级测评实践活动。模拟环境中设计有办公自动化应用场景和安全防护场景,其中安全防护措施按照2019年颁布的《网络安全等级保护基本要求》进行设计部署,安全策略可以根据实践活动的需要进行配置。通过对模拟环境进行等级测评实操活动,可以了解等级测评现场技术测评的主要工作过程和安全分析方法,比较安全防护措施的效果,验证安全防护策略配置的重要性,同时通过模拟环境可以进一步研究并优化相关安全设计方案,验证安全设备部署、安全策略配置的有效性。
中图分类号: