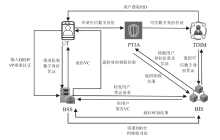
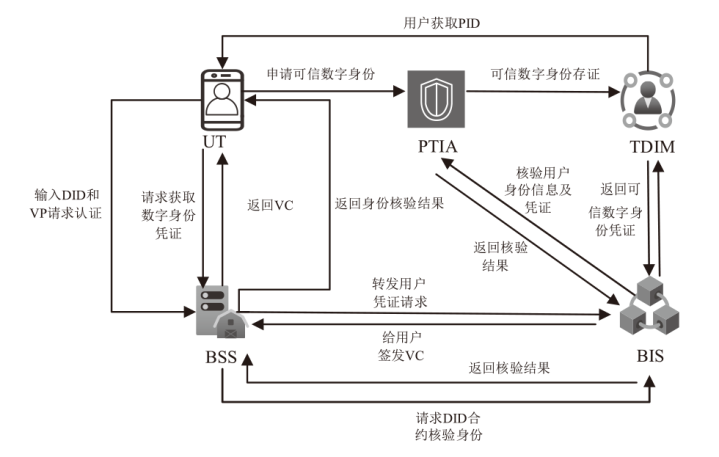
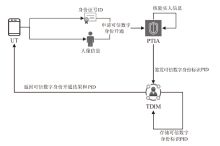
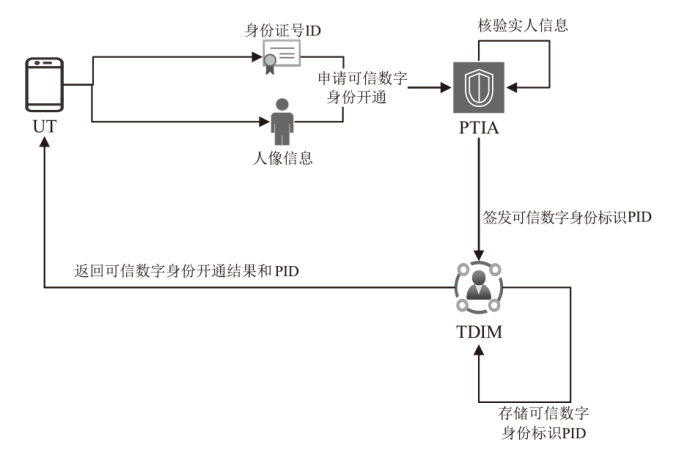
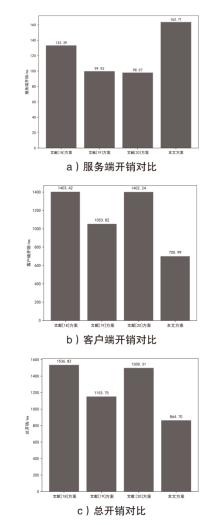
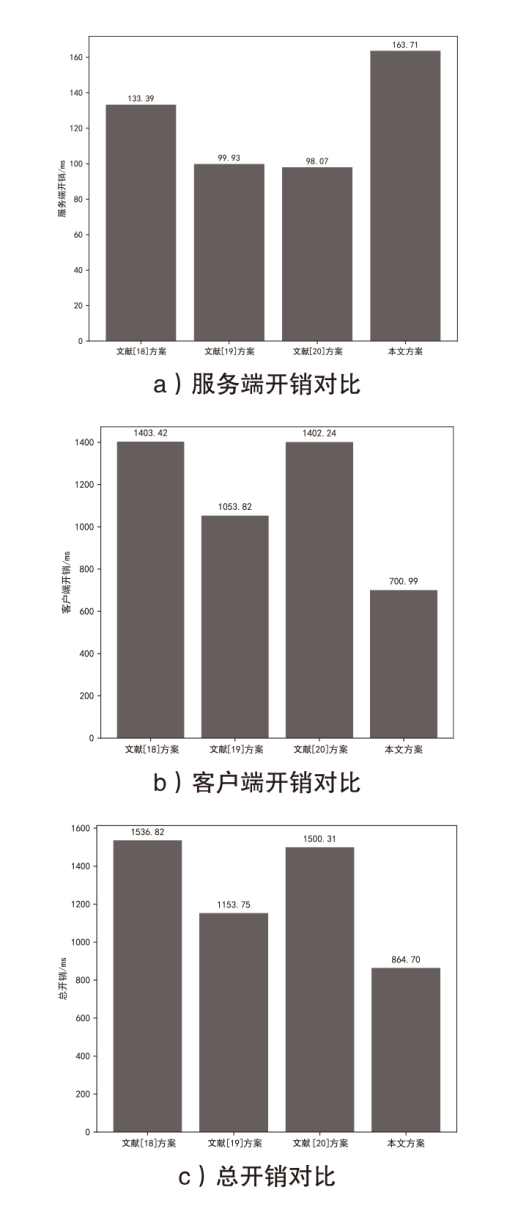
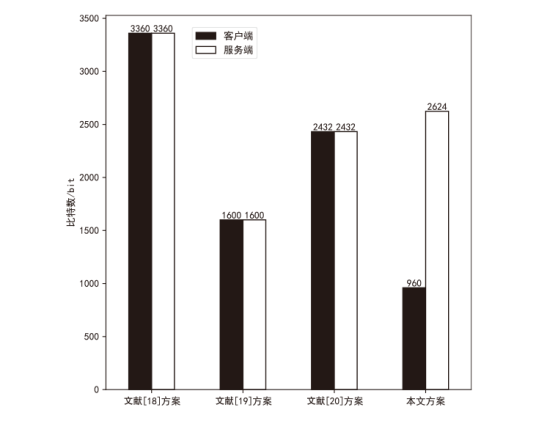
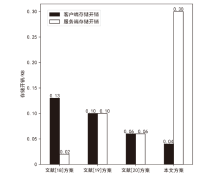
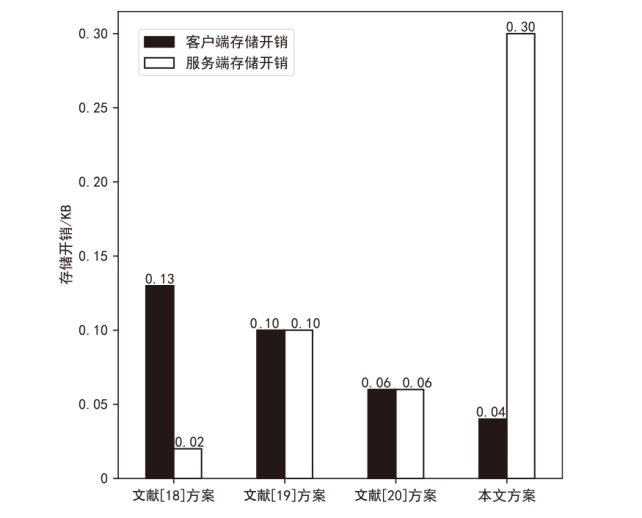
Netinfo Security ›› 2025, Vol. 25 ›› Issue (5): 817-827.doi: 10.3969/j.issn.1671-1122.2025.05.013
Previous Articles Next Articles
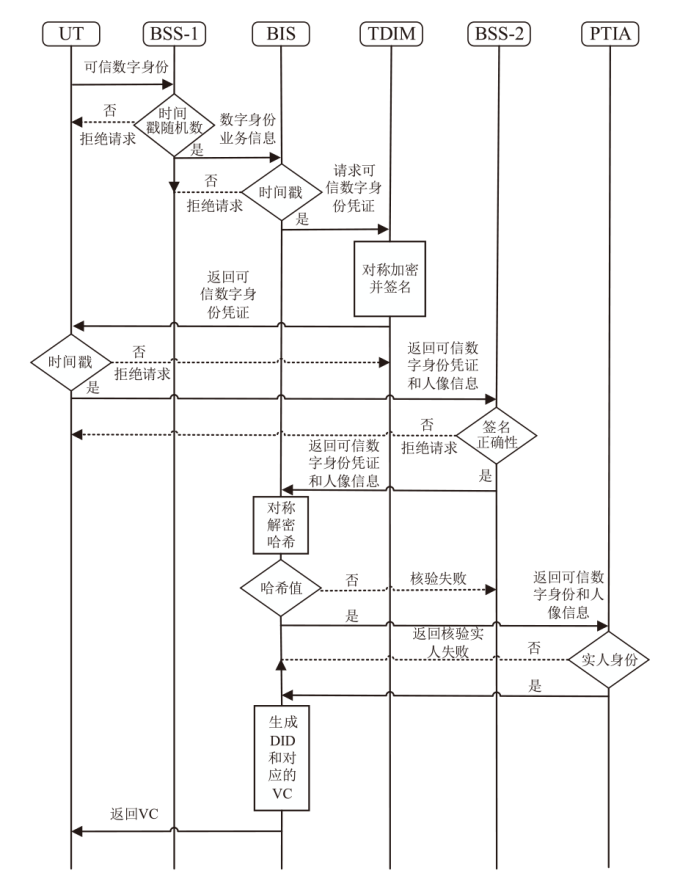
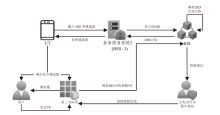
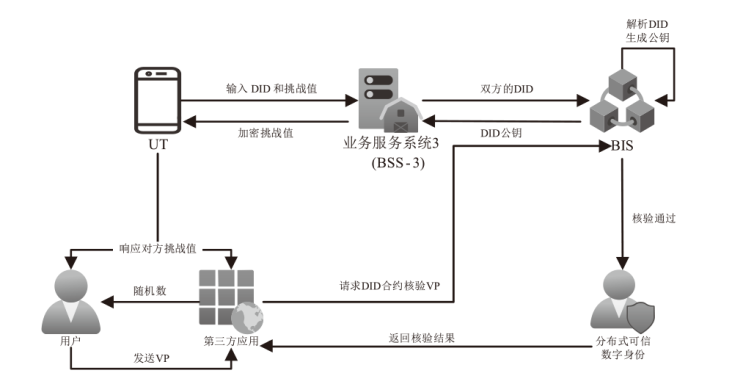
Lightweight Distributed Authentication Scheme Based on Trusted Digital Identity
ZHU Xiaoqiang1( ), ZHANG Haowen2, LIN Yanzi2, LIU Jiqiang1
), ZHANG Haowen2, LIN Yanzi2, LIU Jiqiang1
- 1. School of Cyberspace Science and Technology, Beijing Jiaotong University, Beijing 100044, China
2. School of Software, Beijing Jiaotong University, Beijing 100044, China
-
Received:2025-03-06Online:2025-05-10Published:2025-06-10
CLC Number:
Cite this article
ZHU Xiaoqiang, ZHANG Haowen, LIN Yanzi, LIU Jiqiang. Lightweight Distributed Authentication Scheme Based on Trusted Digital Identity[J]. Netinfo Security, 2025, 25(5): 817-827.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.05.013
| [1] | PODGORELEC B, ALBER L, ZEFFERER T. What is A (Digital) Identity Wallet?A Systematic Literature Review[C]// IEEE. 2022 IEEE 46th Annual Computers, Software, and Applications Conference (COMPSAC). New York: IEEE, 2022: 809-818. |
| [2] | WANG Miaomiao, RUI Lanlan, YANG Yang, et al. A Blockchain-Based Multi-CA Cross-Domain Authentication Scheme in Decentralized Autonomous Network[J]. IEEE Transactions on Network and Service Management, 2022, 19(3): 2664-2676. |
