信息网络安全 ›› 2015, Vol. 15 ›› Issue (1): 1-5.doi: 10.3969/j.issn.1671-1122.2015.01.001
• 等级保护 • 下一篇
一种可信虚拟平台构建方法的研究和改进
- 1. 公安部第一研究所,北京 100048
2. 北京搜狐新动力信息技术有限公司,北京 100190
Research and Improvement on Constructing Method of A Trusted Virtualization Platform
LI Hai-wei1( ), FAN Bo1, LI Wen-feng2
), FAN Bo1, LI Wen-feng2
- 1. The First Research Institute of the Ministry of Public Security of P.R.C,Beijing 100048, China
2. Beijing Sohu New Power Information Technology Co.,Beijing 100190, China
摘要:
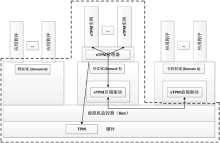
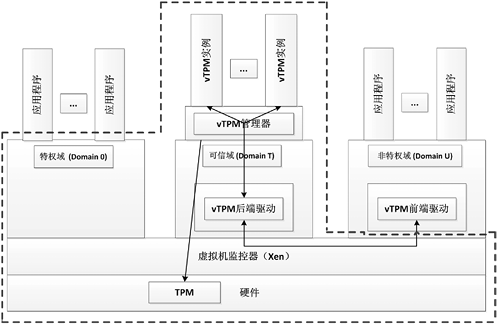
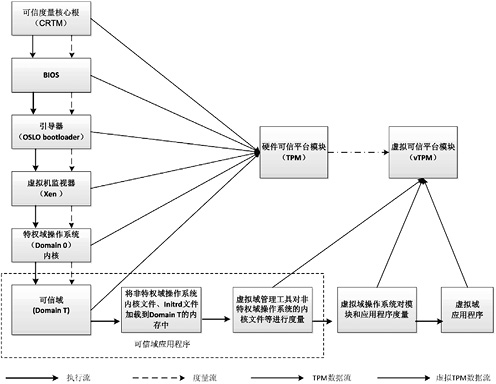
为了减小虚拟环境下虚拟可信平台模块(vTPM)实例及系统软件可信计算基(TCB)的大小,同时进一步保护vTPM组件的机密性、完整性和安全性,解决传统虚拟可信计算平台下可信边界难以界定的问题,文章提出了一种新的构建可信虚拟平台的方法和模型。首先,将Xen特权域Domain 0用户空间中弱安全性的域管理工具、vTPM相关组件等放置于可信域Domain T中,以防止来自Domain 0中恶意软件的攻击及内存嗅探,同时作为Xen虚拟层上面的安全服务实施框架,Domain T可以给vTPM的相关组件提供更高级别的安全保护。其次,通过重构Domain 0中拥有特权的管理和控制应用软件,将特权域的用户空间从可信计算基中分离出来,进而减小虚拟可信平台可信计算基的大小。最后,设计并实现了新的基于可信虚拟平台的可信链构建模型。通过与传统可信虚拟平台比较,该系统可以有效实现将虚拟化技术和可信计算技术相融合,并实现在一个物理平台上同时运行多个不同可信级别的操作系统,且保证每个操作系统仍然拥有可信认证等功能。
中图分类号: