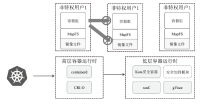
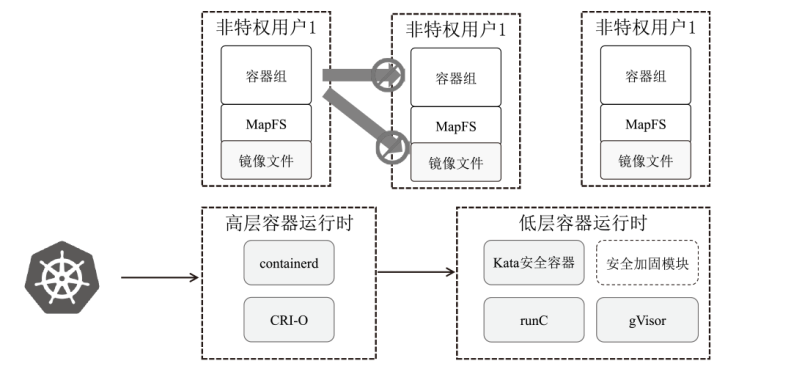
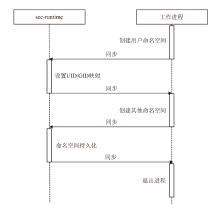
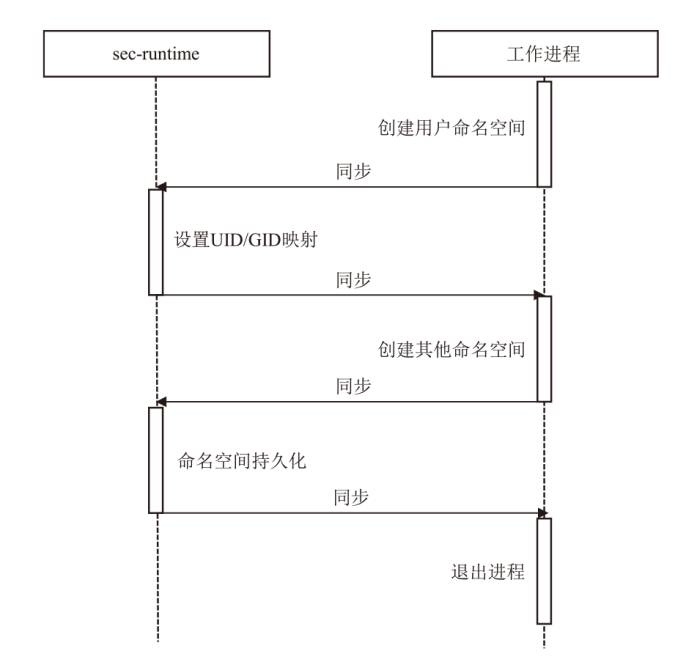
| [1] |
JARKAS O, KO R, DONG Naipeng, et al. A Container Security Survey: Exploits, Attacks, and Defenses[J]. ACM Computing Surveys, 2025, 57(7): 1-36.
|
| [2] |
WANG Yazhe, REN Lei, FENG Dengguo, et al. Security Enhancements for New-Generation PLC of the Industrial Internet Integrating Sensing, Computing, Control and Intelligence: Trends and Perspectives[J]. Chinese Journal of Computers, 2025, 48(3): 738-762.
|
|
王雅哲, 任磊, 冯登国, 等. 面向感算控智一体化融合的工业互联网新型PLC安全增强:趋势与展望[J]. 计算机学报, 2025, 48(3): 738-762.
|
| [3] |
BIAN Manlin, WANG Liming. Analysis and Research on Vulnerability of Docker Container Isolation in Cloud Environment[J]. Netinfo Security, 2020, 20(7): 85-95.
|
|
边曼琳, 王利明. 云环境下Docker容器隔离脆弱性分析与研究[J]. 信息网络安全, 2020, 20(7): 85-95.
|
| [4] |
BARNAWI N, AITOOQ R, ALMUKAYNIZI M. Mitigating Container Escape Threats through Effective Countermeasures: A Survey[EB/OL]. (2024-08-19)[2025-02-15]. https://avestia.com/EECSS2024_Proceedings/files/paper/CIST/CIST_164.pdf.
|
| [5] |
NADGOWDA S, SUNEJA S, ISCI C. RECap: Run-Escape Capsule for on Demand Managed Service Delivery in the Cloud[EB/OL]. [2025-02-15]. https://www.usenix.org/system/files/conference/hotcloud18/hotcloud18-paper-nadgowda.pdf.
|
| [6] |
RunC-CVE-2019-5736[EB/OL]. [2025-02-15]. ttps://www.doc88.com/p-08973989221016.html.
|
| [7] |
SULTAN S, AHMAD I, DIMITRIOU T. Container Security: Issues, Challenges, and the Road Ahead[J]. IEEE Access, 2019, 7: 52976-52996.
|
| [8] |
ABBAS M, KHAN S, MONUM A, et al. PACED: Provenance-Based Automated Container Escape Detection[C]// IEEE. 2022 IEEE International Conference on Cloud Engineering. New York: IEEE, 2022: 261-272.