| [3] | WANG Shushuang, MA Zhaofeng, LIU Jiawei, et al. Research and Implementation of Cross-Chain Security Access and Identity Authentication Scheme of Blockchain[J]. Netinfo Security, 2022, 22(6): 61-72. |
| 王姝爽, 马兆丰, 刘嘉微, 等. 区块链跨链安全接入与身份认证方案研究与实现[J]. 信息网络安全, 2022, 22(6): 61-72. | |
| [4] | MA Zhaofeng, WANG Xiaochang, JAIN D K, et al. A Blockchain-Based Trusted Data Management Scheme in Edge Computing[J]. IEEE Transactions on Industrial Informatics, 2019, 16(3): 2013-2021. |
| [5] | JAROUCHEH Z, ÁLVAREZ I A. Secretation: Toward a Decentralised Identity and Verifiable Credentials Based Scalable and Decentralised Secret Management Solution[C]// IEEE. 2021 IEEE International Conference on Blockchain and Cryptocurrency (ICBC). New York: IEEE, 2021: 1-9. |
| [6] | JÄRPEHULT O, ÅGREN F J, BÄCKSTRÖM M, et al. A Longitudinal Characterization of The Third-Party Authentication Landscape[C]// IEEE. 2022 IFIP Networking Conference (IFIP Networking). New York: IEEE, 2022: 1-9. |
| [7] | ALOM I, ESHITA R M, HARUN A I, et al. Dynamic Management of Identity Federations Using Blockchain[C]// IEEE. 2021 IEEE International Conference on Blockchain and Cryptocurrency (ICBC). New York: IEEE, 2021: 1-9. |
| [8] | MANU S, DAVE L, DAVID C. Verifiable Credentials Data Model 1.0- Expressing Verifiable Information on the Web[EB/OL]. (2022-03-03)[2025-02-25]. https://www.w3.org/TR/vc-data-model/. |
| [9] | KORTESNIEMI Y, LAGUTIN D, ELO T, et al. Improving the Privacy of IoT with Decentralised Identifiers (DIDs)[EB/OL]. (2019-03-20)[2025-02-25]. https://onlinelibrary.wiley.com/doi/10.1155/2019/8706760. |
| [10] | FAN Xinxin, CHAI Qi, XU Lei, et al. Diam-Iot: A Decentralized Identity and Access Management Framework for Internet of Things[C]// ACM. Proceedings of the 2nd ACM International Symposium on Blockchain and Secure Critical Infrastructure. New York: ACM, 2020: 186-191. |
| [11] | ZHOU Tong, ZHAO He, LI Xiaofeng. EverSSDI: Blockchain-Based Framework for Verification, Authorisation and Recovery of Self-Sovereign Identity Using Smart Contracts[J]. International Journal of Computer Applications in Technology, 2019, 60(3): 281-295. |
| [12] | WANG Fennie, FILIPPI P D. Self-Sovereign Identity in a Globalized World: Credentials-Based Identity Systems as a Driver for Economic Inclusion[EB/OL]. (2020-01-23)[2025-02-25]. https://www.mendeley.com/catalogue/ead94f80-fd2a-3138-a848-9c4a2dd29aa9/. |
| [13] | LI Qinan, XUE Zhihao. A Privacy-Protecting Authorization System Based on Blockchain and Zk-SNARK[C]// ACM. The 2020 International Conference on Cyberspace Innovation of Advanced Technologies. New York: ACM, 2020: 439-444. |
| [14] | SI Bingru, XIAO Jiang, LIU Cunyang, et al. Survey on Blockchain Network[J]. Journal of Software, 2024, 35(2): 773-799. |
| 司冰茹, 肖江, 刘存扬, 等. 区块链网络综述[J]. 软件学报, 2024, 35(2):773-799. | |
| [15] | WANG Ze, LIN Jingqiang, CAI Quanwei, et al. Blockchain-Based Certificate Transparency and Revocation Transparency[J]. IEEE Transactions on Dependable and Secure Computing, 2022, 19(1): 681-697. |
| [16] | LUNDKVIST C, HECK R, TORSTENSSON J, et al. Uport: A Platform for Self-Sovereign Identity[EB/OL]. (2016-10-20)[2025-02-25]. https://www.blockchainlab.com/pdf/uPort_whitepaper_DRAFT20161020.pdf. |
| [17] | ZHU Xiaoqiang, LIU Jiqiang, LU Lingyun, et al. Enabling Intelligent Connectivity:A Survey of Secure ISAC in 6G Networks[EB/OL]. (2024-07-24)[2025-02-25]. https://resources.hutubox.com/user-file/cab15ae4255a1d7982bf5cc2b785e4ee.pdf. |
| [18] | HE Debiao, ZEADALLY S, KUMAR N, et al. Anonymous Authentication for Wireless Body Area Networks with Provable Security[J]. IEEE Systems Journal, 2016, 11(4): 2590-2601. |
| [19] | REN Jie, LI Meihong, DU Ye, et al. Identity-Based Authentication Key Agreement Protocol for Horizontal Federated Learning Environment[J]. Journal of Beijing University of Aeronautics and Astronautics, 2023, 49(2): 397-405. |
