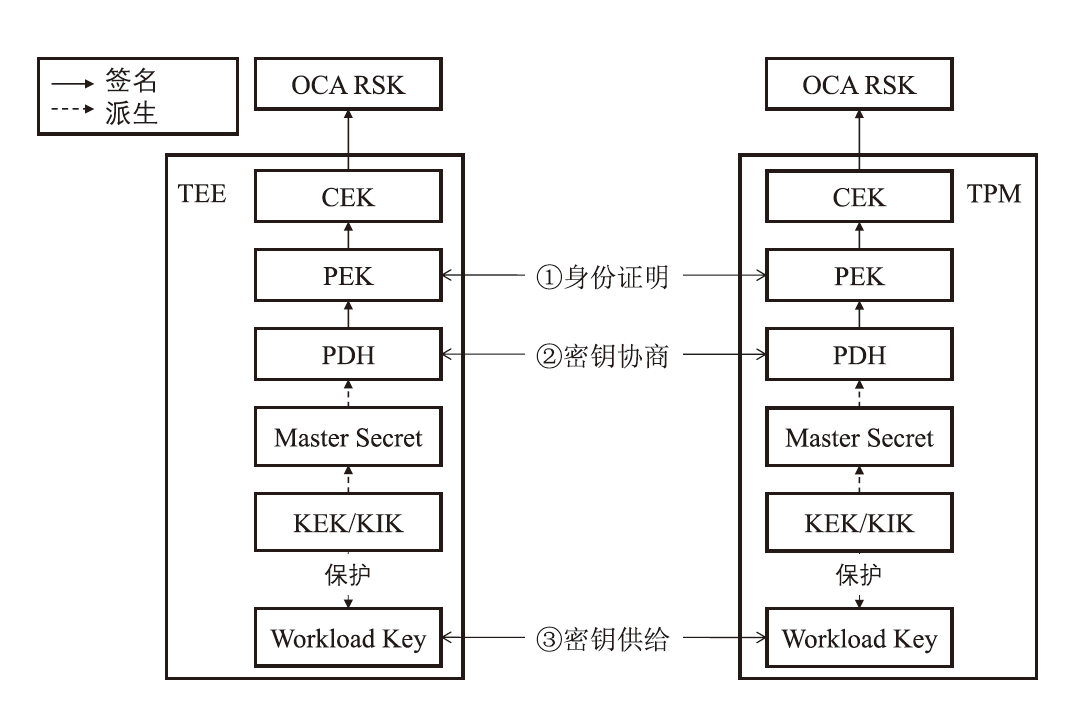
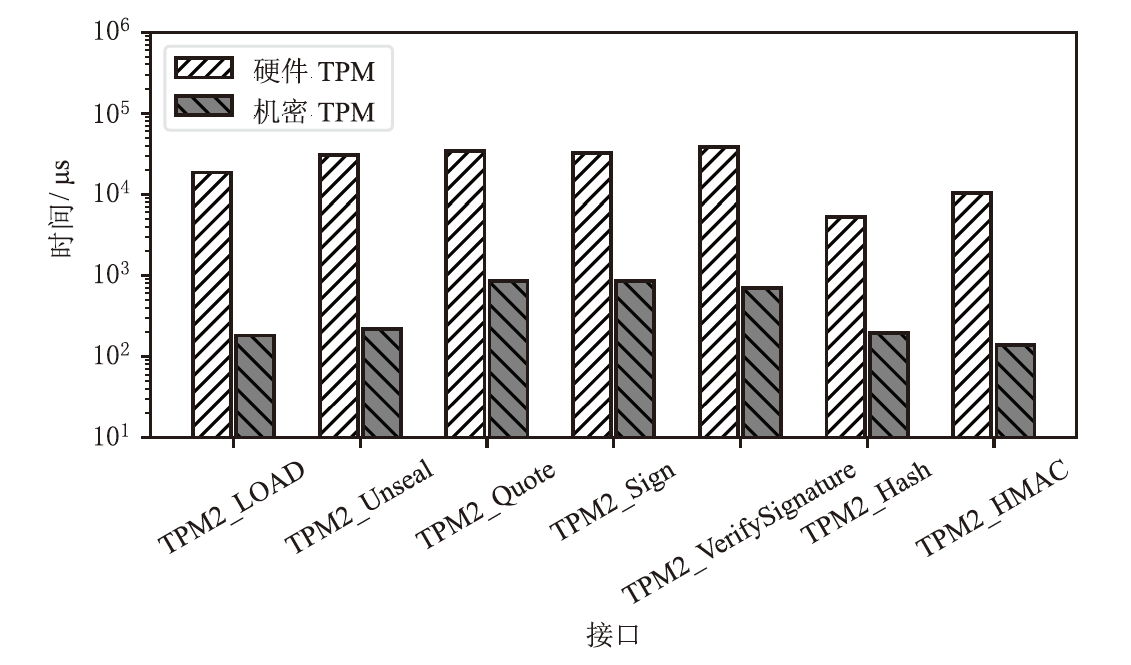
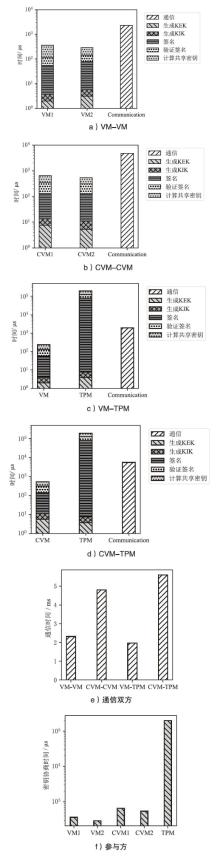
Netinfo Security ›› 2025, Vol. 25 ›› Issue (11): 1792-1810.doi: 10.3969/j.issn.1671-1122.2025.11.011
Previous Articles Next Articles
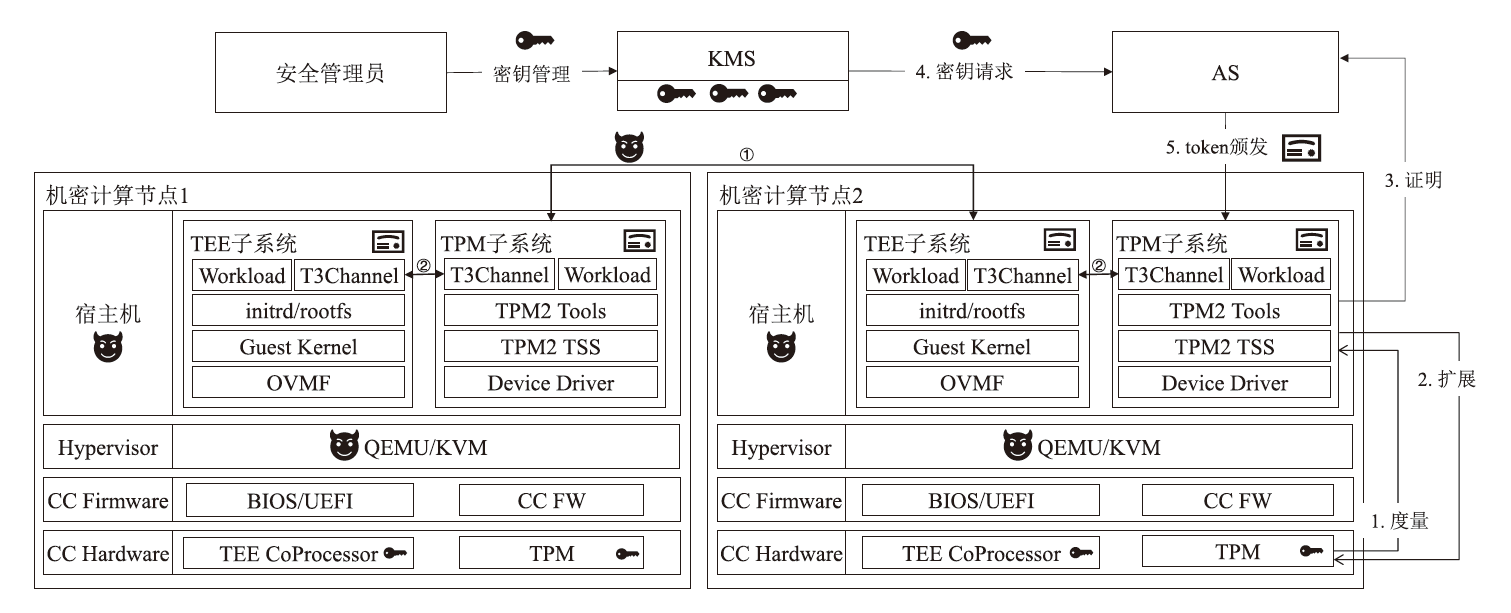
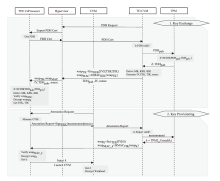
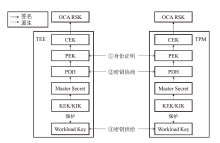
A Hardware Trusted Channel Construction Scheme Based on TEE and TPM for Confidential Computing Platforms
JIN Wa1,2, QIN Yu1( ), LIU Jingrun2, SHANG Ketong1, JIA Menghan1,2, LIN Jiangnan1
), LIU Jingrun2, SHANG Ketong1, JIA Menghan1,2, LIN Jiangnan1
1. Trusted Computing and Information Assurance Laboratory ,Institute of Software Chinese Academy of Sciences Beijing 100190, China 2. University of Chinese Academy of Sciences Beijing 100049, China
-
Received:2025-07-08Online:2025-11-10Published:2025-12-02
CLC Number:
Cite this article
JIN Wa, QIN Yu, LIU Jingrun, SHANG Ketong, JIA Menghan, LIN Jiangnan. A Hardware Trusted Channel Construction Scheme Based on TEE and TPM for Confidential Computing Platforms[J]. Netinfo Security, 2025, 25(11): 1792-1810.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.11.011
| 符号 | 描述 |
|---|---|
| 非对称密钥对,其中,sk为私钥,pk为公钥 | |
| KDF(Z, info) | 密钥派生函数,用于在ECDH密钥协商中基于共享秘密值Z和信息info派生对称密钥 |
| token | AS颁发给可信设备的可验证凭据 |
| D=(q, FR,a,b,{SEED},G, n,h) | 生成EC密钥对使用的域参数 |
| 使用密钥k对消息m加密 | |
| 使用密钥k计算消息m的HMAC值 | |
| 使用密钥k对消息m签名 | |
| x||y | x和y的串联 |
| x·y | 整数x与整数y相乘 |
| [n]P | 整数n与点P相乘 |
| [1] |
FENG Dengguo, QIN Yu, FENG Wei, et al. Survey of Research on Confidential Computing[J]. IET Communications, 2024, 18(9): 535-556.
doi: 10.1049/cmu2.v18.9 URL |
| [2] | FENG Dengguo, QIN Yu. Confidential Computing: Progress and Prospects[J]. Communications of China Computer Federation, 2024, 20(12): 38-46. |
| 冯登国, 秦宇. 机密计算:进展与展望[J]. 中国计算机学会通讯, 2024, 20(12):38-46. | |
| [3] | Confidential Computing Consortium. A Technical Analysis of Confidential Computing[R]. San Francisco:Linux Foundation, v1.2, 2021. |
| [4] | TPM 2.0 Library Specification Revision 1.59 Part 1: Architecture[S]. Beaverton: Trusted Computing Group, 2019. |
| [5] | NVIDIA. Introduction to DGX A100[EB/OL]. (2024-10-16)[2025-07-04]. https://docs.nvidia.com/dgx/dgxa100-user-guide/introduction-to-dgxa100.html. |
