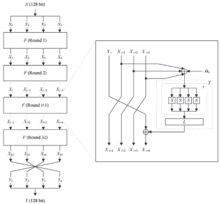
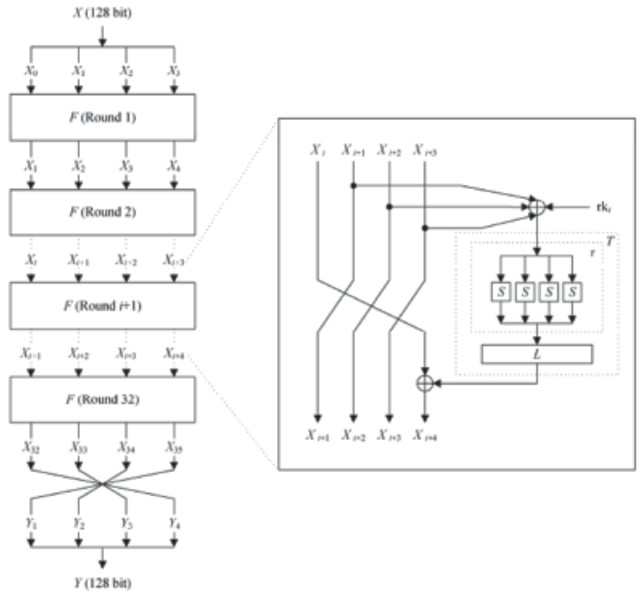
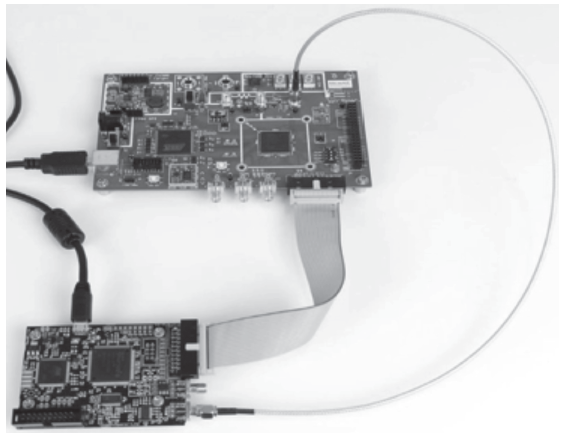
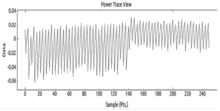
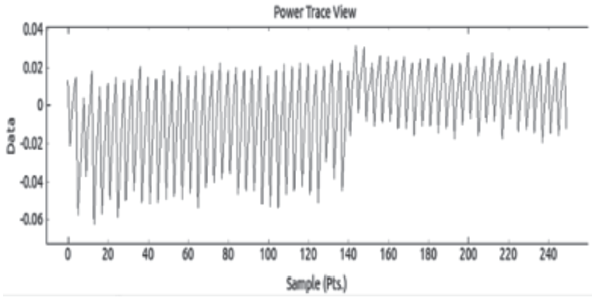
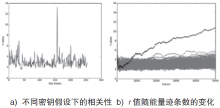
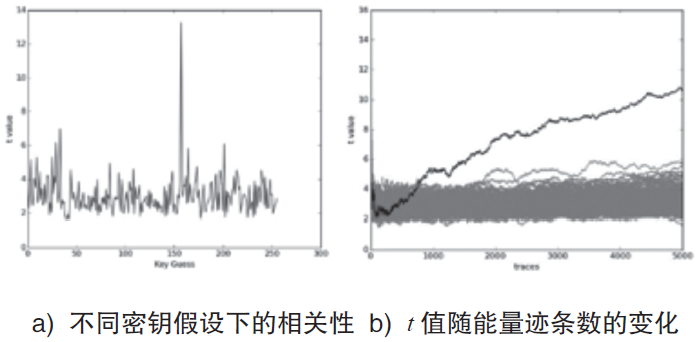
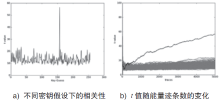
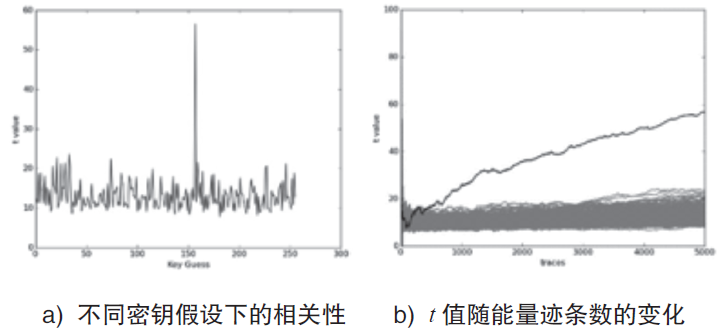
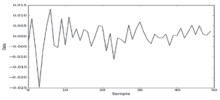
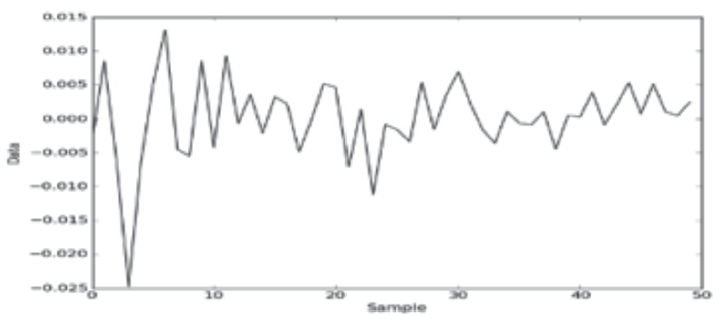
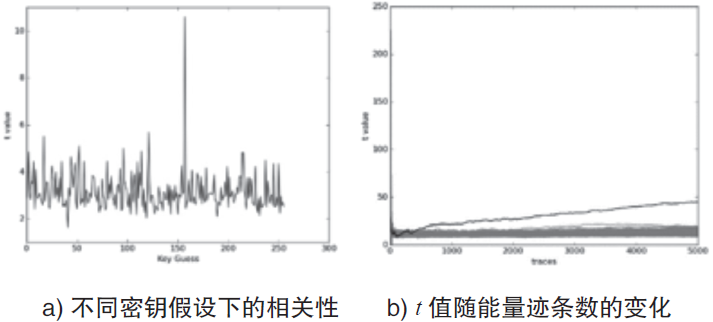
| [1] |
KOCHER P.Timing Attacks on Implementations of Diffie-Hellman, RSA, DSS, and Other Systems[C]//IACR.Annual International Cryptology Conference,August 18-22, 1996,Santa Barbara, California, USA.Berlin, Heidelberg:Springer, 1996: 104-113.
