信息网络安全 ›› 2020, Vol. 20 ›› Issue (1): 40-45.doi: 10.3969/j.issn.1671-1122.2020.01.006
基于功率控制与中继协作的抗窃听攻击模型
- 1. 福建师范大学网络安全与密码技术重点实验室,福州 350007
2. 闽江师范高等专科学校计算机系,福州 350108
3. 物联网福建省高校应用技术工程中心,福州 350108
Anti-eavesdropping Attack Model Based on Power Control and Relay Cooperation
LI Ruixing1,2,3( ), XU Li1,3, FANG He1,3
), XU Li1,3, FANG He1,3
- 1. Key Laboratory of Network Security and Cryptography, Fujian Normal University, Fuzhou 350007, China
2. Department of Computer Science, Minjiang Teachers College, Fuzhou 350108
3. Fujian College Applied Technology Engineering Center of Internet of Things, Fuzhou 350108, China
摘要:
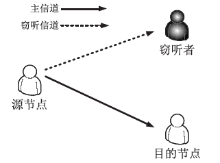
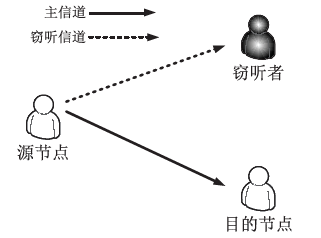
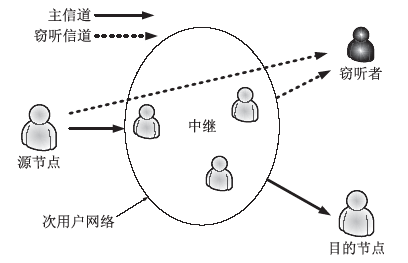
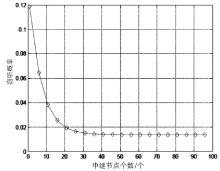
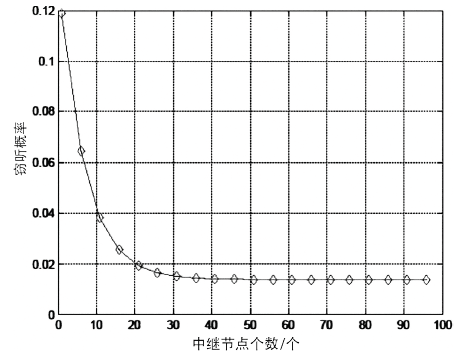
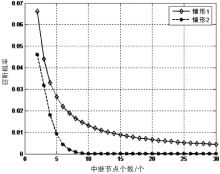
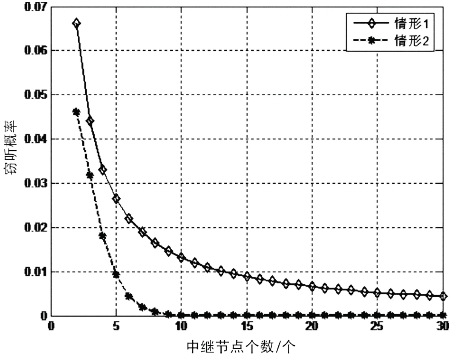
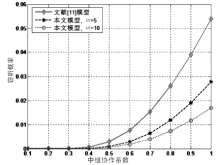
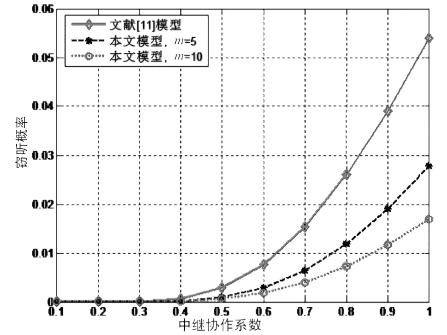
在认知无线电网络中,由于无线通信的广播特性,容易造成链路被恶意窃听。文章首先分析主用户(授权用户)网络中直接传输下窃听概率与功率的关系。接着提出基于功率控制与中继协作的抗窃听攻击模型,计算两种不同情形下的最佳传输功率。第一种情形为窃听者只能窃听中继节点的信号,第二种情形为窃听者可以同时从源节点和中继节点窃听到信息。最后,文章通过分析安全容量给出最佳中继的选择标准。数值分析结果表明,文章模型可以通过增加中继节点的个数来降低窃听概率。此外,相较于其他模型,文章模型在抵御窃听攻击方面能达到更优的效果。
中图分类号: