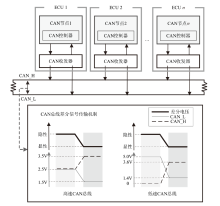
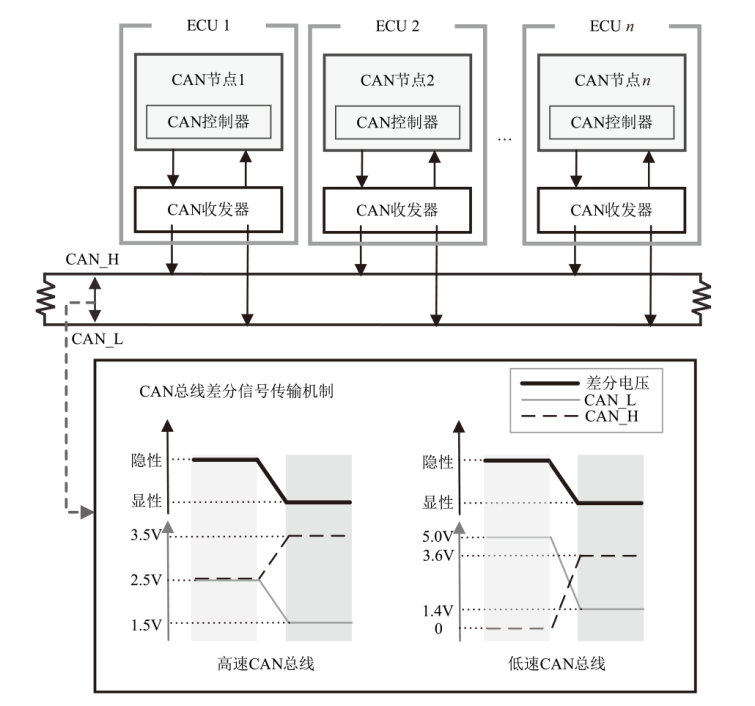
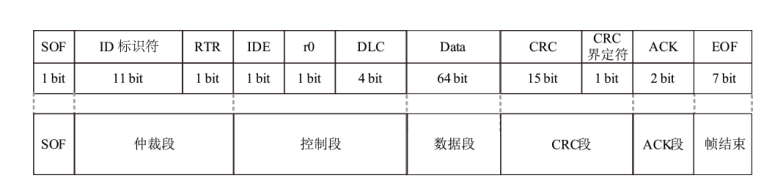
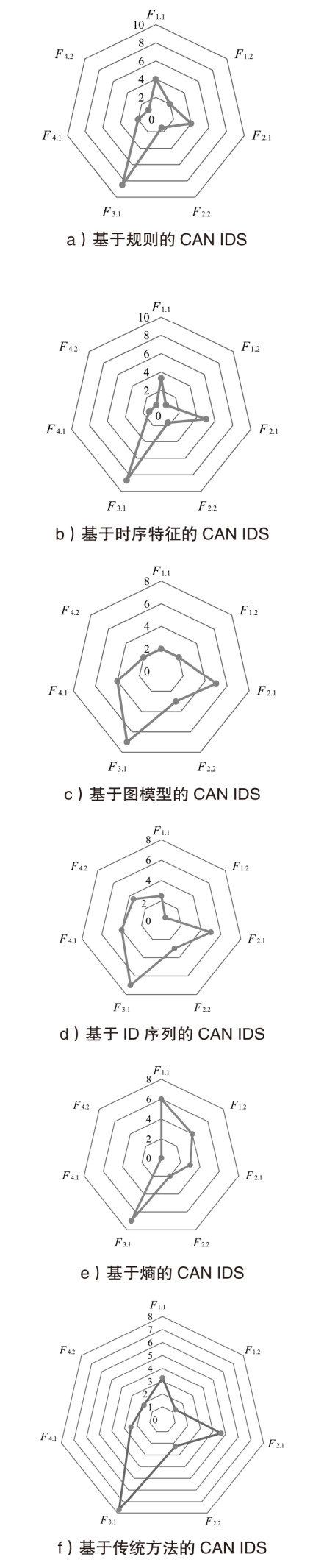
Netinfo Security ›› 2025, Vol. 25 ›› Issue (8): 1175-1195.doi: 10.3969/j.issn.1671-1122.2025.08.001
Previous Articles Next Articles
Compatibility Evaluation and Optimization of CAN Bus Intrusion Detection Systems in In-Vehicle Ethernet Environment
CAO Yue1, FANG Boying1( ), WEI Gaoda1, LI Jinyu1, YANG Yang2, PENG Tao3,4
), WEI Gaoda1, LI Jinyu1, YANG Yang2, PENG Tao3,4
- 1. School of Cyber Science and Engineering, Wuhan University, Wuhan 430040, China
2. Wuhan INCHTEK Technology Co., Ltd., Wuhan 430056, China
3. Datang Interconnect Technology (Wuhan) Co., Ltd., Wuhan 430056, China
4. Hubei Provincial Engineering Research Center for Industrial Internet Integration Technology, Wuhan 430056, China
-
Received:2025-03-19Online:2025-08-10Published:2025-09-09
CLC Number:
Cite this article
CAO Yue, FANG Boying, WEI Gaoda, LI Jinyu, YANG Yang, PENG Tao. Compatibility Evaluation and Optimization of CAN Bus Intrusion Detection Systems in In-Vehicle Ethernet Environment[J]. Netinfo Security, 2025, 25(8): 1175-1195.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.08.001
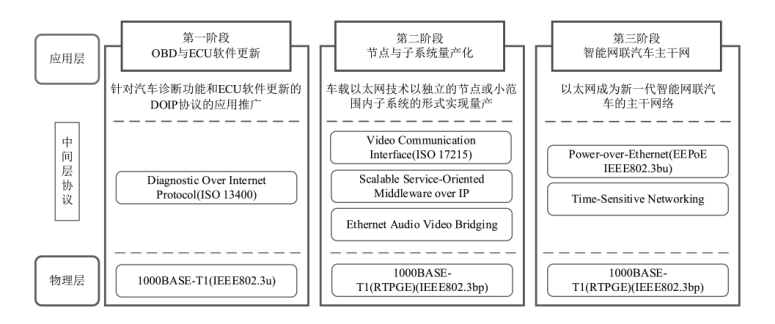
| 评估维度 | 二级标准 | 基准分 | 评分标准 | |
|---|---|---|---|---|
| F1维度协议特性依赖性(40%) | F1.1显式协议依赖 | 6分 | 每依赖一个CAN数据帧专有字段特征(如CAN ID、CAN DLC)或CAN协议独有的通信特征(如基于CAN ID优先级的广播式传输)扣2分,最多扣6分 | |
| F1.2协议无关声明 | 0分 | 每依赖一个CAN协议无关特征(如载荷熵、消息时间间隔),加2分 | ||
| F2维度检测方法兼容性(25%) | F2.1网络层次抽象度 | - | 方法基于物理层信号特征(如电压、时钟),得1分 | |
| 方法基于链路层通用属性(如帧间隔、载荷熵),得3分 | ||||
| 方法基于网络层或传输层特性(如具体协议范式),得5分 | ||||
| F2.2以太网攻击覆盖范围 | 0分 | 能检测CAN总线特有攻击(如检测基于高优先级ID的DDoS攻击),不加分 | ||
| 能检测CAN与车载以太网共有攻击(如数据注入攻击、重放攻击),每种共有攻击加1分,最多加5分 | ||||
| F3维度处理能力适应性(15%) | F3.1检测算法复杂度 | - | 规则方法(算法复杂度近似O(1)), 得10分 | |
| 轻量机器学习方法(算法复杂度近似O(n)~O(nlog n)),得7分 | 若提及模型压缩、数据量减少等优化机制,额外加2分 | |||
| 采用深度学习模型(算法复杂度近似O(n2)), 得5分 | ||||
| F4维度检测架构扩展性(20%) | F4.1模块化 设计 | 0分 | 具有模块化设计,例如,明确划分协议解析、检测模块、响应模块等,得4分 | |
| F4.2组件可替换性 | 0分 | 关键组件易于替换升级而不影响整体架构运行,每具备一个可替换的独立模块加2分,最多加6分 | ||
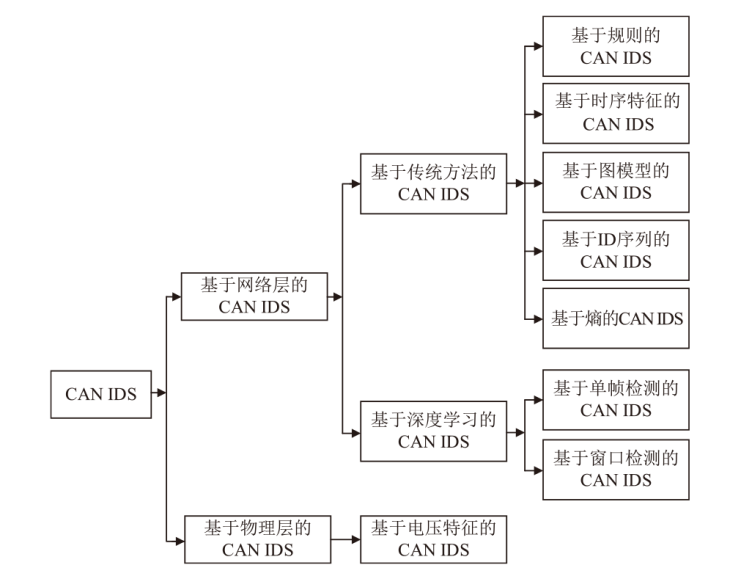
| 方法 | 分类 | IDS入侵检测原理 | F1(40%) | F2(25%) | F3(15%) | F4(20%) | S | 兼容性评级 | |||
|---|---|---|---|---|---|---|---|---|---|---|---|
| F1.1 | F1.2 | F2.1 | F2.2 | F3.1 | F4.1 | F4.2 | |||||
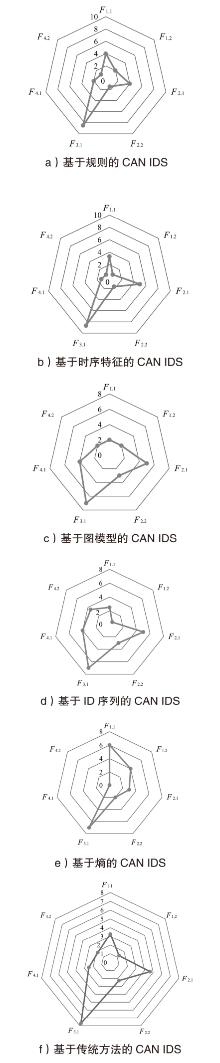
| 文献[ | 图模型 | 计算正常CAN消息的图属性均值和标准差,并设置阈值,从而识别出异常数据 | 2 | 2 | 5 | 3 | 7 | 4 | 2 | 5.85 | 中 |
| 文献[ | 时序 特征 | 检验具有相同ID消息的时间间隔,并与统计数据对比以实现入侵检测 | 4 | 2 | 5 | 1 | 10 | 0 | 0 | 5.40 | 中 |
| 文献[ | ID 序列 | 通过HMM建模正常ID序列的转移概率分布,通过检测异常ID转移模式来识别入侵行为 | 2 | 0 | 5 | 2 | 7 | 4 | 2 | 4.80 | 低 |
| 文献[ | 规则 | 基于CAN协议规范进行入侵检测 | 2 | 2 | 5 | 3 | 10 | 0 | 0 | 5.10 | 中 |
| 文献[ | 规则 | 基于CAN消息字段的规范评分进行入侵检测 | 6 | 2 | 3 | 0 | 7 | 4 | 2 | 6.20 | 中 |
| 文献[ | 时序 特征 | 定期发送远程帧,并分析响应消息的特征 | 2 | 0 | 5 | 2 | 9 | 0 | 0 | 3.90 | 低 |
| 文献[ | 时序 特征 | 通过提取实时消息时序模型参数,构建正常行为规范识别异常 | 4 | 0 | 5 | 2 | 7 | 4 | 2 | 5.60 | 中 |
| 文献[ | ID 序列 | 通过马尔可夫转移矩阵建模正常ID序列的转移概率分布,通过检测异常转移模式来识别攻击行为 | 2 | 0 | 5 | 2 | 7 | 4 | 2 | 4.80 | 低 |
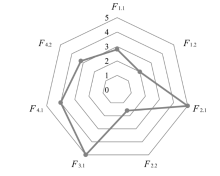
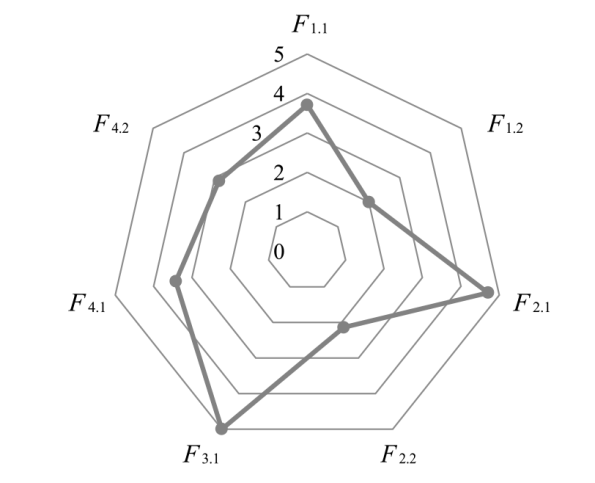
| 文献[ | ID 序列 | 基于ID序列白名单的入侵检测 | 2 | 2 | 5 | 5 | 7 | 4 | 4 | 6.85 | 高 |
| 文献[ | ID 序列 | 基于改进的Levenshtein距离和N-gram算法计算相邻帧相似度的IDS | 4 | 0 | 5 | 3 | 7 | 4 | 6 | 6.65 | 高 |
| 文献[ | 熵 | 基于熵检测,熵的计算仅考虑静态字段内容,未考虑动态特征 | 6 | 4 | 3 | 2 | 7 | 0 | 0 | 6.30 | 中 |
| 方法 | IDS入侵检测原理 | F1(40%) | F2(25%) | F3(15%) | F4(20%) | S | 兼容性评级 | |||
|---|---|---|---|---|---|---|---|---|---|---|
| F1.1 | F1.2 | F2.1 | F2.2 | F3.1 | F4.1 | F4.2 | ||||
| 文献[ | 采用基于单帧特征向量的CNN网络进行检测 | 2 | 2 | 5 | 1 | 5 | 4 | 2 | 5.05 | 中 |
| 文献[ | 基于GAN深度学习模型实现无监督入侵检测 | 4 | 2 | 5 | 1 | 5 | 4 | 4 | 6.25 | 中 |
| 文献[ | 使用前馈神经网络进行监督学习入侵检测,通过CAN ID和数据字节作为输入特征识别异常 | 4 | 2 | 5 | 0 | 5 | 4 | 2 | 5.60 | 中 |
| 文献[ | 使用基于注意力机制的深度学习模型分析单个CAN数据帧,通过学习正常行为特征识别并检测异常行为 | 2 | 2 | 5 | 1 | 5 | 4 | 4 | 5.45 | 中 |
| 文献[ | 通过增强型杜鹃过滤器构建正常流量与入侵流量的索引表,以实现高效的入侵检测 | 2 | 2 | 5 | 5 | 5 | 4 | 4 | 5.95 | 中 |
| 方法 | IDS入侵检测原理 | F1(40%) | F2(25%) | F3(15%) | F4(20%) | S | 兼容性评级 | |||
|---|---|---|---|---|---|---|---|---|---|---|
| F1.1 | F1.2 | F2.1 | F2.2 | F3.1 | F4.1 | F4.2 | ||||
| 文献[ | CANnolo使用LSTM自动编码器学习CAN总线数据序列的正常行为,并通过重建误差检测异常 | 4 | 2 | 5 | 2 | 5 | 4 | 4 | 6.50 | 高 |
| 文献[ | 结合基于规则和基于机器学习的入侵检测方法,旨在平衡高检测率和低计算成本 | 2 | 2 | 5 | 3 | 5 | 4 | 4 | 5.95 | 中 |
| 文献[ | CANet将每个CAN ID对应的LSTM输出特征聚合为联合潜在向量,并通过计算重建误差来实现入侵检测 | 4 | 2 | 5 | 3 | 5 | 4 | 2 | 6.35 | 中 |
| 文献[ | 使用LSTM模型进行时间序列预测,并结合交叉熵损失函数计算异常信号 | 4 | 2 | 5 | 3 | 5 | 4 | 2 | 6.35 | 中 |
| 文献[ | 使用双向GPT模型进行入侵检测 | 4 | 2 | 5 | 2 | 5 | 0 | 2 | 5.30 | 中 |
| 文献[ | 使用滑动窗口方法将连续的CAN消息组合成固定长度的序列,并将每个序列作为一个整体进行检测 | 4 | 2 | 5 | 1 | 5 | 4 | 4 | 6.25 | 中 |
| 文献[ | 将连续的CAN消息序列转换为图像形式的数据表示,并基于BCNN网络实现入侵检测 | 4 | 2 | 3 | 1 | 5 | 4 | 2 | 5.35 | 中 |
| 方法 | IDS入侵检测原理 | F1(40%) | F2(25%) | F3(15%) | F4(20%) | S | 兼容性评级 | |||
|---|---|---|---|---|---|---|---|---|---|---|
| F1.1 | F1.2 | F2.1 | F2.2 | F3.1 | F4.1 | F4.2 | ||||
| 文献[ | VALID通过采集CAN总线上的电压波形,提取信号的统计特征,并与正常行为的基准进行比较,进而实现入侵检测 | 4 | 2 | 1 | 1 | 5 | 4 | 6 | 5.65 | 中 |
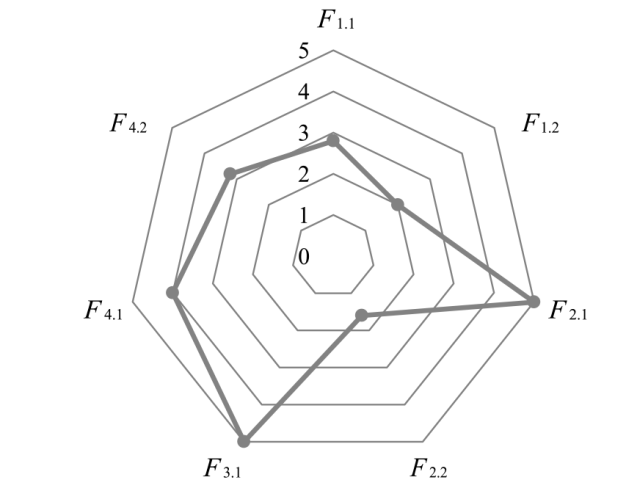
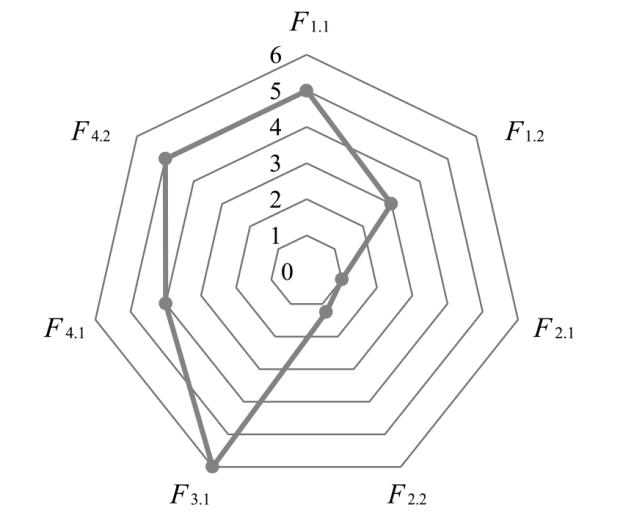
| 文献[ | 对信号来源进行合法性验证,并构建ECU的指纹数据库,通过对比实时采集的电压曲线与数据库中的特征,识别网络中的异常ECU节点 | 6 | 4 | 1 | 3 | 7 | 4 | 2 | 7.25 | 高 |
| 文献[ | 通过分析CAN信号的电压波形来检测异常行为 | 6 | 2 | 1 | 0 | 5 | 4 | 6 | 6.20 | 中 |
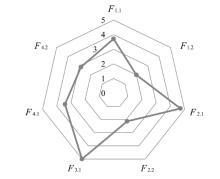
| 文献[ | 通过为每个CAN ID建立电压指纹,将测试帧与对应ID的指纹进行匹配,利用GMM计算匹配得分,进而判定其是否为恶意帧 | 4 | 4 | 1 | 1 | 7 | 4 | 6 | 6.75 | 高 |
| [1] | China-SAE, National Intelligent Connected Vehicle Innovation Center. Annual Report on the Development of China Intelligent Connected Vehicle Industry(2023-2024)[M]. Beijing: Social Sciences Literature Publishing House, 2024. |
| 中国汽车工程学会, 国家智能网联汽车创新中心. 中国智能网联汽车产业发展报告(2023-2024)[M]. 北京: 社会科学文献出版社, 2024. | |
| [2] | National Development and Reform Commission of the People's Republic of China, Ministry of Industry and Information Technology of the People's Republic of China, Ministry of Science and Technology of the People's Republic of China, et al. Innovative Development Strategy for Intelligent Vehicles[EB/OL]. (2020-02-24)[2025-03-01]. https://www.ndrc.gov.cn/xxgk/zcfb/tz/202002/P020200224573058971435.pdf. |
| 中华人民共和国国家发展和改革委员会, 中华人民共和国工业和信息化部, 中华人民共和国科学技术部, 等. 智能汽车创新发展战略[EB/OL]. (2020-02-24)[2025-03-01]. https://www.ndrc.gov.cn/xxgk/zcfb/tz/202002/P020200224573058971435.pdf. | |
