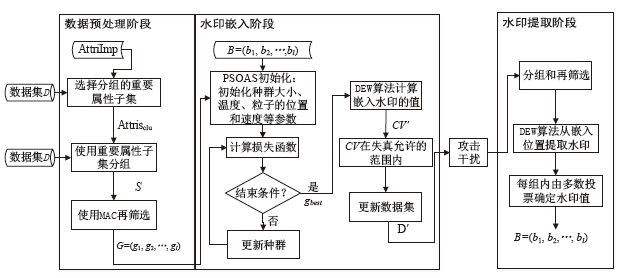
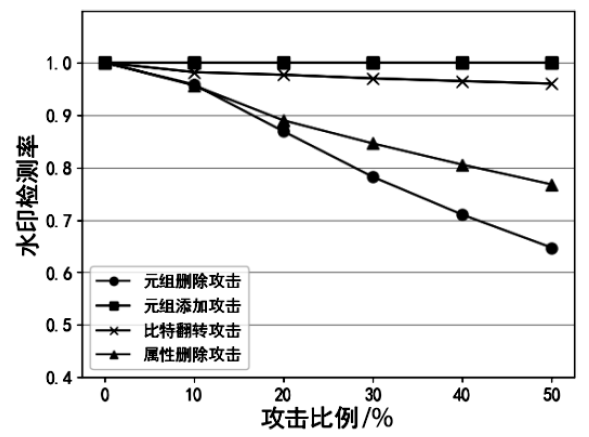
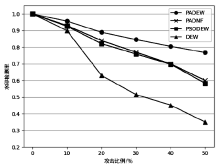
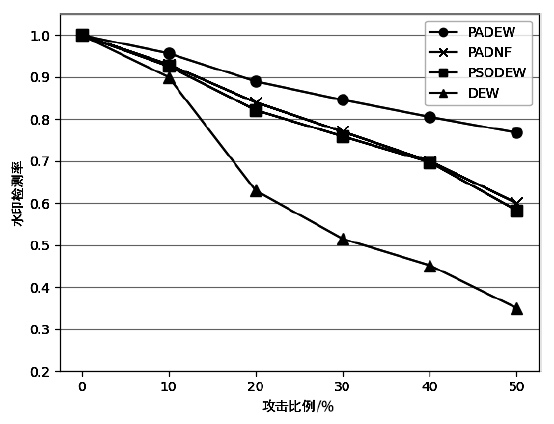
| [1] |
Canalys. Cybersecurity Investment 2020[EB/OL]. [2022-04-12]. https://www.canalys.com/reports/cybersecurity-market.
|
| [2] |
AGRAWAL R, KIERNAN J. Watermarking Relational Databases[C]// VLDB. Proceedings of 28th International Conference on Very Large Data Bases. San Fransisco: Morgan Kaufmann, 2002: 155-166.
|
| [3] |
GUO Fei, WANG Jianmin, LI Deyi. Fingerprinting Relational Databases[C]// SAC. Proceedings of the 2006 ACM Symposium on Applied computing. New York: ACM, 2006: 487-492.
|
| [4] |
GUPTA G, PIEPRZYK J. Reversible and Blind Database Watermarking Using Difference Expansion[C]// e-Forensics. Proceedings of the 1st International Conference on Forensic Applications and Techniques in Telecommunications, Information, and Multimedia and Workshop. Brussels, BEL: ICST, 2008: 6-14.
|
| [5] |
CHAI Heyan, YANG Shuqiang. A Robust and Reversible Watermarking Technique for Relational Dataset Based on Clustering[C]// TrustCom/BigDataSE. 2019 18th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/13th IEEE International Conference on Big Data Science and Engineering. New Zealand: IEEE, 2019: 411-418.
|
| [6] |
JAWAD K, KHAN A. Genetic Algorithm and Difference Expansion Based Reversible Watermarking for Relational Databases[J]. Journal of Systems and Software, 2013, 86(11): 2742-2753.
