信息网络安全 ›› 2018, Vol. 18 ›› Issue (3): 70-77.doi: 10.3969/j.issn.1671-1122.2018.03.009
基于Shapelet的恶意代码检测方法
- 北京航空航天大学计算机学院,北京100191
-
收稿日期:2017-11-30出版日期:2018-03-15发布日期:2020-05-11 -
作者简介:作者简介:李云春(1972—),男,陕西,教授,博士,主要研究方向为并行计算、计算机网络、网络安全和教育信息化;鲁文涛(1991—),男,河南,硕士研究生,主要研究方向为网络与信息安全;李巍(1970—),女,北京,副教授,博士,主要研究方向为移动网络安全、新型网络体系结构及网络测量、高性能计算与分布式应用性能分析。
-
基金资助:国家自然科学基金[2016YFB1000304]
Malware Detection Method Based on Shapelet
Yunchun LI( ), Wentao LU, Wei LI
), Wentao LU, Wei LI
- School of Computer Science and Engineering, Beihang University, Beijing 100191, China
-
Received:2017-11-30Online:2018-03-15Published:2020-05-11
摘要:
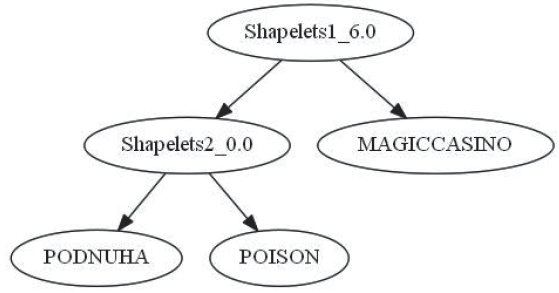
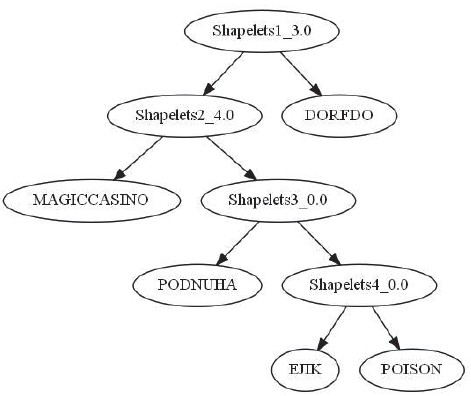
针对基于传统恶意代码签名的恶意代码检测方法在检测恶意代码时难以应对变形、多态与其他恶意代码变异技术等问题,以及在检测过程中最坏情况下的时间复杂度过高的特点,文章基于恶意代码在沙箱中运行时使用的API调用序列,利用时间序列数据分类中的Shapelet思想构建可用于恶意代码分类的恶意代码分类树。实验结果表明该方法不仅能够应对恶意代码变异技术,还可以缩短恶意代码检测的时间。
中图分类号:
引用本文
李云春, 鲁文涛, 李巍. 基于Shapelet的恶意代码检测方法[J]. 信息网络安全, 2018, 18(3): 70-77.
Yunchun LI, Wentao LU, Wei LI. Malware Detection Method Based on Shapelet[J]. Netinfo Security, 2018, 18(3): 70-77.
| [1] | SANTOS I, PENYA Y K, DEVESA J, et al. N-grams-based File Signatures for Malware Detection[EB/OL]. . |
| [2] | STOLFO S J, WANG K. ApparatusMethod and Medium for Detecting Payload Anomaly Using N-gram Distribution of Normal Data: U.S. Patent 7639714[P].2009-12-29. |
| [3] | IDIKA N, MATHUR A P.A Survey of Malware Detection Techniques[D]. West Lafayette:Purdue University, 2007. |
| [4] | TABISH S M, SHAFIQ M Z, FAROOQ M.Malware Detection Using Statistical Analysis of Byte-level File Content[C]//ACM. 18th USENIX Security Symposium, August 10-14, 2009, Montreal, Canada. Berkeley: USENIX, 2009: 23-31. |
| [5] | BAYSA D, LOW R M, STAMP M.Structural Entropy and Metamorphic Malware[J]. Journal of Computer Virology and Hacking Techniques, 2013, 9(4): 179-192. |
| [6] | PATRI O, WOJNOWICZ M, WOLFF M. Discovering Malware with Time Series Shapelets[EB/OL]. , 2017-10-26. |
| [7] | KOLBITSCH C, COMPARETTI P M, KRUEGEL C, et al.Effective and Efficient Malware Detection at the End Host[C]//ACM. 18th USENIX Security Symposium, August 10-14, 2009, Montreal, Canada. Berkeley: USENIX, 2009: 351-366. |
| [8] | YIN H, SONG D, EGELE M, et al.Panorama:Capturing System-wide Information Flow for Malware Detection and Analysis[C]//Association for Computing Machinery. Proceedings of the 14th ACM Conference on Computer and Communications Security, October 29-November 02, 2007, Alexandria, VA, USA. New York: ACM, 2007: 116-127. |
| [9] | BRUSCHI D, MARTIGNONI L, MONGA M.Detecting Self-mutating Malware Using Control-flow Graph Matching[C]//German Society of Informatics (GI). DIMVA, July 13-14, 2006, Berlin, Germany. Verlag Berlin Heidelberg:Springer, 2006:129-143. |
| [10] | CESARE S, XIANG Y.Malware Variant Detection Using Similarity Search over Sets of Control Flow Graphs[C]//IEEE. Trust, Security and Privacy in Computing and Communications (TrustCom), November 16-18, 2011, Changsha, China. Piscataway: IEEE, 2011: 181-189. |
| [11] | BONFANTE G, KACZMAREK M, MARION J Y. Control Flow Graphs as Malware Signatures[EB/OL]. . |
| [12] | Sæbjørnsen A, WILLCOCK J, PANAS T, et al.Detecting Code Clones in Binary Executables[C]//ACM. Proceedings of the Eighteenth International Symposium on Software Testing and Analysis, July 19-23, 2009, Chicago, IL, USA. New York: ACM, 2009: 117-127. |
| [13] | YE L, KEOGH E.Time Series Shapelets: a New Primitive for Data Mining[C]//ACM. Proceedings of the 15th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, June 28-July 1, 2009, Paris, France. New York: ACM, 1971: 17-38. |
| [14] | TANG Y, CHEN S.Defending against Internet Worms: a Signature-based Approach[C]//IEEE. 24th Annual Joint Conference of the IEEE Computer and Communications Societies, March 13-17, 2005, Miami, FL, USA. Piscataway: IEEE, 2005: 1384-1394. |
| [15] | WANG K, STOLFO S J.Anomalous Payload-based Network Intrusion Detection[C]//Eurécom Institute. 7th International Symposium, September 15-17, 2004, France. Verlag Berlin Heidelberg: Springer, 2004: 203-222. |
| [16] | KREIBICHC, CROWCROFT J.Honeycomb: Creating Intrusion Detection Signatures Using Honeypots[J]. ACM SIGCOMM Computer Communication Review, 2004, 34(1): 51-56. |
| [17] | CHRISTODORESCU M, JHA S, SESHIA S A, et al.Semantics-aware Malware Detection[C]//IEEE. Proceedings of the 2005 IEEE Symposium on Security and Privacy, May 8-11, 2005, Los Angeles, Oakland, CA, USA. Piscataway: IEEE, 2005: 32-46. |
| [18] | YEGNESWARAN V, GIFFIN J T, BARFORD P, et al.An Architecture for Generating Semantic Aware Signatures[C]//USENIX. Proceedings of the 14th USENIX Security Symposium, July 31-August 5, 2005, Baltimore, MD USA. Berkeley: USENIX, 2005: 97-112. |
| [19] | NEWSOME J, KARP B, SONG D.Polygraph: Automatically Generating Signatures for Polymorphic Worms[C]//IEEE. Proceedings of the 2005 IEEE Symposium on Security and Privacy, May 8-11, 2005, Los Angeles, Oakland, CA, USA. Piscataway: IEEE, 2005: 226-241. |
| [20] | SINGH S, ESTAN C, VARGHESE G, et al. Automated Worm Fingerprinting [EB/OL]. , 2017-10-24. |
| [21] | FILIOL E, JOSSE S.A Statistical Model for Undecidable Viral Detection[J]. Journal in Computer Virology, 2007, 3(2): 65-74. |
| [22] | TAHAN G, GLEZER C, ELOVICI Y, et al.Auto-sign: an Automatic Signature Generator for High-speed Malware Filtering Fevices[J]. Journal in Computer Virology, 2010, 6(2): 91-103. |
| [23] | TRINIUS P, WILLEMS C, HOLZ T, et al. A Malware Instruction Set for Behavior-based Analysis[EB/OL]. , 2017-10-12. |
| [24] | RAKTHANMANON T, KEOGH E.Fast Shapelets: a Scalable Algorithm for Discovering Time Series Shapelets[C]//SIAM. Proceedings of the 2013 SIAM International Conference on Data Mining, May 2-4, 2013, Austin, Texas. Berlin: Springer, 2013: 668-676. |
| [25] | RIECK K, TRINIUS P, WILLEMS C, et al.Automatic Analysis of Malware Behavior Using Machine Learning[J]. Journal of Computer Security, 2011, 19(4): 639-668. |
| [1] | 张家旺, 李燕伟. 基于N-gram算法的恶意程序检测系统研究与设计[J]. 信息网络安全, 2016, 16(8): 74-80. |
| [2] | . 电力移动智能终端安全技术研究[J]. , 2014, 14(4): 70-. |
| [3] | 金玉荣;谢亿鑫;杨奕;张博. 一个多重变形vbs木马解码分析[J]. , 2013, 13(12): 0-0. |
| [4] | 罗文华. 基于抽象解释理论抽取多态恶意程序特征码[J]. , 2013, 13(1): 0-0. |
| [5] | 彭国军;王泰格;邵玉如;刘梦冷. 基于网络流量特征的未知木马检测技术及其实现[J]. , 2012, 12(10): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||