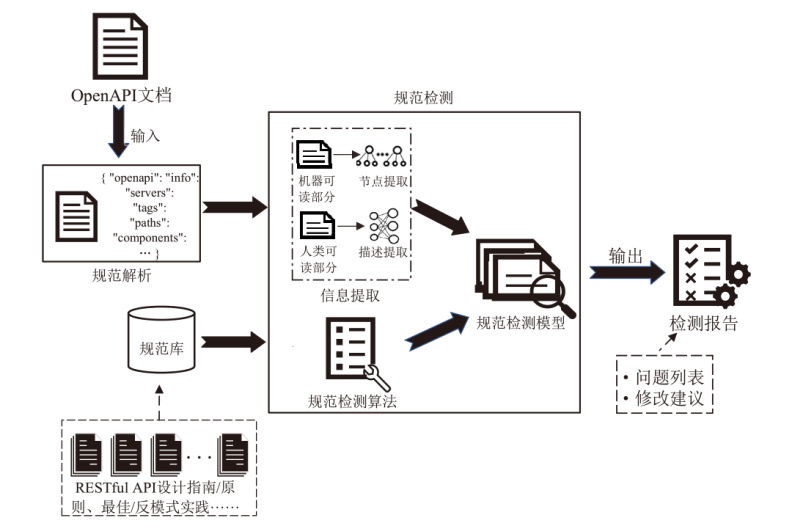
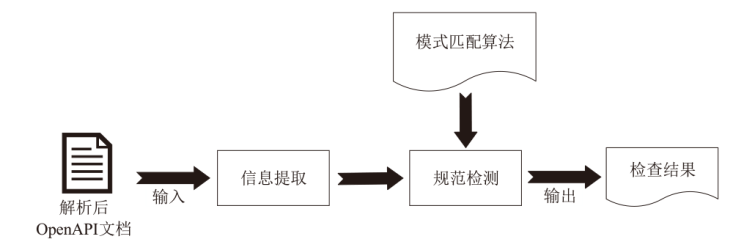
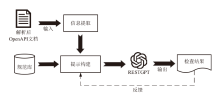
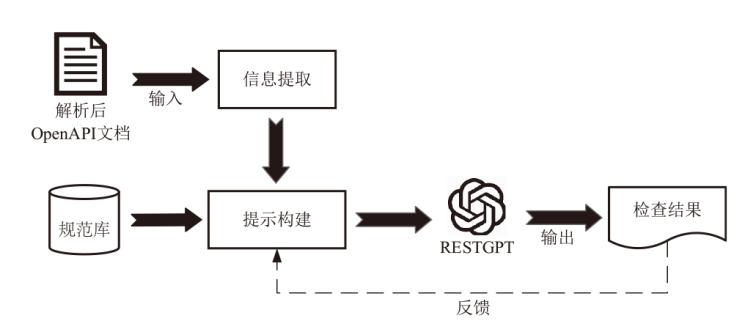
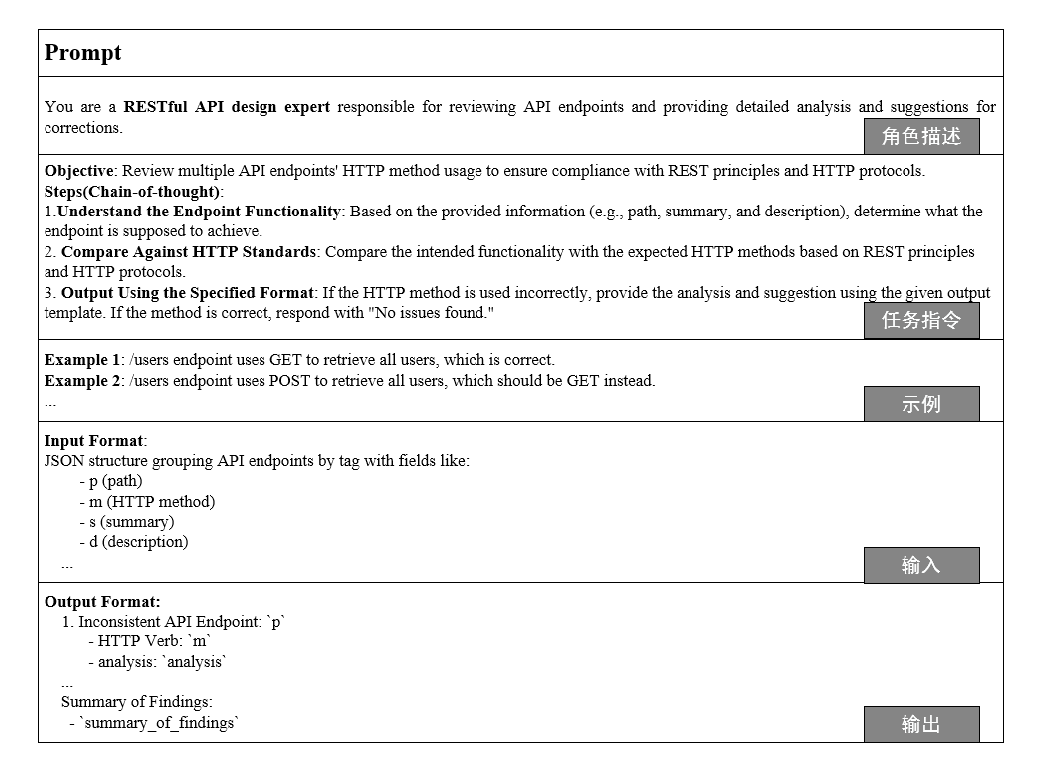
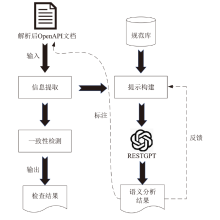
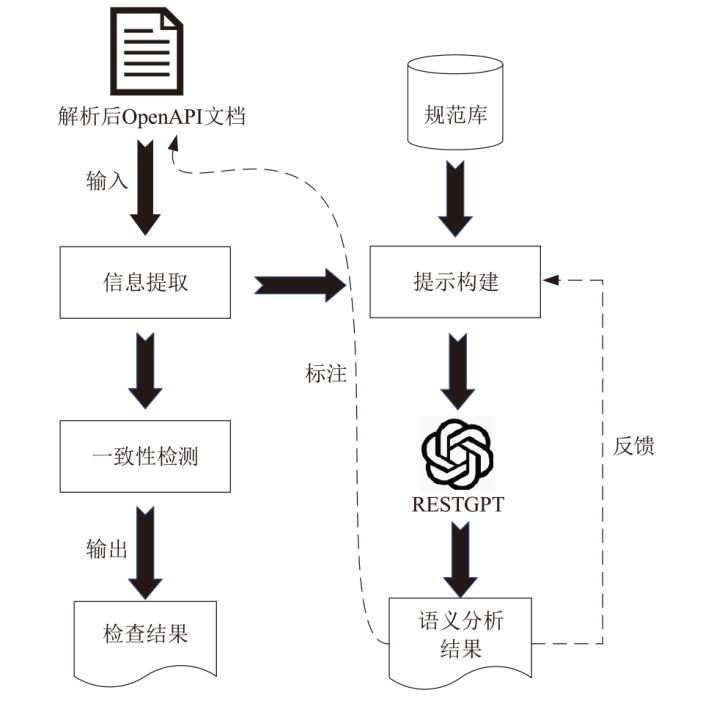
Netinfo Security ›› 2025, Vol. 25 ›› Issue (8): 1313-1325.doi: 10.3969/j.issn.1671-1122.2025.08.011
Previous Articles Next Articles
Research on REST API Design Security Testing
ZHANG Yanyi1,2,3, RUAN Shuhua1,2,3( ), ZHENG Tao1,2,3
), ZHENG Tao1,2,3
- 1. School of Cyber Science and Engineering, Sichuan University, Chengdu 610065, China
2. Key Laboratory of Data Protection and Intelligent Management (Sichuan University), Ministry of Education, Chengdu 610065, China
3. Cyber Science Research Institute, Sichuan University, Chengdu 610065, China
-
Received:2024-10-25Online:2025-08-10Published:2025-09-09
CLC Number:
Cite this article
ZHANG Yanyi, RUAN Shuhua, ZHENG Tao. Research on REST API Design Security Testing[J]. Netinfo Security, 2025, 25(8): 1313-1325.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.08.011
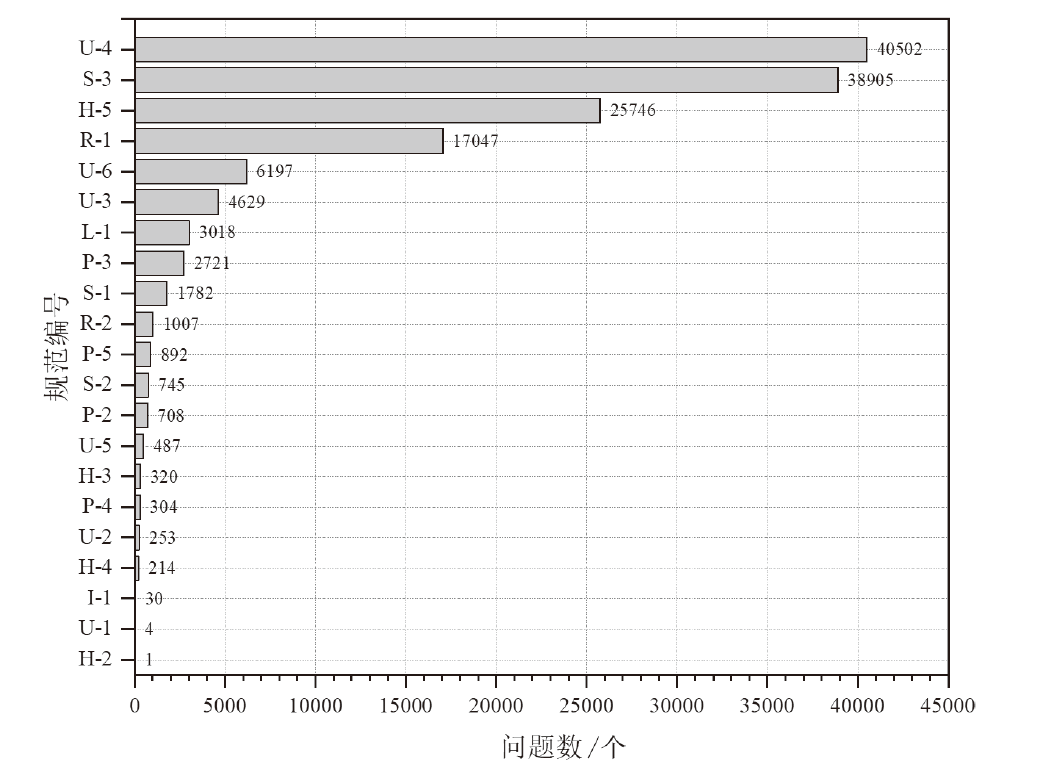
| 编号 | 规范描述 | 类别 |
|---|---|---|
| U-1 | URI中必须使用分隔符/表示层次关系[ | URI 安全 |
| U-2 | URI中不能包含尾随的斜杠(/)[ | |
| U-3 | URI中应该使用“-”而不是“_”作为连接符[ | |
| U-4 | URI路径应该使用小写字母[ | |
| U-5 | URI中不能包含文件扩展名[ | |
| U-6 | URI中不能出现CRUD方法名[ | |
| P-1 | 查询参数中避免出现版本号[ | 参数 安全 |
| P-2 | 查询参数中避免出现CRUD方法名[ | |
| P-3 | 同一参数的类型定义不能发生冲突[ | |
| P-4 | 敏感参数不能在URL上传播[ | |
| P-5 | 参数默认值应该安全配置[ | |
| H-1 | 对资源的操作必须遵循HTTP协议定义的标准方法[ | HTTP交互 安全 |
| H-2 | 自定义HTTP头不能用来改变HTTP方法的行为[ | |
