信息网络安全 ›› 2018, Vol. 18 ›› Issue (9): 66-73.doi: 10.3969/j.issn.1671-1122.2018.09.011
基于Inject和Hook的安卓终端管控技术
秦中元1, 张峻瑞1, 张群芳2, 宋志勇1
- 1. 东南大学网络空间安全学院,江苏南京 210096
2. 炮兵防空兵学院南京校区,江苏南京 211132
-
收稿日期:2018-07-17出版日期:2018-09-30发布日期:2020-05-11 -
作者简介:作者简介:秦中元(1974—),男,副教授,博士,主要研究方向为网络安全;张峻瑞(1993—),男,江苏,硕士研究生,主要研究方向为网络安全;张群芳(1981—),女,江苏,讲师,硕士,主要研究方向为网络安全;宋志勇(1994—),男,山东,硕士研究生,主要研究方向为网络安全。
-
基金资助:国家自然科学基金[61601113]
Android Terminals Control Technology Based on Inject and Hook
Zhongyuan QIN1, Junrui ZHANG1, Qunfang ZHANG2, Zhiyong SONG1
- 1. School of Cyberspace Security, Southeast University, Nanjing Jiangsu 210096, China
2. Artillery and Air-defence Institute Nanjing Campus, Nanjing Jiangsu 211132, China
-
Received:2018-07-17Online:2018-09-30Published:2020-05-11
摘要:
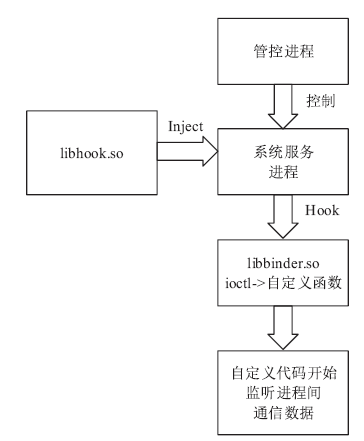
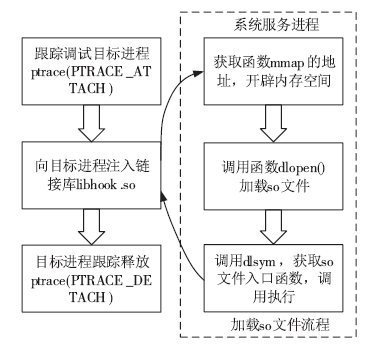
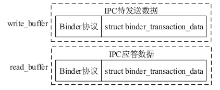
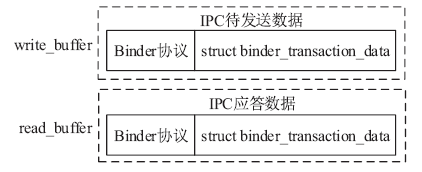
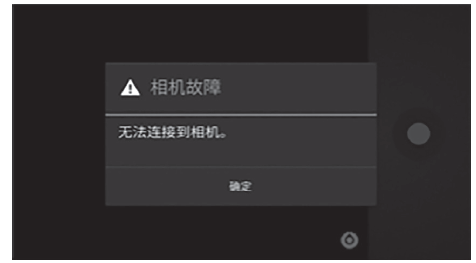
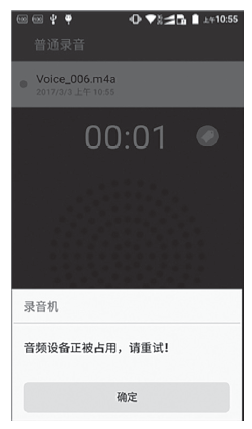
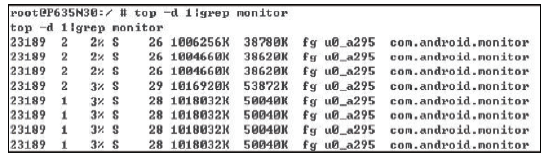
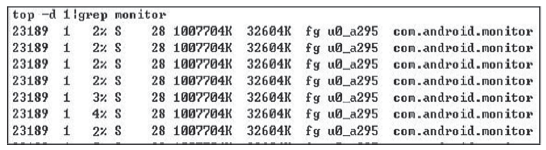
针对安卓终端缺乏有效的软件化管控方案,文章提出了一种基于Inject和Hook的安卓终端管控技术。该技术向系统服务进程注入管控自定义代码,通过劫持进程间通信(IPC)关键函数ioctl()的地址监听服务请求数据包并进行解析,得出当前请求的服务信息,若请求的服务方法位于管控黑名单上,则对相应的请求数据包进行修改,从而实现实时管控的功能。测试结果表明,文章提出的方案可以有效实现安卓终端管控。
中图分类号:
引用本文
秦中元, 张峻瑞, 张群芳, 宋志勇. 基于Inject和Hook的安卓终端管控技术[J]. 信息网络安全, 2018, 18(9): 66-73.
Zhongyuan QIN, Junrui ZHANG, Qunfang ZHANG, Zhiyong SONG. Android Terminals Control Technology Based on Inject and Hook[J]. Netinfo Security, 2018, 18(9): 66-73.
| [1] | ZHOU Hang, YANG Yang, QIU Xuesong, et al.The Strategy of Probe Station Selection of Active Probing in WSNs[C]//IEEE. 16th Asia-Pacific Network Operations and Management Symposium, September 17-19, 2014, Hsinchu, Taiwan, China. New Jersey: IEEE, 2014: 1-4. |
| [2] | LI Yongxing, HENG Yang, HAO Ankang, et al.Detecting and Tracking Pseudo Base Stations in GSM Signal Hijacking and Frauds: a Visualized Approach[J]. Information Security and Computer Fraud, 2017, 5(1): 1-8. |
| [3] | ZHANG Yuan, YANG Min, XU Bingquan, et al.Vetting Undesirable Behaviors in Android APPs with Permission use Analysis[C]//ACM. 2013 ACM SIGSAC Conference on Computer & Communications Security, November 4-8, 2013, Berlin, Germany. New York: ACM, 2013: 611-622. |
| [4] | ZHAI Gaoshou, LIU Chen, XIANG Yong.Study and Implementation of Systematic Protection by Monitoring Abnormal Invocation of Linux Kernel Functions[J]. Netinfo Security, 2018, 18(3): 26-38. |
| 翟高寿,刘晨,向勇. 基于内核函数监控的Linux系统防护方法的研究与实现[J]. 信息网络安全,2018,18(3):26-38. | |
| [5] | LI Zhoujun, WU Chunming, WANG Xiao.Assessment of Android Application’s Risk Behavior Based on a Sandbox System[J]. Journal of Tsinghua University(Science & Technology), 2016, 56(5): 453-460. |
| 李舟军,吴春明,王啸. 基于沙盒的Android应用风险行为分析与评估[J]. 清华大学学报 (自然科学版),2016,56(5):453-460. | |
| [6] | SONG Xinlong, ZHENG Dong, YANG Zhonghuang.Mobile Device Management System Based on AOSP and SELinux[J]. Netinfo Security, 2017, 17(9): 103-106. |
| 宋新龙,郑东,杨中皇. 基于AOSP与SELinux的移动设备管理系统[J]. 信息网络安全,2017,17(9):103-106. | |
| [7] | ENCK W, GILBERT P, CHUN B G, et al.TaintDroid: an Information Flow Tracking System for Real-time Privacy Monitoring on Smartphones[J]. ACM Transactions on Computer Systems, 2012, 32(2): 1-29. |
| [8] | TAM K, KHAN S J, FATTORI A, et al. CopperDroid: Automatic Reconstruction of Android Malware Behaviors[EB/OL]>, 2018-3-11. |
| [9] | XU Rubin,SAÏDI H, ANDERSON R. Aurasium: Practical Policy Enforcement for Android Applications[C]//ACM. 21st USENIX Conference on Security Symposium, August 8-10, 2012, Bellevue, USA. New York: ACM, 2012: 27-40. |
| [10] | SINGH L, HOFMANN M.Dynamic Behavior Analysis of Android Applications for Malware Detection[C]//IEEE. 2017 International Conference on Intelligent Communication and Computational Techniques, December 22-23, 2017, Jaipur, India. New Jersey: IEEE, 2017: 1-7. |
| [11] | ZHENG Min, SUN Mingshen, LUI J C S. DroidTrace: a Ptrace Based Android Dynamic Analysis System with Forward Execution Capability[C]//IEEE. 2014 International Wireless Communications and Mobile Computing Conference, Auguest 4-8, 2014, Nicosia, Cyprus. Jersey: IEEE, 2014: 128-133. |
