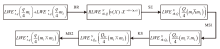
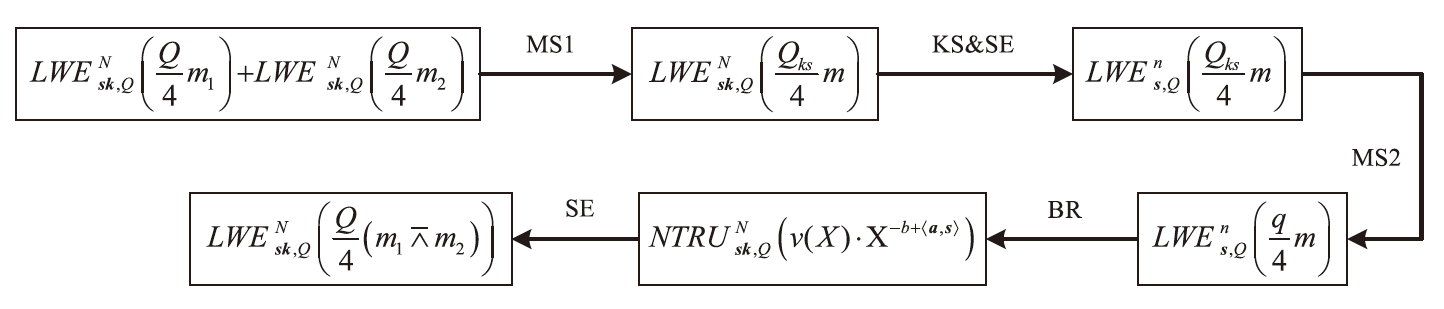
Netinfo Security ›› 2025, Vol. 25 ›› Issue (11): 1691-1706.doi: 10.3969/j.issn.1671-1122.2025.11.004
Previous Articles Next Articles
Research on Gate Bootstrapping in Fully Homomorphic Encryption
CHEN Chunling1,2, LU Xianhui1,2( ), WANG Ruida1,2, BAI Jikang1,2, XIE Shubing1,2
), WANG Ruida1,2, BAI Jikang1,2, XIE Shubing1,2
1. Institute of Information Engineering ,Chinese Academy of Sciences Beijing 100085, China 2. School of Cybersecurity ,University of Chinese Academy of Sciences Beijing 100049, China
-
Received:2025-07-25Online:2025-11-10Published:2025-12-02
CLC Number:
Cite this article
CHEN Chunling, LU Xianhui, WANG Ruida, BAI Jikang, XIE Shubing. Research on Gate Bootstrapping in Fully Homomorphic Encryption[J]. Netinfo Security, 2025, 25(11): 1691-1706.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.11.004
| 方法 | 底层 结构 | 方法类型 | 参数 | 密钥分布 | #NTT/FFT | BSK/bit |
|---|---|---|---|---|---|---|
| FHEW[ | RLWE | AP | STD128[ | 三元 | & 4nN{{d}_{r}}\text{(}{{B}_{r}}- \\ & 1\text{)}l{{\log }_{2}}Q \\ \end{align}$ | |
| TFHE[ | RLWE | GINX | STD128[ | 三元 | ||
| LMKC+[ | RLWE | Automorphism | LMKC128G[ | 高斯 | ||
| Final[ | NTRU | GINX | PT128T[ | 三元 | ||
| XZD+[ | NTRU | Automorphism GINX | P128G[ P128T[ | 高斯 三元 | ||
| LLW+[ | NTRU | GINX | STD128B[ | 二元 | ||
| CXL+[ | NTRU | Automorphism | C128B2Q25[ | 二元 |
| 方法 | 密钥分布 | 噪声公式 |
|---|---|---|
| AP[ | 二元 三元 | |
| GINX[ | 二元 三元 | |
| LMKC+[ | 高斯 | |
| FINAL[ | 三元 | |
| XZD+[ | 高斯 三元 | |
| LLW+[ | 二元 |
| 参数 | Key Distr. | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| CSTD128B | 128 | 二元 | 571 | 211 | 1024 | 225 | 214 | 27 | 2 | 214 | 1 | 2-40.7 |
| CSTD128B1 | 128 | 二元 | 532 | 211 | 1024 | 225 | 213 | 27 | 2 | 213 | 1 | 2-28.2 |
| CSTD128T | 128 | 二元 | 512 | 211 | 1024 | 227 | 214 | 29 | 2 | 214 | 1 | 2-63 |
| CSTD128G | 128 | 高斯 | 458 | 211 | 1024 | 228 | 213 | 29 | 2 | 213 | 1 | 2-52 |
| 方案 | 解密 失败率 | 平台 | 资源消耗 (ASIC:mm2/FPGA:LUT/FF/DSP) | 延迟 / | 吞吐率 /BS/s |
|---|---|---|---|---|---|
| FPT[ | 2-15 | FPGA | 595K / 1024K / 5980 | 6600 | 28400 |
| NFP[ | 2-31 | FPGA | 891K / 217K / 4508 | 920 | — |
| 2-15 | 891K / 217K / 4508 | 290 | |||
| Matcha[ | — | ASIC | 36.96 mm2 @??nm PTM | 200 | 10000 |
| Strix[ | — | ASIC | 141.37 mm2 @28nm TSMC | 440 | 21104 |
| Morphling[ | — | ASIC | 74.79 mm2 @28nm TSMC | 160 | 98933 |
| [1] | GENTRY C, HALEVI S, RAYKOVA M, et al. Outsourcing Private RAM Computation[C]// IEEE. 2014 IEEE 55th Annual Symposium on Foundations of Computer Science. New York: IEEE, 2014: 404-413. |