| H-3 | GET和POST方法不能用于隧道其他请求方法[ | |
| H-4 | 响应必须遵循HTTP协议定义的标准响应码及 状态描述[ | |
| H-5 | 401 (“Unauthorized”)响应在需要验证身份认证时必须 使用[ | |
| R-1 | 请求/响应消息头中必须包含“Content-Type”[ | HTTP消息 安全 |
| R-2 | 请求/响应消息表示应该支持JSON格式[ | |
| S-1 | API应该正确配置身份认证/授权机制[ | 安全 方案 |
| S-2 | API应该正确配置安全传输协议[ | |
| S-3 | API应该正确配置HTTP安全头[ | |
| L-1 | 自链接应该使用一致且正确的表单来表示 | 自链接 安全 |
| I-1 | 同一服务的API应该使用一致的子域名[ | 服务 管理 安全 |
| I-2 | API信息中应该具有版本声明[ |
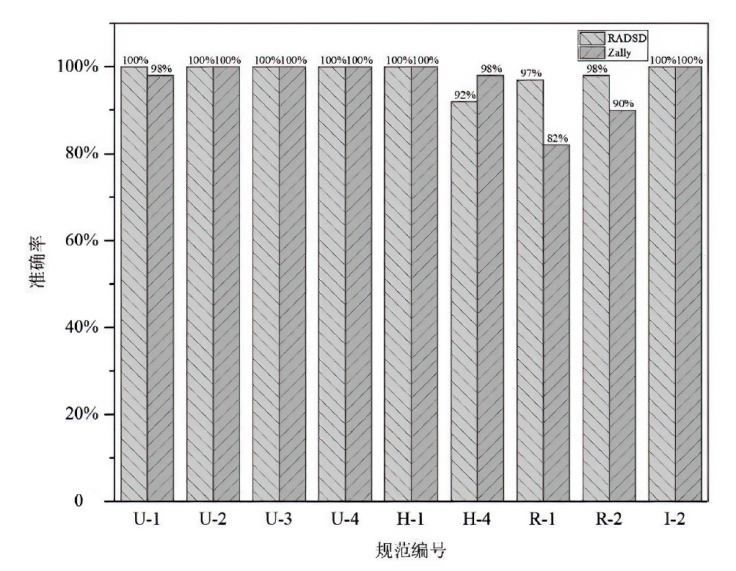
| 规范编号 | 准确率 | 召回率 | 规范 编号 | 准确率 | 召回率 | 规范 编号 | 准确率 | 召回率 | 规范 编号 | 准确率 | 召回率 |
|---|---|---|---|---|---|---|---|---|---|---|---|
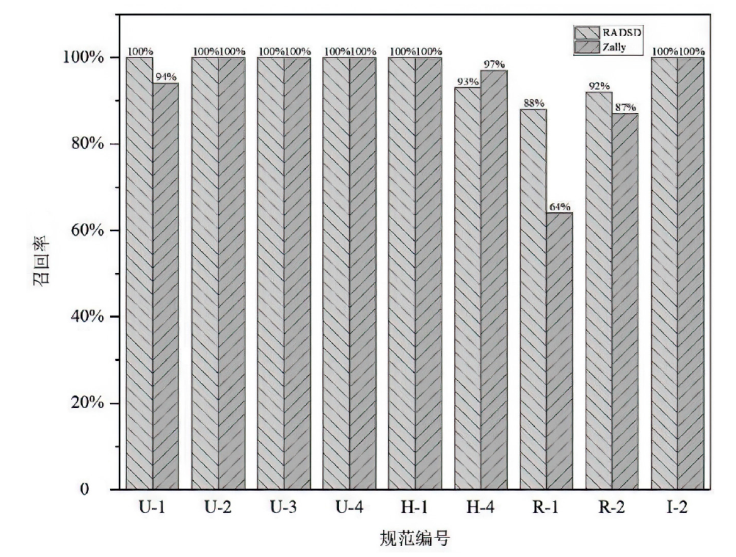
| U-1 | 100% | 100% | P-1 | 100% | 100% | H-2 | 100% | 100% | S-1 | 100% | 100% |
| U-2 | 100% | 100% | P-2 | 95% | 96% | H-3 | 86% | 84% | S-2 | 93% | 92% |
| U-3 | 100% | 100% | P-3 | 94% | 82% | H-4 | 92% | 93% | S-3 | 100% | 100% |
| U-4 | 100% | 100% | P-4 | 97% | 98% | H-5 | 95% | 98% | L-1 | 96% | 97% |
| U-5 | 97% | 98% | P-5 | 96% | 96% | R-1 | 97% | 88% | I-1 | 100% | 100% |
| U-6 | 94% | 97% | H-1 | 100% | 100% | R-2 | 98% | 92% | I-2 | 100% | 100% |
| [1] | FIELDING R T. Architectural Styles and the Design of Network-Based Software Architectures[M]. Irvine: University of California, 2000. |
| [2] | HIGGINBOTHAM J. Principles of Web API Design: Delivering Value with APIs and Microservices[M]. Boston: Addison-Wesley Professional, 2021. |
| [3] | ZHOU Xinyu, CHEN Wei, WU Guoquan, et al. REST API Design Analysis and Empirical Study[J]. Journal of Software, 2022, 33(9): 3271-3296. |
