信息网络安全 ›› 2015, Vol. 15 ›› Issue (2): 46-50.doi: 10.3969/j.issn.1671-1122.2015.02.008
Kad网络协议研究与实验
- 四川大学电子信息学院,四川成都 610064
Analysis and Experiment of Kad Network Protocol
- College of Electronics and Information, Sichuan University, Chengdu Sichuan 610064, China
摘要:
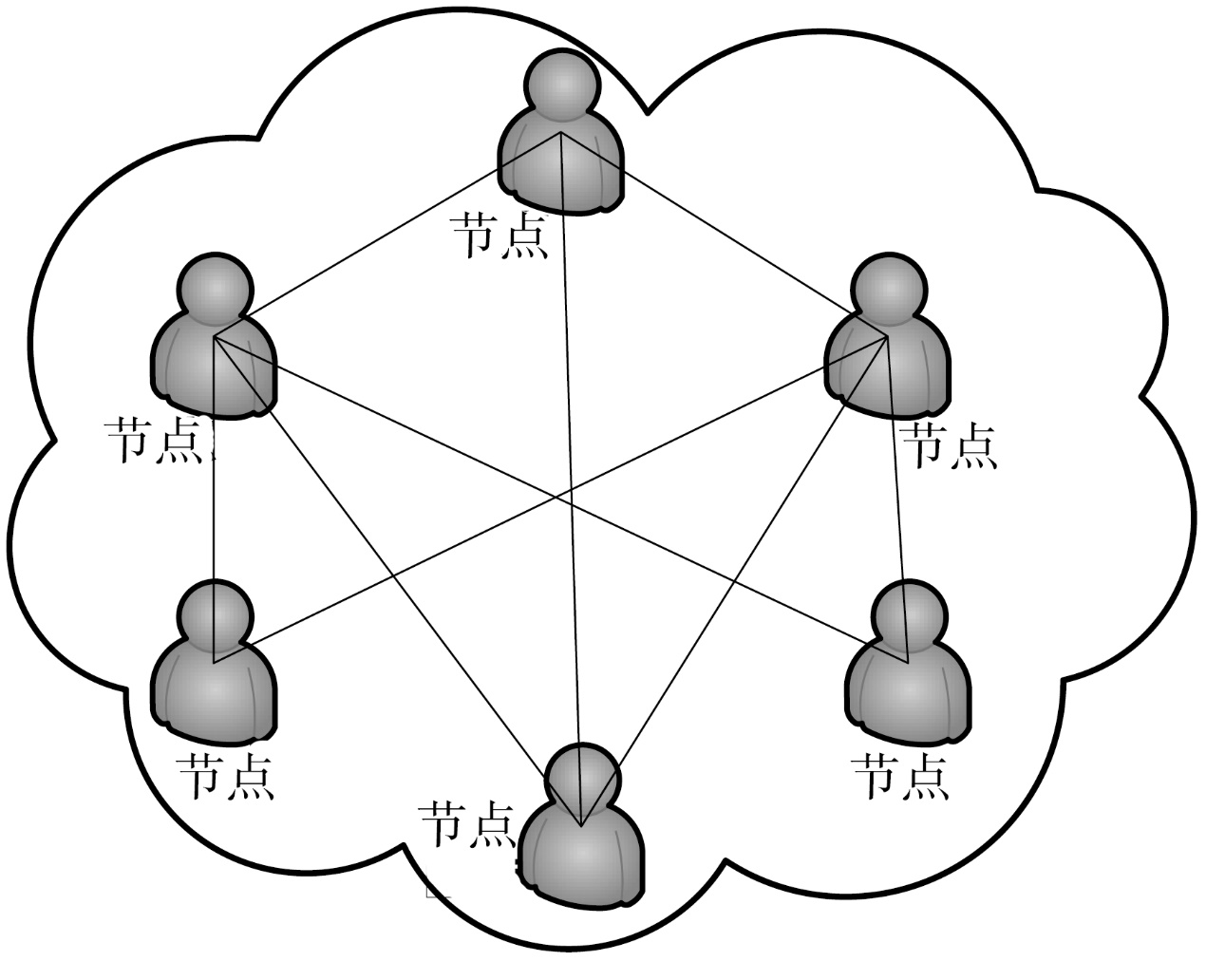
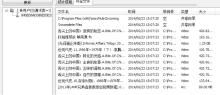
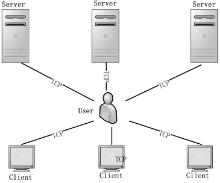
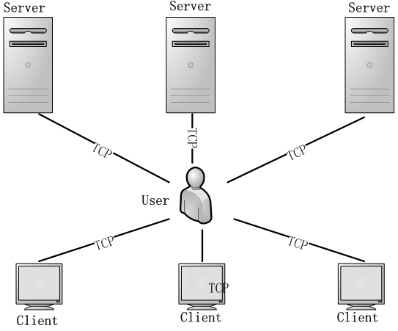
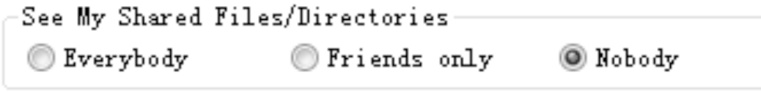
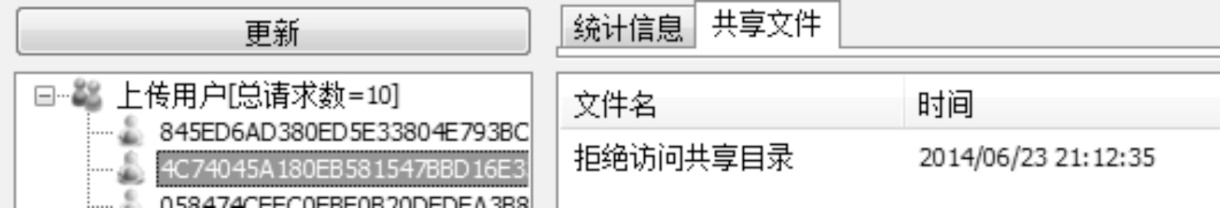
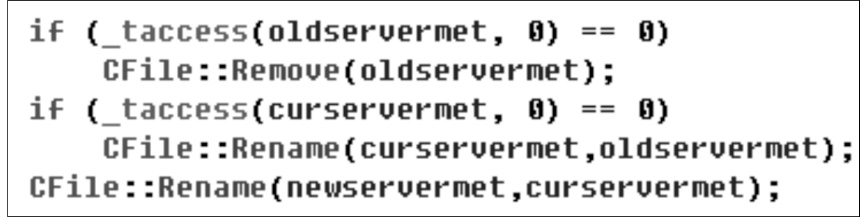
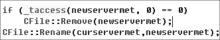
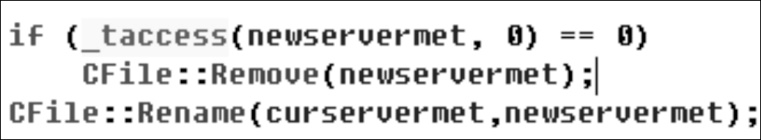
Kad作为一种开放性的网络协议,为深入研究和改进Kad网络协议提供了可能性。文章在对Kad客户端系统的体系结构进行整体分析后,结合其开放源码的静态测试,从用户隐私、内容隐私和服务器及节点文件这3个方面来研究Kad协议通信的安全性,并指出协议的缺陷和潜在的威胁。同时,每个研究均从原理和实验数据进行具体的分析和研究,对Kad客户端的数据通信的主要方法进行剖析。最后,针对协议不同的威胁提出相应的解决方案, 识别出了设计实现中主要的抽象类,通过抽象类的方法改进,使得存在的威胁降低到使用者的可接受范围内,这样不仅保证了用户能拥有安全的Kad网络环境,也可以为Kad网络安全、查询策略、拓扑优化等领域提供实际的数据基础和必要的实验结论。
中图分类号: