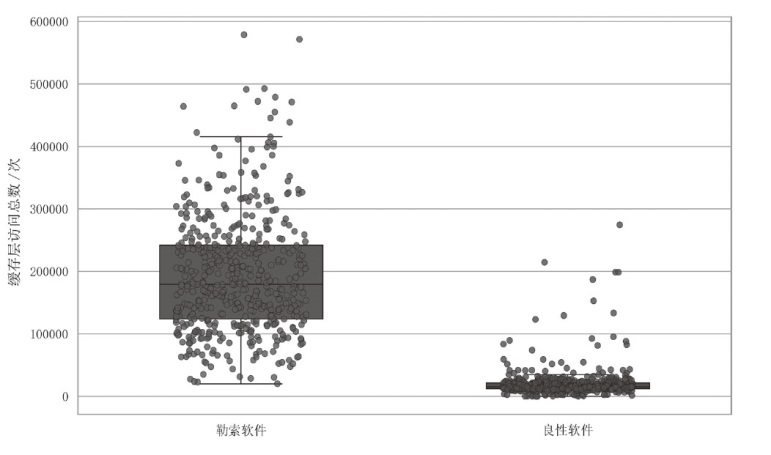
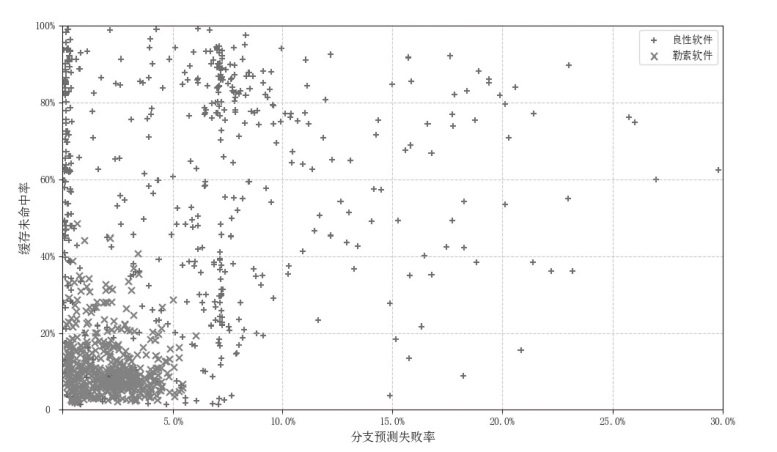
| [1] |
360 Digital Security Group. 2024 Ransomware Trends Report[EB/OL]. (2025-01-09)[2025-05-20]. https://360.cn/n/12648.html.
|
| [2] |
Cybersecurity Ventures. 2024 Cybersecurity Almanac: 100 Facts, Figures, Predictions And Statistics[EB/OL]. (2024-06-24)[2025-05-20]. https://cybersecurityventures.com/cybersecurity-almanac-2024/.
|
| [3] |
KHARAZ A, ARSHAD S, MULLINER C, et al. UNVEIL:A Large-Scale, Automated Approach to Detecting Ransomware[C]// USENIX. 25th USENIX Security Symposium (USENIX Security 16). Berkeley: USENIX Association, 2016: 757-772.
|
| [4] |
SCAIFE N, CARTER H, TRAYNOR P, et al. Cryptolock (and Drop It): Stopping Ransomware Attacks on User Data[C]// IEEE. 2016 IEEE 36th International Conference on Distributed Computing Systems (ICDCS). New York: IEEE, 2016: 303-312.
|
| [5] |
CHEN ZhiGuo, KANG H S, YIN Shangnan, et al. Automatic Ransomware Detection and Analysis Based on Dynamic API Calls Flow Graph[C]// ACM. The International Conference on Research in Adaptive and Convergent Systems. New York: ACM, 2017: 196-201.
|
| [6] |
LEE J, JEONG K, LEE H. Detecting Metamorphic Malwares Using Code Graphs[C]// ACM. The 2010 ACM Symposium on Applied Computing. New York: ACM, 2010: 1970-1977.
|
| [7] |
KOK S H, ABDULLAH A, JHANJHI N Z, et al. Prevention of Crypto-Ransomware Using a Pre-Encryption Detection Algorithm[J]. Computers, 2019, 8(4): 79-94.
|
| [8] |
ALHAWI O M K, BALDWIN J, DEHGHANTANHA A. Leveraging Machine Learning Techniques for Windows Ransomware Network Traffic Detection[J]. Cyber Threat Intelligence, 2018: 93-106.
|
| [9] |
ZHOU Boyou, GUPTA A, JAHANSHAHI R, et al. Hardware Performance Counters can Detect Malware: Myth or Fact?[C]// ACM. The 2018 on Asia Conference on Computer and Communications Security. New York: ACM, 2018: 457-468.
|
| [10] |
ZHOU Hongwei, WU Xin, SHI Wenchang, et al. HDROP: Detecting ROP Attacks Using Performance Monitoring Counters[C]// Springer. International Conference on Information Security Practice and Experience. Heidelberg: Springer, 2014: 172-186.
|
| [11] |
HERATH N, FOGH A. CPU Hardware Performance Counters for Security[EB/OL]. (2015-08-01)[2025-08-20]. https://www.blackhat.com/us-15/briefings.html.
|
| [12] |
CARVALHO DE MELO A. The New Linux Perf Tools[J]. Slides from Linux Kongress. 2010, 18(1): 1-42.
|
| [13] |
ALAM M, BHATTACHARYA S, DUTTA S, et al. RATAFIA: Ransomware Analysis Using Time and Frequency Informed Autoencoders[C]// IEEE. 2019 IEEE International Symposium on Hardware Oriented Security and Trust (HOST). New York: IEEE, 2019: 218-227.
|
| [14] |
WANG Xueyang, CHAI S, ISNARDI M, et al. Hardware Performance Counter-Based Malware Identification and Detection with Adaptive Compressive Sensing[J]. ACM Transactions on Architecture and Code Optimization (TACO), 2016, 13(1): 1-23.
|
| [15] |
DEMME J, MAYCOCK M, SCHMITZ J, et al. On the Feasibility of Online Malware Detection with Performance Counters[J]. ACM SIGARCH Computer Architecture News, 2013, 41(3): 559-570.
|
| [16] |
KAZDAGLI M, REDDI V J, TIWARI M. Quantifying and Improving the Efficiency of Hardware-Based Mobile Malware Detectors[C]// IEEE. 2016 49th Annual IEEE/ACM International Symposium on Microarchitecture (MICRO). New York: IEEE, 2016: 1-13.
|
| [17] |
KRISHNAMURTHY P, RAMESH K, FAARSHAD K. Anomaly Detection in Real-Time Multi-Threaded Processes Using Hardware Performance Counters[J]. IEEE Transactions on Information Forensics and Security, 2020, 15: 666-680.
|
| [18] |
HE Zhangying, HOUMAN H, HOSSEIN S. Beyond Conventional Defenses: Proactive and Adversarial-Resilient Hardware Malware Detection Using Deep Reinforcement Learning[C]// ACM. The 61st ACM/IEEE Design Automation Conference. New York: ACM, 2024: 1-6.
|
| [19] |
LI Congmiao, GAUDIOT J L. Detecting Spectre Attacks Using Hardware Performance Counters[J]. IEEE Transactions on Computers, 2022, 71(6): 1320-1331.
|
| [20] |
GANFURE G O, WU Chunfeng, CHANG Yuanhao, et al. Deepware: Imaging Performance Counters with Deep Learning to Detect Ransomware[J]. IEEE Transactions on Computers, 2022, 72(3): 600-613.
|
| [21] |
HOCHREITER S, SCHMIDHUBER J. Long Short-Term Memory[J]. Neural Computation, 1997, 9(8): 1735-1780.
doi: 10.1162/neco.1997.9.8.1735
pmid: 9377276
|
| [22] |
GRAVES A. Supervised Sequence Labelling with Recurrent Neural Networks[M]. Heidelberg: Springer, 2012.
|
| [23] |
VASWANI A, SHAZEER N, PARMAR N, et al. Attention is all you need[C]// Curran Associates Inc. Proceedings of the 31st International Conference on Neural Information Processing Systems. New York: Curran Associates Inc, 2017: 6000-6010.
|
| [24] |
AURANGZEB S, RAIS R N B, ALEEM M, et al. On the Classification of Microsoft-Windows Ransomware Using Hardware Profile[EB/OL]. (2021-02-02) [2025-08-20]. https://peerj.com/articles/cs-361/#intro.
|
 )
)