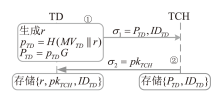
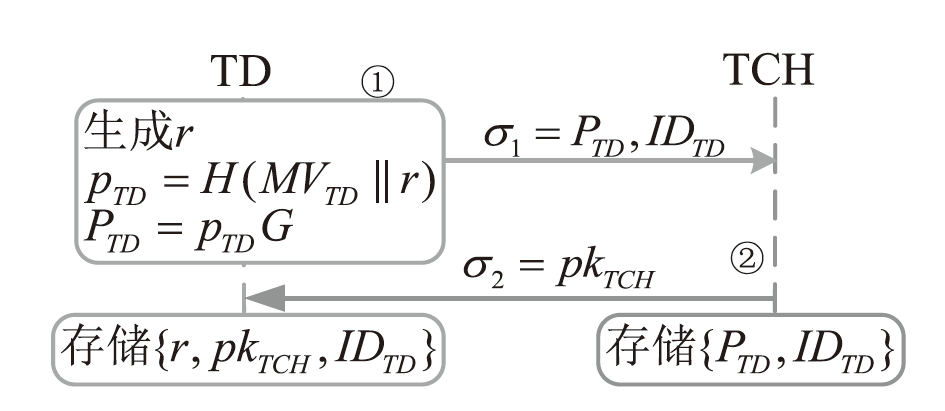
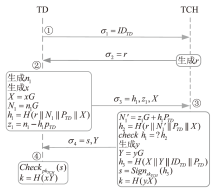
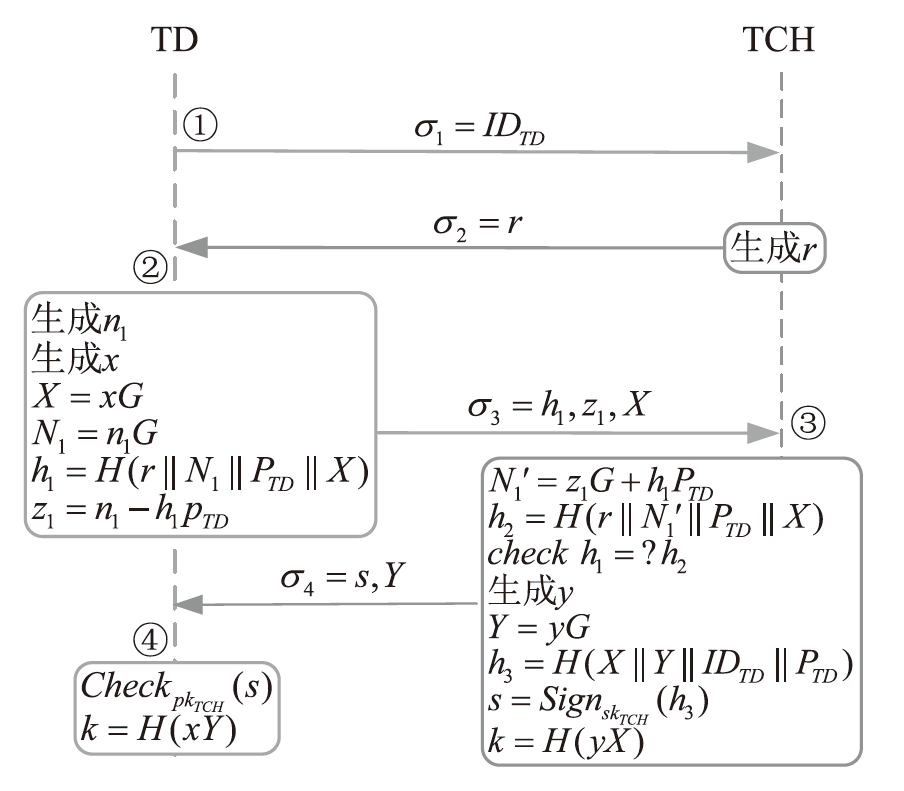
Netinfo Security ›› 2025, Vol. 25 ›› Issue (11): 1774-1791.doi: 10.3969/j.issn.1671-1122.2025.11.010
Previous Articles Next Articles
Cloud-Native TEE Service Sharing Mechanism for Secure Edge Computing
LU Di1, LIU Yujia1( ), LYU Chaoyue2, SUN Mengna1, ZHANG Qingwen1, YANG Li1
), LYU Chaoyue2, SUN Mengna1, ZHANG Qingwen1, YANG Li1
1. School of Computer Science and Technology ,Xidian University Xi’an 710126, China 2. VeriSilicon (Chengdu) Co. ,Ltd. Chengdu 610041, China
-
Received:2025-06-20Online:2025-11-10Published:2025-12-02
CLC Number:
Cite this article
LU Di, LIU Yujia, LYU Chaoyue, SUN Mengna, ZHANG Qingwen, YANG Li. Cloud-Native TEE Service Sharing Mechanism for Secure Edge Computing[J]. Netinfo Security, 2025, 25(11): 1774-1791.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.11.010
| 共享 方式 | 技术特点 | 技术不足 | 基于虚拟机级TEE相较不同共享方式的优势 |
|---|---|---|---|
| TEE与LibOS结合的远程计算保护 | 通过LibOS提供轻量级系统抽象,实现敏感任务在TEE环境中的无缝执行;支持敏感任务远程交付,通常无需大量修改即可运行;利用硬件TEE实现强隔离和远程 认证 | 系统兼容性有限;资源隔离与多租户支持弱;性能开销较高;云原生集成能力不足 | 更强的环境兼容性与灵活性:提供独立的操作系统环境,支持多类型任务和复杂应用的执行,更接近传统虚拟化平台。 优越的隔离性与多租户支持:具备硬件级内存加密和强隔离边界,天然支持多租户场景下的安全隔离。 更优的性能与可扩展性:避免了LibOS的系统调用拦截开销,结合云平台资源,能提供低延迟、高吞吐的服务 更好的云原生集成:更易于与云原生基础设施集成,支持动态调度和弹性伸缩,适合大规模服务 共享 |
| 基于TPM的远程设备完整性保护 | 依托专用硬件芯片(TPM)提供可信根与安全操作集合(如加解密、签名);通过物理隔离和硬件保护机制,可有效抵御恶意篡改和侧信道攻击;专注于系统启动时的静态可信度量与关键数据完整性保护 | 计算与存储资源受限;功能相对固化导致运行时保护能力不足,主要为辅助安全组件;通用性与可扩展性差;对新型攻击适应 性弱 | 更强大的计算能力与资源弹性:利用云平台的计算与存储资源,可轻松应对高并发和弹性扩展需求。 全面的运行时保护:在虚拟化层面实现工作负载的全程隔离与动态可信验证,契合云应用生命周期管理 更高的通用性与灵活性:作为通用计算架构,不依赖特定硬件,易于在异构云环境中部署和迁移。 更深的防御纵深:可通过嵌套虚拟化与硬件辅助安全扩展,提供更强健、灵活的可信基础 |
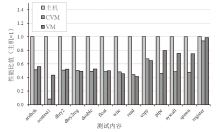
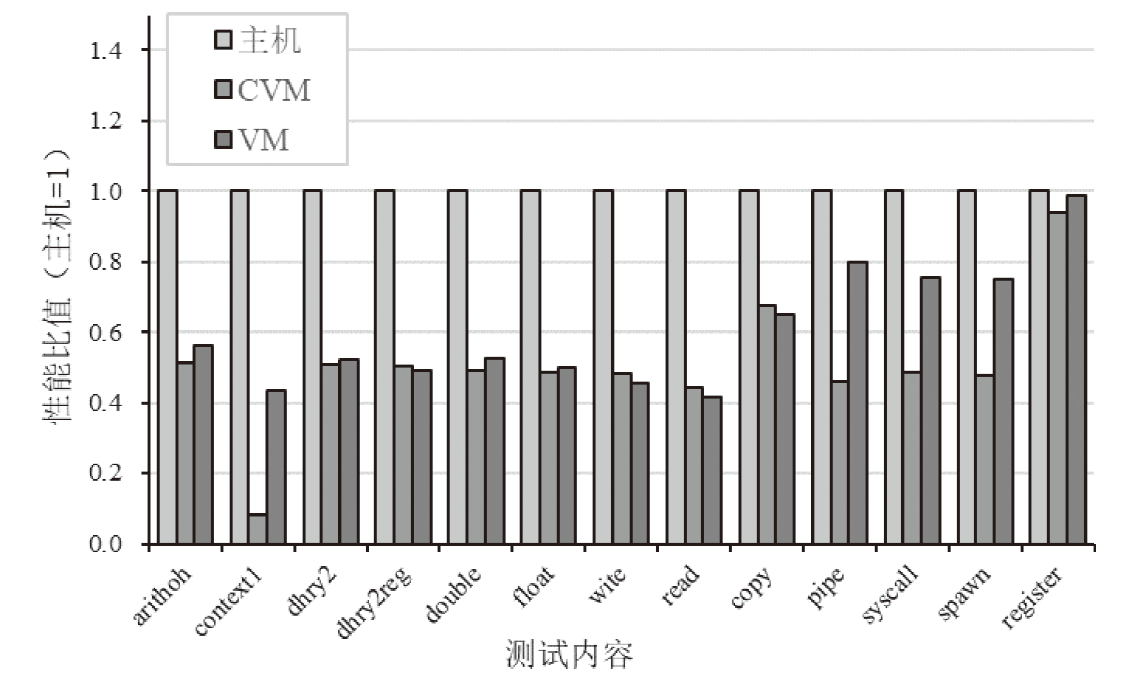
| 测试项目名称 | 含义 |
|---|---|
| arithoh | 简单整数运算的性能,即一秒内计算次数 |
| context1 | 上下文切换的性能,即一秒内上下文切换次数 |
| dhry2 | 整数运算基准测试(不使用显式的寄存器变量) |
| dhry2reg | 整数运算基准测试(使用显式的寄存器变量) |
| double | 双精度浮点数运算性能,即一秒内计算次数 |
| float | 单精度浮点数运算性能,即一秒内计算次数 |
| write | 文件系统写操作性能,即两秒内写入字节数 |
| read | 文件系统读操作性能,即两秒内读出字节数 |
| copy | 文件系统复制操作性能,即两秒内复制字节数 |
| pipe | 管道通信性能,即一秒内管道读写完成次数 |
| syscall | 系统调用性能,即一秒内进行系统调用的次数 |
| spawn | 创建进程性能,即一秒内创建进程的数量 |
| register | 寄存器操作性能,即一秒内进行寄存器操作的次数 |
| [1] | Gramine Contributors. Gramine Documentation[EB/OL]. [2025-06-05]. https://gramine.readthedocs.io/en/latest/. |
| [2] | ARNAUTOV S, TRACH B, GREGOR F, et al. SCONE: Secure Linux Containers with Intel {SGX}[C]// USENIX. The 12th USENIX Symposium on Operating Systems Design and Implementation (OSDI 16). Berkeley: USENIX, 2016: 689-703. |
| [3] | BAUMANN A, PEINADO M, HUNT G. Shielding Applications from an Untrusted Cloud with Haven[J]. ACM Transactions on Computer Systems (TOCS), 2015, 33(3): 1-26. |
| [4] | BRESCIA L, ALDINUCCI M. Secure Generic Remote Workflow Execution with TEEs[C]// IEEE. The 2nd Workshop on Workflows in Distributed Environments. New York: IEEE, 2024: 8-13. |
