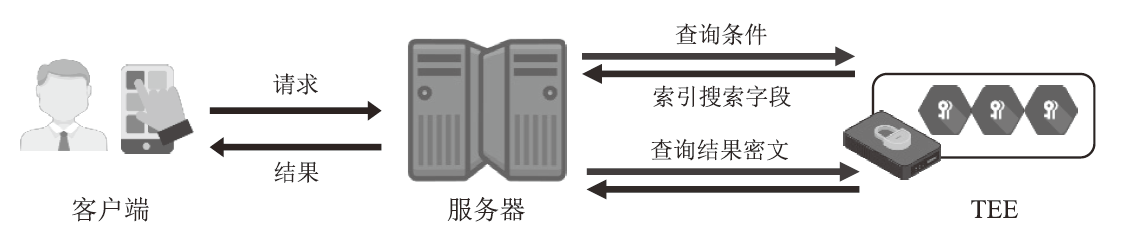
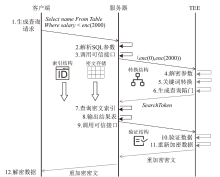
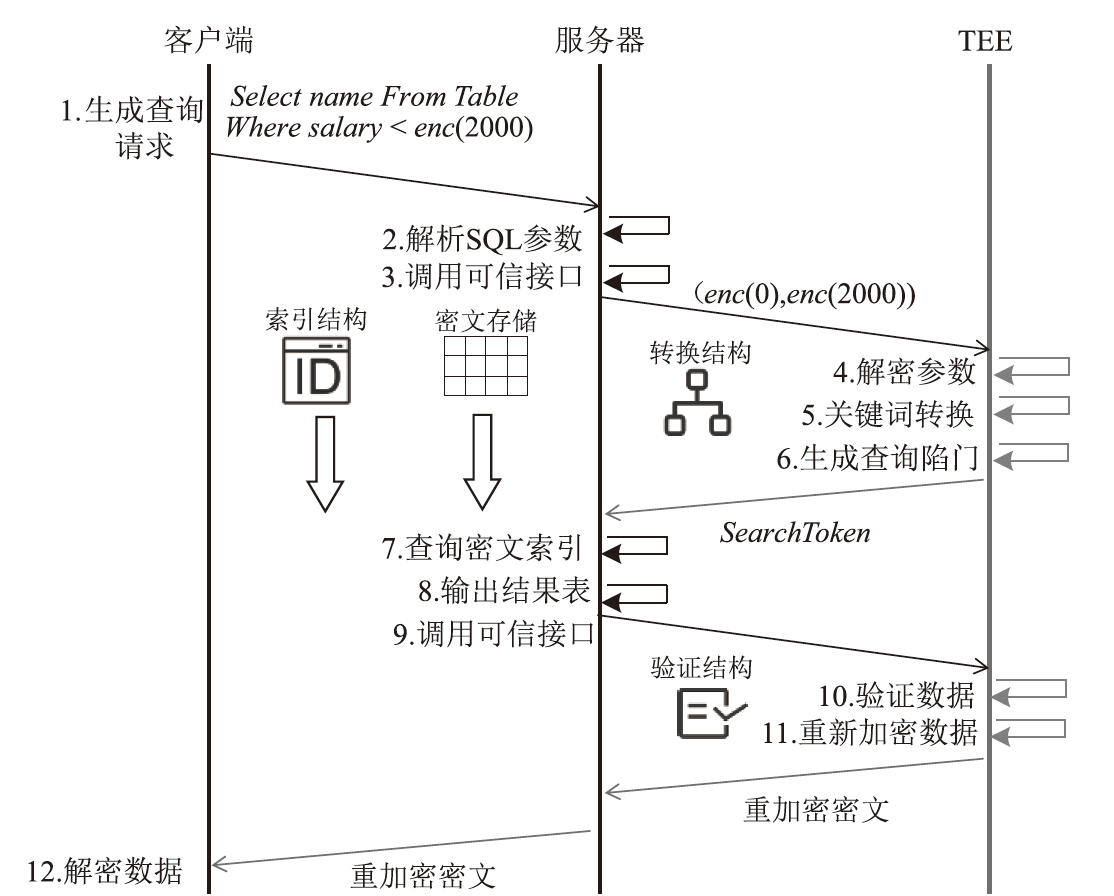
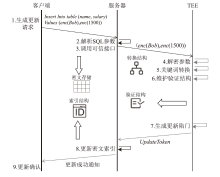
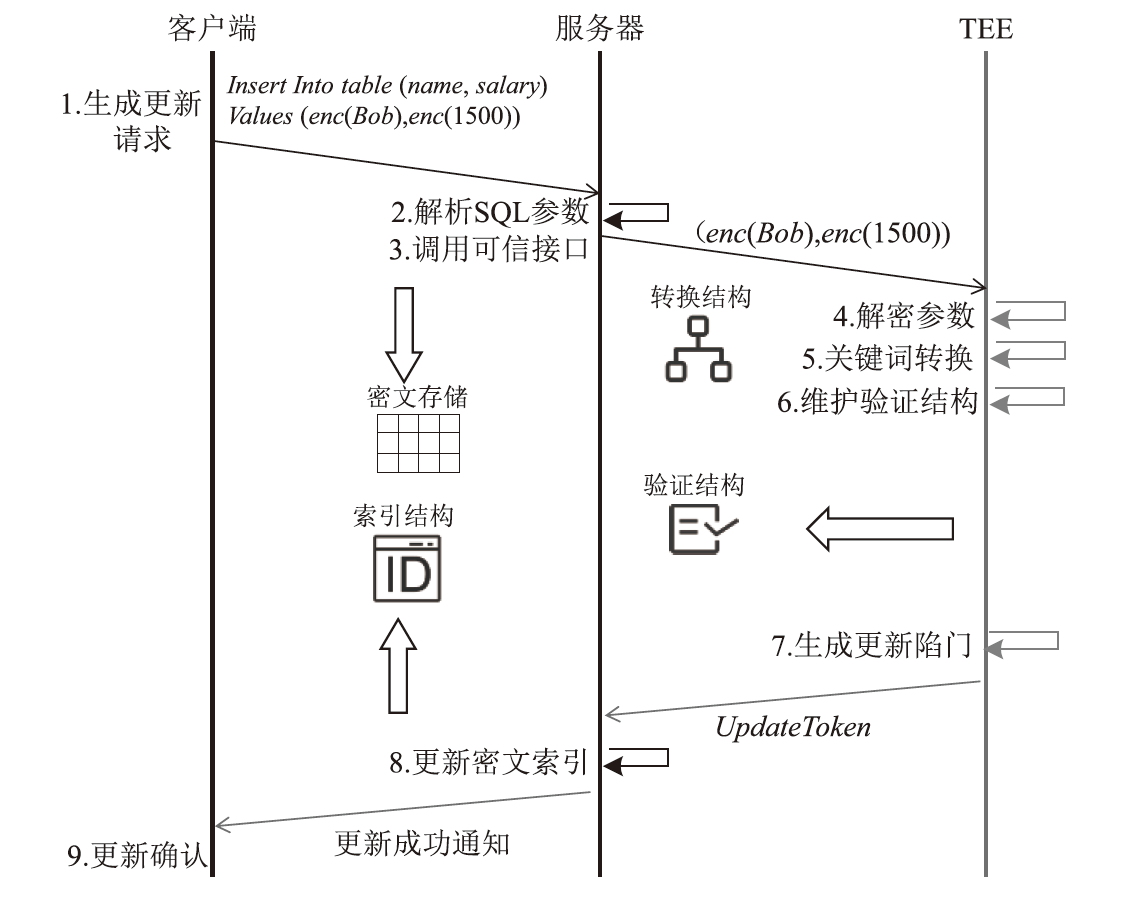
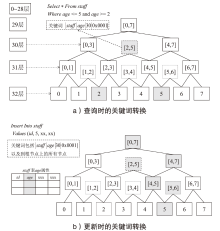
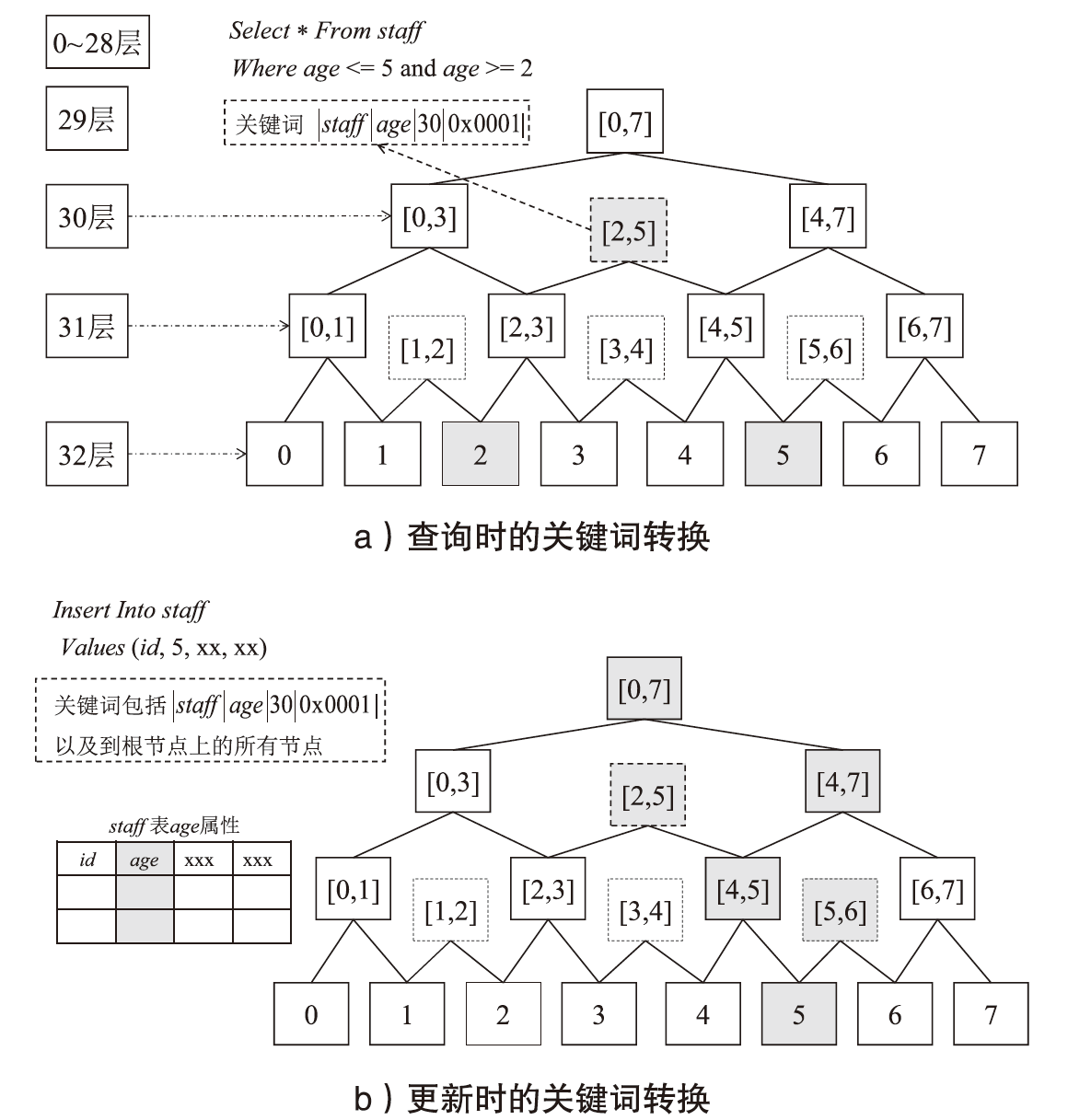
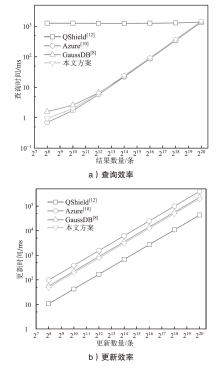
