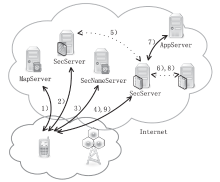
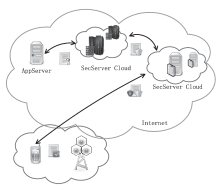
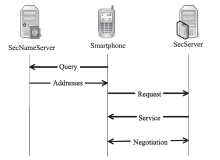
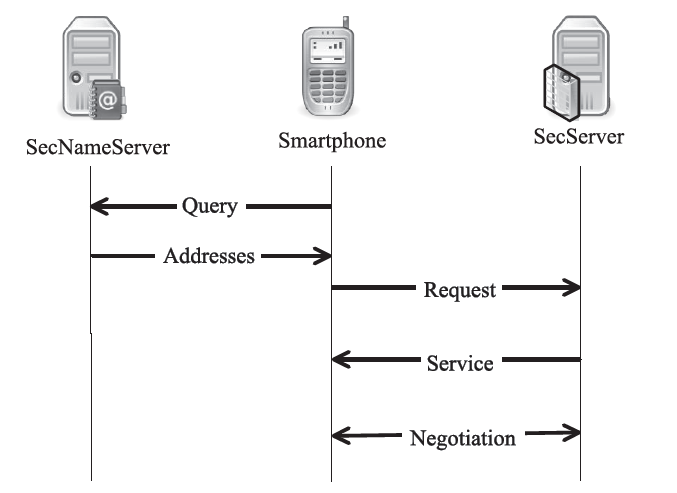
信息网络安全 ›› 2020, Vol. 20 ›› Issue (3): 18-28.doi: 10.3969/j.issn.1671-1122.2020.03.003
移动互联网的通行证式统一威胁管理架构
- 1.中山大学电子与通信工程学院,广州 510006
2.中山大学新华学院信息科学学院,广州 510520
-
收稿日期:2019-11-14出版日期:2020-03-10发布日期:2020-05-11 -
作者简介:作者简介:李宁(1956—),女,江西,副教授,硕士,主要研究方向为计算机网络与信息处理;李柏潮(1988—),男,广东,博士,主要研究方向为网络安全。
-
基金资助:国家自然科学基金[U1636118];广东省科技发展专项资金[2017B030306015]
Token-based UTM Architecture for Mobile Internet
- 1. School of Electronics and Information Technology, Sun Yat-Sen University, Guangzhou 510006, China
2. School of Information Science, Xinhua College, Sun Yat-Sen University, Guangzhou 510520, China
