信息网络安全 ›› 2015, Vol. 15 ›› Issue (5): 69-76.doi: 10.3969/j.issn.1671-1122.2015.05.011
高速网络下P2P流量识别研究
- 1.国家计算机网络应急技术处理协调中心辽宁分中心,辽宁沈阳 110036
2.中国移动通信集团辽宁有限公司,辽宁沈阳110179
-
收稿日期:2015-04-09出版日期:2015-05-10发布日期:2018-07-16 -
作者简介:作者简介: 穆筝(1981-),男,辽宁,工程师,硕士,主要研究方向:网络信息安全;吴进(1978-),男,辽宁,工程师,本科,主要研究方向:网络信息安全;许书娟(1982-),女,河北,工程师,硕士,主要研究方向:移动互联网。
-
基金资助:国家自然科学基金[61171193];国家科技支撑计划[2015BAK21B01]
Research on P2P Traffic Identification Under the High Speed Network
MU Zheng1( ), WU Jin1, XU Shu-juan2
), WU Jin1, XU Shu-juan2
- 1. CNCERT/CC-LN, Shenyang Liaoning 110036, China
2. China Mobile Group Liaoning co., ltd, Shenyang Liaoning 110179, China
-
Received:2015-04-09Online:2015-05-10Published:2018-07-16
摘要:
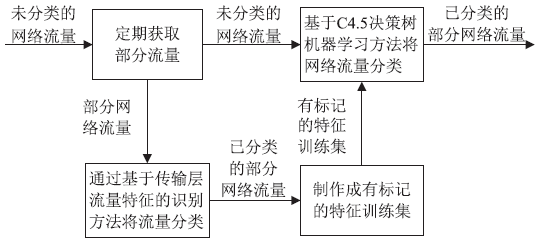
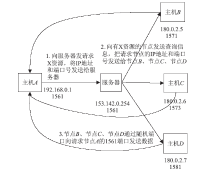
网络流量分类是指将混有各种应用的流量按照流量所使用的协议进行分类。网络流量分类一直是各界共同关注的热点之一。研究网络流量分类可以为设计下一代高性能网络协议提供基础,可以为网络管理和网络流量调度提供依据,可以为网络攻击防护和流量清洗提供支撑。文章分析了当今主流的网络流量识别方法,归纳总结了流量分类技术的发展现状和研究成果。文章针对P2P流量迅猛增长的现状和高速网络下数据流量的特性,重点研究高速网络下P2P流量的二元分类方法,首先采用基于传输层行为的流量识别方法将部分样本数据流分为P2P流量和非P2P流量,并根据分类结果动态生成有标记的特征训练集,有效避免了网络数据流发生变化后导致分类算法所使用的样本特征集不准确的情况;然后提出一种基于C4.5决策树算法的P2P流量识别方法,该方法只需计算一个数据流的前若干个数据包即可完成流量识别,无需考虑数据流的单双向和数据加密等问题。实验表明该方法识别准确率高,计算复杂度低,适用于高速网络下的流量识别。
中图分类号:
引用本文
穆筝, 吴进, 许书娟. 高速网络下P2P流量识别研究[J]. 信息网络安全, 2015, 15(5): 69-76.
MU Zheng, WU Jin, XU Shu-juan. Research on P2P Traffic Identification Under the High Speed Network[J]. Netinfo Security, 2015, 15(5): 69-76.