| [6] | BERGER S, CACERES R, GOLDMAN K A, et al. vTPM: Virtualizing the Trusted Platform Module[C]// USENIX. The 15th USENIX Security Symposium. Berkeley: USENIX, 2006: 305-320. |
| [7] | Inclavare Containers. RATS-TLS Project[EB/OL]. (2025-04-21)[2025-07-07]. https://github.com/inclavare-containers/rats-tls. |
| [8] | HALDERMAN J A, SCHOEN S D, HENINGER N, et al. Lest We Remember: Cold Boot Attacks on Encryption Keys[C]// USENIX. 17th USENIX Security Symposium. Berkeley: USENIX, 2008: 68-78. |
| [9] | CHEN Weijie. Research on Side-Channel Defenses for Trusted Execution Environment Based on Real-Time Monitoring[D]. Wuhan: Huazhong University of Science and Technology, 2024. |
| 陈维杰. 基于实时监测的可信执行环境侧信道防御研究[D]. 武汉: 华中科技大学, 2024. | |
| [10] | FU Jianming, LIU Xiuwen, TANG Yi, et al. Survey of Memory Address Leakage and Its Defense[J]. Journal of Computer Research and Development, 2016, 53(8): 1829-1849. |
| 傅建明, 刘秀文, 汤毅, 等. 内存地址泄漏分析与防御[J]. 计算机研究与发展, 2016, 53(8):1829-1849. | |
| [11] | RFC 9334 Remote Attestation Procedures Architecture[S]. Internet Engineering Task Force (IETF), 2023. |
| [12] | Veraison Project. Veraison[EB/OL]. (2025-07-04)[2025-07-07]. https://github.com/veraison. |
| [13] | Intel. Intel® Enhanced Privacy ID (EPID) Security Technology[EB/OL]. (2021-07-13)[2025-07-04]. https://www.intel.com/content/www/us/en/developer/articles/technical/intel-enhanced-privacy-id-epid-security-technology.html. |
| [14] | Intel. Intel Software Guard Extensions Data Center Attestation Primitives Quick Install Guide[EB/OL]. (2024-05-13)[2025-07-04]. https://www.intel.com/content/www/us/en/developer/articles/guide/intel-software-guard-extensions-data-center-attestation-primitives-quick-install-guide.html. |
| [15] | CHEN Guoxing, ZHANG Yinqian, LAI T H. Opera: Open Remote Attestation for Intel’s Secure Enclaves[C]// ACM. The 2019 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2019: 2317-2331. |
| [16] | CHEN Guoxing, ZHANG Yinqian. MAGE: Mutual Attestation for a Group of Enclaves without Trusted Third Parties[C]// USENIX. The 31st USENIX Security Symposium. Berkeley: USENIX, 2022: 4095-4110. |
| [17] | DHAR A, PUDDU I, KOSTIAINEN K, et al. ProximiTEE: Hardened SGX Attestation by Proximity Verification[C]// ACM. The 10th ACM Conference on Data and Application Security and Privacy. New York: ACM, 2020: 5-16. |