| 周芯宇, 陈伟, 吴国全, 等. REST API 设计分析及实证研究[J]. 软件学报, 2022, 33(9): 3271-3296. | |
| [4] | RAUTENSTRAUCH J, STOCK B. Who's Breaking the Rules? Studying Conformance to the HTTP Specifications and its Security Impact[C]// ASIA-CCS. Proceedings of the 19th ACM Asia Conference on Computer and Communications Security. New York: ACM, 2024: 843-855. |
| [5] | BOGNER J, KOTSTEIN S, PFAFF T. Do RESTful API Design Rules Have an Impact on the Understandability of Web APIs?[J]. Empirical Software Engineering, 2023, 28(6): 132-167. |
| [6] | OpenAPI Initiative. OpenAPI Specification[EB/OL]. (2021-02-15)[2024-10-14]. https://www.openapis.org. |
| [7] | GORSKI P L, MÖLLER S, WIEFLING S, et al. “I Just Looked for the Solution!” On Integrating Security-Relevant Information in Non-Security API Documentation to Support Secure Coding Practices[J]. IEEE Transactions on Software Engineering, 2021, 48(9): 3467-3484. |
| [8] | EHSAN A, ABUHALIQA M A M E, CATAL C, et al. RESTful API Testing Methodologies: Rationale, Challenges, and Solution Directions[J]. Applied Sciences, 2022, 12(9): 4369-4385. |
| [9] | GOLMOHAMMADI A, ZHANG Man, ARCURI A. Testing Restful APIs: A Survey[J]. ACM Transactions on Software Engineering and Methodology, 2023, 33(1): 1-41. |
| [10] | PATNAIK N, DWYER A, HALLETT J, et al. SLR: From Saltzer and Schroeder to 2021… 47 Years of Research on the Development and Validation of Security API Recommendations[J]. ACM Transactions on Software Engineering and Methodology, 2023, 32(3): 1-31. |
| [11] | ZHANG Man, ARCURI A. Open Problems in Fuzzing Restful APIs: A Comparison of Tools[J]. ACM Transactions on Software Engineering and Methodology, 2023, 32(6): 1-45. |