doi: 10.1016/j.jss.2013.06.023
URL
|
| [7] |
HU Donghui, ZHAO Dan, ZHENG Shuli. A New Robust Approach for Reversible Database Watermarking with Distortion Control[J]. IEEE Transactions on Knowledge and Data Engineering, 2018, 31(6): 1024-1037.
doi: 10.1109/TKDE.2018.2851517
URL
|
| [8] |
PARSOPOULOS K E, VRAHATIS M N. Particle Swarm Optimization Method for Constrained Optimization Problems[J]. Intelligent Technologies-Theory and Application: New Trends in Intelligent Technologies, 2002, 76(1): 214-220.
|
| [9] |
KAMRAN M, FAROOQ M. An Information-Preserving Watermarking Scheme for Right Protection of EMR Systems[J]. IEEE Transactions on Knowledge and Data Engineering, 2011, 24(11): 1950-1962.
doi: 10.1109/TKDE.2011.223
URL
|
| [10] |
KAMRAN M, SUHAIL S, FAROOQ M. A Robust, Distortion Minimizing Technique for Watermarking Relational Databases Using Once-for-All Usability Constraints[J]. IEEE Transactions on Knowledge and Data Engineering, 2013, 25(12): 2694-2707.
doi: 10.1109/TKDE.2012.227
URL
|
| [11] |
SHEHAB M, BERTINO E, GHAFOOR A. Watermarking Relational Databases Using Optimization-Based Techniques[J]. IEEE Transactions on Knowledge and Data Engineering, 2007, 20(1): 116-129.
doi: 10.1109/TKDE.2007.190668
URL
|
| [12] |
UNNIKRISHNAN K, PRAMOD K V. Robust Aptimal Position Detection Scheme for Relational Database Watermarking Through HOLPSOFA Algorithm[J]. Journal of Information Security& Applications, 2017, 35(8): 1-12.
|
| [13] |
IFTIKHAR S, KAMRAN M. RRW-A Robust and Reversible Watermarking Technique for Relational Data[J]. IEEE Transactions on Knowledge& Data Engineering, 2014, 27(4): 1132-1145.
|
| [14] |
MACQUEEN J. Some Methods for Classification and Analysis of MultiVariate Observations[C]// Berkeley. Proceedings of the Fifth Berkeley Symposium on Mathematical Statistics and Probability. USA: University of California Press, 1967:281-297.
|
| [15] |
KENNEDY J, EBERHART R. Particle Swarm Optimization[C]// IEEE. Proceedings of ICNN'95-International Conference on Neural Networks. New York: IEEE, 1995: 1942-1948.
|
| [16] |
METROPOLIS N, ROSENBLUTH A W, ROSENBLUTH M N, et al. Equation of State Calculations by Fast Computing Machines[J]. The Journal of Chemical Physics, 1953, 21(6): 1087-1092.
doi: 10.1063/1.1699114
URL
|
| [17] |
LIU Aijun, YANG Yu, LI Fei, et al. Chaotic Simulated Annealing Particle Swarm Optimization Algorithm Research and Its Application[J]. Journal of Zhejiang University(Engineering Science), 2013, 47(10): 1722-1730.
|
|
刘爱军, 杨育, 李斐, 等. 混沌模拟退火粒子群优化算法研究及应用[J]. 浙江大学学报(工学版), 2013, 47(10): 1722-1730.
|
| [18] |
WANG Huaqiu, CAO Changxiu. Parallel Particle Swarm Optimization Based on Simulated Annealing[J]. Control and Decision, 2005(5): 500-504.
|
|
王华秋, 曹长修. 基于模拟退火的并行粒子群优化研究[J]. 控制与决策, 2005(5):500-504.
|
| [19] |
ZHAO Xinye, TANG Shuai, YANG Mei, et al. Hybrid Algorithm Based on Particle Swarm Optimization and Simulated in Timed Influence Nets[J]. Computer Science, 2012, 39(Z3): 63-66.
|
|
赵鑫业, 唐帅, 杨妹, 等. 基于赋时影响网的模拟退火与粒子群混合改进算法[J]. 计算机科学, 2012, 39(Z3):63-66.
|
 ), GE Xiaoxue1,2
), GE Xiaoxue1,2