| [18] |
WANG Juan, HONG Zhi, ZHANG Yuhan, et al. Enabling Security-Enhanced Attestation with Intel SGX for Remote Terminal and IoT[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2017, 37(1): 88-96.
doi: 10.1109/TCAD.2017.2750067 URL |
| [19] | ZHOU Lei, ZHANG Fengwei, WANG Guojun. Using Asynchronous Collaborative Attestation to Build a Trusted Computing Environment for Mobile Applications[C]// IEEE. The 2017 IEEE SmartWorld, Ubiquitous Intelligence & Computing, Advanced & Trusted Computing, Scalable Computing & Communications, Cloud & Big Data Computing, Internet of People and Smart City Innovation (SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI). New York: IEEE, 2017: 1-6. |
| [20] | KUCAB M, BORYLO P, CHOLDA P. Remote Attestation and Integrity Measurements with Intel SGX for Virtual Machines[EB/OL]. (2021-07-01)[2025-07-04]. https://doi.org/10.1016/j.cose.2021.102300. |
| [21] | WALSH K, MANFERDELLI J. Mechanisms for Mutual Attested Microservice Communication[C]// ACM. Proceedings of the 10th International Conference on Utility and Cloud Computing (UCC’17 Companion). New York: ACM, 2017: 59-64. |
| [22] | HAMIDY G M, YULIANTI S, PHILIPPAERTS P, et al. TC4SE: A High-Performance Trusted Channel Mechanism for Secure Enclave-Based Trusted Execution Environments[C]// Springer. Information Security, ISC 2023. Heidelberg: Springer, 2023: 225-244. |
| [23] | KNAUTH T, STEINER M, CHAKRABARTI S, et al. Integrating Remote Attestation with Transport Layer Security[EB/OL]. (2019-07-26)[2025-07-04]. https://doi.org/10.48550/arXiv.1801.05863. |
| [24] | WALTHER R, WEINHOLD C, ROITZSCH M. RATLS: Integrating Transport Layer Security with Remote Attestation[C]// Springer. Applied Cryptography and Network Security Workshops(ACNS 2022). Heidelberg: Springer, 2022: 319-338. |
| [25] | NIEMI A, POP V A B, EKBERG J. Trusted Sockets Layer: A TLS 1.3 Based Trusted Channel Protocol[C]// Springer. Secure IT Systems:26th Nordic Conference(NordSec 2021). Heidelberg: Springer, 2021: 175-191. |
| [26] | KING G, WANG H. HTTPA: HTTPS Attestable Protocol[C]// Springer. The 2023 Future of Information and Communication Conference. Heidelberg: Springer, 2023: 811-823. |