| [12] | ALONSO J C, MARTIN-LOPEZ A, SEGURA S, et al. ARTE: Automated Generation of Realistic Test Inputs for Web APIs[J]. IEEE Transactions on Software Engineering, 2022, 49(1): 348-363. |
| [13] | SWAGGER. API Development for Everyone[EB/OL]. [2024-10-14]. http://swagger.io/. |
| [14] | MANNING C D. Human Language Understanding & Reasoning[J]. Daedalus, 2022, 151(2): 127-138. |
| [15] | ZHAO Wayne Xin, ZHOU Kun, LI Junyi, et al. A Survey of Large Language Models[EB/OL]. (2023-12-24) [2024-10-14]. https://arxiv.org/abs/2303.18223. |
| [16] | LIU Yiheng, HAN Tianle, MA Siyuan, et al. Summary of Chatgpt-Related Research and Perspective towards the Future of Large Language Models[EB/OL]. (2023-08-18)[2024-10-14]. https://doi.org/10.1016/j.metrad.2023.100017. |
| [17] | OpenAI. ChatGPT[EB/OL]. [2024-10-14]. https://openai.com. |
| [18] | WEI J, WANG Xuezhi, SCHUURMANS D, et al. Chain-of-Thought Prompting Elicits Reasoning in Large Language Models[J]. Advances in Neural Information Processing Systems, 2022, 35: 24824-24837. |
| [19] | BROWN T, MANN B, RYDER N, et al. Language Models Are Few-Shot Learners[J]. Advances in Neural Information Processing Systems, 2020, 33: 1877-1901. |
| [20] | OWASP. OWASP Cheat Sheet Series[EB/OL]. [2024-10-14]. https://cheatsheetseries.owasp.org. |
| [21] | KOTSTEIN S, BOGNER J. Which Restful API Design Rules are Important and How Do they Improve Software Quality? A Delphi Study with Industry Experts[C]// Springer. Service-Oriented Computing:15th Symposium and Summer School. Heidelberg: Springer, 2021: 154-173. |
