信息网络安全 ›› 2020, Vol. 20 ›› Issue (8): 55-61.doi: 10.3969/j.issn.1671-1122.2020.08.007
云环境中基于分组的安全虚拟机放置方法
- 四川大学网络空间安全学院,成都 610041
-
收稿日期:2020-05-15出版日期:2020-08-10发布日期:2020-10-20 -
通讯作者:王运鹏 E-mail:haocwy@126.com -
作者简介:陈婉莹(1996—),女,四川,硕士研究生,主要研究方向为云计算|王运鹏(1984—),男,四川,博士研究生,主要研究方向为信息安全、区块链|赵珂雨(1996—),女,四川,硕士研究生,主要研究方向为计算机网络与信息安全|刘晓洁(1965—),女,江苏,教授,硕士,主要研究方向为网络信息对抗与保护技术、数字虚拟资产保护技术。 -
基金资助:国家自然科学基金(U1736212);国家自然科学基金(U19A2068);四川省重点研发项目(2018GZ0183);四川省重点研发项目(20ZDYF3145)
Secure Virtual Machine Placement Method Based on Grouping in Cloud Environment
CHEN Wanying, WANG Yunpeng( ), ZHAO Keyu, LIU Xiaojie
), ZHAO Keyu, LIU Xiaojie
- College of Cybersecurity, Sichuan University, Chengdu 610041, China
-
Received:2020-05-15Online:2020-08-10Published:2020-10-20 -
Contact:WANG Yunpeng E-mail:haocwy@126.com
摘要:
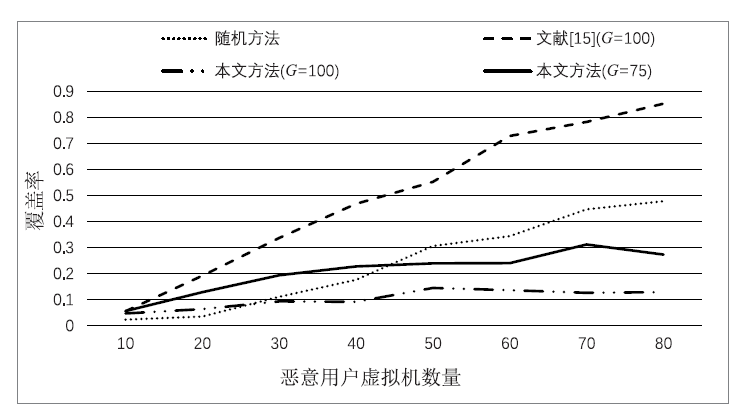
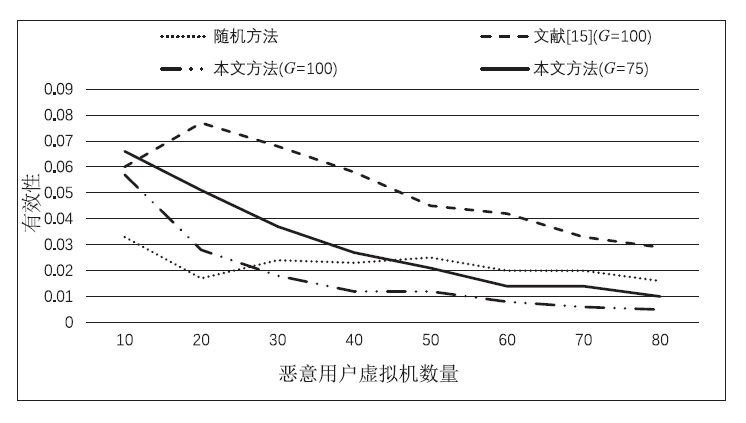
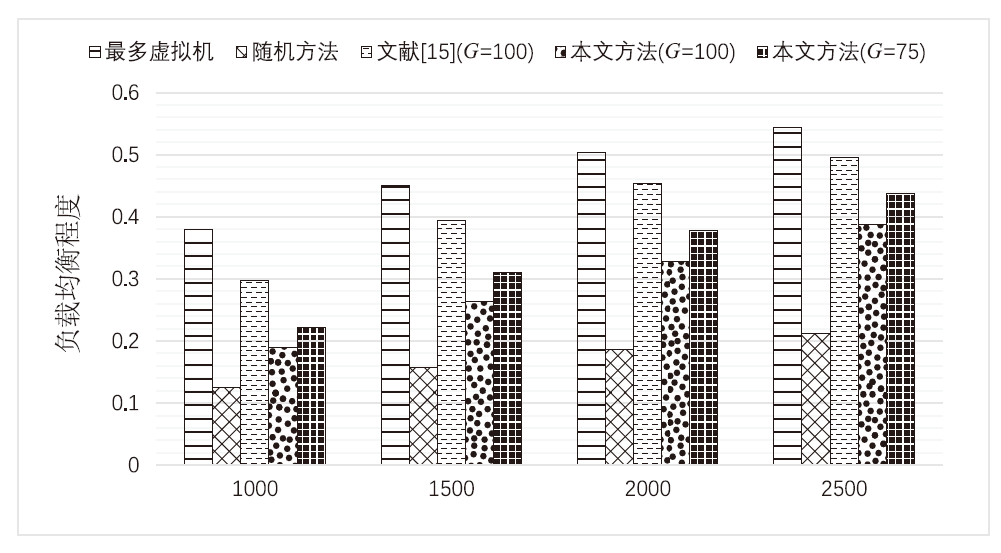
在云环境中,通常将不同用户的虚拟机放置在同一台物理机上,这种物理资源的共享对用户的隐私数据构成了严重威胁。恶意用户可以通过启动大量虚拟机或者利用虚拟机放置策略存在的漏洞提高与目标虚拟机共存的概率。为了进行主动防御,文章提出一种在考虑安全性的同时也关注能耗以及负载均衡的放置方法。将虚拟机以相同的概率进行随机分组,以防止恶意用户获取并利用虚拟机在放置位置上表现出的特征;为了减小恶意用户通过启动过多虚拟机以增大与目标虚拟机共存的概率,当某个用户的虚拟机分配的组数超过阈值后,将不被分配新的组;综合考虑能耗和负载均衡的情况,将其分配到合适的物理机上。实验结果表明,文章在考虑负载和能耗的基础上,减少了不同用户虚拟机之间共存的概率,增强了虚拟机放置的安全性。
中图分类号:
引用本文
陈婉莹, 王运鹏, 赵珂雨, 刘晓洁. 云环境中基于分组的安全虚拟机放置方法[J]. 信息网络安全, 2020, 20(8): 55-61.
CHEN Wanying, WANG Yunpeng, ZHAO Keyu, LIU Xiaojie. Secure Virtual Machine Placement Method Based on Grouping in Cloud Environment[J]. Netinfo Security, 2020, 20(8): 55-61.