| [12] | WEN Weiping, TANG Yang, SHEN Li.An APP Sensitive Behaviors Detection Method Based on Android Kernel and Its Implementation[J]. Netinfo Security, 2016, 16(8): 18-23. |
| 文伟平,汤炀,谌力. 一种基于Android内核的APP敏感行为检测方法及实现[J]. 信息网络安全,2016,16(8):18-23. | |
| [13] | ISOHARA T, TAKEMORI K, KUBOTA A.Kernel-based Behavior Analysis for Android Malware Detection[C]//IEEE. 7th International Conference on Computational Intelligence and Security, December 3-4, 2011, Hainan, China. Jersey: IEEE, 2012: 1011-1015. |
| [14] | WEN Weiping, MEI Rui, NING Ge, et al.Malware Detection Technology Analysis and Applied Research of Android Platform[J]. Journal on Communications, 2014, 35(8): 78-85. |
| [15] | TAM K, FEIZOLLAH A, ANUAR N B, et al.The Evolution of Android Malware and Android Analysis Techniques[J]. ACM Computing Surveys, 2017, 49(4): 1-41. |
| [16] | SADEGHI A, BAGHERI H, GARCIA J, et al.A Taxonomy and Qualitative Comparison of Program Analysis Techniques for Security Assessment of Android Software[J]. IEEE Transactions on Software Engineering, 2017, 43(6): 492-530. |
| [17] | BHATTACHARYA A, GOSWAMI R T. Comparative Analysis of Different Feature Ranking Techniques in Data Mining-based Android Malware Detection[EB/OL]. , 2018-3-13. |
| [18] | OZSOY M, KHASAWNEH K N, DONOVICK C, et al.Hardware-based Malware Detection using Low Level Architectural Features[J]. IEEE Transactions on Computers, 2016, 65(11): 3332-3344. |
| [19] | LI Guizhi, HAN Zhen, ZHOU Qihui, et al.A Detecting System for Android Malicious Behavior Based on Binder Information Flow[J]. Netinfo Security, 2016, 16(2): 54-59. |
| 李桂芝,韩臻,周启惠,等. 基于Binder信息流的Android恶意行为检测系统[J]. 信息网络安全,2016,16(2):54-59. | |
| [20] | SALEHI M, DARYABAR F, TADAYON M H.Welcome to Binder: A Kernel Level Attack Model for the Binder in Android Operating System[C]//IEEE. 8th International Symposium on Telecommunications, September 27-28, 2016, Tehran, Iran. New Jersey: IEEE, 2017: 156-161. |
| [1] | 雷青, 荆丽桦, 赵德明, 郑继龙. 基于深度学习的安卓APP视频枪支检测技术研究[J]. 信息网络安全, 2016, 16(9): 149-153. |
| [2] | 张涛, 裴蓓, 文伟平, 陈钟. 一种安卓平台下提权攻击检测系统的设计与实现[J]. 信息网络安全, 2016, 16(2): 15-21. |
| [3] | 林佳萍, 李晖. 安卓恶意软件检测研究综述[J]. 信息网络安全, 2016, 16(10): 80-88. |
| [4] | 杨刚, 温涛, 张玉清. Android漏洞库的设计与实现[J]. 信息网络安全, 2015, 15(9): 240-244. |
| [5] | 任伟, 柳坤, 周金. AnDa:恶意代码动态分析系统[J]. 信息网络安全, 2014, 14(8): 28-33. |
| [6] | 杨春晖, 严承华. 基于进程管理的安全策略分析[J]. 信息网络安全, 2014, 14(8): 61-66. |
| [7] | . Windows主机键盘记录技术对比分析[J]. , 2014, 14(6): 43-. |
| [8] | 何弦庭;叶小平;黄耿星. PE病毒感染行为重定向器设计与实现[J]. , 2013, 13(4): 0-0. |
| [9] | 刘文卓;丁杰;罗继明;李昕. 防键盘鼠标记录器的设计与实现[J]. , 2013, 13(3): 0-0. |
| [10] | 贾菲;刘威. 基于Android平台恶意代码逆向分析技术的研究[J]. , 2012, 12(4): 0-0. |
| [11] | 马国群;刘忆宁;龙腾飞;黄龙;张永昌;罗家华. 智能手机安全防护系统开发研究[J]. , 2011, 11(5): 0-0. |
| [12] | 张婷;张辉极. 智能手机安全问题及防护技术分析[J]. , 2011, 11(12): 0-0. |
| [13] | 卢立蕾;文伟平. Windows环境木马进程隐藏技术研究[J]. , 2009, 9(5): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||