| [27] | KING G, WANG H. HTTPA/2: A Trusted End-to-End Protocol for Web Services[EB/OL]. (2022-09-25)[2025-07-04]. https://doi.org/10.48550/arXiv.2205.01052. |
| [28] | SCHUSTER F, COSTA M, FOURNET C, et al. VC3: Trustworthy Data Analytics in the Cloud Using SGX[C]// IEEE. 2015 IEEE Symposium on Security and Privacy. New York: IEEE, 2015: 38-54. |
| [29] | BHARDWAJ K, SHIH M W, GAVRILOVSKA A, et al. SPX: Preserving End-to-End Security for Edge Computing[EB/OL]. (2018-09-24)[2025-07-04]. https://doi.org/10.48550/arXiv.1809.09038. |
| [30] | CHALKIADAKIS N, DEYANNIS D, KARNIKIS D, et al. The Million Dollar Handshake: Secure and Attested Communications in the Cloud[C]// IEEE. 2020 IEEE 13th International Conference on Cloud Computing. New York: IEEE, 2020: 63-70. |
| [31] | GREVELER U, JUSTUS B, LOHR D. Mutual Remote Attestation: Enabling System Cloning for TPM Based Platforms[C]// Springer. The 7th International Conference on Security and Trust Management. Heidelberg: Springer, 2011: 193-206. |
| [32] | WAGNER P G, BIRNSTILL P, BEYERER J. Establishing Secure Communication Channels Using Remote Attestation with TPM 2.0[C]// Springer. Security and Trust Management. Heidelberg: Springer, 2020: 53-67. |
| [33] | AKRAM R N, MARKANTONAKIS K, MAYES K, et al. An Efficient, Secure and Trusted Channel Protocol for Avionics Wireless Networks[C]// IEEE. IEEE/AIAA 35th Digital Avionics Systems Conference. New York: IEEE, 2016: 1-10. |
| [34] | OTT S, ORTHEN B, WEIDINGER A, et al. MultiTEE: Distributing Trusted Execution Environments[C]// ACM. The 19th ACM Asia Conference on Computer and Communications Security. New York: ACM, 2024: 1617-1629. |
| [35] | SHEPHERD C, AKRAM R N, MARKANTONAKIS K. Establishing Mutually Trusted Channels for Remote Sensing Devices with Trusted Execution Environments[C]// ACM. The 12th International Conference on Availability, Reliability and Security. New York: ACM, 2017: 1-10. |
| [36] | CHEN Jian, DAI Bo, WANG Yanbo, et al. SecTube: SGX-Based Trusted Transmission System[C]// Springer. Smart Computing and Communication. Heidelberg: Springer, 2018: 231-238. |
| [37] | WILL N C, HEINRICH T, VIESCINSKI A B, et al. Trusted Inter-Process Communication Using Hardware Enclaves[C]// IEEE. IEEE International Systems Conference. New York: IEEE, 2021: 1-7. |
