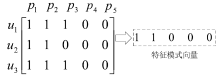信息网络安全 ›› 2022, Vol. 22 ›› Issue (11): 7-16.doi: 10.3969/j.issn.1671-1122.2022.11.002
异常权限配置下的角色挖掘方案
沈卓炜1,2, 范琳丽1,2, 华童1,2, 王科翔3
- 1. 东南大学网络空间安全学院,南京 211189
2. 东南大学计算机网络和信息集成教育部重点实验室,南京211189
3. 中国航空研究院,北京 100029
-
收稿日期:2022-06-01出版日期:2022-11-10发布日期:2022-11-16 -
作者简介:沈卓炜(1974—),男,江苏,副教授,博士,主要研究方向为分布式系统与网络安全|范琳丽(1996—),女,吉林,硕士研究生,主要研究方向为分布式系统与网络安全|华童(1998—),男,江苏,硕士研究生,主要研究方向为分布式系统与网络安全|王科翔(1991—),男,河南,工程师,硕士,主要研究方向为航空电子系统 -
基金资助:国家重点研发计划(2018YFB1800602)
Role Mining Scheme with Abnormal Permission Configuration
SHEN Zhuowei1,2, FAN Linli1,2, HUA Tong1,2, WANG Kexiang3
- 1. School of Cyber Science and Engineering, Southeast University, Nanjing 211189, China
2. Key Laboratory of Computer Network and Information Integration of Ministry of Education, Southeast University, Nanjing 211189, China
3. Chinese Aeronautical Establishment, Beijing 100029, China
-
Received:2022-06-01Online:2022-11-10Published:2022-11-16
摘要:
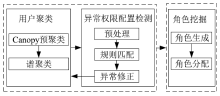
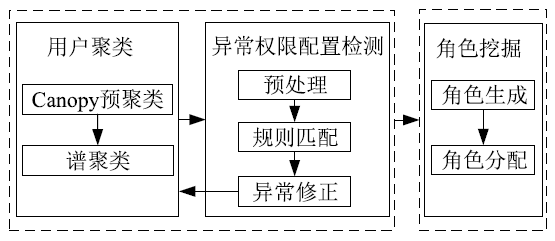
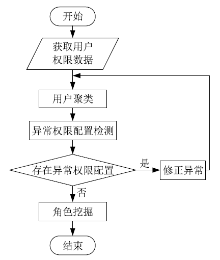
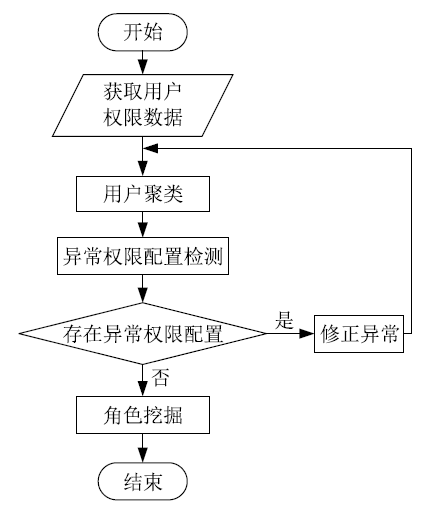
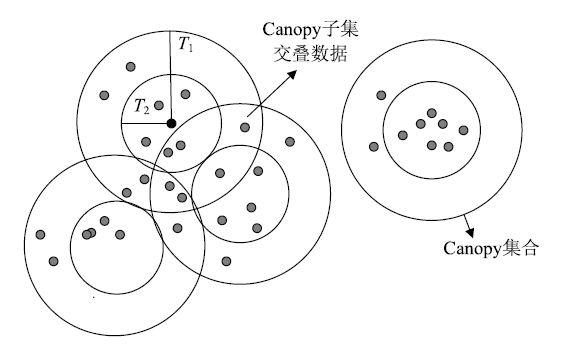
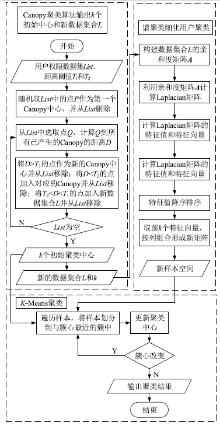
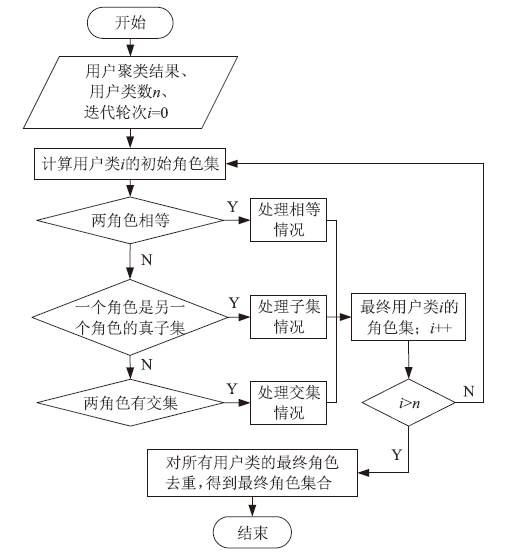
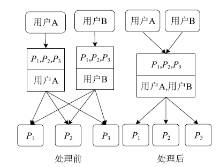
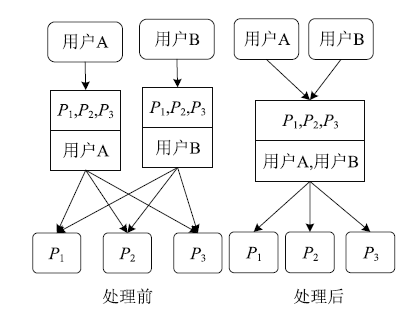
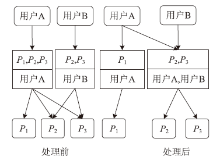
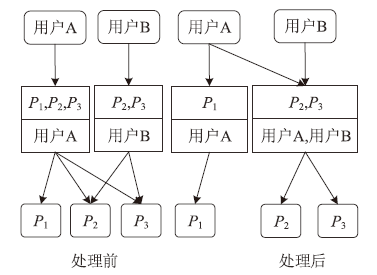
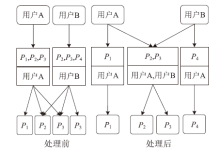
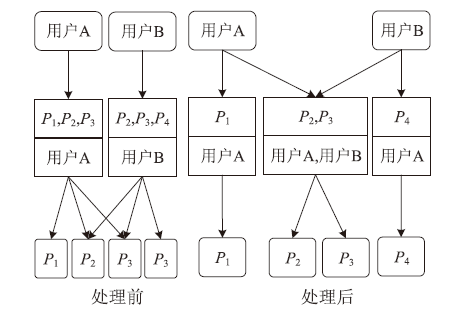
角色挖掘是构建RBAC系统的常用方法,但目前的角色挖掘方案在设计 时未考虑原始系统存在异常权限配置问题,导致角色挖掘的结果可能包含错误的角色 权限配置,给系统带来极大的安全风险。针对该问题,文章提出一种异常权限配置下 的角色挖掘方案。首先在用户聚类部分引入Canopy预聚类,通过预聚类提取子集交 叠数据,缩小后续谱聚类计算量;然后结合预聚类结果优化谱聚类的初始值选取,并 针对访问控制数据由布尔值表示的特点,采用杰卡德距离和汉明距离相结合的方式对 Canopy预聚类和谱聚类的距离进行度量,提高用户聚类效果;最后对异常权限配置检 测规则进行细化,利用修正后的用户聚类结果进行角色挖掘。实验结果表明,该方案 能够有效发现异常权限配置,提高角色挖掘效率。
中图分类号:
引用本文
沈卓炜, 范琳丽, 华童, 王科翔. 异常权限配置下的角色挖掘方案[J]. 信息网络安全, 2022, 22(11): 7-16.
SHEN Zhuowei, FAN Linli, HUA Tong, WANG Kexiang. Role Mining Scheme with Abnormal Permission Configuration[J]. Netinfo Security, 2022, 22(11): 7-16.
表4
异常权限配置下的角色挖掘运行时间
| 数据集 | 运行时间/s | T2 /T1 | |
|---|---|---|---|
| 文献[16]方案(T1) | 本文方案(T2) | ||
| Emea | 0.17 | 0.2 | 1.17 |
| Healthcare | 0.23 | 0.25 | 1.09 |
| Domino | 0.72 | 0.71 | 0.99 |
| Firewall2 | 27.95 | 23.3 | 0.83 |
| Firewall1 | 39.41 | 29.45 | 0.75 |
| University_Large | 92.67 | 68.93 | 0.74 |
| Apj | 6595.98 | 4723.54 | 0.72 |
| Americas_Small | 10154.17 | 6594.22 | 0.65 |
| Americas_Large | 12309.52 | 8113.94 | 0.66 |
表5
异常检测指标
| 数据集 | 文献[16]方案 | 本文方案 | ||||||
|---|---|---|---|---|---|---|---|---|
| Acc | Pre | Recall | F1 | Acc | Pre | Recall | F1 | |
| Emea | 0.779 | 0.724 | 0.843 | 0.779 | 0.84 | 0.79 | 0.91 | 0.846 |
| Healthcare | 0.768 | 0.704 | 0.835 | 0.764 | 0.826 | 0.774 | 0.904 | 0.834 |
| Domino | 0.772 | 0.713 | 0.837 | 0.77 | 0.831 | 0.779 | 0.906 | 0.838 |
| Firewall2 | 0.788 | 0.725 | 0.846 | 0.781 | 0.838 | 0.788 | 0.912 | 0.846 |
| Firewall1 | 0.783 | 0.722 | 0.847 | 0.78 | 0.839 | 0.791 | 0.915 | 0.849 |
| University_Large | 0.776 | 0.716 | 0.841 | 0.774 | 0.837 | 0.787 | 0.909 | 0.844 |
| Apj | 0.797 | 0.739 | 0.867 | 0.798 | 0.842 | 0.794 | 0.919 | 0.852 |
| Americas_Small | 0.801 | 0.751 | 0.873 | 0.808 | 0.848 | 0.798 | 0.923 | 0.856 |
| Americas_Large | 0.805 | 0.768 | 0.877 | 0.819 | 0.855 | 0.802 | 0.929 | 0.861 |
表6
加权结构复杂度实验结果
| 数据集 | 文献[16]方案 | 本文方案 | ||
|---|---|---|---|---|
| W=<1,0,0,0> | W=<1,1,1,1> | W=<1,0,0,0> | W=<1,1,1,1> | |
| Emea | 30 | 6984 | 33 | 6843 |
| Healthcare | 13 | 202 | 15 | 147 |
| Domino | 31 | 440 | 33 | 413 |
| Firewall2 | 10 | 1299 | 12 | 947 |
| Firewall1 | 60 | 1820 | 85 | 1397 |
| University_Large | 17 | 607 | 21 | 564 |
| Apj | 596 | 5820 | 612 | 5512 |
| Americas_Small | 624 | 18370 | 674 | 17595 |
| Americas_Large | 1739 | 57847 | 1826 | 55047 |
| [1] | MITRA B, SURAL S, VAIDYA J, et al. A Survey of Role Mining[J]. ACM Computing Surveys, 2016, 48(4): 1-37. |
| [2] | LIU Zhengtao, GU Wen, XIA Jinyue. Review of Access Control Model[J]. Journal of Cyber Security, 2019, 1(1): 43-50. |
| [3] | LI Hao, ZHANG Min, FENG Dengguo, et al. Research on Access Control of Big Data[J]. Chinese Journal of Computers, 2017, 40(1): 72-91. |
| 李昊, 张敏, 冯登国, 等. 大数据访问控制研究[J]. 计算机学报, 2017, 40(1):72-91. | |
| [4] | BAI Wei, PAN Zhisong, GUO Shize, et al. RMMDI: A Novel Framework for Role Mining Based on the Multi-Domain Information[EB/OL]. (2019-06-11)[2022-05-11]. . |
| [5] | KUHLMANN M, SHOHAT D, SCHIMPF G. Role Mining-Revealing Business Roles for Security Administration Using Data Mining Technology[C]// ACM. 8th ACM Symposium on Access Control Models and Technologies. New York: ACM, 2003: 179-186. |
| [6] | YUAN Xuebin, LI Wenping, LIU Shengcheng, et al. Role Mining Algorithm in RBAC[J]. Communications Technology, 2020, 53(8): 1994-2001. |
| 袁学斌, 李文萍, 刘生成, 等. RBAC中角色挖掘算法研究[J]. 通信技术, 2020, 53(8):1994-2001. | |
| [7] |
BLUNDO C, CIMATO S, SINISCALCHI L. Role Mining Heuristics for Permission-Role-Usage Cardinality Constraints[J]. The Computer Journal, 2022, 65(6): 1386-1411.