| [5] | WIDANAGE C, LIU Weijie, LI Jiayu, et al. HySec-Flow: Privacy-Preserving Genomic Computing with SGX-Based Big-Data Analytics Framework[C]// IEEE.2021 IEEE 14th International Conference on Cloud Computing (CLOUD). New York: IEEE, 2021: 733-743. |
| [6] | Advanced Micro Devices. Secure Encrypted Virtualization API Version 0.24[EB/OL]. [2025-06-05]. https://www.amd.com/content/dam/amd/en/documents/epyc-technical-docs/programmer-references/55766_SEV-KM_API_Specification.pdf. |
| [7] | Intel Corporation. Intel® Trust Domain Extensions[EB/OL]. [2025-06-05]. https://www.intel.com/content/www/us/en/developer/tools/trust-domain-extensions/documentation.html. |
| [8] | ARM. ARM CCA Security Model 1.0[EB/OL]. [2025-06-05]. https://developer.arm.com/documentation/DEN0096/latest/. |
| [9] | RUSSINOVICH M. Azure Confidential Computing[EB/OL]. [2025-06-05]. https://azure.microsoft.com/en-us/blog/azure-confidential-computing/. |
| [10] |
MOFRAD S, AHMED I, ZHANG Fengwei, et al. Securing Big Data Scientific Workflows via Trusted Heterogeneous Environments[J]. IEEE Transactions on Dependable and Secure Computing, 2021, 19(6): 4187-4203.
doi: 10.1109/TDSC.2021.3123640 URL |
| [11] | ARTHUR W, CHALLENER D, GOLDMAN K. A Practical Guide to TPM 2.0: Using the New Trusted Platform Module in the New Age of Security[M]. Heidelburg: Springer Nature, 2015. |
| [12] | DEWAN P, DURHAM D, KHOSRAVI H, et al. A Hypervisor-Based System for Protecting Software Runtime Memory and Persistent Storage[J]. SpringSim, 2008, 8: 828-835. |
| [13] | LIN K, WANG C. Using TPM to Improve Boot Security at BIOS Layer[C]// IEEE.2012 IEEE International Conference on Consumer Electronics (ICCE). New York: IEEE, 2012: 376-377. |