| [38] |
JANG J, KANG B B. Securing a Communication Channel for the Trusted Execution Environment[J]. Computers & Security, 2019, 83: 79-92.
doi: 10.1016/j.cose.2019.01.012 URL |
| [39] | JANG J, KONG S, KIM M, et al. SeCReT: Secure Channel between Rich Execution Environment and Trusted Execution Environment[EB/OL]. (2015-02-08)[2025-07-04]. https://www.ndss-symposium.org/wp-content/uploads/2017/09/03_3_2.pdf. |
| [40] | WAGNER P G, BIRNSTILL P, BEYERER J. DDS Security+: Enhancing the Data Distribution Service with TPM-Based Remote Attestation[C]// ACM. The 19th International Conference on Availability, Reliability and Security. New York: ACM, 2024: 1-11. |
| [41] | Confidential 6G Project. Confidential 6G[EB/OL]. (2024-03-15)[2025-07-04]. https://confidential6g.eu/. |
| [42] | DOLEV D, YAO A C. On the Security of Public Key Protocols[EB/OL]. (1981-10-28)[2025-07-04]. https://www.cs.huji.ac.il/-dolev/pubs/dolev-yao-ieee-01056650.pdf. |
| [43] | SHEN Pei, LIU Fulong, SANG Haiwei. Research on Malicious Code Detection[J]. Journal of Chongqing University of Technology (Natural Science Edition), 2022, 36(11): 212-218. |
| 申培, 刘福龙, 桑海伟. 恶意代码检测研究综述[J]. 重庆理工大学学报(自然科学版), 2022, 36(11):212-218. | |
| [44] | KIM Y, SUH H, MUTLU O, et al. Flipping Bits in Memory without Accessing Them: An Experimental Study of DRAM Disturbance Errors[C]// IEEE. 2014 International Symposium on Computer Architecture (ISCA). New York: IEEE, 2014: 361-372. |
| [45] | CASLEY C, TSAFRIR D, GUPTA V, et al. Cuckoo Attacks on Device Authenticated Key Exchange[C]// ACM. ACM Conference on Security and Privacy in Wireless & Mobile Networks (WiSec). New York: ACM, 2013: 1-12. |
| [46] | NIST SP 800-56A Recommendation for Pair-Wise Key Establishment Schemes Using Discrete Logarithm Cryptography[S]. Gaithersburg: National Institute of Standards and Technology, 2013. |
| [47] | ZHAO Shijun, ZHANG Qianying, QIN Yu, et al. SecTEE: A Software Based Approach to Secure Enclave Architecture Using TEE[C]// ACM. The 2019 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2019: 1723-1740. |
| [1] | QIN Zhongyuan, GE Zhenwei, PAN Jingwei, CHEN Liquan. Research on Integrity Measurement Scheme Based on Virtual Trusted Platform Module [J]. Netinfo Security, 2023, 23(2): 11-18. |
| [2] | LIU Qin, GUO Kaiyuan, TU Hang. Task Data Migration Solution Based on SM2 and SM4 Under TEE [J]. Netinfo Security, 2023, 23(1): 9-17. |
| [3] | WANG Chao, HAN Yiliang, DUAN Xiaowei, LI Yu. RLWE-type Authentication Key Exchange Protocol Based on Key Encapsulation Mechanism [J]. Netinfo Security, 2021, 21(6): 80-88. |
| [4] | XIAO Shuai, ZHANG Hanlin, XIAN Hequn, CHEN Fei. A Password Authentication Key Agreement Protocol for IoT Devices [J]. Netinfo Security, 2021, 21(10): 83-89. |
| [5] | CHEN Lu, SUN Yajie, ZHANG Liqiang, CHEN Yun. A Scheme of Measurement for Terminal Equipment Based on DICE in IoT [J]. Netinfo Security, 2020, 20(4): 21-30. |
| [6] | YOU Weijing, LIU Limin, MA Yue, HAN Dong. An Intel SGX-based Proof of Encryption in Clouds [J]. Netinfo Security, 2020, 20(12): 1-8. |
| [7] | DUAN Xiaowei, HAN Yiliang, WANG Chao, LI Zhe. Analysis and Improvement of Public Key Reuse for A RLWE Key Exchange Protocol [J]. Netinfo Security, 2020, 20(11): 87-94. |
| [8] | LI Yu, HAN Yiliang, LI Zhe, ZHU Shuaishuai. A Post Quantum Authenticated Key Exchange Protocol Based on LWE [J]. Netinfo Security, 2020, 20(10): 92-99. |
| [9] | Zhe LI, Yiliang HAN, Yu LI. A Key Exchange Cryptosystem Based on Polar Codes [J]. Netinfo Security, 2019, 19(10): 84-90. |
| [10] | Bo FAN, Runkai YANG, Lin LI. Research on Establish SSH-based Trusted Channels [J]. Netinfo Security, 2018, 18(1): 45-51. |
| [11] | Juanjuan CHENG, Fangyu ZHENG, Jingqiang LIN, Jiankuo DONG. High-performance Implementation of Curve25519 on GPU [J]. Netinfo Security, 2017, 17(9): 122-127. |
| [12] | Weiqing YOU, Xiaoming CHEN, Jian QI. Research on a Kind of Anti-quantum Computing Public Key Cryptosystem [J]. Netinfo Security, 2017, 17(4): 53-60. |
| [13] | Siqi LU, Shuhui FAN, Xu HAN, Qingfeng CHENG. A Leakage Resilient Authenticated Key Exchange Protocol Based on the CAFL Model [J]. Netinfo Security, 2016, 16(4): 31-37. |
| [14] | Guannan FAN, Pan DONG. Research on Trusted Execution Environment Building Technology Based on TrustZone [J]. Netinfo Security, 2016, 16(3): 21-27. |
| [15] | YANG Yong-jiao, YAN Fei, YU Zhao, ZHANG Huan-guo. Research on VT-d based Virtual Machine Isolation Framework [J]. Netinfo Security, 2015, 15(11): 7-8. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||