| [1] | WANG J, ZHOU Y, YANG Y, et al.Classify the majority of the total bytes on the Internet[C]//Information Processing (ISIP), 2008 International Symposiums on, Moscow, 2008. |
| [2] | KIM M S, KANG H J, HONG J W.Towards peer-to-peer traffic analysis using flows[C]//Self-Managing Distributed Systems, LNCS 2867. Berlin: Springer, 2004: 55-67. |
| [3] | 鲁刚,张宏莉,叶麟. P2P流量识别[J]. 软件学报,2011,22(6):1281-1298. |
| [4] | KARAGIANNIS T, BROIDO A, FALOUTSOS M.Transport layer identification of P2P traffic[C]//New York, NY, USA: ACM, 2004: 121-134. |
| [5] | HAFFNER P, SEN S, SPATSCHECK O, et al.ACAS: Automated construction of application signatures[C]//SIGCOMM’05 Workshops, New York, 2005: 197-202. |
| [6] | BASET S, SCHUNZRINNE H G.An analysis of the Skype peer-to-peer Internet telephony protocol[C]//Proceedings of the 25th IEEE International Conference on Computer Communications, USA: INFOCOM, 2006: 1-11. |
| [7] | 袁雪美,王晖. P2P流量识别技术综述[J]. 计算机应用,2009,29(5):12-13. |
| [8] | MARIOS I, PAPPU P, FALOUTSOS M. Network Traffic Analysis using Traffic Dispersion Graphs (TDGs):Techniques and Hardware Implementation[J]. Technical Report, 2007, UCR-CS-2007-05001: 15-18. |
| [9] | GU CHENGJIE, ZHANG SHUNYI, XUE XIAOZHEN.Encrypted Internet Traffic Classification Method based on Host Behavior[J]. Internet Journal of Digital Content Technology and its Applications, 2011, 5(3): 167-174. |
| [10] | BRANCH P A, HEYDE A, ARMITAGE G J.Rapid identification of Skype traffic flows[C]//NOSSDAV’09. USA: Virginia, 2009: 91-96. |
| [11] | FREIRE E P, ARTUR Z, RONALDO M.On Metrics to Distinguish Skype flows from HTTP traffic[J]. Journal of Network and Systems Management, 2009, 17(1-2): 57-66. |
| [12] | EHLERT S, SANDRINE PETGAND.Analysis and Signature of Skype VoIP Session Traffic[C]//Fraunhofer FOKUS Technical Report NGNI-SKYPE-06b, 2006:14-15. |
| [13] | IDREESS F, UZMA A K.A generic technique for Voice over Internet Protocol(VoIP) traffic detection[J]. IJCSNS International Journal of Computer Science and Network Security, 2008, 8(2): 52-59. |
| [14] | ROUGHAN M,SEN S,SPATSCHECK O.Class-of-service mapping for QoS: a statistical signature-based approach to IP traffic classification[C]//Proceedings of the 4th ACM SIG- COMM conference on Internet measurement. Taormina, Sicily, Italy: ACM, 2004: 135-148. |
| [15] | CONSTANTINOU F, MAVROMMATIS P.Identifying Known and Unknown Peer-to-Peer Traffic[J]. NCA, 2006: 93-102. |
| [16] | SEN S, WANG J.Analyzing peer-to-peer traffic across large networks[J]. IEEE-ACM TRANSACTIONS ON NETWORKING, 2004, 12(2): 219-232. |
| [17] | KARAGIANNIS T,PAPAGIANNAKI K,FALOUTSOS M.BLINC: multilevel traffic classification in the dark[C]// SIGCOMM’05, New York, 2005: 229-240. |
| [18] | ALSHAMMARI R, LICHODZIJEWSKI P, HEYWOOD M, et al.Classifying SSH Encrypted Traffic with Minimum Packet Header Features using Genetic Programming[C]//Defense applications of computational intelligence workshop, USA: GECCO, 2009: 2539-2546. |
| [19] | THANH V V, FUKUDA K, CHAN H N, et al.A study on P2P traffic characteristics evaluation in the WIDE backbone[C]//The 6th ICITA, USA, 2009: 286-291. |
| [20] | ESTEVES A F, INACIO P, PEREIRA M, et al.On-line Detection of Encrypted Traffic Generated by Mesh-Based Peer-to-Peer Live Streaming Applications: The Case of GoalBit[C]//IEEE 10th International Symposium on Network Computing and Applications, 2011: 223-228. |
| [21] | ROSSI D, VALENTI S.Fine-grained traffic classification with Netflow data[C]//IWCMC, France, 2010: 479-483. |
