信息网络安全 ›› 2018, Vol. 18 ›› Issue (5): 24-31.doi: 10.3969/j.issn.1671-1122.2018.05.003
基于深度无合成误差模型的三维图像可逆信息隐藏方法研究
- 湖南大学信息科学与工程学院,湖南长沙 410082
-
收稿日期:2018-01-15出版日期:2018-05-15发布日期:2020-05-11 -
作者简介:作者简介:欧博(1985—),男,湖南,助理教授,博士,主要研究方向为信息安全、计算机视觉;石向莲(1993—),女,湖南,硕士研究生,主要研究方向为图像可逆信息隐藏。
-
基金资助:国家自然科学基金[61502160]
Reversible Data Hiding for Three-dimensional Image Based on Depth No-synthesis-error Model
- College of Computer Science and Electronic Engineering, Hunan University, Changsha Hunan 410082, China
-
Received:2018-01-15Online:2018-05-15Published:2020-05-11
摘要:
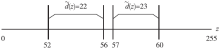
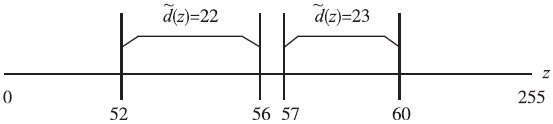
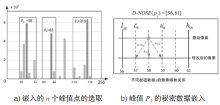
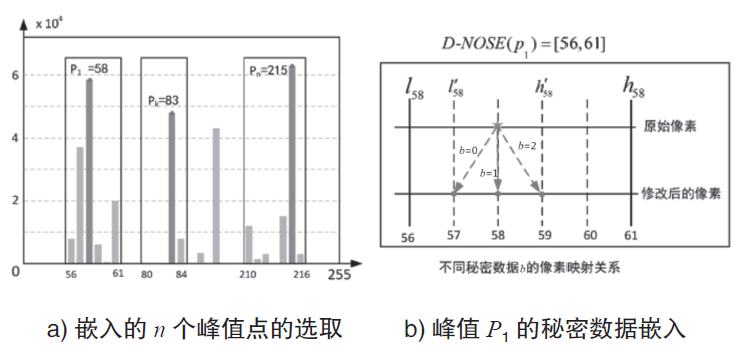
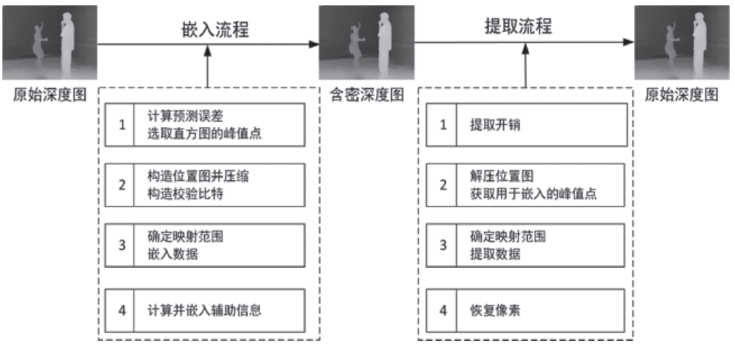
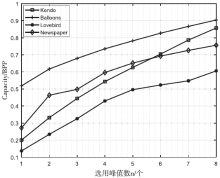
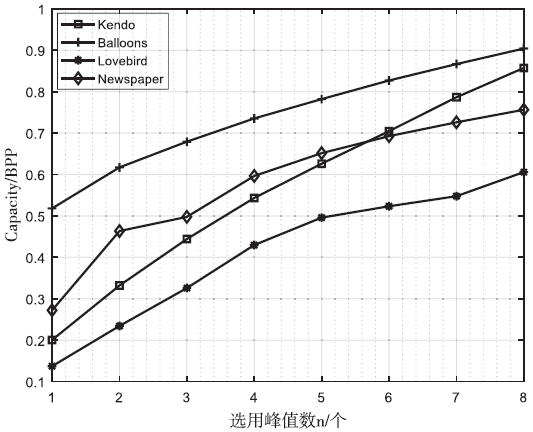
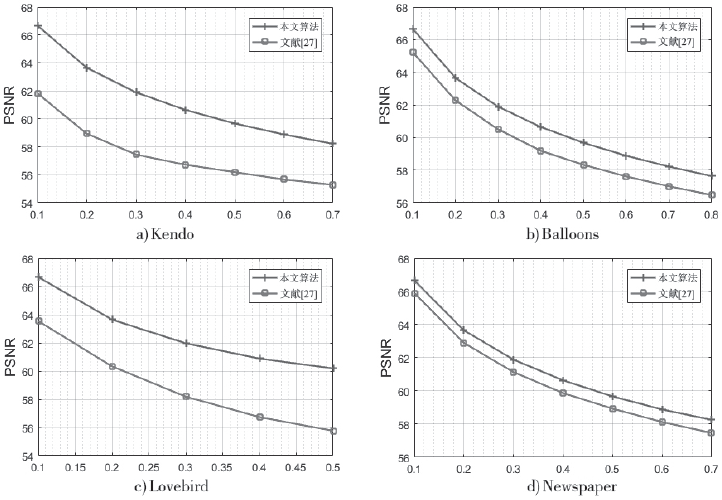
传统的可逆信息隐藏方法主要针对传统二维(2D)图像,极少有研究涉及三维(3D)图像。3D可逆信息隐藏方法以深度图为嵌入载体,通过2D图像和深度图合成3D图像,并实现无损于3D图像的数据嵌入。但现有算法还存在嵌入性能欠佳的缺点,为此文章提出了一种基于深度无合成误差(D-NOSE)模型的3D合成图像的可逆信息隐藏方法。该方法结合预测误差扩展算法和直方图移位算法,以预测误差值与像素频数两者来优选嵌入像素,通过控制选用的峰值数量和像素映射范围,来实现嵌入质量的提升以及容量的自适应控制。实验结果表明,该方法具有良好的嵌入性能,一方面能自适应调节嵌入容量,另一方面能提升嵌入载体深度图的嵌入质量。
中图分类号:
引用本文
欧博, 石向莲. 基于深度无合成误差模型的三维图像可逆信息隐藏方法研究[J]. 信息网络安全, 2018, 18(5): 24-31.
Bo OU, Xianglian SHI. Reversible Data Hiding for Three-dimensional Image Based on Depth No-synthesis-error Model[J]. Netinfo Security, 2018, 18(5): 24-31.
| [1] | FEHN C. Depth-image-based Rendering (DIBR), Compression,Transmission for a New Approach on 3D-TV[EB/OL].,2017-7-15. |
| [2] | TIAN D,LAI P L, LOPEZ P, et al. View Synthesis Techniques for 3D Video[EB/OL]. ,2017-7-15. |
| [3] | TIAN J.Reversible Data Embedding Using a Difference Expansion[J]. IEEE Transactions on Circuits and Systems for Video Technology, 2003, 13(8): 890-896. |
| [4] | ALATTAR A M.Reversible Watermark Using the Difference Expansion of a Generalized Integer Transform[J]. IEEE Transactions on Image Processing, 2004, 13(8):1147-56. |
| [5] | HU Y, LEE H K, CHEN K, et al.Difference Expansion Based Reversible Data Hiding Using Two Embedding Directions[J]. IEEE Transactions on Multimedia, 2008, 10(8):1500-1512. |
| [6] | LI X, ZHANG W,GUI X, et al.A Novel Reversible Data Hiding Scheme Based on Two-dimensional Difference-histogram Modification[J]. IEEE Transactions on Information Forensics and Security, 2013, 8(7): 1091-1100. |
| [7] | KIM H J, SACHNEV V, SHI Y Q, et al.A Novel Difference Expansion Transform for Reversible Data Embedding[J]. IEEE Transactions on Information Forensics and Security, 2008, 3(3): 456-465. |
| [8] | NI Z, SHI Y Q, ANSARi N, et al.Reversible Data Hiding[J]. IEEE Transactions on Circuits and Systems for Video Technology, 2006, 16(3): 354-362. |
| [9] | LEE S,SUH Y,HO Y.Reversiblee Image Authentication Based on Watermarking[C]//IEEE. IEEE International Conference on Multimedia and Expo, July 9-12, 2006, Toronto, Ont, Canada. New York:IEEE, 2006:1321-1324. |
| [10] | ARABZADEH M, Helfroush M S, Danyali H, et al.Reversible Watermarking Based on Generalized Histogram Shifting[C]// IEEE. IEEE International Conference on Image Processing, September 11-14, 2011, Brussels, Belgium. New York:IEEE, 2011: 2741-2744. |
| [11] | AN L,GAO X,YUAN Y, et al.Robust Lossless Data Hiding Using Clustering and Statistical Quantity Histogram[J]. Neurocomputing, 2012, 77(1): 1-11. |
| [12] | OU B,LI X,WANG J.Improved PVO-based Reversible Data Hiding: a New Implementation Based on Multiple Histograms Modification[J]. Journal of Visual Communication and Image Representation, 2016, 38(7): 328-339. |
| [13] | PENG F,ZHOU D,Long M, et al.Discrimination of Natural Images and Computer Generated Graphics Based on Multi-fractal and Regression Analysis[J].AEU-international Journal of Electronics and Communications, 2017, 71(1): 72-81. |
| [14] | THODI D M, RODRIGUEZ J J.Expansion Embedding Techniques for Reversible Watermarking[J]. IEEE Transactions on Image Processing, 2007, 16(3): 721-730. |
| [15] | SACHNEV V,KIM H J,NAM J, et al.Reversible Watermarking Algorithm Using Sorting and Prediction[J]. IEEE Transactions on Circuits and Systems for Video Technology, 2009, 19(7): 989-999. |
| [16] | LI X,YANG B,ZENG T.Efficient Reversible Watermarking Based on Adaptive Prediction-error Expansion and Pixel Selection[J]. IEEE Transactions on Image Processing a Publication of the IEEE Signal Processing Society, 2011, 20(12):3524-33. |
| [17] | CHANG C C,HUANG Y H,TSAI H Y, et al.Prediction-based Reversible Data Hiding Using the Difference of Neighboring Pixels[J].AEUE-international Journal of Electronics and Communications, 2012, 66(9):758-766. |
| [18] | OU B,Li X,ZHAO Y, et al.Pairwise Prediction-error Expansion for Efficient Reversible Data Hiding[J]. IEEE Transactions on Image Processing, 2013, 22(12): 5010-5021. |
| [19] | WU H T,HUANG J.Reversible Image Watermarking on Prediction Errors by Efficient Histogram Modification[J]. Signal Processing, 2012, 92(12): 3000-3009. |
| [20] | COLTUC D,CHASSERY J M.Very Fast Watermarking by Reversible Contrast Mapping[J].IEEE Signal Processing Letters, 2007, 14(4): 255-258. |
| [21] | LEE S,CHANG D Y,KALKER T.Reversible Image Watermarking Based on Integer-to-Integer Wavelet Transform[J]. IEEE Transactions on Information Forensics and Security, 2007, 2(3):321-330. |
| [22] | WANG X,LI X,YANG B, et al.Efficient Generalized Integer Transform for Reversible Watermarking[J]. IEEE Signal Processing Letters, 2010, 17(6): 567-570. |
| [23] | WENG S,ZHAO Y,PAN J S, et al.Reversible Watermarking Based on Invariability and Adjustment on Pixel Pairs[J]. IEEE Signal Processing Letters, 2008, 15(20):721-724. |
| [24] | COLTUC D.Low Distortion Transform for Reversible Watermarking[J]. IEEE Transactions on Image Processing a Publication of the IEEE Signal Processing Society, 2012, 21(1):412-417. |
| [25] | LIN Y H,WU J L.A Digital Blind Watermarking for Depth-image-based Rendering 3D Images[J]. IEEE Transactions on Broadcasting, 2011, 57(2): 602-611. |
| [26] | KIM H D,LEE J W,OH T W,et al.Robust DT-CWT Watermarking for DIBR 3D Images[J]. IEEE Transactions on Broadcasting, 2012, 58(4): 533-543. |
| [27] | CHUNG K L,YANG W J,YANG W N.Reversible Data Hiding for Depth Maps Using the Depth No-synthesis-error Model[J]. Information Sciences, 2014, 269(6): 159-175. |
| [28] | ZHAO Y,ZHU C,CHEN Z, et al.Depth No-synthesis-error Model for View Synthesis in 3-D Video[J]. IEEE Transactions on Image Processing, 2011, 20(8): 2221-2228. |
| [1] | 唐洪琼, 钮可, 张英男, 杨晓元. 自适应二维直方图迁移的视频可逆隐写算法[J]. 信息网络安全, 2019, 19(9): 106-110. |
| [2] | 肖迪, 王莹, 常燕廷, 周佳奇. 基于加法同态与多层差值直方图平移的密文图像可逆信息隐藏算法[J]. 信息网络安全, 2016, 16(4): 9-16. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||