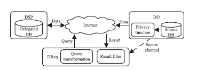
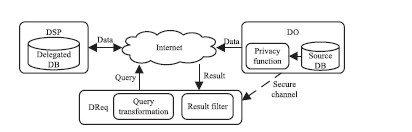
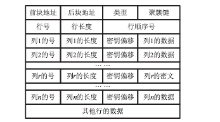
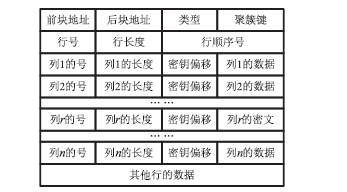
| [1] |
Hacigümüs H, Iyer B, Mehrotras S.Providing database as a service[C]//Proceedings of the 18th International Conference on Data Engineering, Washington, 2002: 29-38.
|
| [2] |
田秀霞,王晓玲,高明,等. 数据库服务——安全与隐私保护[J]. 软件学报,2010,21(5): 991-1006.
|
| [3] |
刘占斌,刘虹,火一莽. 云计算中基于密文策略属性基加密的数据访问控制协议[J]. 信息网络安全,2014,(7):57-60.
|
| [4] |
Rivest L, Adleman M,Dertouzos L.On data banks and privacy homomorphisms[J]. Foundations of Secure Computation, 1978: 169-178.
|
| [5] |
Bijit H.Storing and querying data securely in untrusted environments[D]. University of California, 2007.
|
| [6] |
林艳纯,王晓明. 基于最佳桶划分的数据库加密存储与查询[J]. 计算机工程,2011,37(17):105-107.
|
| [7] |
陈何峰,林柏钢,杨旸,等. 基于密文的中文关键词模糊搜索方案[J]. 信息网络安全,2014,(7):69-74.
|
| [8] |
蔡克,张敏,冯登国. 基于单断言的安全的密文区间检索[J]. 计算机学报,2011,34(11): 2093-2103.
|
| [9] |
Cao Ning, Wang Cong, Li Ming, et al.Privacy-preserving multi-keyword ranked search over encrypted cloud data[C]//Proceedings of INFOCOM. Shanghai, 2011, 829-837.
|
| [10] |
Sun S.Anti-tamper database research: Query encrypted databases[D]. Case Western Reserve University. 2005.
|
| [11] |
章恒,禄凯. 构建云计算环境的安全检查与评估指标体系[J]. 信息网络安全,2014,(9):115-119.
|
| [12] |
Craig G.Fully homomorphic encryption using ideal lattices[C]//Proceedings of the 41st ACM Symposium on Theory of Computing. Maryland, 2009, 169-179.
|
| [13] |
Marten D, Craig G, Shai H, et al. Fully homomorphic encryption over the integers[C]//Proceedings of the 29th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Riviera, 2010, LNCS 6110: 24-43.
|
| [14] |
Nigel S, Fvercaut V. Fully homomorphic encryption with relatively small key and ciphertext sizes[C]//Proceedings of the 13th Internaltional Conference on Practice and Theory in Public Key Cryptography. Paris, 2010, LNCS 6056: 420-443.
|
| [15] |
Michael C. IBM touts encryption innovation [EB/OL]. .
|
| [16] |
唐春明,郑晓龙. 云计算中一种对大群组用户的隐私保护公共审计方案[J]. 信息网络安全,2015,(2):19-25.
|
 ), Qing ZHOU1, Guo-shuang ZHANG1, Xin WANG2
), Qing ZHOU1, Guo-shuang ZHANG1, Xin WANG2