| [14] | ZHAO Lianying, MANNAN M. TEE-Aided Write Protection against Privileged Data Tampering[EB/OL]. (2019-05-26)[2025-06-05]. https://arxiv.org/abs/1905.10723. |
| [15] |
LU Di, HAN Ruidong, SHEN Yulong, et al. xTSeH: A Trusted Platform Module Sharing Scheme towards Smart IoT-Ehealth Devices[J]. IEEE Journal on Selected Areas in Communications, 2020, 39(2): 370-383.
doi: 10.1109/JSAC.49 URL |
| [16] | COSTAN V, DEVADAS S. Intel SGX Explained[EB/OL]. (2016-08-01)[2025-06-05]. https://eprint.iacr.org/2016/086. |
| [17] | ARM. TrustZone for ARMv8-A[EB/OL]. (2016-08-01)[2025-06-05]. https://developer.arm.com/-/media/Arm%20Developer%20Community/PDF/Learn%20the%20Architecture/TrustZone%20for%20Armv8-A.pdf?revision=c3134c8e-f1d0-42ff-869e-0e6a6bab824f |
| [18] | ZOU Deqing, QIANG Weizhong, JIN Hai. Trusted Computing Technology Principle and Application[M]. Beijing: Science Press, 2011. |
| 邹德清, 羌卫中, 金海. 可信计算技术原理与应用[M]. 北京: 科学出版社, 2011. | |
| [19] | HU Jun, SHEN Changxiang, GONG Bei. Preliminary Study on Trusted Computing 3.0 Engineering[M]. Beijing: Posts & Telecom Press, 2018. |
| 胡俊, 沈昌祥, 公备. 可信计算3.0工程初步[M]. 北京: 人民邮电出版社, 2018. | |
| [20] | BRASSER F, EL MAHJOUB B, SADEGHI A R, et al. TyTAN: Tiny Trust Anchor for Tiny Devices[C]// ACM. The 52nd Annual Design Automation Conference. New York: ACM, 2015: 1-6. |
| [21] |
DOLEV D, YAO A. On the Security of Public Key Protocols[J]. IEEE Transactions on Information Theory, 1983, 29(2): 198-208.