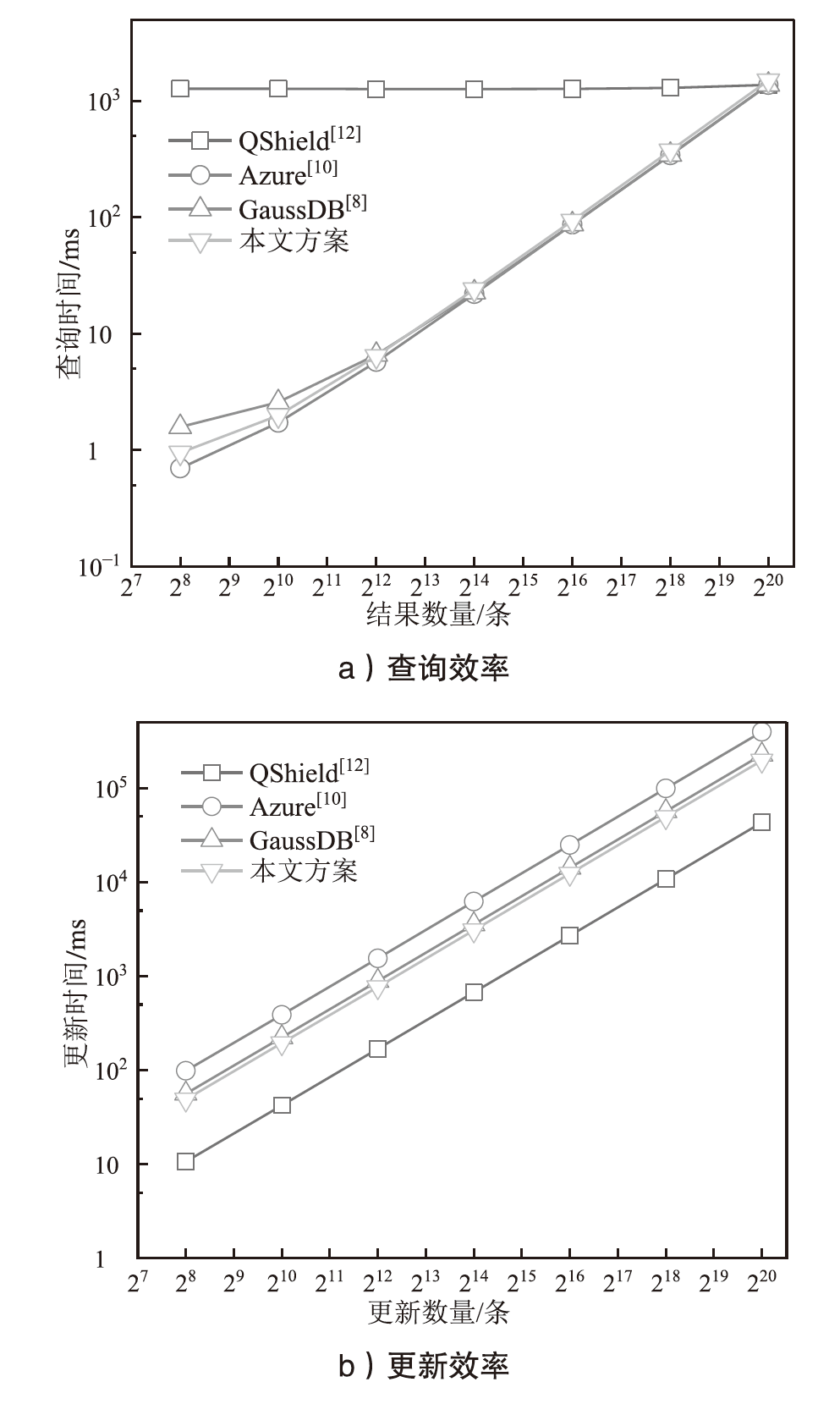
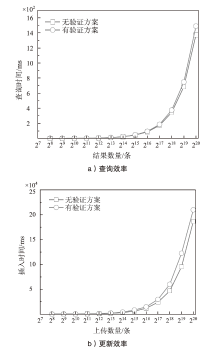
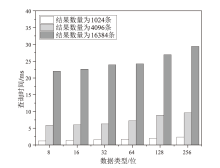
| [1] |
POPA R A, REDFIELD C M S, ZELDOVICH N, et al. CryptDB: Protecting Confidentiality with Encrypted Query Processing[C]// ACM. The Twenty-Third ACM Symposium on Operating Systems Principles. New York: ACM, 2011: 85-100.
|
| [2] |
CHI Jialin, FENG Dengguo, ZHANG Min, et al. Advances in Privacy-Preserving Ciphertext Retrieval[J]. Journal of Electronics & Information Technology, 2024, 46(5): 1546-1569.
|
|
迟佳琳, 冯登国, 张敏, 等. 隐私保护密文检索技术研究进展[J]. 电子与信息学报, 2024, 46(5): 1546-1569.
|
| [3] |
FANG Wenjing, CAO Shunde, HUA Guojin, et al. SecretFlow-SCQL: A Secure Collaborative Query Platform[J]. Proceedings of the VLDB Endowment, 2024, 17(12): 3987-4000.
doi: 10.14778/3685800.3685821
URL
|
| [4] |
SHARMA S, LI Yin, MEHROTRA S, et al. Prism: Privacy-Preserving and Verifiable Set Computation over Multi-Owner Secret Shared Outsourced Databases[J]. IEEE Transactions on Dependable and Secure Computing, 2024, 21(3): 1355-1371.
doi: 10.1109/TDSC.2023.3279356
URL
|
| [5] |
ZHANG Zhou, BIAN Song, ZHAO Zian, et al. ArcEDB: An Arbitrary-Precision Encrypted Database via (Amortized) Modular Homomorphic Encryption[C]// ACM. ACM SIGSAC Conference on Computer and Communications Security 2024. New York: ACM, 2024: 4613-4627.
|
| [6] |
MA Chengyan, LU Di, LYU Chaoyue, et al. BiTDB: Constructing a Built-In TEE Secure Database for Embedded Systems[J]. IEEE Transactions on Knowledge and Data Engineering, 2024, 36(9): 4472-4485.
doi: 10.1109/TKDE.2024.3380367
URL
|
| [7] |
PRIEBE C, VASWANI K, COSTA M. EnclaveDB: A Secure Database Using SGX[C]// IEEE. 2018 IEEE Symposium on Security and Privacy (S&P 2018). New York: IEEE, 2018: 264-278.
|
| [8] |
ZHU Jinwei, CHENG Kun, LIU Jiayang, et al. Full Encryption[J]. Proceedings of the VLDB Endowment, 2021, 14(12): 2811-2814.
doi: 10.14778/3476311.3476351
URL
|
| [9] |
WANG Sheng, LI Yiran, LI Huorong, et al. Operon: An Encrypted Database for Ownership-Preserving Data Management[J]. Proceedings of the VLDB Endowment, 2022, 15(12): 3332-3345.
doi: 10.14778/3554821.3554826
URL
|
| [10] |
ANTONOPOULOS P, ARASU A, SINGH K D, et al. Azure SQL Database Always Encrypted[C]// ACM. The 2020 ACM SIGMOD International Conference on Management of Data. New York: ACM, 2020: 1511-1525.
|
| [11] |
SEAH R, KHU D, HOOVER A, et al. LAMA: Leakage Abuse Attacks Against Microsoft Always Encrypted[EB/OL]. (2024-08-21)[2025-03-10]. https://eprint.iacr.org/2024/1308.
|
| [12] |
CHEN Yaxing, ZHENG Qinghua, YAN Zheng, et al. QShield: Protecting Outsourced Cloud Data Queries with Multi-User Access Control Based on SGX[J]. IEEE Transactions on Parallel and Distributed Systems, 2021, 32(2): 485-499.
doi: 10.1109/TPDS.71
URL
|
| [13] |
CHEN Yaxing, ZHENG Qinghua, YAN Zheng. Efficient Bi-Objective SQL Optimization for Enclaved Cloud Databases with Differentially Private Padding[J]. ACM Transactions on Database Systems, 2023, 48(2): 1-40.
|
| [14] |
ESKANDARIAN S, ZAHARIA M. ObliDB: Oblivious Query Processing for Secure Databases[C]// ACM. The 2019 International Conference on Very Large DataBases (VLDB). New York: ACM, 2019: 169-183.
|
| [15] |
ZHENG Wenting, DAVE A, BEEKMAN J G, et al. Opaque: An Oblivious and Encrypted Distributed Analytics Platform[C]// USENIX. The 2017 USENIX Symposium on Network System Design and Implementation (NSDI). Berkeley: USENIX, 2017: 283-298.
|
| [16] |
SONG D X, WAGNER D, PERRIG A. Practical Techniques for Searches on Encrypted Data[C]// IEEE. 2000 IEEE Symposium on Security and Privacy(S&P 2000). New York: IEEE, 2000: 44-55.
|
| [17] |
BOST R. ∑oϕoς: Forward Secure Searchable Encryption[C]// ACM. The 2016 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2016: 1143-1154.
|
| [18] |
SONG Xiangfu, DONG Changyu, YUAN Dandan, et al. Forward Private Searchable Symmetric Encryption with Optimized I/O Efficiency[J]. IEEE Transactions on Dependable and Secure Computing, 2020, 17(5): 912-927.
doi: 10.1109/TDSC.8858
URL
|
| [19] |
DEMERTZIS I, PAPADOPOULOS S, PAPAPETROU O, et al. Practical Private Range Search Revisited[C]// ACM. The 2016 International Conference on Management of Data. New York: ACM, 2016: 185-198.
|
| [20] |
KAMARA S, MOATAZ T. SQL on Structurally-Encrypted Databases[C]// Springer. The 24th International Conference on the Theory and Application of Cryptology and Information Security(Cryptology-ASIACRYPT 2018). Heidelberg: Springer, 2018: 149-180.
|
 )
)