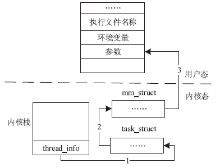
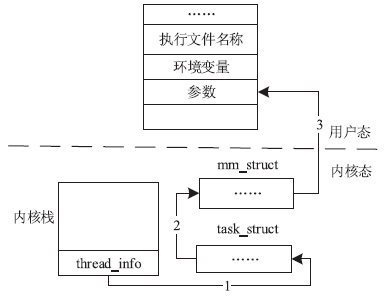
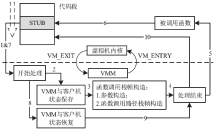
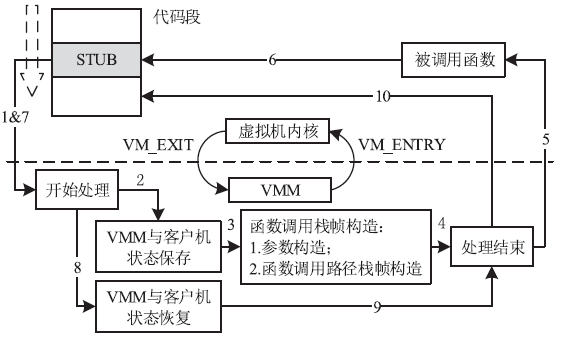
信息网络安全 ›› 2015, Vol. 15 ›› Issue (4): 56-61.doi: 10.3969/j.issn.1671-1122.2015.04.010
一种基于VMM的内核级Rootkit检测技术
- 四川大学计算机学院网络与可信计算研究所,四川成都 610065
-
收稿日期:2015-02-05出版日期:2015-04-10发布日期:2018-07-16 -
作者简介:作者简介: 张磊(1983-),男,四川,博士研究生,主要研究方向:信息安全、虚拟化技术;陈兴蜀(1968-),女,四川,教授,博士,主要研究方向:信息安全、计算机网络、云计算;任益(1990-),男,四川,硕士研究生,主要研究方向:信息安全、虚拟化技术;李辉(1989-),男,重庆,硕士研究生,主要研究方向:信息安全、虚拟化技术。
-
基金资助:国家自然科学基金[61272447];国家科技支撑计划[2012BAH18B05]
Kernel-level Rootkit Detection Technology Based on VMM
ZHANG Lei, CHEN Xing-shu( ), REN Yi, LI Hui
), REN Yi, LI Hui
- Network and Trusted Computing Institute, School of Computer Science, Sichuan Univ, Chengdu Sichuan 610065, China
-
Received:2015-02-05Online:2015-04-10Published:2018-07-16
摘要:
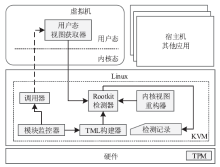
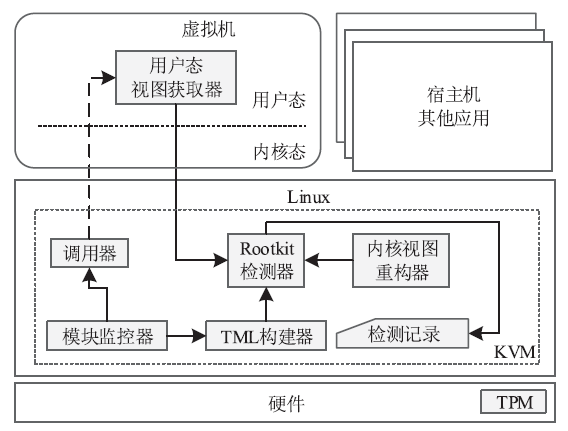
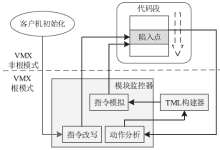
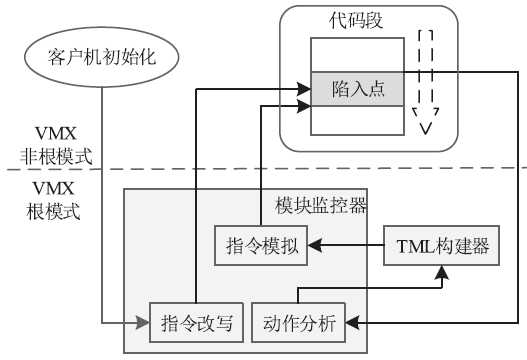
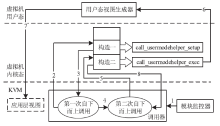
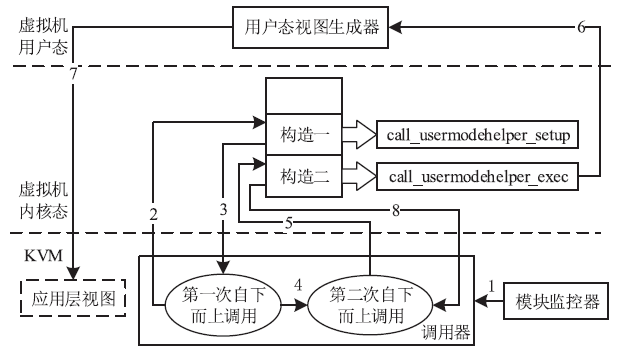
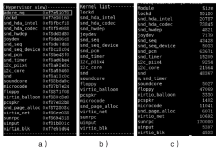
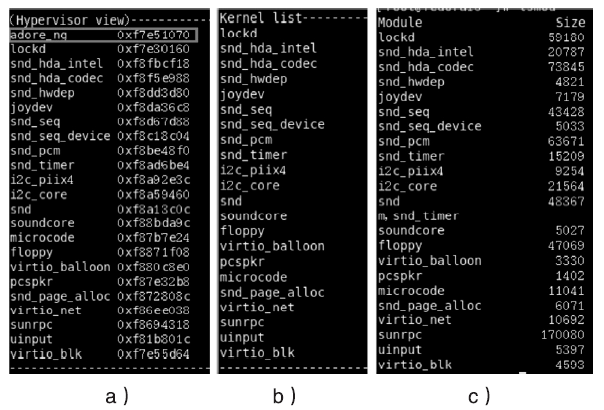
针对云平台中的虚拟机内核级Rootkit破坏租户虚拟机完整性的问题,文章提出一种基于VMM(虚拟机监视器,Virtual Machine Monitor)的内核级Rootkit检测技术。该技术以在关键路径设置陷入点的方式构建TML(True Module List),得到虚拟机中真实的内核模块视图,在VMM层利用自下而上的调用方式获取虚拟机用户态视图,并在VMM层获取重构的虚拟机内核态视图,通过交叉对比这三个视图检测隐藏在虚拟机中的Rootkit。最后,利用该技术在KVM(基于内核的虚拟机,Kernel-based Virtual Machine)中实现了原型系统,实验结果表明系统能迅速准确地检测出虚拟机中的Rootkit,并依据TML报告内核级Rootkit的详细信息,系统的综合性能损耗在可接受范围内。
中图分类号:
引用本文
张磊, 陈兴蜀, 任益, 李辉. 一种基于VMM的内核级Rootkit检测技术[J]. 信息网络安全, 2015, 15(4): 56-61.
ZHANG Lei, CHEN Xing-shu, REN Yi, LI Hui. Kernel-level Rootkit Detection Technology Based on VMM[J]. Netinfo Security, 2015, 15(4): 56-61.
| [1] | 袁源, 戴冠中. LKM后门综述[J]. 计算机科学,2008,35(7):5-8. |
| [2] | 刘喆,张家旺. Rootkit木马隐藏技术分析与检测技术综述[J]. 信息安全与通信保密,2010 ,(11):61-65. |