| [22] | MASSE M. REST API Design Rulebook[M]. Sebastopol: O'Reilly Media, Inc., 2011. |
| [23] | PALMA F, GONZALEZ-HUERTA J, MOHA N, et al. Are Restful APIs Well-Designed? Detection of Their Linguistic (Anti) Patterns[C]// Springer. Service-Oriented Computing:13th International Conference. Heidelberg: Springer, 2015: 171-187. |
| [24] | PETRILLO F, MERLE P, MOHA N, et al. Are REST APIs for Cloud Computing Well-Designed? An Exploratory Study[C]// Springer. Service-Oriented Computing:14th International Conference. Heidelberg: Springer, 2016: 157-170. |
| [25] | PALMA F, OLSSON T, WINGKVIST A, et al. Assessing the Linguistic Quality of REST APIs for IoT Applications[J]. Journal of Systems and Software, 2022, 191: 111369. |
| [26] | SUBRAMANIAN H, RAJ P. Hands-On RESTful API Design Patterns and Best Practices: Design, Develop, and Deploy Highly Adaptable, Scalable, and Secure RESTful Web APIs[M]. Birmingham: Packt Publishing Ltd., 2019. |
| [27] | GREEN M, SMITH M. Developers are not the Enemy: The Need for Usable Security APIs[J]. IEEE Security & Privacy, 2016, 14(5): 40-46. |
| [28] | BRABRA H, MTIBAA A, PETRILLO F, et al. On Semantic Detection of Cloud API (Anti) Patterns[J]. Information and Software Technology, 2019, 107: 65-82. |
| [29] | NSFocus. REST API Security Design Guide[EB/OL]. (2020-06-22)[2024-10-14]. https://www.infoq.cn/article/eyj8icgmp3j3pm9uf4y4. |
| 绿盟科技. REST API安全设计指南[EB/OL]. (2020-06-22)[2024-10-14]. https://www.infoq.cn/article/eyj8icgmp3j3pm9uf4y4. | |