-
Received:2019-11-14Online:2020-03-10Published:2020-05-11
摘要:
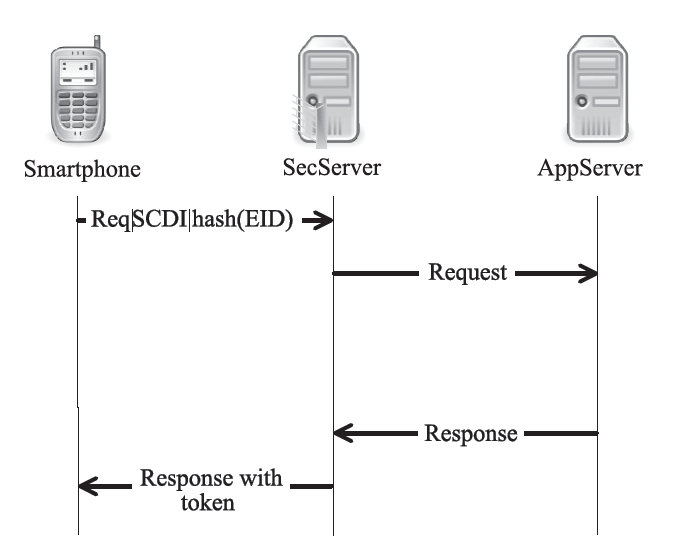
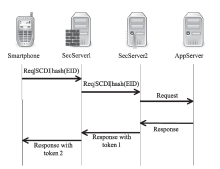
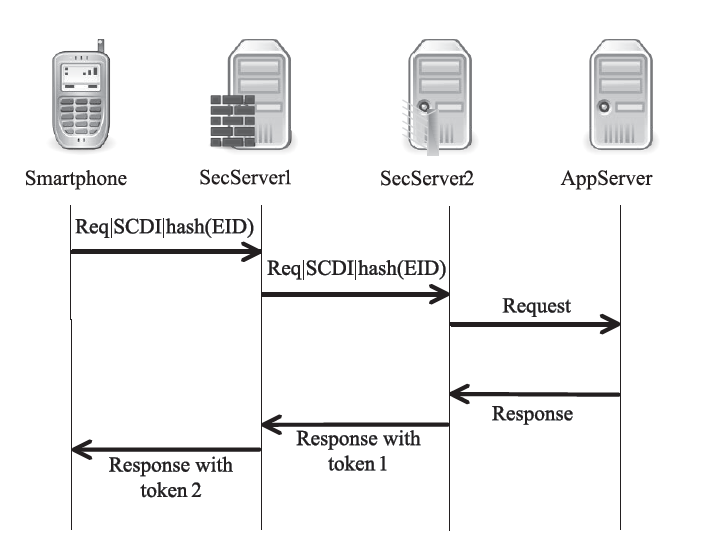
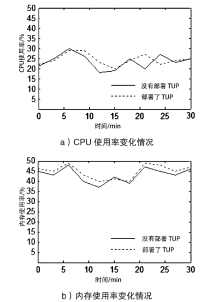
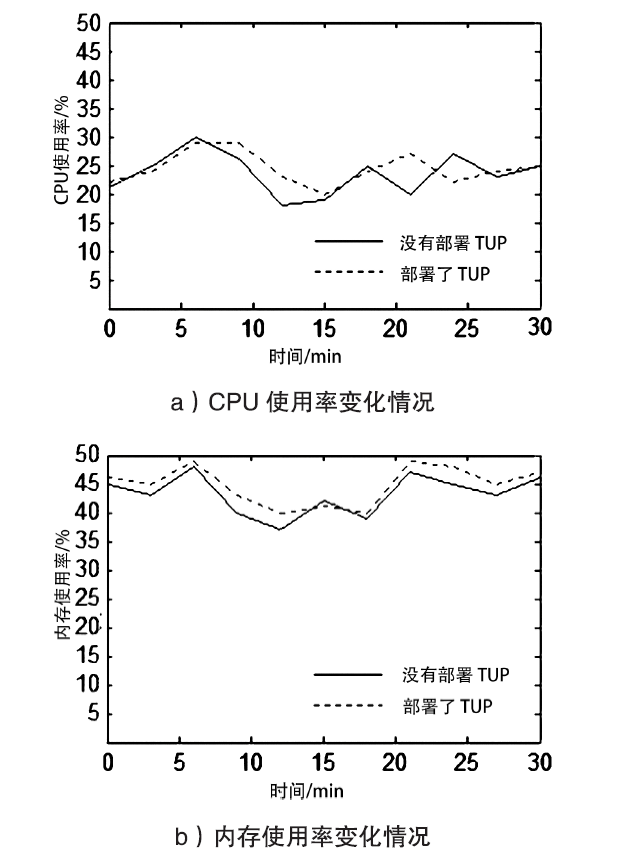
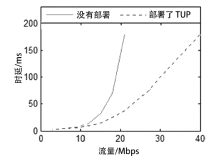
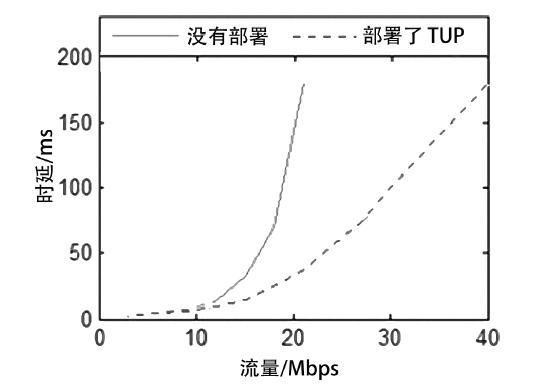
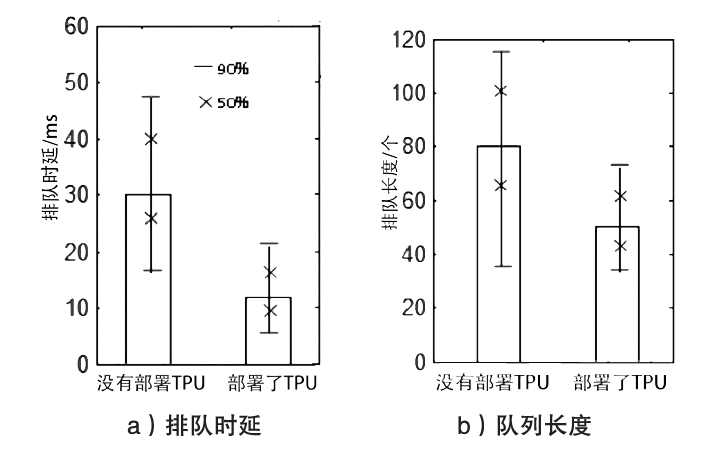
越来越多的恶意软件以智能手机为攻击目标,智能手机的安全是移动互联网所面临的重要问题之一。智能手机在运算能力、电量供应等方面受限,难以运行复杂的安全软件保障自身的安全,且统一威胁管理等安全设备的现有部署方法不适用于移动互联网。文章提出将移动终端安全作为网络的一项可定制的基础服务,设计了通行证式统一威胁管理架构及对应的通行证式统一威胁管理协议。在该架构中,安全策略不再与网络位置绑定,而是与用户身份绑定,使得用户移动到任何位置都可以获得按需的、差异化的安全服务。性能分析和实验表明,该架构对现有网络的改动小,具有良好的可扩展性;智能手机通信开销小;网络流量更加均衡,网络整体吞吐量得到提高。
中图分类号:
引用本文
李宁, 李柏潮. 移动互联网的通行证式统一威胁管理架构[J]. 信息网络安全, 2020, 20(3): 18-28.