| [3] | 梁冰. Windows Rootkit实现及其检测技术分析[J]. 电子世界,2013,(9):13-15. |
| [4] | Mell P, Grance T.The NIST definition of cloud computing (draft)[J]. NIST special publication, 2011, 800(145):7-12. |
| [5] | Clark B, Deshane T, Dow E M, et al.Xen and the Art of Repeated Research[C]//USENIX Annual Technical Conference, FREENIX Track. 2004: 135-144. |
| [6] | KVM. Kernel based virtual machine[EB/OL] . |
| [7] | Payne B D, De Carbone M D P, Lee W. Secure and flexible monitoring of virtual machines[C]//Computer Security Applications Conference, 2007. ACSAC 2007. Twenty-Third Annual. IEEE, 2007: 385-397. |
| [8] | Nance K, Hay B, Bishop M. virtual machine introspection[J]. IEEE Computer Society, 2008. |
| [9] | Xiong H, Liu Z, Xu W, et al.Libvmi: A Library for Bridging the Semantic Gap between Guest OS and VMM[C]//Computer and Information Technology (CIT), 2012 IEEE 12th International Conference on. IEEE, 2012: 549-556. |
| [10] | 李博,沃天宇,胡春明,等.基于VMM的操作系统隐藏对象关联检测技术[J]. Journal of Software, 2013, 24(2). |
| [11] | Wang Y, Hu C, Li B.Vmdetector: a VMM-based platform to detect hidden process by multi-view comparison[C]//High-Assurance Systems Engineering (HASE), 2011 IEEE 13th International Symposium on. IEEE, 2011: 307-312. |
| [12] | 王丽娜,高汉军,刘炜,等.利用虚拟机监视器检测及管理隐藏进程[J]. 计算机研究与发展, 2011,48(8):1534-1541. |
| [13] | 李晔. 基于系统虚拟化技术的内核态Rootkit检测[D]. 哈尔滨:哈尔滨工业大学,2010. |
| [14] | Litty L, Lagar-Cavilla H A, Lie D. Hypervisor Support for Identifying Covertly Executing Binaries[C]//USENIX Security Symposium. 2008: 243-258. |
| [15] | Tomlinson A.Introduction to the TPM[M]//Smart Cards, Tokens, Security and Applications. New York: Spring US,2008:155-172. |
| [16] | Sailer R, Zhang X, Jaeger T, et al.Design and Implementation of a TCG-based Integrity Measurement Architecture[C]//USENIX Security Symposium. 2004, 13: 223-238. |