| [2] | GENTRY C, SAHAI A, WATERS B. Homomorphic Encryption from Learning with Errors:Conceptually-Simpler, Asymptotically-Faster, Attribute-Based[C]// Springer.Advances in Cryptology(CRYPTO 2013). Heidelberg: Springer, 2013: 75-92. |
| [3] | DOWLIN N, GILAD-BACHRACH R, LAINE K, et al. CryptoNets: Applying Neural Networks to Encrypted Data with High Throughput and Accuracy[C]// ICML. The 33rd International Conference on Machine Learning. New York: ICML, 2016: 201-210. |
| [4] | GENTRY C, HALEVI S, SMART, N P. Homomorphic Evaluation of the AES Circuit[C]// Springer.Advances in Cryptology(CRYPTO 2012). Heidelberg: Springer, 2012: 850-867. |
| [5] |
AMUTHAN A, SENDHIL R. Hybrid GSW and DM Based Fully Homomorphic Encryption Scheme for Handling False Data Injection Attacks under Privacy Preserving Data Aggregation in Fog Computing[J]. Journal of Ambient Intelligence and Humanized Computing, 2020, 11: 5217-5231.
doi: 10.1007/s12652-020-01849-8 |
| [6] |
CURTMOLA R, GARAY J, KAMARA S, et al. Searchable Symmetric Encryption: Improved Definitions and Efficient Constructions[J]. Journal of Computer Security, 2011, 19(5): 895-934.
doi: 10.3233/JCS-2011-0426 URL |
| [7] | CASH D, JARECKI S, JUTLA C, et al. Dynamic Searchable Encryption in Very-Large Databases: Data Structures and Implementation[C]// NDSS. Network and Distributed System Security Symposium (NDSS 2014). San Diego: NDSS, 2014: 463-478. |
| [8] | PAPPAS V, KRELL F, VO B, et al. Blind Seer: A Scalable Private DBMS[C]// IEEE.2014 IEEE Symposium on Security and Privacy. New York: IEEE, 2014: 359-374. |
| [9] | LUO Ming, LIU Fenghao, WANG Han. Faster FHE-Based Single-Server Private Information Retrieval[C]// ACM. Proceedings of the 2024 on ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2024: 1405-1419. |
| [10] | IEZZI M. Practical Privacy-Preserving Data Science with Homomorphic Encryption: An Overview[C]// IEEE. 2020 IEEE International Conference on Big Data. New York: IEEE, 2020: 3979-3988. |
| [11] | RIVEST R L, ADLEMAN L, DEAOUZOS M L. On Data Banks and Privacy Homomorphism[J]. Foundations of Secure Computation, 1978, 4(11): 169-180. |
| [12] |
MARCOLLA C, SUCASAS V, MANZANO M, et al. Survey on Fully Homomorphic Encryption, Theory, and Applications[J]. Proceedings of the IEEE, 2022, 110(10): 1572-1609.
doi: 10.1109/JPROC.2022.3205665 URL |
| [13] | BOURA C, GAMA N, GEORGIEVA M, et al. Simulating Homomorphic Evaluation of Deep Learning Predictions[C]// Springer.Cyber Security Cryptography and Machine Learning. Heidelberg: Springer, 2019: 212-230. |
| [14] |
LEE J W, KANG H, LEE Y, et al. Privacy-Preserving Machine Learning with Fully Homomorphic Encryption for Deep Neural Network[J]. IEEE Access, 2022, 10: 30039-30054.
doi: 10.1109/ACCESS.2022.3159694 URL |
| [15] | MATSUMOTO M, OGUCHI M. Speeding up Encryption on IoT Devices Using Homomorphic Encryption[C]// IEEE. 2021 IEEE International Conference on Smart Computing (SMARTCOMP). New York: IEEE, 2021: 270-275. |
| [16] | REGEV O. On Lattices, Learning with Errors, Random Linear Codes, and Cryptography[J]. Journal of the ACM, 2009, 56(6): 1-40. |
| [17] | LYUBASHEVSKY V, PEIKERT C, REGEV O. On Ideal Lattices and Learning with Errors over Rings[C]// Springer.Advances in Cryptology (EUROCRYPT 2010). Heidelberg: Springer, 2010: 1-23. |
| [18] | KIRCHNER P, FOUQUE P A. Revisiting Lattice Attacks on Overstretched NTRU Parameters[C]// Springer.Advances in Cryptology (EUROCRYPT 2017). Heidelberg: Springer, 2017: 3-26. |
| [19] | GENTRY C. A Fully Homomorphic Encryption Scheme[D]. California: Stanford University, 2009. |
| [20] | BRAKERSKI Z, GENTRY C, VAIKUNTANATHAN V. (Leveled) Fully Homomorphic Encryption without Bootstrapping[J]. ACM Transactions on Computation Theory, 2014, 6(3): 1-36. |
| [21] | BRAKERSKI Z, VAIKUNTANATHAN V. Fully Homomorphic Encryption from Ring-LWE and Security for Key Dependent Messages[C]// Springer.Advances in Cryptology(CRYPTO 2011). Heidelberg: Springer, 2011: 505-524. |
| [22] | FAN J, VERCAUTEREN F. Somewhat Practical Fully Homomorphic Encryption[EB/OL]. (2012-06-26)[2025-11-13]. https://eprint.iacr.org/2012/144. |
| [23] | CHEON J H, KIM A, KIM M, et al. Homomorphic Encryption for Arithmetic of Approximate Numbers[C]// Springer.Advances in Cryptology (ASIACRYPT 2017). Heidelberg: Springer, 2017: 409-437. |
| [24] | CHEON J H, HAN K, KIM A, et al. Bootstrapping for Approximate Homomorphic Encryption[C]// Springer.Advances in Cryptology (EUROCRYPT 2018). Heidelberg: Springer, 2018: 360-384. |
| [25] | DUCAS L, MICCIANCIO D. FHEW: Bootstrapping Homomorphic Encryption in Less than a Second[C]// Springer.Advances in Cryptology (EUROCRYPT 2015). Heidelberg: Springer, 2015: 617-640. |
| [26] | CHILLOTTI I, GAMA N, GEORGIEVA M, et al. Faster Fully Homomorphic Encryption: Bootstrapping in Less than 0.1 Seconds[C]// Springer.Advances in Cryptology (ASIACRYPT 2016). Heidelberg: Springer, 2016: 3-33. |
| [27] | CHILLOTTI I, GAMA N, GEORGIEVA M, et al. Faster Packed Homomorphic Operations and Efficient Circuit Bootstrapping for TFHE[C]// Springer.Advances in Cryptology (ASIACRYPT 2017). Heidelberg: Springer, 2017: 377-408. |
| [28] |
CHILLOTTI I, GAMA N, GEORGIEVA M, et al. TFHE: Fast Fully Homomorphic Encryption over the Torus[J]. Journal of Cryptology, 2020, 33(1): 34-91.
doi: 10.1007/s00145-019-09319-x |
| [29] | MICCIANCIO D, POLYAKOV Y. Bootstrapping in FHEW-Like Cryptosystems[C]// ACM. The 9th on Workshop on Encrypted Computing & Applied Homomorphic Cryptography. New York: ACM, 2021: 17-28. |
| [30] | LEE Y, MICCIANCIO D, KIM A, et al. Efficient FHEW Bootstrapping with Small Evaluation Keys, and Applications to Threshold Homomorphic Encryption[C]// Springer.Advances in Cryptology (EUROCRYPT 2023). Heidelberg: Springer, 2023: 227-256. |
| [31] | XIANG Binwu, ZHANG Jiang, DENG Yi, et al. Fast Blind Rotation for Bootstrapping FHEs[C]// Springer.Advances in Cryptology(CRYPTO 2023). Heidelberg: Springer, 2023: 3-36. |
| [32] | LI Zhihao, LU Xianhui, WANG Zhiwei, et al. Faster NTRU-Based Bootstrapping in less than 4 ms[J]. IACR Transactions on Cryptographic Hardware and Embedded Systems, 2024(3): 418-451. |
| [33] | LI Zhihao, LIU Ying, LU Xianhui, et al. Faster Bootstrapping via Modulus Raising and Composite NTT[J]. IACR Transactions on Cryptographic Hardware and Embedded Systems, 2024(1): 563-591. |
| [34] | CHEN Chunling, LU Xianhui, XIANG Binwu, et al. Refined Error Management for Gate Bootstrapping[C]// Springer.Information Security and Privacy. Heidelberg: Springer, 2025: 252-274. |
| [35] | ALPERIN-SHERIFF J, PEIKERT C. Faster Bootstrapping with Polynomial Error[C]// Springer.Advances in Cryptology (CRYPTO 2014). Heidelberg: Springer, 2014: 297-314. |
| [36] | KIM A, LEE Y, DERYABIN M, et al. LFHE: Fully Homomorphic Encryption with Bootstrapping Key Size Less than a Megabyte[EB/OL]. (2023-05-26)[2025-11-12]. https://eprint.iacr.org/2023/767. |
| [37] | GAMA N, IZABACHÈNE M, NGUYEN P Q, et al. Structural Lattice Reduction: Generalized Worst-Case to Average-Case Reductions and Homomorphic Cryptosystems[C]// Springer.Advances in Cryptology (EUROCRYPT 2016). Heidelberg: Springer, 2016: 528-558. |
| [38] | BONTE C, ILIASHENKO I, PARK J, et al. FINAL: Faster FHE Instantiated with NTRU and LWE[C]// Springer.Advances in Cryptology (ASIACRYPT 2022). Heidelberg: Springer, 2022: 188-215. |
| [39] | PEREIRA H V L. Bootstrapping Fully Homomorphic Encryption over the Integers in Less than One Second[C]// Springer.Public-Key Cryptography(PKC 2021). Heidelberg: Springer, 2021: 331-359. |
| [40] | BONTE C, ILIASHENKO I, PARK J, et al. FINAL: Faster FHE Instantiated with NTRU and LWE[C]// Springer.Advances in Cryptology (ASIACRYPT 2022). Heidelberg: Springer, 2022: 188-215. |
| [41] | GENTRY C, HALEVI S, SMART N P. Homomorphic Evaluation of the AES Circuit[C]// Springer.Advances in Cryptology(CRYPTO 2012). Heidelberg: Springer, 2012: 850-867. |
| [42] |
ALBRECHT M R, PLAYER R, SCOTT S. On the Concrete Hardness of Learning with Errors[J]. Journal of Mathematical Cryptology, 2015, 9(3): 169-203.
doi: 10.1515/jmc-2015-0016 URL |
| [43] | ALKIM E, DUCAS L, POPPELMANN T, et al. Post-Quantum Key Exchange: A New Hope[C]// USENIX. The 25th USENIX Conference on Security Symposium. Berkeley: USENIX, 2016: 327-343. |
| [44] | DUCAS L, VAN WOERDEN W. NTRU Fatigue: How Stretched is Overstretched[C]// Springer.Advances in Cryptology (ASIACRYPT 2021). Heidelberg: Springer, 2021: 3-32. |
| [45] | XIANG Binwu, ZHANG Jiang, WANG Kaixing, et al. NTRU-Based Bootstrapping for MK-FHEs without Using Overstretched Parameters[C]// Springer.Advances in Cryptology (ASIACRYPT 2024). Heidelberg: 2024: 241-270. |
| [46] |
ALBRECHT M R, PLAYER R, SCOTT S. On the Concrete Hardness of Learning with Errors[J]. Journal of Mathematical Cryptology, 2015, 9(3): 169-203.