| [3] | Ministry of Industry and Information Technology of the People's Republic of China, Ministry of Public Security of the People's Republic of China, Ministry of Housing and Urban-Rural Development of the People's Republic of China, et al. Notice from Four Ministries on Launching Pilot Projects for Intelligent Connected Vehicles Access and Road Traffic[EB/OL].(2023-11-17)[2025-03-01].https://www.gov.cn/zhengce/zhengceku/202311/content_6915788.htm. |
| 中华人民共和国工业和信息化部, 中华人民共和国公安部, 中华人民共和国住房和城乡建设部, 等. 四部委关于开展智能网联汽车准入和上路通行试点工作的通知[EB/OL]. (2023-11-17)[2025-03-01]. https://www.gov.cn/zhengce/zhengceku/202311/content_6915788.htm. | |
| [4] | LAMPE B, MENG Weizhi. A Survey of Deep Learning-Based Intrusion Detection in Automotive Applications[EB/OL]. (2023-07-01)[2025-03-01]. https://www.sciencedirect.com/science/article/pii/S0957417423002725. |
| [5] | RAJAPAKSHA S, KALUTARAGE H, AL-KADRI M O, et al. AI-Based Intrusion Detection Systems for In-Vehicle Networks: A Survey[J]. ACM Computing Surveys, 2023, 55(11): 1-40. |
| [6] | HAN M L, KWAKET B I, KIM H K, et al. TOW-IDS: Intrusion Detection System Based on Three Overlapped Wavelets for Automotive Ethernet[J]. IEEE Transactions on Information Forensics and Security, 2022(18): 411-422. |
| [7] | CAO Yue, LYU Chenchen, SUN Yaping, et al. Review of Research on Misbehavior Detection in VANET[J]. Netinfo Security, 2023, 23(4): 10-19. |
| 曹越, 吕臣臣, 孙娅苹, 等. 面向车联网环境的异常行为检测机制研究综述[J]. 信息网络安全, 2023, 23(4): 10-19. | |
| [8] | WANG Qiyan, SAWHNEY S. VeCure: A Practical Security Framework to Protect the CAN Bus of Vehicles[C]// IEEE. 2014 International Conference on the Internet of Things (IOT). New York: IEEE, 2014: 13-18. |
| [9] | GROZA B, MURVAY S. Efficient Protocols for Secure Broadcast in Controller Area Networks[J]. IEEE Transactions on Industrial Informatics, 2013, 9(4): 2034-2042. |
| [10] | HERREWEGE A V, SINGELEE D, VERBAUWHEDE I. CANAuth-A Simple, Backward Compatible Broadcast Authentication Protocol for CAN Bus[EB/OL]. (2011-01-01)[2025-03-01]. https://www.researchgate.net/publication/235323481_CANAuth_-_A_Simple_Backward_Compatible_Broadcast_Authentication_Protocol_for_CAN_bus. |
| [11] | SIDDIQUI A S, GUI Yutian, PLUSQUELLIC J, et al. Secure Communication over CANBus[C]// IEEE. 2017 IEEE 60th International Midwest Symposium on Circuits and Systems(MWSCAS). New York: IEEE, 2017: 1264-1267. |
| [12] | HALABI J, ARTAIL H. A Lightweight Synchronous Cryptographic Hash Chain Solution to Securing the Vehicle CAN Bus[C]// IEEE. 2018 IEEE International Multidisciplinary Conference on Engineering Technology(IMCET). New York: IEEE, 2018: 1-6. |
| [13] | VERENDEL V, NILSSON D K, LARSON U E, et al. An Approach to Using Honeypots in In-Vehicle Networks[C]// IEEE. 2008 IEEE 68th Vehicular Technology Conference. New York: IEEE, 2008: 1-5. |
| [14] | HOSSAIN D M, INOUE H, OCHIAI H, et al. An Effective In-Vehicle CAN Bus Intrusion Detection System Using CNN Deep Learning Approach[C]// IEEE. GLOBECOM 2020-2020 IEEE Global Communications Conference. New York: IEEE, 2020: 1-6. |
| [15] | LOKMAN S F, OTHMAN A T, ABU-BAKAR M H. Intrusion Detection System for Automotive Controller Area Network(CAN) Bus System: A Review[J]. EURASIP Journal on Wireless Communications and Networking, 2019(1): 184-200. |
| [16] | HAAS R E, MÖLLER D P F, BANSAL P, et al. Intrusion Detection in Connected Cars[C]// IEEE. 2017 IEEE International Conference on Electro Information Technology (EIT). New York: IEEE, 2017: 516-519. |
| [17] | YANG Zi. Research on Key Technologies of Vehicle Ethernet[J]. Automation Application, 2024, 65(12): 256-258. |
| 杨子. 车载以太网关键技术的研究[J]. 自动化应用, 2024, 65(12): 256-258. | |
| [18] | FU Dandan, ZHAO Jie, MEI Shaonan, et al. Application of Automotive Ethernet Communication Technology Based on Heavy Duty Automobile[J]. Auto Electric Parts, 2021(7): 34-35, 39. |
| 符丹丹, 赵杰, 美少楠, 等. 基于商用车的车载以太网通信技术应用[J]. 汽车电器, 2021(7): 34-35, 39. | |
| [19] | Huaxia EV. A Brief Analysis of the Development Status and Trends of Ethernet Technology in Intelligent Vehicles[EB/OL]. (2022-07-18)[2025-03-01].http://www.evinchina.com/articleshow-180.html. |
| 华夏EV. 简析智能汽车以太网技术发展现状与趋势[EB/OL]. (2022-07-18)[2025-03-01]. http://www.evinchina.com/articleshow-180.html. | |
| [20] | 35.100.10 35.110-Physical layer Networking 802.3cy-2023-IEEE Standard for Ethernet Amendment8: Physical Layer Specifications and Management Parameters for 25 Gb/s-Electrical Automotive Ethernet[S]. New York: IEEE, 2023. |
| [21] | Beijing Xinsijie International Information Consulting Co., Ltd. Deep Research Report on Global and Chinese TSN Switching Chip (Time Sensitive Network Switching Chip) Industry in 2025[EB/OL]. (2024-12-19)[2025-03-01]. http://www.newsijie.com/baogao/2024/1219/11349412.html. |
| 北京新思界国际信息咨询有限公司. 2025年全球及中国TSN交换芯片(时间敏感网络交换芯片)产业深度研究报告[EB/OL]. (2024-12-19)[2025-03-01]. http://www.newsijie.com/baogao/2024/1219/11349412.html. | |
| [22] | DIAO Zhaokun, CAO Shiqiang, MENG Fanli. Technology Development and Application Profiling of Internet of Things Based on “Loud, Pipe, Terminal”[J]. Telecom Engineering Technics and Standardization, 2012, 25(6): 36-41. |
| 刁兆坤, 曹世强, 孟繁丽. 物联网“云管端”的技术发展与应用[J]. 电信工程技术与标准化, 2012, 25(6): 36-41. | |
| [23] | IDTechEX. Future Automotive Technologies 2024-2034: Applications, Megatrends, Forecasts[EB/OL]. (2023-12-19)[2025-03-01]. https://www.idtechex.com/en/research-report/future-automotive-technologies-2024-2034-applications-megatrends-forecasts/979. |
| [24] | REN Kui, YANG Kun, SHEN Haoting, et al. A Survey of Cybersecurity for Intelligent Connected Vehicles[J]. Journal of Cybersecurity, 2024, 2(6): 16-35. |
| [25] | ALFARDUS A, RAWAT D B. Intrusion Detection System for CAN Bus In-Vehicle Network Based on Machine Learning Algorithms[C]// IEEE. 2021 IEEE 12th Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON). New York: IEEE, 2021: 944-949. |
| [26] | KOSCHER K, CZESKIS A, ROESNER F, et al. Experimental Security Analysis of a Modern Automobile[C]// IEEE. 2010 IEEE Symposium on Security and Privacy. New York: IEEE, 2010: 447-462. |
| [27] | GOODIN D. There's a New Form of Keyless Car Theft that Works in under 2 Minutes[EB/OL]. (2023-04-08)[2025-03-01]. https://arstechnica.com/information-technology/2023/04/crooks-are-stealing-cars-using-previously-unknown-keyless-can-injection-attacks/. |
| [28] | HOSSAIN M D, INOUE H, OCHIAI H, et al. LSTM-Based Intrusion Detection System for In-Vehicle Can Bus Communications[J]. IEEE Access, 2020, 8: 185489-185502. |
| [29] |
DOUSS A B C, ABASSI R, SAUVERON D. State-of-the-Art Survey of In-Vehicle Protocols and Automotive Ethernet Security and Vulnerabilities[J]. Mathematical Biosciences and Engineering, 2023, 20(9): 17057-17095.
