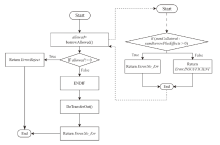
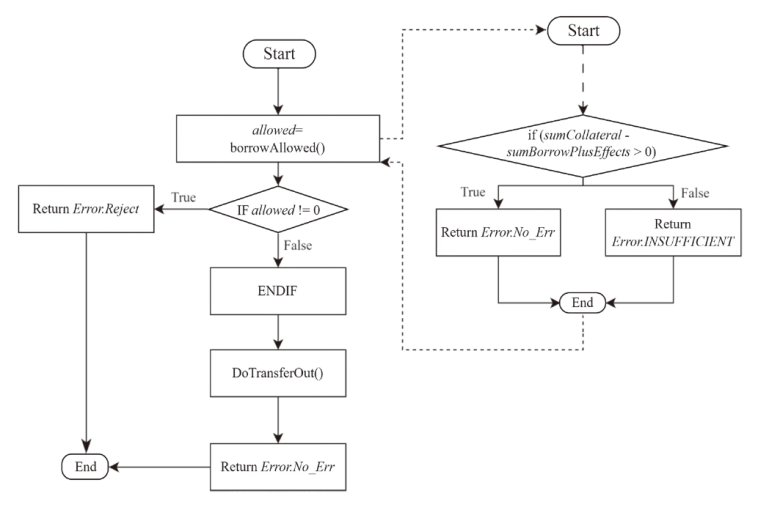
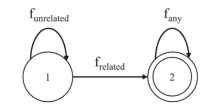
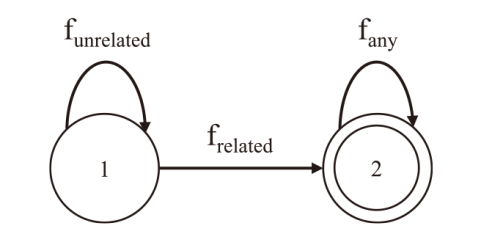
Netinfo Security ›› 2025, Vol. 25 ›› Issue (5): 732-746.doi: 10.3969/j.issn.1671-1122.2025.05.006
Previous Articles Next Articles
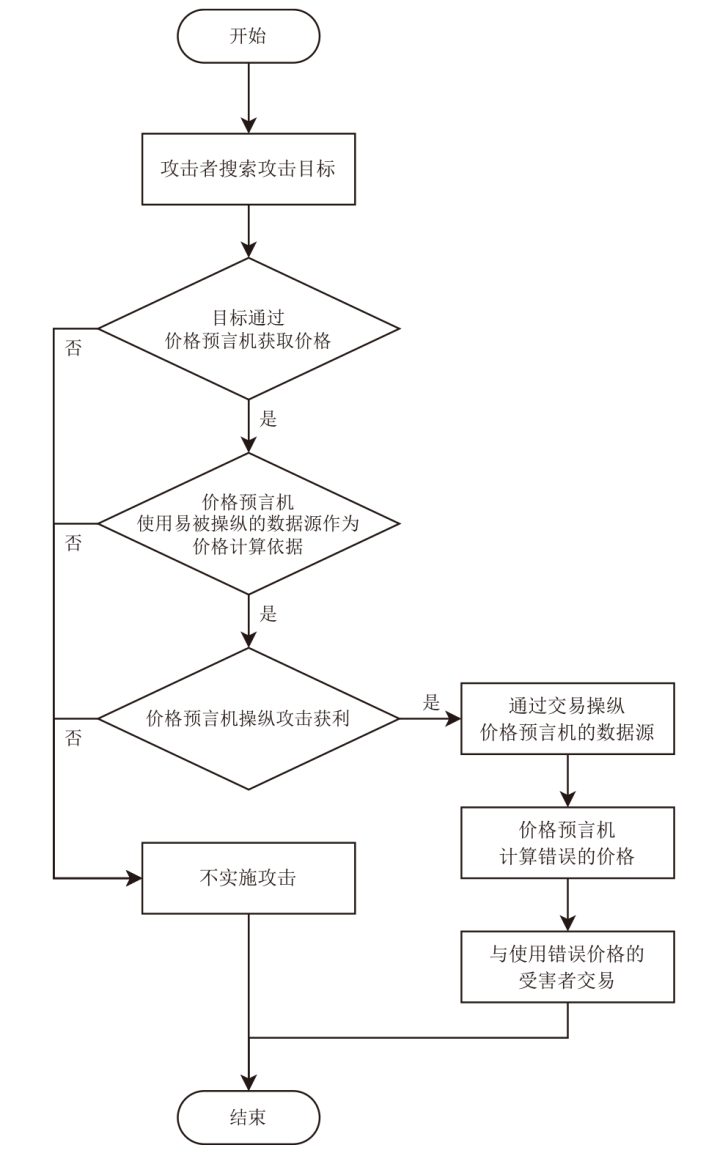
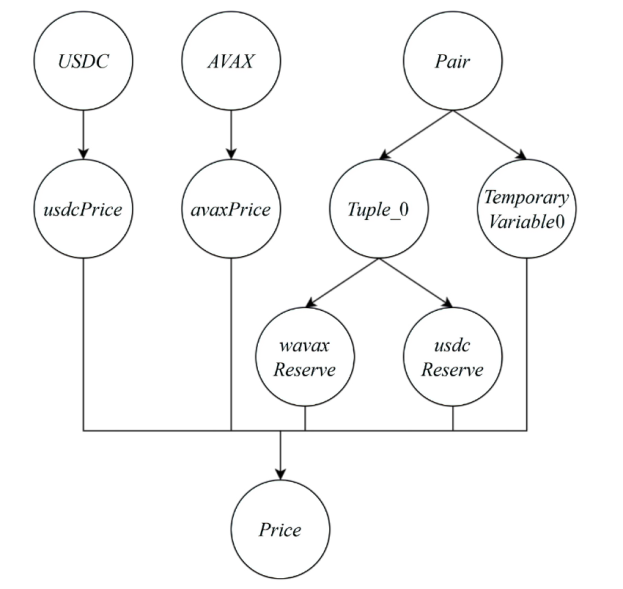
Research on Price Oracle Manipulation Source Code Detection Method Based on Static Analysis
YE Jiajun, GAO Cuifeng, XUE Yinxing( )
)
- Department of Computer Science and Technology, University of Science and Technology of China, Hefei 230026, China
-
Received:2024-04-29Online:2025-05-10Published:2025-06-10
CLC Number:
Cite this article
YE Jiajun, GAO Cuifeng, XUE Yinxing. Research on Price Oracle Manipulation Source Code Detection Method Based on Static Analysis[J]. Netinfo Security, 2025, 25(5): 732-746.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.05.006
| [1] | BUTERIN V. A Next-Generation Smart Contract and Decentralized Application Platform[J]. White Paper, 2014, 3(37): 1-36. |
| [2] | NAKAMOTO S. Bitcoin: A Peer-to-Peer Electronic Cash System[EB/OL]. [2024-04-10]. https://bitcoin.org/en/bitcoin-paper. |
| [3] | DefiLlama. DeFi Dashboard[EB/OL]. (2024-03-20)[2024-04-10]. https://defillama.com/. |
| [4] | SZABO N. Formalizing and Securing Relationships on Public Networks[J]. First Monday, 1997, 2(9): 1-25. |
| [5] | BARTOLETTI M, POMPIANU L. An Empirical Analysis of Smart Contracts:Platforms, Applications, and Design Patterns[C]// Springer. Financial Cryptography and Data Security. Heidelberg: Springer, 2017: 494-509. |
| [6] | MEHAR M I, SHIER C L, GIAMBATTISTA A, et al. Understanding a Revolutionary and Flawed Grand Experiment in Blockchain[J]. Journal of Cases on Information Technology, 2019, 21(1): 19-32. |
| [7] | QIAN Peng, LIU Zhenguang, HE Qinming, et al. Smart Contract Vulnerability Detection Technique: A Survey[J]. Journal of Software, 2022, 33(8): 3059-3085. |
| 钱鹏, 刘振广, 何钦铭, 等. 智能合约安全漏洞检测技术研究综述[J]. 软件学报, 2022, 33(8):3059-3085. | |
| [8] | ZHANG Zhuo, ZHANG B, XU Wen, et al. Demystifying Exploitable Bugs in Smart Contracts[C]// IEEE. 2023 IEEE/ACM 45th International Conference on Software Engineering (ICSE). New York: IEEE, 2023: 615-627. |
| [9] | WU Siwei, WANG Dabao, HE Jianting, et al. DeFiRanger: Detecting Price Manipulation Attacks on DeFi Applications[EB/OL]. (2021-04-30)[2024-04-10]. https://arxiv.org/abs/2104.15068v1. |
| [10] | ZHANG Wuqi, WEI Lili, CHEUNG S C, et al. Combatting Front-Running in Smart Contracts: Attack Mining, Benchmark Construction and Vulnerability Detector Evaluation[J]. IEEE Transactions on Software Engineering, 2023, 49(6): 3630-3646. |
| [11] | QIN Kaihua, ZHOU Liyi, LIVSHITS B, et al. Attacking the DeFi Ecosystem with Flash Loans for Fun and Profit[C]// Springer. Financial Cryptography and Data Security. Heidelberg: Springer, 2021: 3-32. |
| [12] | DONG Weiliang, LIU Zhe, LIU Kui, et al. Survey on Vulnerability Detection Technology of Smart Contracts[J]. Journal of Software, 2024, 35(1): 38-62. |
| 董伟良, 刘哲, 刘逵, 等. 智能合约漏洞检测技术综述[J]. 软件学报, 2024, 35(1): 38-62. | |
| [13] | ALMAKHOUR M, SLIMAN L, SAMHAT A E, et al. Verification of Smart Contracts: A Survey[EB/OL]. (2019-06-10)[2024-04-10]. https://doi.org/10.1016/j.pmcj.2020.101227. |
| [14] | LUU L, CHU D H, OLICKEL H, et al. Making Smart Contracts Smarter[C]// ACM. Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2016: 254-269. |
| [15] | GRIECO G, SONG W, CYGAN A, et al. Echidna:Effective, Usable, and Fast Fuzzing for Smart Contracts[C]// ACM. Proceedings of the 29th ACM SIGSOFT International Symposium on Software Testing and Analysis. New York: ACM, 2020: 557-560. |
| [16] | CHESS B, MCGRAW G. Static Analysis for Security[J]. IEEE Security & Privacy, 2004, 2(6): 76-79. |
| [17] | SCHNEIDEWIND C, GRISHCHENKO I, SCHERER M, et al. EThor: Practical and Provably Sound Static Analysis of Ethereum Smart Contracts[C]// ACM. Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2020: 621-640. |
| [18] | TIKHOMIROV S, VOSKRESENSKAYA E, IVANITSKIY I, et al. SmartCheck: Static Analysis of Ethereum Smart Contracts[C]// IEEE. 2018 IEEE/ACM 1st International Workshop on Emerging Trends in Software Engineering for Blockchain (WETSEB). New York: IEEE, 2018: 9-16. |
| [19] | FEIST J, GRIECO G, GROCE A. Slither: A Static Analysis Framework for Smart Contracts[C]// IEEE. 2019 IEEE/ACM 2nd International Workshop on Emerging Trends in Software Engineering for Blockchain (WETSEB). New York: IEEE, 2019: 8-15. |
| [20] | CYTRON R, FERRANTE J, ROSEN B K, et al. Efficiently Computing Static Single Assignment Form and the Control Dependence Graph[J]. ACM Transactions on Programming Languages and Systems, 1991, 13(4): 451-490. |
| [21] | ABDELAZIZ T, HOBOR A. Smart Learning to Find Dumb Contracts (Extended Version)[EB/OL]. (2023-06-27)[2024-04-10]. https://arxiv.org/abs/2304.10726v2. |
| [22] | TJIAM K, WANG Rui, CHEN Huanhuan, et al. Your Smart Contracts are Not Secure: Investigating Arbitrageurs and Oracle Manipulators in Ethereum[C]// ACM. Proceedings of the 3rd Workshop on Cyber-Security Arms Race. New York: ACM, 2021: 25-35. |
| [23] | WANG S H, WU C C, LIANG Yuchuan, et al. ProMutator: Detecting Vulnerable Price Oracles in DeFi by Mutated Transactions[C]// IEEE. 2021 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW). New York: IEEE, 2021: 380-385. |
| [24] | DENG Xun, BEILLAHI S M, MINWALLA C, et al. Safeguarding DeFi Smart Contracts against Oracle Deviations[C]// ACM. Proceedings of the IEEE/ACM 46th International Conference on Software Engineering. New York: ACM, 2024: 1-12. |
| [25] | Tintinweb. Smart Contract Sanctuary[EB/OL]. (2024-03-20)[2024-04-10]. https://github.com/tintinweb/smart-contract-sanctuary.git/. |
| [1] | YANG Yatao, DING Yucheng, LIU Peihe, SANG Peng. Research on Blockchain-Based Privacy Preservation and Digital Authentication [J]. Netinfo Security, 2025, 25(4): 640-653. |
| [2] | ZHANG Yuxuan, HUANG Cheng, LIU Rong, LENG Tao. Smart Contract Vulnerability Detection Method Combining Prompt Tuning [J]. Netinfo Security, 2025, 25(4): 664-673. |
| [3] | ZHANG Liqiang, LU Mengjun, YAN Fei. A Cross-Contract Fuzzing Scheme Based on Function Dependencies [J]. Netinfo Security, 2024, 24(7): 1038-1049. |
| [4] | LIU Feng, JIANG Jiaqi, HUANG Hao. Security Overview of Cryptocurrency Trading Media and Processes [J]. Netinfo Security, 2024, 24(3): 330-351. |
| [5] | XU Liangchen, MENG Zhaoyi, HUANG Wenchao, XIONG Yan. Array Processing Loop Compression Method for Program Reachability Verification [J]. Netinfo Security, 2024, 24(3): 374-384. |
| [6] | LI Pengchao, ZHANG Quantao, HU Yuan. Smart Contract Vulnerability Detection Method Based on Graph Convolutional Network with Dual Attention Mechanism [J]. Netinfo Security, 2024, 24(11): 1624-1631. |
| [7] | QIN Sihang, DAI Weiqi, ZENG Haiyan, GU Xianjun. Secure Sharing of Power Application Data Based on Blockchain [J]. Netinfo Security, 2023, 23(8): 52-65. |
| [8] | LI Chunxiao, WANG Yaofei, XU Enliang, ZHAO Yu. Enabling Privacy-Preserving Range Queries in Blockchain-Based Collaborative Databases with Bilinear Pairings [J]. Netinfo Security, 2023, 23(3): 22-34. |
| [9] | CHEN Xingren, XIONG Yan, HUANG Wenchao, FU Guilu. A Multi-View Hardware Trojan Detection Method Based on Static Analysis [J]. Netinfo Security, 2023, 23(10): 48-57. |
| [10] | FENG Yiting, MA Zhaofeng, XU Danheng, DUAN Pengfei. Evaluation Method for Cross-Chain Security Strength Access [J]. Netinfo Security, 2023, 23(1): 84-92. |
| [11] | ZHANG Guanghua, LIU Yongsheng, WANG He, YU Naiwen. Smart Contract Vulnerability Detection Scheme Based on BiLSTM and Attention Mechanism [J]. Netinfo Security, 2022, 22(9): 46-54. |
| [12] | ZHANG Yujian, LIU Daifu, TONG Fei. Reentrancy Vulnerability Detection in Smart Contracts Based on Local Graph Matching [J]. Netinfo Security, 2022, 22(8): 1-7. |
| [13] | HU Yi, SHE Kun. Blockchain and Smart Contract Based Dual-Chain Internet of Vehicles System [J]. Netinfo Security, 2022, 22(8): 26-35. |
| [14] | WANG Jian, HUANG Jun. Smart Contract-Based Log Secure Storage and Fair Access Method [J]. Netinfo Security, 2022, 22(7): 27-36. |
| [15] | YU Kechen, GUO Li, YIN Hongwei, YAN Xuesong. The High-Value Data Sharing Model Based on Blockchain and Game Theory for Data Centers [J]. Netinfo Security, 2022, 22(6): 73-85. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||