| 任杰, 黎妹红, 杜晔, 等. 横向联邦学习环境基于身份认证及密钥协商协议[J]. 北京航空航天大学学报, 2023, 49(2):397-405. | |
| [20] | KULJEET K, GARG S, GEORGES K, et al. A Lightweight and Privacy-Preserving Authentication Protocol for Mobile Edge Computing[C]// IEEE. Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM). New York: IEEE, 2019: 1-6. |
| [21] | TSOBDJOU L D, PIERRE S, QUINTERO A. A New Mutual Authentication and Key Agreement Protocol for Mobile Client-Server Environment[J]. IEEE Transactions on Network and Service Management, 2021, 18(2): 1275-1286. |
| [22] | LIU Xin, YANG Haorui, GUO Zhenbin, et al. An Authentication Protocol Achieving Online Registrationand Privilege Separation for Industrial Internet of Things[J]. Netinfo Security, 2021, 21(7): 1-9. |
| 刘忻, 杨浩睿, 郭振斌, 等. 一种实现在线注册与权限分离的工业物联网身份认证协议[J]. 信息网络安全, 2021, 21(7):1-9. |
| [1] | YE Jiajun, GAO Cuifeng, XUE Yinxing. Research on Price Oracle Manipulation Source Code Detection Method Based on Static Analysis [J]. Netinfo Security, 2025, 25(5): 732-746. |
| [2] | QIN Jinlei, KANG Yimin, LI Zheng. Lightweight Fine-Grained Multi-Dimensional Multi-Subset Privacy-Preserving Data Aggregation for Smart Grid [J]. Netinfo Security, 2025, 25(5): 747-757. |
| [3] | YANG Yatao, DING Yucheng, LIU Peihe, SANG Peng. Research on Blockchain-Based Privacy Preservation and Digital Authentication [J]. Netinfo Security, 2025, 25(4): 640-653. |
| [4] | ZHANG Yuxuan, HUANG Cheng, LIU Rong, LENG Tao. Smart Contract Vulnerability Detection Method Combining Prompt Tuning [J]. Netinfo Security, 2025, 25(4): 664-673. |
| [5] | LI Qiang, SHEN Yuanhai, WANG Jinze, HUANG Yanyu, SUN Jianguo. An Offline-Online Signature Scheme for Industrial Internet of Things Environment [J]. Netinfo Security, 2025, 25(3): 392-402. |