LI Ning, LI Bochao. Token-based UTM Architecture for Mobile Internet[J]. Netinfo Security, 2020, 20(3): 18-28.
表1
SCD内容
| 字段 | 要求 | 示例 |
|---|---|---|
| Source | 必需 | IPv4:12.34.56.78, TCP:80, Type:Server |
| Target | 必需 | IPv4:56.78.91.23, TCP:1000, Type:Client |
| Protocol | 必需 | HTTP-TCP-IPv4 |
| SecurityNeed | 必需 | pseudo-code description |
| NextAction | 必需 | pseudo-code description |
| LifeTime | 必需 | 5 min |
| OS Platform | 可选 | Android 2.3 |
| App Name & Vertion | 可选 | Browser: Firefox 4.0 | Browser: Opera v6.2 |
| App Setting | 可选 | JavaScrip Enabled, Cookie Enabled, SSH disabled |
表1
| [1] | PORTOKAILIDIS G, HOMBURG P C, ANAGNOSTAKIS K, et al. Paranoid Android: Versatile Protection for Smartphones[EB/OL]. , 2019-10-10. |
| [2] | BECHER M, FREILING F C, HOFFMANN J, et al.Mobile Security Catching Up? Revealing the Nuts and Bolts of the Security of Mobile Devices[C]//IEEE. 2011 IEEE Symposium on Security and Privacy(SP’11), May 22-25, 2011, Berkeley, CA, USA. NJ: IEEE, 2011: 96-111. |
| [3] | LUO Junzhou, WU Wenjia, YANG Ming.Mobile Internet: Terminal Devices, Networks and Services[J]. Chinese Journal of Computers, 2011, 34(11): 2029-2051. |
| 罗军舟,吴文甲,杨明.移动互联网:终端、网络与服务[J].计算机学报,2011,34(11):2029-2051. | |
| [4] | OBERHEIDE J, COOKE E, JAHANIAN F. CloudAV: N-version Antivirus in the Network Cloud[EB/OL]. , 2019-10-10. |
| [5] | WU Bin, LIN Xing, LI Weidong, et al.Smartphone Malware Detection Model Based on Artificial Immune System in Cloud Computing[J]. Journal of Beijing University of Posts and Telecommunications, 2015,38(4):33-37. |
| 武斌,林幸,李卫东,等.云计算下手机人工免疫恶意代码检测模型[J].北京邮电大学学报,2015,38(4):33-37. | |
| [6] | LI Jun.Research on a Mobile Malicious Code Management and Control Method Based on Cloud-Pipeline-Terminal[J]. Telecommunications Science, 2013, 8: 156-167. |
| 李俊. 一种基于云一管一端的移动互联网恶意程序管控方案研究[J].电信科学,2013,8:156-167. | |
| [7] | JOSEPH D A, TAVAKOLI A, STOICA I, A Policy-aware Switching Layer for Data Centers[J]. ACM SIGCOMM Computer Communication Review, 2008, 38(4): 51-62. |
| [8] | CASADO M, FREEDMAN M, PETTIT J, et al.Ethane: Taking Control of the Enterprise[J]. Computer Communication Review, 2007, 37(4): 1-12. |
| [9] | WALFISH M, STRIBLING J, KROHN M, et al. Middleboxes No Longer Considered Harmful[EB/OL]. ,2019-10-10. |
| [10] | JIANG Guoqing.The Study on Security of Data in Intelligent Mobile Based on Cloud Computing[J]. Software Engineer, 2015,18(11): 22-23. |
| 蒋国清. 基于云计算的智能移动终端的数据安全性研究[J].软件工程师,2015,18(11):22-23. | |
| [11] | ZHAO Yu, ZHANG Kecheng.Implementation of Mobile Internet Security Solutions Based on Mobile Core Network[J]. Communications Technology, 2018, 51(1): 205-209. |
| 赵宇,张科程.基于移动核心网的手机信息安全系统实现[J].通信技术,2018,51(1):205-209. | |
| [12] | GUHA S, FRANCIS P.An End-middle-end Approach to Connection Establishment[J]. Computer Communication Review, 2007, 37(4): 193-204. |
| [13] | MUTHUKRISHNAN C, PAXSON V, ALLMAN M, et al.Using Strongly Typed Networking to Architect for Tussle[C]//ACM. The 9th ACM SIGCOMM Workshop on Hot Topics in Networks, October 20-21, 2010, Monterey, California, USA. New York: ACM, 2010: 1-6. |
| [14] | ERIKSSON A, FODOR G.A Middlebox Control Plane Framework for Wireless and Mobile IP Networks[C]//IEEE. The 2004 International Conference on Parallel Processing Workshops, August 18, 2004, Montreal, QC, Canada. NJ: IEEE, 2004: 322-329. |
| [15] | DOGAR F R, STEENKISTE P. M2: Using Visible Middleboxes to Serve Pro-active Mobile-hosts[EB/OL]. ,2019-10-10. |
| [16] | ROCHA B P S, COSTA D N O, MOREIRA R A, et al. Adaptive Security Protocol Selection for Mobile Computing[J]. Journal of Network and Computer Applications, 2010, 33(5): 569-587. |
| [17] | PANJA B, MADRIA S K, BHARGAVA B.A Role-based Access in a Hierarchical Sensor Network Architecture to Provide Multilevel Security[J]. Computer Communications, 2008, 31(4): 793-806. |
| [18] | WANG Hui, WANG Rui, HU Zhaohua.Future Development Direction of Terminal Security Protection[J]. Communications Technology, 2019, 52(2): 455-459. |
| 王慧,王锐,胡兆华.未来终端安全防护的发展方向[J].通信技术,2019,52(2):455-459. | |
| [19] | ANDERSEN D, BALAKRISHNAN H, FEAMSTER N, et al.Accountable Internet Protocol(AIP)[J]. Computer Communication Review, 2008, 38(4): 339-350. |
| [20] | SESKAR I, NAGARAJA K, NELSON S, et al.MobilityFirst Future Internet Architecture Project[C]//SIGCOMM. The 7th Asian Internet Engineering Conference, November 9-11, 2011, Bangkok, Thailand. New York: ACM, 2011: 1-3. |
| [21] | ClearFoundationg. Application Layer Packet Classifier for Linux[EB/OL]. , 2019-10-10. |
| [1] | 蔡晶晶, 钱晓敏. 广电全台网统一接入平台的网络安全策略研究[J]. 信息网络安全, 2017, 17(2): 79-84. |
| [2] | 陈开放, 李汇云, 刘松, 周纯杰. 基于DDS舰载通信系统的信息安全分析研究[J]. 信息网络安全, 2016, 16(3): 47-52. |
| [3] | 罗霄峰, 王文贤, 罗万伯. 访问控制技术现状及展望[J]. 信息网络安全, 2016, 16(12): 19-27. |
| [4] | 陈红松, 韩至, 邓淑宁. 智慧城市中大数据安全分析与研究[J]. 信息网络安全, 2015, 15(7): 1-6. |
| [5] | 黄可臻, 李宇翔, 林柏钢. 基于Android的隐私数据安全保护系统[J]. 信息网络安全, 2014, 14(9): 54-57. |
| [6] | 张明德. 应用安全机制研究[J]. , 2013, 13(Z): 0-0. |
| [7] | 王伟;张之栋;雷雨诗;伍琦. 基于策略的Android应用检测系统[J]. , 2013, 13(2): 0-0. |
| [8] | 佟晖;刘长文;齐莹素;魏喆. 政务云构建与安全问题研究[J]. , 2012, 12(9): 0-0. |
| [9] | 张明德;郑雪峰;蔡翌. 应用安全模型研究[J]. , 2012, 12(8): 0-0. |
| [10] | 彭国军;邵玉如;王泰格. 基于Android的手机隐私保护技术及实现[J]. , 2012, 12(4): 0-0. |
| [11] | 季辉. 公共计算资源身份认证与安全保护的加密协议[J]. , 2011, 11(3): 0-0. |
| [12] | 赵章界;李晨旸;刘海峰. 信息安全策略开发的关键问题研究[J]. , 2011, 11(3): 0-0. |
| [13] | 李力;董建锋;贾磊雷. 无线影子网络环境下安全策略研究[J]. , 2011, 11(10): 0-0. |
| [14] | 李亮. 重要信息系统局域网安全策略分析与研究[J]. , 2010, (7): 0-0. |
| [15] | 何月. 基层检察院信息网络系统安全探究[J]. , 2010, (2): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||