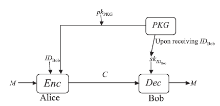
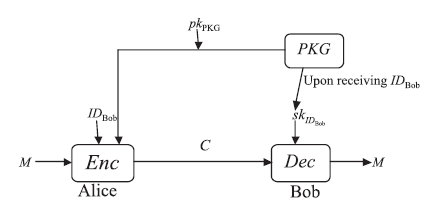
信息网络安全 ›› 2015, Vol. 15 ›› Issue (10): 32-39.doi: 10.3969/j.issn.1671-1122.2015.10.005
基于大整数分解的身份加密体制研究
- 广州大学数学与信息科学学院,广东广州510006
-
收稿日期:2015-07-03出版日期:2015-10-01发布日期:2015-11-04 -
作者简介:作者简介: 刘锦刚(1989-),男,河南,硕士研究生,主要研究方向:公钥密码学;董军武(1971-),男,河南,副教授,博士,主要研究方向:公钥密码学。
-
基金资助:国家自然科学基金[11371106];广州市属高校科技项目[1201420765]
Research on Identity-based Encryptions from Large Integer Factorization
- College of Mathematics & Information Science, Guangzhou University, Guangzhou Guangdong 510006, China
-
Received:2015-07-03Online:2015-10-01Published:2015-11-04
摘要:
近年来,基于身份的密码体制研究受到了广泛关注。不同于传统公钥密码体制,基于身份的加密体制(IBE)可直接利用用户的身份标识作为公钥,不需要使用数字证书,密钥管理简单,这使其成为公钥加密领域的一个研究热点。目前,已有的身份加密体制大多是基于椭圆曲线上的双线性对来构造的,然而双线性群上的乘法和指数运算较慢,参数选择过于复杂,导致计算效率较低,这使得基于双线性对构造的身份加密方案难以走向实用。传统公钥密码体制所依赖的标准大整数分解问题计算效率较好,是用于构造安全实用的基于身份的加密体制的另一个方向。文章综述了基于大整数分解的身份加密体制的最新研究进展,概述了基于身份的加密体制的定义和安全模型,总结了基于身份的加密体制的研究现状;对几种典型的基于大整数分解的身份加密算法进行了对比、分析,总结各算法的优劣;对基于身份的加密体制中存在的热点问题进行剖析,并提出有价值的问题供进一步研究。
中图分类号:
引用本文
刘锦刚, 董军武. 基于大整数分解的身份加密体制研究[J]. 信息网络安全, 2015, 15(10): 32-39.
Jin-gang LIU, Jun-wu DONG. Research on Identity-based Encryptions from Large Integer Factorization[J]. Netinfo Security, 2015, 15(10): 32-39.
| [1] | Diffie W, Hellman M E.New directions in cryptography[J]. IEEE Transactions on Information Theory, 1976, 22(6): 644-654. |
| [2] | Rivest R L, Shamir A, Adleman L.A method for obtaining digital signatures and public-key cryptosystems[J]. Communications of the ACM, 1978, 21(2): 120-126. |
| [3] | Rabin M O.Digitalized signatures and public-key functions as intractable as factorization[R].MASSACHUSETTS INST OF TECH CAMBRIDGE LAB FOR COMPUTER SCIENCE, 1979. |
| [4] | ElGamal T. A public key cryptosystem and a signature scheme based on discrete logarithms[C]//Advances in Cryptology. Springer Berlin Heidelberg, 1985: 10-18. |
| [5] | Miller V.Use of elliptic curves in cryptography[C]//Advances in Cryptology—CRYPTO’85 Proceedings. Springer Berlin Heidelberg, 1986: 417-426. |
| [6] | 徐权佐,蔡庆军. 一种基于编码的公钥密码体制的参数选择研究[J]. 信息网络安全,2014,(10):54-58. |
| [7] | Shamir A.Identity-based cryptosystems and signature schemes[C]//Advances in cryptology. Springer Berlin Heidelberg, 1985: 47-53. |
| [8] | Boneh D, Franklin M. Identity-based encryption from the Weil pairing[C]//Kilian J. (ed.) CRYPTO 2001. LNCS, vol. 2139, pp. 213-229. Springer, Berlin. |
| [9] | Bellare M, Rogaway P.Random oracles are practical: A paradigm for designing efficient protocols[C]//Proceedings of the 1st ACM conference on Computer and communications security. ACM, 1993: 62-73. |
| [10] | Boneh D, Boyen X.Efficient selective-ID secure identity-based encryption without random oracles[C]//Advances in Cryptology-EUROCRYPT 2004. Springer Berlin Heidelberg, 2004: 223-238. |
| [11] | Boneh D, Boyen X.Secure identity based encryption without random oracles[C]//Advances in Cryptology-Crypto 2004. Springer Berlin Heidelberg, 2004: 443-459. |
| [12] | Sakai R, Kasahara M.ID based Cryptosystems with Pairing on Elliptic Curve[J]. IACR Cryptology ePrint Archive, 2003: 54. |
| [13] | Waters B.Efficient identity-based encryption without random oracles[C]// Advances in Cryptology-EUROCRYPT 2005. Springer Berlin Heidelberg, 2005: 114-127. |
| [14] | Gentry C.Practical identity-based encryption without random oracles[C]//Advances in Cryptology-EUROCRYPT 2006. Springer Berlin Heidelberg, 2006: 445-464. |
| [15] | Cocks C.An identity based encryption scheme based on quadratic residues[C]//Cryptography and coding. Springer Berlin Heidelberg, 2001: 360-363. |
| [16] | Goldwasser S, Micali S.Probabilistic encryption[J]. Journal of computer and system sciences, 1984, 28(2): 270-299. |
| [17] | Rosen K H.Elementary number theory and its applications[M]. New Jersey: Addison Wesley, 1993. |
| [18] | Yan S Y.Number theory for computing[M]. Berlin: Springer Science & Business Media, 2002. |
| [19] | 裴定一,祝跃飞.算法数论[M]. 北京:科学出版社, 2002. |
| [20] | Katz J, Lindell Y.Introduction to modern cryptography[M]. Boca Raton, FL:CRC Press, 2014. |
| [21] | Delfs H, Knebl H.Introduction to cryptography: principles and applications[M]. Berlin:Springer Science & Business Media, 2007. |
| [22] | Goldreich O.Foundations of cryptography: volume 2, basic applications[M]. Cambridge:Cambridge university press, 2004. |
| [23] | Pohlig S C, Hellman M E.An Improved Algorithm for Computing Logarithms over GF (p) and its Cryptographic Significance[J]. IEEE Transactions on Information Theory, 1978, (24): 106-110. |
| [24] | Bellare M, Desai A, Pointcheval D, et al.Relations among notions of security for public-key encryption schemes[C]//Advances in Cryptology—CRYPTO'98. Springer Berlin Heidelberg, 1998: 26-45. |
| [25] | Kiltz E, Malone-Lee J.A general construction of IND-CCA2 secure public key encryption[C]//IMA Conference on Cryptography and Coding. Springer Berlin Heidelberg, 2003: 152-166. |
| [26] | Cramer R, Shoup V.A practical public key cryptosystem provably secure against adaptive chosen ciphertext attack[C]//Advances in Cryptology—CRYPTO'98. Springer Berlin Heidelberg, 1998: 13-25. |
| [27] | 冯登国. 密码学原理与实践[J].(第二版). 北京:电子工业出版社, 2003. |
| [28] | Mao W.Modern cryptography: theory and practice[M]. New Jersey:Prentice Hall Professional Technical Reference, 2003. |
| [29] | Fujisaki E,Okamoto T.How to enhance the security of public-key encryption at minimum cost[C]//Public Key Cryptography - PKC ’99, volume 1560 of LNCS, pages 53-68. Springer, 1999. |
| [30] | Boneh D, Gentry C, Hamburg M.Space-efficient identity based encryption without pairings[C]//Foundations of Computer Science, 2007. FOCS'07. 48th Annual IEEE Symposium on. IEEE, 2007: 647-657. |
| [31] | Boneh D, LaVigne R, Sabin M. Identity-Based Encryption with eth Residuosity and its Incompressibility[C]//Autumn 2013 TRUST Conference, Washington DC. 2013. |
| [32] | Paterson K G, Srinivasan S.On the relations between non-interactive key distribution, identity-based encryption and trapdoor discrete log groups[J]. Designs, Codes and Cryptography, 2009, 52(2): 219-241. |
| [33] | Meshram C.An efficient ID-based cryptographic encryption based on discrete logarithm problem and integer factorization problem[J]. Information Processing Letters, 2015, 115(2): 351-358. |
| [34] | Gentry C, Peikert C, Vaikuntanathan V.Trapdoors for hard lattices and new cryptographic constructions[C]//Proceedings of the fortieth annual ACM symposium on Theory of computing. ACM, 2008: 197-206. |
| [35] | Gentry C, Silverberg A.Hierarchical ID-based cryptography[C]//Advances in cryptology—ASIACRYPT 2002. Springer Berlin Heidelberg, 2002: 548-566. |
| [36] | Boneh D, Boyen X, Goh E J.Hierarchical identity based encryption with constant size ciphertext[C]//Advances in Cryptology-EUROCRYPT 2005. Springer Berlin Heidelberg, 2005: 440-456. |
| [37] | Shamir A.How to share a secret[J]. Communications of the ACM, 1979, 22(11): 612-613. |
| [38] | Chen L, Harrison K, Soldera D, et al.Applications of multiple trust authorities in pairing based cryptosystems[C]//Infrastructure Security. Springer Berlin Heidelberg, 2002: 260-275. |
| [39] | Al-Riyami S S, Paterson K G. Certificateless public key cryptography[C]//Advances in Cryptology-ASIACRYPT 2003. Springer Berlin Heidelberg, 2003: 452-473. |
| [40] | Goyal V.Reducing trust in the PKG in identity based cryptosystems[C]//Advances in Cryptology-CRYPTO 2007. Springer Berlin Heidelberg, 2007: 430-447. |
| [41] | Bellare M, Boldyreva A, Desai A, et al.Key-privacy in public-key encryption[C]//Advances in Cryptology—ASIACRYPT 2001. Springer Berlin Heidelberg, 2001: 566-582. |
| [42] | Boneh D, Di Crescenzo G, Ostrovsky R, et al.Public key encryption with keyword search[C]//Advances in Cryptology-Eurocrypt 2004. Springer Berlin Heidelberg, 2004: 506-522. |
| [43] | Ateniese G, Gasti P.Universally anonymous IBE based on the quadratic residuosity assumption[C]//Topics in Cryptology-CT-RSA 2009. Springer Berlin Heidelberg, 2009: 32-47. |
| [44] | Aouinatou R, Belkasmi M.Efficient anonymity for Cock's scheme[C]//2010 5th International Symposium On I/V Communications and Mobile Network. 2010. |
| [45] | Clear M, Tewari H, McGoldrick C. Anonymous IBE from quadratic residuosity with improved performance[C]//Progress in Cryptology-AFRICACRYPT 2014. Springer International Publishing, 2014: 377-397. |
| [46] | 连科,赵泽茂,王丽君,等 . 一种支持属性重用的DCP-ABE方案研究[J]. 信息网络安全,2015,(6):41-46. |
| [47] | Gentry C.A fully homomorphic encryption scheme[D]. California:Stanford University, 2009. |
| [48] | 杨晨,游林. 可计算密文加密体制研究[J]. 信息网络安全,2014,(5):78-81. |
| [49] | Clear M, Hughes A, Tewari H.Homomorphic Encryption with Access Policies: Characterization and New Constructions[C]//AFRICACRYPT,2013: 61-87. |
| [50] | Van Dijk M, Gentry C, Halevi S, et al.Fully homomorphic encryption over the integers[C]//Advances in Cryptology-EUROCRYPT 2010. Springer Berlin Heidelberg, 2010: 24-43. |
| [1] | 徐权佐, 蔡庆军. 一种基于编码的公钥密码体制的参数选择研究[J]. 信息网络安全, 2014, 14(10): 54-58. |
| [2] | 卢伟龙. 基于公钥密码体制的动态无线传感器网络安全数据聚合研究[J]. , 2013, 13(12): 0-0. |
| [3] | 项顺伯. 一种有效的基于身份的两方密钥交换协议[J]. , 2012, 12(2): 0-0. |
| [4] | 李智星;许春根. 一种基于多变量的代理签名方案[J]. , 2011, 11(12): 0-0. |
| [5] | 刘丹;刘畅;宋樵. 基于身份的安全电子邮件系统[J]. , 2010, (5): 0-0. |
| [6] | 王文博;杜彦辉. 公钥密码体制在网上银行中的应用[J]. , 2009, 9(4): 0-0. |
| [7] | 管海明. 抗量子计算公钥密码需求分析与技术路线[J]. , 2009, 9(4): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||