|
| [2] |
KOCHER P, JAFFE J, JUN B.Differential Power Analysis[C]//IACR. Annual International Cryptology Conference, August 15-19, 1999, Santa Barbara, California, USA. Berlin, Heidelberg:Springer, 1999: 388-397.
|
| [3] |
WEN Weiping, GUO Ronghua, MENG Zheng, et al.Research and Implementation on Information Security Risk Assessment Key Technology[J]. Netinfo Security, 2015 (2): 7-14.
|
|
文伟平,郭荣华,孟正,等. 信息安全风险评估关键技术研究与实现[J]. 信息网络安全,2015(2):7-14.
|
| [4] |
KELSEY J, SCHNEIER B, WAGNER D, et al.Side Channel Cryptanalysis of Product Ciphers[C]//IACR. European Symposium on Research in Computer Security, September 16-18, 1998, Belgium. Berlin, Heidelberg:Springer, 1998: 97-110.
|
| [5] |
ZHANG Ping, CHEN Changsong,Hu Honggang.Authenticated Encryption Modes Based on Block Ciphers[J]. Netinfo Security, 2014(11): 8-17.
|
|
张平,陈长松,胡红钢. 基于分组密码的认证加密工作模式[J]. 信息网络安全,2014(11):8-17.
|
| [6] |
BRIER E, CLAVIER C, OLIVIER F.Correlation Power Analysis with a Leakage Model[C]//IACR. International Workshop on Cryptographic Hardware and Embedded Systems, August 11-13, 2004, MA, USA. Berlin, Heidelberg: Springer, 2004: 16-29.
|
| [7] |
CHARI S, RAO J R, ROHATGI P.Template Attacks[C]//IACR. International Workshop on Cryptographic Hardware and Embedded Systems,August 13-15, 2002, CA, USA. Berlin, Heidelberg:Springer, 2002: 13-28.
|
| [8] |
国家商用密码管理办公室. 无线局域网产品使用的SMS4密码算法[EB/OL]. ,2016-5-3.
|
| [9] |
WANG S, GU D, LIU J, et al.A Power Analysis on SMS4 Using the Chosen Plaintext Method[C]//IEEE. 2013 9th International Conference on Computational Intelligence and Security (CIS), December 14-15. 2013, Leshan, China. New York:IEEE, 2013: 748-752.
|
| [10] |
SHAN W, WANG L, LI Q, et al.A Chosen-plaintext Method of CPA on SM4 Block Cipher[C]//IEEE. 2014 Tenth International Conference on Computational Intelligence and Security (CIS), November 15-16. 2014, Kunming, China. New York:IEEE, 2014: 363-366.
|
| [11] |
TANG S, WU L, ZHANG X, et al.A Novel Method of Correlation Power Analysis on SM4 Hardware Implementation[C]//IEEE. 2016 12th International Conference on Computational Intelligence and Security (CIS), December 16-19, 2016, Wuxi, China. New York:IEEE, 2016: 203-207.
|
| [12] |
ZHANG Z, WU L, WANG A, et al.A Novel Bit Scalable Leakage Model Based on Genetic Algorithm[J]. Security and Communication Networks, 2015, 8(18): 3896-3905.
|
| [13] |
DU Zhibo, WU Zhen, WANG Min, et al.Improved Chosen-plaintext Power Analysis Attack Against SM4 at the Round-output[J]. Journal on Communications, 2015, 36(10):85-91.
|
|
杜之波, 吴震, 王敏, 等. 针对SM4 轮输出的改进型选择明文功耗分析攻击[J]. 通信学报, 2015, 36(10): 85-91.
|
| [14] |
ZHANG Jianbiao, ZHAO Zixiao, HU Jun, et al.The Design Framework of Reconfigurable Virtual Root of Trust in Cloud Environment[J]. Netinfo Security, 2018(1): 1-8.
|
|
张建标, 赵子枭, 胡俊, 等. 云环境下可重构虚拟可信根的设计框架[J]. 信息网络安全, 2018(1): 1-8.
|
| [15] |
O'FLYNN C, CHEN Z D. Chipwhisperer: An Open-source Platform for Hardware Embedded Security Research[C]//IEEE International Workshop on Constructive Side-channel Analysis and Secure Design, April 13-15, 2014, Paris, France.Berlin, Heidelberg: Springer,2014: 243-260.
|
 )
)