表1
主要的符号定义和描述
| 符号 | 描述 |
|---|---|
| M | 全部的物理机集合 |
| m | 物理机数量 |
| V | 全部的虚拟机集合 |
| H | 所有用户的集合 |
| Vi | 第i个虚拟机 |
| Pj | 第j个物理机 |
| Hk | 第k个用户 |
| $V_{i}^{\text{cpu}}$,$V_{i}^{\text{men}}$ | 表示虚拟机Vi的资源需求情况 |
| $AV{{G}^{\text{cpu}}}$,$AV{{G}^{\text{men}}}$ | 各个物理机的平均CPU利用率、内存利用率 |
| $PA_{j}^{\text{cpu}}$,$PA_{j}^{\text{men}}$ | 表示物理机Pj的CPU利用率、内存利用率 |
| $P_{j}^{\text{full}}$ | 物理机Pj满载时的功率 |
| [1] | LUO Junzhou, JIN Jiahui, SONG Aibo, et al. Cloud Computing: Architecture and Key Technologies[J]. Journal on Communications, 2011. 32(7):3-21. |
| 罗军舟, 金嘉晖, 宋爱波, 等. 云计算:体系架构与关键技术[J]. 通信学报, 2011,32(7):3-21. | |
| [2] | RISTENPART T, TROMER E, SHACHAM H, et al. Hey, You, Get off of My Cloud: Exploring Information Leakage in Third-Party Compute Clouds[C]// ACM. ACM Conference on Computer and Communications Security, November 9-13, 2009, Chicago, IL, USA. New York: ACM, 2009: 199-212. |
| [3] | LIANG Xin, GUI Xiaolin, DAI Huijun, et al. Cross VM Cache Side Channel Attacks in Cloud:A Survey[J]. Chinese Journal of Computers, 2017,40(2):317-336. |
| 梁鑫, 桂小林, 戴慧珺, 等. 云环境中跨虚拟机的Cache侧信道攻击技术研究[J]. 计算机学报, 2017,40(2):317-336. | |
| [4] | ZHANG Yinqian, JUEKS A, REITER M K, et al. Cross-VM Side Channels and Their Use to Extract Private Keys[C]// ACM. ACM Conference on Computer and Communications Security, October 16-18, 2012, Raleigh, NC, USA. New York: ACM, 2012: 305-316. |
| [5] | HAN Yi, JEFFREY C, ALPCAN T, et al. Using Virtual Machine Allocation Policies to Defend against Co-Resident Attacks in Cloud Computing[J]. IEEE Transactions on Dependable and Secure Computing, 2017,14(1):95-108. |
| [6] | MOHAMED M S E, BULYGIN S, ZOHNER M, et al. Improved Algebraic Side-Channel Attack on AES[J]. Journal of Cryptographic Engineering, 2013,3(3):139-156. |
| [7] | YAO Jianbo, ZHANG Tao. Safe and Effective Elliptic Encryption Algorithm Resistance against Side-Channel Attack[J]. Application Research of Computers, 2019,29(12):4639-4643. |
| 姚剑波, 张涛. 抗侧信道攻击的安全有效椭圆加密算法[J]. 计算机应用研究, 2012,29(12):4639-4643. | |
| [8] | LIU Weijie. Attack, Detection and Defense of Cross Virtual Machine Side Channel in Cloud Computing Environment[D]. Wuhan: WUHAN University, 2018. |
| 刘维杰. 云计算环境下跨虚拟机侧信道的攻击、检测与防御[D]. 武汉:武汉大学, 2018. | |
| [9] | PENG Shuanghe, TUERGONG Maitisabier, JIN Fu. Research on Xen Virtual Machine Scheduling Strategy to Mitigate Covert Side Attacks[J]. Engineering Journal of Wuhan University, 2018,51(4):371-376. |
| 彭双和, 图尔贡·麦提萨比尔, 金傳, 针对减弱隐蔽信道攻击的Xen虚拟机调度策略[J]. 武汉大学学报(工学版), 2018,51(4):371-376. | |
| [10] | XING Chaochao. Research on System Level Defense Method of Cache Side Channel Based on vcpu Scheduling[D]. Hefei: University of Science and Technology of China, 2019. |
| 邢超超. 基于vCPU调度的Cache侧信道系统级防御方法研究[D]. 合肥:中国科学技术大学, 2019. | |
| [11] | XU Zhang, WANG Haining, WU Zhenyu. A Measurement Study on Co-residence Threat inside the Cloud[C]// USENIX. USENIX Security Symposium, August 12-14, 2015, Washington, DC, USA. Berkley: USENIX Association, 2015: 929-944. |
| [12] | MOONS, SEKAR V, REITER M K. Nomad: Mitigating Arbitrary Cloud Side Channels via Provider-Assisted Migration[C]// ACM. ACM SIGSAC Conference on Computer and Communications Security, October 12-16, 2015, Denver, CO, USA. New York: ACM, 2015: 1595-1606. |
| [13] | ZHAO Shuo, JI Xinsheng, MAO Yuxing, et al. Research on Dynamic Migration of Virtual Machine Based on Security Level[J]. Journal on Communications, 2017,38(7):165-174. |
| 赵硕, 季新生, 毛宇星, 等. 基于安全等级的虚拟机动态迁移方法[J]. 通信学报, 2017,38(7):165-174. | |
| [14] | HUANG Kaizhi, PAN Qirun, YUAN Quan, et al. A Virtual Node Migration Method for Sensing Side-channel Risk[J]. Journal of Electronics & Information Technology, 2019,41(9):2164-2171. |
| 黄开枝, 潘启润, 袁泉, 等. 一种侧信道风险感知的虚拟节点迁移方法[J]. 电子与信息学报, 2019,41(9):2164-2171. | |
| [15] | LIANG Xin, GUI Xiaolin, JIANA. N, et al. Mitigating Cloud Co-Resident Attacks via grouping-Based Virtual Machine Placement Strategy[C]// IEEE. IEEE International Performance Computing and Communications Conference, December 10-12, 2017, San Diego, CA, USA. New York: IEEE, 2017: 1-8. |
| [16] | ZHANG Miao, JI Xinsheng, LIU Wenyan, et al. Research on Active Defense Against Co-Resident Attack Based on Dynamic Placement Strategies[J]. Journal of Information Engineering University, 2018,19(3):257-263. |
| 张淼, 季新生, 刘文彦, 等. 基于放置策略动态化的共存攻击主动防御方法[J]. 信息工程大学学报, 2018,19(3):257-263. | |
| [17] | VARADARA J, ZHANG Yinqian, RISTEN P, et al. A Placement Vulnerability Study in Multi-Tenant Public Clouds[C]// USENIX. USENIX Security Symposium, August 12-14, 2015, Washington, DC, USA. Berkley: USENIX Association, 2015: 913-928. |
| [18] | LUO Yang, SHEN Qingni, LI Cong, et al. Probing the Scheduling Algorithms in the Cloud Based on Openstack[C]// Springer. International Conference on Cloud Computing and Security, August 13-15,Nanjing, China.Berlin: Springer, 2015: 510-520. |
| [19] | OUSMANE S B, MBACKE B C S, IBRAHIMA N. A Game Theoretic Approach for Virtual Machine Allocation Security in Cloud Computing[C]// ACM. International Conference on Networking, March 27-19, 2019, Rabat, Morocco. New York: ACM, 2019: 1-8. |
| [20] | BELOGLAZOV A, BUYYA R. Energy Efficient Resource Management in Virtualized Cloud Data Centers[C]// IEEE. IEEE/ACM International Symposium on Cluster, Cloud, and Grid Computing, May 17-20, 2010, Melbourne, VIC, Australia. New York: IEEE, 2010: 826-831. |
| [1] | 陈亚楠, 梅倩, 熊虎, 徐维祥. 适用于工业物联网的无证书并行密钥隔离签名[J]. 信息网络安全, 2018, 18(10): 1-9. |
| [2] | 闫玺玺, 刘媛, 胡明星, 黄勤龙. 云环境下基于LWE的多机构属性基加密方案[J]. 信息网络安全, 2017, 17(9): 128-133. |
| [3] | 闫玺玺, 刘媛, 李子臣, 黄勤龙. 云环境下理想格上的多机构属性基加密隐私保护方案[J]. 信息网络安全, 2017, 17(8): 19-25. |
| [4] | 闫玺玺, 叶青, 刘宇. 云环境下支持隐私保护和用户撤销的属性基加密方案[J]. 信息网络安全, 2017, 17(6): 14-21. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||