doi: 10.1515/jmc-2015-0016 URL |
| [47] | MATSUOKA K, BANNO R, MATSUMOTO, et al. Virtual Secure Platform: A Five-Stage Pipeline Processor over TFHE[C]// USENIX.USENIX Security Symposium. Berkeley: USENIX,2021: 4007-4024. |
| [48] | ZAMA. TFHE-rs: A Pure Rust Implementation of the TFHE Scheme for Boolean and Integer Arithmetics over Encrypted Data[EB/OL]. [2025-06-23]. https://github.com/zama-ai/tfhe-rs. |
| [49] | VANBEIREN DONCK M, D’ANVERS J P, TURAN F, et al. FPT: A Fixed-Point Accelerator for Torus Fully Homomorphic Encryption[C]// ACM. The 2023 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2023: 741-745. |
| [50] | JIANG Lei, LOU Qian, JOSHI N. MATCHA: A Fast and Energy-Efficient Accelerator for Fully Homomorphic Encryption over the Torus[C]// ACM. The 59th ACM/IEEE Design Automation Conference. New York: ACM, 2022: 235-240. |
| [51] | PUTRA A, PRASETIYO, CHEN Yi, et al. Strix: An End-to-End Streaming Architecture with Two-Level Ciphertext Batching for Fully Homomorphic Encryption with Programmable Bootstrapping[C]// ACM. The 56th Annual IEEE/ACM International Symposium on Microarchitecture. New York: ACM, 2023: 1319-1331. |
| [52] | PRASETIYO, PUTRA A, KIM J Y. Morphling: A Throughput-Maximized TFHE-Based Accelerator Using Transform-Domain Reuse[C]// IEEE. 2024 IEEE International Symposium on High-Performance Computer Architecture (HPCA). New York: IEEE, 2024: 249-262. |
| [1] | ZHU Hui, FANG Yunyi, WANG Fengwei, XU Wei. Research Progress on Data Security Processing Integrating Confidential Computing [J]. Netinfo Security, 2025, 25(11): 1643-1657. |
| [2] | HAO Meng, LI Jiayong, YANG Hongwei, ZHANG Weizhe. Heterogeneous CPU-GPU System Confidential Computing Survey [J]. Netinfo Security, 2025, 25(11): 1658-1672. |
| [3] | GUAN Zhi, HU Jianbin, LI Yue, CHEN Zhong. A Comprehensive Survey of Blockchain Technologies and Applications Based on Trusted Execution Environments [J]. Netinfo Security, 2025, 25(11): 1673-1690. |
| [4] | REN Fengyuan, ZHANG Xinyue, LEI Zhuoyi, LIU Xin. Research on Key-Value Data Storage and Operation Optimization Method Based on Confidential Computing [J]. Netinfo Security, 2025, 25(11): 1707-1717. |
| [5] | XUE Kaiping, ZHANG Chunyi, LIU Feng, WANG Feng. Security-Enhanced Index Scheme in Encrypted Database Based on Trusted Execution Environment [J]. Netinfo Security, 2025, 25(11): 1718-1731. |
| [6] | SHEN Haoting, PENG Zhigang, LIU Yuxuan, WANG Yafei. Hardware Authentication Mechanism for Consortium Blockchain Based on Differentiated Physical Unclonable Function Models [J]. Netinfo Security, 2025, 25(11): 1732-1744. |
| [7] | ZHAO Bo, LYU Jiamin, WANG Yixuan. A Multidimensional Security Measurement Architecture for the Container Lifecycle [J]. Netinfo Security, 2025, 25(11): 1745-1761. |
| [8] | WANG Yajie, LU Jinbiao, LI Yuhang, FAN Qing, ZHANG Zijian, ZHU Liehuang. Hierarchical Dynamic Protection Algorithm for Federated Learning Based on Trusted Execution Environment [J]. Netinfo Security, 2025, 25(11): 1762-1773. |
| [9] | LU Di, LIU Yujia, LYU Chaoyue, SUN Mengna, ZHANG Qingwen, YANG Li. Cloud-Native TEE Service Sharing Mechanism for Secure Edge Computing [J]. Netinfo Security, 2025, 25(11): 1774-1791. |
| [10] | JIN Wa, QIN Yu, LIU Jingrun, SHANG Ketong, JIA Menghan, LIN Jiangnan. A Hardware Trusted Channel Construction Scheme Based on TEE and TPM for Confidential Computing Platforms [J]. Netinfo Security, 2025, 25(11): 1792-1810. |
| [11] | HU Yuyi, CAI Wei, CHEN Jingfan, LIU Mohan, WANG Juan, HE Yun. Research on Unified Remote Attestation Mechanism for Confidential Containers Devices [J]. Netinfo Security, 2025, 25(11): 1811-1823. |
| [12] | HU Bin, HEI Yiming, WU Tiejun, ZHENG Kaifa, LIU Wenzhong. A Review of Safety Detection and Evaluation Technologies for Large Models [J]. Netinfo Security, 2025, 25(10): 1477-1492. |
| [13] | ZHANG Dalong, DING Shuguang, HAN Zhilong, FU Shouli, TANG Zhiqing, SHI Lei. Review of Cyber Resilience Assessment Framework and Methods [J]. Netinfo Security, 2025, 25(10): 1493-1505. |
| [14] | LAN Jiachen, CHEN Xiarun, ZHOU Yangkai, WEN Weiping. A Survey of Routing Technologies and Protocols in Polymorphic Networks [J]. Netinfo Security, 2025, 25(10): 1506-1522. |
| [15] | YU Fajiang, WANG Chaozhou. Implementation Mechanism for TrustZone Paravirtualization and Containerization [J]. Netinfo Security, 2025, 25(10): 1523-1536. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||