doi: 10.3934/mbe.2023761 pmid: 37920047 |
| [30] | Huawei Technologies Co., Ltd. IP Autonomous Driving Network White Paper[EB/OL]. (2024-06-27)[2025-03-01]. https://carrier.huawei.com/-/media/cnbgv2/download/products/networks/IP-ADN-WP.pdf. |
| 华为技术有限公司. IP自动驾驶网络白皮书[EB/OL]. (2024-06-27) [2025-03-01]. https://carrier.huawei.com/-/media/cnbgv2/download/products/networks/IP-ADN-WP.pdf. | |
| [31] | CHEN Paizhang. The Analysis of the Common Attacking Methods of TCP/IP Protocol[J]. Journal of Ningde Teachers College(Natural Science), 2010, 22(1): 56-58. |
| 陈派樟. 基于TCP/IP协议的常见攻击方法[J]. 宁德师专学报(自然科学版), 2010, 22(1): 56-58. | |
| [32] | KODURU S, MACHINA S P, MADICHETTY S, et al. Data-Driven Solutions for Next-Generation Automotive Cybersecurity[J]. Transactions of the Indian National Academy of Engineering, 2024, 9(4): 847-866. |
| [33] | JEONG S, KIM H K, HAN M L, et al. AERO: Automotive Ethernet Real-Time Observer for Anomaly Detection in In-Vehicle Networks[J]. IEEE Transactions on Industrial Informatics, 2023, 20(3): 4651-4662. |
| [34] | ALKHATIB N, GHAUCH H, DANGER J L. SOME/IP Intrusion Detection Using Deep Learning-Based Sequential Models in Automotive Ethernet Networks[C]// IEEE. 2021 IEEE 12th Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON). New York: IEEE, 2021: 954-962. |
| [35] | MARQUES D L L F, ARAUJO-FILHO P F D, CAMPELO D R. Multi-Stage Deep Learning-Based Intrusion Detection System for Automotive Ethernet Networks[EB/OL]. (2024-09-01)[2025-03-01]. https://doi.org/10.1016/j.adhoc.2024.103548. |
| [36] | SCHELL O, KNEIB M. VALID: Voltage-Based Lightweight Intrusion Detection for the Controller Area Network[C]// IEEE. 2020 IEEE 19th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom). New York: IEEE, 2020: 225-232. |
| [37] | ISLAM R, REFAT R U D, YERRAM S M, et al. Graph-Based Intrusion Detection System for Controller Area Networks[J]. IEEE Transactions on Intelligent Transportation Systems, 2022, 23(3): 1727-1736. |
| [38] | SONG H M, KIM H R, KIM H K. Intrusion Detection System Based on the Analysis of Time Intervals of CAN Messages for In-Vehicle Network[C]// IEEE. 2016 International Conference on Information Networking (ICOIN). New York: IEEE, 2016: 63-68. |
| [39] | LAMPE B, MENG Weizhi. IDS for CAN: A Practical Intrusion Detection System for CAN Bus Security[C]// IEEE. 2022 IEEE Global Communications Conference (GLOBECOM). New York: IEEE, 2022: 1782-1787. |
| [40] | LONGARI S, NOVA V D H, ZAGO M, et al. CANnolo: An Anomaly Detection System Based on LSTM Autoencoders for Controller Area Network[J]. IEEE Transactions on Network and Service Management, 2021, 18(2): 1913-1924. |
| [41] | ZHANG Linxi, MA Di. A Hybrid Approach Toward Efficient and Accurate Intrusion Detection for In-Vehicle Networks[J]. IEEE Access, 2022(10): 10852-10866. |
| [42] | LARSON U E, NILSSON D K, JONSSON E. An Approach to Specification-Based Attack Detection for In-Vehicle Networks[C]// IEEE. 2008 IEEE Intelligent Vehicles Symposium. New York: IEEE, 2008: 220-225. |
| [43] | MARKOVITZ M, WOOL A. Field Classification, Modeling and Anomaly Detection in Unknown CAN Bus Networks[J]. Vehicular Communications, 2017(9): 43-52. |
| [44] | LEE H, JEONG S H, KIM H K. OTIDS: A Novel Intrusion Detection System for In-Vehicle Network by Using Remote Frame[C]// IEEE. 2017 15th Annual Conference on Privacy, Security and Trust (PST). New York: IEEE, 2017: 5700-5709. |
| [45] | OLUFOWOBI H, YOUNG C, ZAMBRENO J, et al. SAIDuCANT: Specification-Based Automotive Intrusion Detection Using Controller Area Network (CAN) Timing[J]. IEEE Transactions on Vehicular Technology, 2020, 69(2): 1484-1494. |
| [46] | MARCHETTI M, STABILI D. Anomaly Detection of CAN Bus Messages through Analysis of ID Sequences[C]// IEEE. 2017 IEEE Intelligent Vehicles Symposium (IV). New York: IEEE, 2017: 1577-1583. |
| [47] | DÖNMEZ T C M. Anomaly Detection in Vehicular CAN Bus Using Message Identifier Sequences[J]. IEEE Access, 2021(9): 136243-136252. |
| [48] | SONG Jiaru, QIN Guihe, LIANG Yanhua, et al. SIDiLDNG: A Similarity-Based Intrusion Detection System Using Improved Levenshtein Distance and N-Gram for CAN[EB/OL]. (2024-07-05)[2025-03-01]. https://doi.org/10.1016/j.cose.2024.103847. |
| [49] | MÜTER M, ASAJ N. Entropy-Based Anomaly Detection for In-Vehicle Networks[C]// IEEE. 2011 IEEE Intelligent Vehicles Symposium(IV). New York: IEEE, 2011: 1110-1115. |