| [30] | OpenAI. OpenAPI Spec Validator[EB/OL]. (2023-10-13)[2024-10-14]. https://github.com/python-openapi/openapi-spec-validator/. |
| [31] | OpenAI. Completion-OpenAI API[EB/OL]. (2023-08-12)[2024-10-14]. https://beta.openai.com/docs/guides/completion/prompt-design. |
| [32] | KARAVISILEIOU A, MAINAS N, BOURAIMIS F, et al. Automated Ontology Instantiation of OpenAPI REST Service Descriptions[C]// SAI Conferences. Advances in Information and Communication:Proceedings of the 2021 Future of Information and Communication Conference (FICC). Heidelberg: Springer, 2021: 945-962. |
| [33] | GONCHAROV I. APIs.guru[EB/OL]. (2016-05-28)[2024-10-14]. https://apis.guru/. |
| [34] | FIELDING R, GETTYS J, MOGUL J, et al. Hypertext Transfer Protocol--HTTP/1.1[R]. Fremont: Internet Engineering Task Force (IETF), RFC 2616, 1999. |
| [1] | CHEN Ping, LUO Mingyu. Research on Large Model Analysis Methods for Kernel Race Vulnerabilities in Cloud-Edge-Device Scenarios [J]. Netinfo Security, 2025, 25(7): 1007-1020. |
| [2] | FENG Wei, XIAO Wenming, TIAN Zheng, LIANG Zhongjun, JIANG Bin. Research on Semantic Intelligent Recognition Algorithms for Meteorological Data Based on Large Language Models [J]. Netinfo Security, 2025, 25(7): 1163-1171. |
| [3] | ZHANG Xuewang, LU Hui, XIE Haofei. A Data Augmentation Method Based on Graph Node Centrality and Large Model for Vulnerability Detection [J]. Netinfo Security, 2025, 25(4): 550-563. |
| [4] | XIE Mengfei, FU Jianming, YAO Renyi. Research on LLM-Based Fuzzing of Native Multimedia Libraries [J]. Netinfo Security, 2025, 25(3): 403-414. |