doi: 10.1093/comjnl/bxaa186 URL |
| [8] | WANG Jingyu, CUI Yongjiao, TAN Yuesheng. Role Mining Algorithm Based on Double Cardinality Constraints[J]. Computer Engineering and Design, 2020, 41(6): 1599-1604. |
| 王静宇, 崔永娇, 谭跃生. 基于双重约束的角色挖掘算法[J]. 计算机工程与设计, 2020, 41(6):1599-1604. | |
| [9] | CUI Yongjiao. Research on Role Mining Algorithm for Access Control[D]. Baotou: Inner Mongolia University of Science & Technology, 2020. |
| 崔永娇. 面向访问控制的角色挖掘算法研究[D]. 包头: 内蒙古科技大学, 2020. | |
| [10] |
ZHOU Chao, REN Zhiyu, WU Wenchao. Semantic Roles Mining Algorithms Based on Formal Concept Analysis[J]. Computer Science, 2018, 45(12): 117-122,129.
doi: 10.11896/j.issn.1002-137X.2018.12.018 |
|
周超, 任志宇, 毋文超. 基于形式概念分析的语义角色挖掘算法[J]. 计算机科学, 2018, 45(12):117-122,129.
doi: 10.11896/j.issn.1002-137X.2018.12.018 |
|
| [11] | VAIDYA J, ATLURI V, GUO Qi. The Role Mining Problem: Finding A Minimal Descriptive Set of Roles[C]// ACM. 12th ACM Symposium on Access Control Models and Technologies. New York: ACM, 2007: 175-184. |
| [12] | LU Haibing, VAIDYA J, ATLURI V. Optimal Boolean Matrix Decomposition: Application to Role Engineering[C]// IEEE. 24th International Conference on Data Engineering. New York: IEEE, 2008: 297-306. |
| [13] | MOLLOY I, LI Ninghui, QI Yuan, et al. Mining Roles with Noisy Data[C]// ACM. 15th ACM Symposium on Access Control Models and Technologies. New York: ACM, 2010: 45-54. |
| [14] | MENG Deyu, XU Zongben, ZHANG Lei, et al. A Cyclic Weighted Median Method for l1 Low-Rank Matrix Factorization with Missing Entries[C]// AAAI. 27th AAAI Conference on Artificial Intelligence. Washington: AAAI, 2013: 704-710. |
| [15] | PAN Ning. Research on Several Key Technologies of Role Mining[D]. Zhengzhou: PLA Strategic Support Force Information Engineering University, 2018. |
| 潘宁. 角色挖掘若干关键技术研究[D]. 郑州: 战略支援部队信息工程大学, 2018. | |
| [16] | FANG Liang, YIN Lihua, LI Fenghua, et al. Spectral-Clustering-Based Abnormal Permission Assignments Hunting Framework[J]. Journal on Communications, 2017, 38(12): 63-72. |
| 房梁, 殷丽华, 李凤华, 等. 基于谱聚类的访问控制异常权限配置挖掘机制[J]. 通信学报, 2017, 38(12):63-72. | |
| [17] | MOLLOY I, CHEN Hong, LI Tiancheng, et al. Mining Roles with Multiple Objectives[J]. ACM Transactions on Information and System Security, 2010, 13(4): 1-35. |
| [1] | 赵薇, 赵娜, 张怡兴. 基于颜色不变特征的谱聚类双分图分割方法[J]. 信息网络安全, 2018, 18(12): 8-14. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||