|
| [9] |
DEVI P V S, CHAKKARAVARTHY S S, KHAN M K. Container Security: Precaution Levels, Mitigation Strategies, and Research Perspectives[EB/OL]. (2023-09-22)[2025-02-15]. https://doi.org/10.1016/j.cose.2023.103490.
|
| [10] |
LEE K, KIM J, KWON I H, et al. Impact of Secure Container Runtimes on File I/O Performance in Edge Computing[EB/OL]. (2023-12-18)[2025-02-15]. https://doi.org/10.3390/app132413329.
|
| [11] |
COMBE T, MARTIN A, DI PO R. To Docker or not to Docker: A Security Perspective[J]. IEEE Cloud Computing, 2016, 3(5): 54-62.
|
| [12] |
PONTES R, CARVALHO P, MAIA F, et al. SafeFS: A Modular Architecture for Secure User-Space File Systems: One FUSE to Rule them All[EB/OL]. (2017-05-22)[2025-02-15]. https://dl.acm.org/doi/abs/10.1145/3078468.3078480.
|
| [13] |
REEVES M. Investigating Escape Vulnerabilities in Container Runtimes[D]. West Lafayette: Purdue University, 2021.
|
| [14] |
LI Yun, HUANG Chenlin, YUAN Lu, et al. ASPGen: An Automatic Security Policy Generating Framework for AppArmor[C]// IEEE. 2020 IEEE Intl Conf on Parallel & Distributed Processing with Applications, Big Data & Cloud Computing, Sustainable Computing & Communications, Social Computing & Networking. New York: IEEE, 2020: 392-400.
|
| [15] |
BAKER S A, MOHAMMED H H, ALSAIF O I. Docker Container Security Analysis Based on Virtualization Technologies[EB/OL]. [2025-02-15]. https://www.nstl.gov.cn/paper_detail.html?id=62263f7377f8741360ca99b0009570ac.
|
| [16] |
LI Dong, YU Junqing, WEN Ruibin, et al. Endogenous Security Methods for Container Cloud Based on IPv6[J]. Netinfo Security, 2023, 23(12): 21-28.
|
|
李冬, 于俊清, 文瑞彬, 等. 基于IPv6的容器云内生安全机制[J]. 信息网络安全, 2023, 23(12): 21-28.
|
| [17] |
MINNA F, MASSACCI F. SoK: Run-Time Security for Cloud Microservices. Are We There Yet?[EB/OL]. (2023-01-24)[2025-02-15]. https://doi.org/10.1016/j.cose.2023.103119.
|
| [18] |
YOUNG E G, ZHU Pengfei, CARAZA-HARTER T, et al. The True Cost of Containing: A Gvisor Case Study[EB/OL]. [2025-02-15]. https://www.xueshufan.com/publication/2965859899.
|
| [19] |
AGACHE A, BROOKER M, IORDACHE A, et al. Firecracker: Lightweight Virtualization for Serverless Applications[EB/OL]. [2025-02-15]. https://www.xueshufan.com/publication/3010457348.
|
| [20] |
SOLTESZ S, PÖTZL H, FIUCZYNSKI M E, et al. Container-Based Operating System Virtualization[J]. ACM SIGOPS Operating Systems Review, 2007, 41(3): 275-287.
|
| [21] |
HOF A V, NIEH J. BlackBox: A Container Security Monitor for Protecting Containers on Untrusted Operating Systems[EB/OL]. (2022-07-11)[2025-02-15]. https://www.cs.columbia.edu/-nieh/pubs/osdi2022_blackbox.pdf.
|
| [22] |
HE Yi, GUO Ziyi, XING Yunlong, et al. Cross Container Attacks: The Bewildered eBPF on Clouds[EB/OL]. [2025-02-15].https://www.usenix.org/conference/usenixsecurity23/presentation/he.
|
| [23] |
SUN Yuqiong, SAFFORD D, ZOHAR M, et al. Security Namespace: Making Linux Security Frameworks Available to Containers[C]// USENIX. The 27th USENIX Security Symposium. Berkeley: USENIX, 2018: 1423-1439.
|
| [24] |
BORATE I, R K. Sandboxing in Linux: From Smartphone to Cloud[J]. International Journal of Computer Applications, 2016, 148(8): 1-8.
|
| [25] |
KAISER S, HAQ M S, TOSUN A Ş, et al. Container Technologies for ARM Architecture: A Comprehensive Survey of the State-of-the-Art[J]. IEEE Access, 2022, 10: 84853-84881.
|
| [26] |
HAYDEN M, CARBONE R. Securing Linux Containers[EB/OL]. (2015-07-26)[2025-02-15]. https://major.io/wp-content/uploads/2015/08/Securing-Linux-Containers-GCUX-Gold-Paper-Major-Hayden.pdf.
|
| [27] |
LI Zhi, LIU Weijie, WANG Xiaofeng, et al. Lost along the Way: Understanding and Mitigating Path-Misresolution Threats to Container Isolation[C]// ACM. The 2023 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2023: 3063-3077.
|
 )
)