| [6] | WANG Yong, WU Yifan, WAN Qiancheng. Research on Redactable Blockchain Scheme Based on the Chinese Remainder Theorem [J]. Netinfo Security, 2025, 25(1): 36-47. |
| [7] | XIA Zhe, XIA Xuezhi, LYU Wenjie, ZHANG Mingwu. Certificate-Based Locally Verifiable Aggregate Signature Scheme in VANETs [J]. Netinfo Security, 2025, 25(1): 48-62. |
| [8] | DUAN Haozhe, LI Zhihui, WEI Xingjia, HU Kexin. Quantum Identity Authentication Protocol without Entanglement in d-Dimensional Quantum System [J]. Netinfo Security, 2024, 24(9): 1364-1374. |
| [9] | YU Lisu, LI Biao, YAO Yuanzhi, WEN Jiajin, LI Zipeng, WANG Zhen. Performance Optimization of Blockchain-Assisted Unmanned Aerial Vehicle Mobile Edge Computing System [J]. Netinfo Security, 2024, 24(9): 1432-1443. |
| [10] | SUN Zhongxiu, PENG Cheng, FAN Wei. System Broadcast Information Authentication Protocol Based on Certificateless Signature for 5G Network [J]. Netinfo Security, 2024, 24(8): 1220-1230. |
| [11] | LYU Qiuyun, ZHOU Lingfei, REN Yizhi, ZHOU Shifei, SHENG Chunjie. A Lifecycle-Manageable Public Data Sharing Scheme [J]. Netinfo Security, 2024, 24(8): 1291-1305. |
| [12] | HUANG Wangwang, ZHOU Hua, WANG Daiqiang, ZHAO Qi. Design of Reconfigurable Key Security Authentication Protocol for IoT Based on National Cryptography SM9 [J]. Netinfo Security, 2024, 24(7): 1006-1014. |
| [13] | ZHANG Jiwei, WANG Wenjun, NIU Shaozhang, GUO Xiangkuo. Blockchain Scaling Solutions: ZK-Rollup Review [J]. Netinfo Security, 2024, 24(7): 1027-1037. |
| [14] | GUO Rui, YANG Xin, WANG Junming. Verifiable and Revocable Attribute Encryption Scheme Based on Blockchain [J]. Netinfo Security, 2024, 24(6): 863-878. |
| [15] | LING Zhi, YANG Ming, YU Jiangyin. Research on Power Security Trading Platform Based on IPFS and Blockchain Technology [J]. Netinfo Security, 2024, 24(6): 968-976. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||