| [17] | L. McVoy and C. Staelin. lmbench: portable tools for performance analysis[C]//Proceedings of the 1996 annual conference on USENIX Annual Technical Conference. Berkeley: USENIX Association, 1996: 23-23. |
| [18] | 李琼,张宝昌. 基于在线拓扑模板更新的目标跟踪[J]. 信息网络安全,2014,(1):52-55. |
| [19] | 刘丽,周亚建. 二维条码数字水印技术研究[J]. 信息网络安全,2014,(1):56-60. |
| [20] | 康海燕,祈鑫,魏美荣. 中小型网站智能安全检测研究[J]. 信息网络安全,2014,(1):61-64. |
| [21] | 郭磊,胡晓勤,江天宇,等. 基于行为特征识别的网络诈骗嫌疑人追踪系统[J]. 信息网络安全,2014,(1):65-70. |
| [22] | 张红旗,刘江,代向东,等. 一种多级跨域访问控制管理模型[J]. 信息网络安全,2014,(2):1-6. |
| [23] | 王涛,胡爱群. 基于边界检测的IPSec VPN协议的一致性测试方法[J]. 信息网络安全,2014,(2):7-11. |
| [24] | 李艺颖,邓皓文,王思齐,等. 基于机器学习和NetFPGA的智能高速入侵防御系统[J]. 信息网络安全,2014,(2):12-19. |
| [25] | 段新东,林玉香,张鑫. 基于智能化自学习方式的入侵检测防护系统设计与实现[J]. 信息网络安全,2014,(2):20-26. |
| [26] | 高岳,胡爱群. 基于权限分析的Android隐私数据泄露动态检测方法[J]. 信息网络安全,2014,(2):27-31. |
| [27] | 晁沛,周亚建. 基于区域性构建支持向量机模型的空域水印算法[J]. 信息网络安全,2014,(2):32-36. |
| [28] | 唐文政,白成杰. 网络虚拟环境中两运动物体安全避障互寻相遇的一种算法及实现[J]. 信息网络安全,2014,(2):37-40. |
| [29] | 张涛,焦英楠,禄立杰,等. 一种基于Windows内核驱动的可疑样本采集系统的设计与实现[J]. 信息网络安全,2014,(2):41-47. |
| [30] | 朱圣才,徐御,王火剑. 常见源代码安全漏洞分析与研究[J]. 信息网络安全,2014,(2):48-52. |
| [31] | 王景中,凌晨. 基于节点认证的物联网感知层信息安全传输机制的研究[J]. 信息网络安全,2014,(2):53-57. |
| [32] | 夏戈明,史立哲,周文,等. 轻量级RFID双向通信认证协议优化方案[J]. 信息网络安全,2014,(2):58-62. |
| [33] | 陈敏欣,谢冬青,黄海. 环境监测有害成分的数据融合及其水质状况评价[J]. 信息网络安全,2014,(2):63-67. |
| [34] | 王威,吴羽翔,金鑫,等. 基于可信第三方的公有云平台的数据安全存储方案[J]. 信息网络安全,2014,(2):68-74. |
| [35] | 赵晓丹,徐燕. 垃圾邮件分类技术对比研究[J]. 信息网络安全,2014,(2):75-80. |
| [36] | 李卫,王文贤. QVOD资源爬行系统的研究与实现[J]. 信息网络安全,2014,(2):81-85. |
| [37] | 袁艳祥,游林. 基于身份加密的可认证密钥协商协议[J]. 信息网络安全,2014,(3):1-6. |
| [38] | 刘亚春,王景中. 基于人脸检测的网络图像内容过滤技术研究[J]. 信息网络安全,2014,(3):7-11. |
| [39] | 刘建忠,刘鎏,张云东,等. 二值图像中基于陡变度的拐角点集检测方法[J]. 信息网络安全,2014,(3):12-16. |
| [40] | 王文明. 机器人一体机远程监控平台的音视频传输研究与设计[J]. 信息网络安全,2014,(3):17-23. |
| [41] | 陈小兵. Linux操作系统root账号密码获取防范技术研究[J]. 信息网络安全,2014,(3):24-27. |
| [1] | 张健, 蔡长亮, 宫良一, 顾兆军. 基于KVM虚拟化环境的异常行为检测技术研究[J]. 信息网络安全, 2017, 17(11): 1-6. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||