| [22] | Gomes J V P, INACIO P, FREIER M, et al. Analysis of Peer-to-Peer Traffic Using a Behavioural Method Based on Entropy[C]//The 27th IEEE IPCCC, USA, 2008: 201-208. |
| [23] | 鲁刚,张宏莉. P2P流量分类研究[J]. 智能计算机与应用,2013,3(3):2-3. |
| [24] | MUNZ G, HECKMULLER S, BRAUN L, et al.Improving Markov-based TCP Traffic Classification[C]//17th GI/ITC Conference on Communication in Distributed Systems, Viet nam, 2010: 61-72. |
| [25] | MOORE A W, ZUEV D.Internet Traffic Classification Using Bayesian Analysis Techniques[C]//SIGMETRICS’05, Canada: ACM, 2005: 50-60. |
| [26] | ERMAN J, ARLITT M F, MAHANTI A.Traffic classification using clustering algorithms[J]. MineNet, 2006: 281-286. |
| [27] | ERMAN J, MAHANTI A, ARLITT M F.Byte me: a case for byte accuracy in traffic classification[J]. MineNet, 2007: 35-38. |
| [28] | ABI P S.Efficient Detection of VoIP calls Hidden in Web Traffic[J]. IJTES, 2011, 2(1): 1-4. |
| [29] | AULD T, MOORE A W, GULL S F.Bayesian Neural networks for Internet Traffic Classification[J].IEEE Transactions on neural networks, 2007, 18(1): 223-239. |
| [30] | YUAN R X, LI Z, GUAN X H, et al.An SVM-based machine learning method for accurate internet traffic classification[J]. Information Systems Frontiers, 2010, 12(2): 149-156. |
| [31] | 戴磊. 流分类技术研究[D]. 北京:中科院计算所,2009. |
| [32] | SALGARELLI L, GRINGOLI F, KARAGIANNIS T.Comparing Traffic Classifiers[J]. ACM SIGCOMM Computer Communication Review, 2007, 37(3): 65-68. |
| [33] | KIM H, CLAFFY K, FOMENKOV M.Internet traffic Classification Demystified: Myths, Caveats and the Best Practices[C]//CoNEXT 2008, Madrid: ACM 2008: 10-12. |
| [34] | WILLIAMS N, ZANDER S, ARMITAGE G J.A preliminary performance comparison of five machine learning algorithms for practical IP traffic flow classification[J]. Computer Communication Review, 2006, 36(5): 5-16. |
| [35] | KIM H, BARMAN D, KWON T T, et al.NeTraMark: a network traffic classification benchmark[J]. Computer Communication Review, 2011, 41(1): 22-30. |
| [36] | COLLINS M, REITER M.Finding peer-to-peer file-sharing using coarse network behaviors[C]//The European Symposium on Research in Computer Security, Germany, 2006: 73-75. |
| [37] | DAINOTTI A, PESCAPE A, ROSSI P S.Internet traffic modeling by means of Hidden Markov Models[J]. Computer Networks, 2008, (52): 2645-2662. |
| [1] | 闫苗, 马占友, 姜子姝, 秦国丽. 基于N抢占策略且播放器数可变的P2P网络性能分析[J]. 信息网络安全, 2022, 22(12): 87-95. |
| [2] | 陈良臣, 高曙, 刘宝旭, 卢志刚. 网络加密流量识别研究进展及发展趋势[J]. 信息网络安全, 2019, 19(3): 19-25. |
| [3] | 王旭东, 余翔湛, 张宏莉. 面向未知协议的流量识别技术研究[J]. 信息网络安全, 2019, 19(10): 74-83. |
| [4] | 刘浩, 陈志刚, 张连明. P2P网络中基于准入度的任务访问控制模型[J]. 信息网络安全, 2017, 17(6): 22-29. |
| [5] | 刘浩, 羊四清, 陈志刚. 云计算环境中抗欺诈行为的P2P文件共享激励机制研究[J]. 信息网络安全, 2017, 17(11): 37-43. |
| [6] | 车浩然, 何永忠, 刘吉强. 基于P2P和网格ID的位置匿名算法研究[J]. 信息网络安全, 2015, 15(3): 28-32. |
| [7] | . 基于VOIP的语音视频流量监控方案设计与实施[J]. , 2014, 14(6): 53-. |
| [8] | 姚洪波;孟正;李希;文伟平. 基于 P2P 的远程控制系统设计与实现[J]. , 2014, 14(3): 0-0. |
| [9] | . 基于 P2P 的远程控制系统设计与实现[J]. , 2014, 14(3): 32-. |
| [10] | 马苑;罗永龙;刘飞;黄刘生. P2P安全防护机制研究与分析[J]. , 2013, 13(12): 0-0. |
| [11] | 元业云;郑哲星. 基于Skype P2P混合模式网络的流量控制技术的研究[J]. , 2012, 12(11): 0-0. |
| [12] | 徐京;张彦;辛阳;朱洪亮. 高速网络内容监控系统的关键技术分析[J]. , 2012, 12(10): 0-0. |
| [13] | 张瀚;朱洪亮;辛阳. 基于DPI技术的P2P流量检测系统设计[J]. , 2012, 12(10): 0-0. |
| [14] | 魏玉人;于洪跃. 基于秘密群的分布式认证[J]. , 2010, (9): 0-0. |
| [15] | 王伟;张利刚;何伟. P2P流量主动识别技术在防火墙中的实现[J]. , 2010, (5): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||