doi: 10.1109/TIT.1983.1056650 URL |
| [1] | SHI Yijuan, ZHOU Danping, FAN Lei, LIU Yin. Secure Multi-Party Computation Protocol Based on Trusted Execution Environment [J]. Netinfo Security, 2025, 25(9): 1439-1446. |
| [2] | GENG Zhiyuan, XU Zexuan, ZHANG Hengwei. A Decision-Making Method for Cloud-Native Moving Target Defense Based on Stochastic Games and DQN Algorithm [J]. Netinfo Security, 2025, 25(6): 967-976. |
| [3] | ZHU Hui, FANG Yunyi, WANG Fengwei, XU Wei. Research Progress on Data Security Processing Integrating Confidential Computing [J]. Netinfo Security, 2025, 25(11): 1643-1657. |
| [4] | HAO Meng, LI Jiayong, YANG Hongwei, ZHANG Weizhe. Heterogeneous CPU-GPU System Confidential Computing Survey [J]. Netinfo Security, 2025, 25(11): 1658-1672. |
| [5] | GUAN Zhi, HU Jianbin, LI Yue, CHEN Zhong. A Comprehensive Survey of Blockchain Technologies and Applications Based on Trusted Execution Environments [J]. Netinfo Security, 2025, 25(11): 1673-1690. |
| [6] | REN Fengyuan, ZHANG Xinyue, LEI Zhuoyi, LIU Xin. Research on Key-Value Data Storage and Operation Optimization Method Based on Confidential Computing [J]. Netinfo Security, 2025, 25(11): 1707-1717. |
| [7] | XUE Kaiping, ZHANG Chunyi, LIU Feng, WANG Feng. Security-Enhanced Index Scheme in Encrypted Database Based on Trusted Execution Environment [J]. Netinfo Security, 2025, 25(11): 1718-1731. |
| [8] | ZHAO Bo, LYU Jiamin, WANG Yixuan. A Multidimensional Security Measurement Architecture for the Container Lifecycle [J]. Netinfo Security, 2025, 25(11): 1745-1761. |
| [9] | WANG Yajie, LU Jinbiao, LI Yuhang, FAN Qing, ZHANG Zijian, ZHU Liehuang. Hierarchical Dynamic Protection Algorithm for Federated Learning Based on Trusted Execution Environment [J]. Netinfo Security, 2025, 25(11): 1762-1773. |
| [10] | HU Yuyi, CAI Wei, CHEN Jingfan, LIU Mohan, WANG Juan, HE Yun. Research on Unified Remote Attestation Mechanism for Confidential Containers Devices [J]. Netinfo Security, 2025, 25(11): 1811-1823. |
| [11] | YU Fajiang, WANG Chaozhou. Implementation Mechanism for TrustZone Paravirtualization and Containerization [J]. Netinfo Security, 2025, 25(10): 1523-1536. |
| [12] | ZHOU Shucheng, LI Yang, LI Chuanrong, GUO Lulu, JIA Xinhong, YANG Xinghua. Context-Based Abnormal Root Cause Algorithm [J]. Netinfo Security, 2024, 24(7): 1062-1075. |
| [13] | SUN Yu, XIONG Gaojian, LIU Xiao, LI Yan. A Survey on Trusted Execution Environment Based Secure Inference [J]. Netinfo Security, 2024, 24(12): 1799-1818. |
| [14] | TANG Yu, ZHANG Chi. A Privacy Protection Scheme for Information-Centric Networking Based on Intel SGX [J]. Netinfo Security, 2023, 23(6): 55-65. |
| [15] | LIU Xin, LI Yunyi, WANG Miao. A Lightweight Authentication Protocol Based on Confidential Computing for Federated Learning Nodes [J]. Netinfo Security, 2022, 22(7): 37-45. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||