| [50] | SEO E, SONG H M, KIM H K. GIDS: GAN Based Intrusion Detection System for In-Vehicle Network[C]// IEEE. 2018 16th Annual Conference on Privacy, Security and Trust (PST). New York: IEEE, 2018: 1-6. |
| [51] | SAMI M, IBARRA M, ESPARZA A C, et al. Rapid, Multi-Vehicle and Feed-Forward Neural Network Based Intrusion Detection System for Controller Area Network Bus[C]// IEEE. 2020 IEEE Green Energy and Smart Systems Conference (IGESSC). New York: IEEE, 2020: 1-6. |
| [52] | NASRELDIN A, BAHAA-ELDIN A M, SOBH M A. In-Vehicle Intrusion Detection Based on Deep Learning Attention Technique[C]// IEEE. 2021 16th International Conference on Computer Engineering and Systems(ICCES). New York: IEEE, 2021: 1-7. |
| [53] | LI Sifan, CAO Yue, HADI H J, et al. ECF-IDS: An Enhanced Cuckoo Filter-Based Intrusion Detection System for In-Vehicle Network[J]. IEEE Transactions on Network and Service Management, 2024, 21(4): 3846-3860. |
| [54] | HANSELMANN M, STRAUSS T, DORMANN K, et al. CANet: An Unsupervised Intrusion Detection System for High Dimensional CAN Bus Data[J]. IEEE Access, 2020(8): 58194-58205. |
| [55] | DESTA A K, OHIRA S, ARAI I, et al. MLIDS: Handling Raw High-Dimensional CAN Bus Data Using Long Short-Term Memory Networks for Intrusion Detection in In-Vehicle Networks[C]// IEEE. 2020 30th International Telecommunication Networks and Applications Conference (ITNAC). New York: IEEE, 2020: 1-7. |
| [56] | NAM M, PARK S, KIM D S. Intrusion Detection Method Using Bi-Directional GPT for In-Vehicle Controller Area Networks[J]. IEEE Access, 2021(9): 124931-124944. |
| [57] | AGRAWAL K, ALLADI T, AGRAWAL A, et al. NovelADS: A Novel Anomaly Detection System for Intra-Vehicular Networks[J]. IEEE Transactions on Intelligent Transportation Systems, 2022, 23(11): 22596-22606. |
| [58] | ZHANG Linxi, YAN Xuke, MA Di. Efficient and Effective In-Vehicle Intrusion Detection System Using Binarized Convolutional Neural Network[C]// IEEE. IEEE INFOCOM 2024-IEEE Conference on Computer Communications. New York: IEEE, 2024: 2299-2307. |
| [59] | CHO K T, SHIN K. Viden: Attacker Identification on In-Vehicle Networks[EB/OL]. (2017-08-28)[2025-03-01]. https://doi.org/10.48550/arXiv.1708.08414. |
| [60] | CHOI W, JOO K, JO H J, et al. VoltageIDS: Low-Level Communication Characteristics for Automotive Intrusion Detection System[J]. IEEE Transactions on Information Forensics and Security, 2018, 13(8): 2114-2129. |
| [61] | DENG Zhouyan, LIU Jiajia, XUN Yijie, et al. IdentifierIDS: A Practical Voltage-Based Intrusion Detection System for Real In-Vehicle Networks[J]. IEEE Transactions on Information Forensics and Security, 2023(19): 661-676. |
| [1] | XUN Yijie, CUI Jiarong, MAO Bomin, QIN Junman. Intrusion Detection System for the Controller Area Network Bus of Intelligent Vehicles Based on Federated Learning [J]. Netinfo Security, 2025, 25(6): 872-888. |
| [2] | LIU Chenfei, WAN Liang. CAN Bus Intrusion Detection Method Based on Spatio-Temporal Graph Neural Networks [J]. Netinfo Security, 2025, 25(3): 478-493. |
| [3] | JIANG Rong, LIU Haitian, LIU Cong. Unsupervised Network Intrusion Detection Method Based on Ensemble Learning [J]. Netinfo Security, 2024, 24(3): 411-426. |
| [4] | PENG Hanzhong, ZHANG Zhujun, YAN Liyue, HU Chenglin. Research on Intrusion Detection Mechanism Optimization Based on Federated Learning Aggregation Algorithm under Consortium Chain [J]. Netinfo Security, 2023, 23(8): 76-85. |
| [5] | JIN Zhigang, LIU Kai, WU Xiaodong. A Review of IDS Research in Smart Grid AMI Field [J]. Netinfo Security, 2023, 23(1): 1-8. |
| [6] | REN Tao, JIN Ruochen, LUO Yongmei. Network Intrusion Detection Algorithm Integrating Blockchain and Federated Learning [J]. Netinfo Security, 2021, 21(7): 27-34. |
| [7] | JIANG Nan, CUI Yaohui, WANG Jian, WU Jinchao. Context-based Attack Scenario Reconstruction Model for IDS Alarms [J]. Netinfo Security, 2020, 20(7): 1-10. |
| [8] | Dongmei CHENG, Biao YAN, Hui WEN, Limin SUN. The Design and Implement of Rule Matching-based Distributed Intrusion Detection Framework for Industry Control System [J]. Netinfo Security, 2017, 17(7): 45-51. |
| [9] | Tingting SHI, Youjian ZHAO. Overviews of Network Intrusion Evasion and Defense Techniques [J]. Netinfo Security, 2016, 16(1): 70-74. |
| [10] | Yi-zhou ZHOU, Bin WANG, Xiao-quan XIE. Design of Software Defined Intrusion Detection System in Cloud [J]. Netinfo Security, 2015, 15(9): 191-195. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||