| [5] | QIN Zhongyuan, WANG Tiantian, LIU Weiqiang, ZHANG Qunfang. Advances in Watermarking Techniques for Large Language Models [J]. Netinfo Security, 2025, 25(2): 177-193. |
| [6] | CHEN Haoran, LIU Yu, CHEN Ping. Endogenous Security Heterogeneous Entity Generation Method Based on Large Language Model [J]. Netinfo Security, 2024, 24(8): 1231-1240. |
| [7] | XIANG Hui, XUE Yunhao, HAO Lingxin. Large Language Model-Generated Text Detection Based on Linguistic Feature Ensemble Learning [J]. Netinfo Security, 2024, 24(7): 1098-1109. |
| [8] | GUO Xiangxin, LIN Jingqiang, JIA Shijie, LI Guangzheng. Security Analysis of Cryptographic Application Code Generated by Large Language Model [J]. Netinfo Security, 2024, 24(6): 917-925. |
| [9] | QIN Zhenkai, XU Mingchao, JIANG Ping. Research on the Construction Method and Application of Case Knowledge Graph Based on Prompt Learning [J]. Netinfo Security, 2024, 24(11): 1773-1782. |
| [10] | LI Jiao, ZHANG Yuqing, WU Yabiao. Data Augmentation Method via Large Language Model for Relation Extraction in Cybersecurity [J]. Netinfo Security, 2024, 24(10): 1477-1483. |
| [11] | HUANG Kaijie, WANG Jian, CHEN Jiongyi. A Large Language Model Based SQL Injection Attack Detection Method [J]. Netinfo Security, 2023, 23(11): 84-93. |
| [12] | Chaoling LIU, Yan ZHANG, Huiran YANG, Hongjing WU. Design and Implementation of a DPDK-based Virtual NIPS [J]. Netinfo Security, 2018, 18(5): 41-51. |
| [13] | Gang ZHAO, Xingren YAO. Anomaly Detection Model Based on User Portrait [J]. Netinfo Security, 2017, 17(7): 18-24. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||