信息网络安全 ›› 2025, Vol. 25 ›› Issue (9): 1385-1396.doi: 10.3969/j.issn.1671-1122.2025.09.007
基于污点分析与文本语义的固件程序交互关系智能逆向分析方法
- 国防科技大学电子科学学院,长沙 410003
-
收稿日期:2025-05-29出版日期:2025-09-10发布日期:2025-09-18 -
通讯作者:王剑jwang@nudt.edu.cn -
作者简介:王磊(1996—),男,河南,硕士研究生,主要研究方向为二进制程序逆向工程|陈炯峄(1993—),男,湖南,讲师,博士,CCF会员,主要研究方向为网络与系统安全|王剑(1975—),男,湖南,教授,博士,主要研究方向为网络空间对抗、漏洞分析与检测、无线网络安全|冯袁(2002—),男,湖北,博士研究生,主要研究方向为二进制程序逆向工程 -
基金资助:国家自然科学基金(62302508)
Intelligent Reverse Analysis Method of Firmware Program Interaction Relationships Based on Taint Analysis and Textual Semantics
WANG Lei, CHEN Jiongyi, WANG Jian( ), FENG Yuan
), FENG Yuan
- College of Electronic Science and Technology, National University of Defense Technology, Changsha 410003, China
-
Received:2025-05-29Online:2025-09-10Published:2025-09-18
摘要:
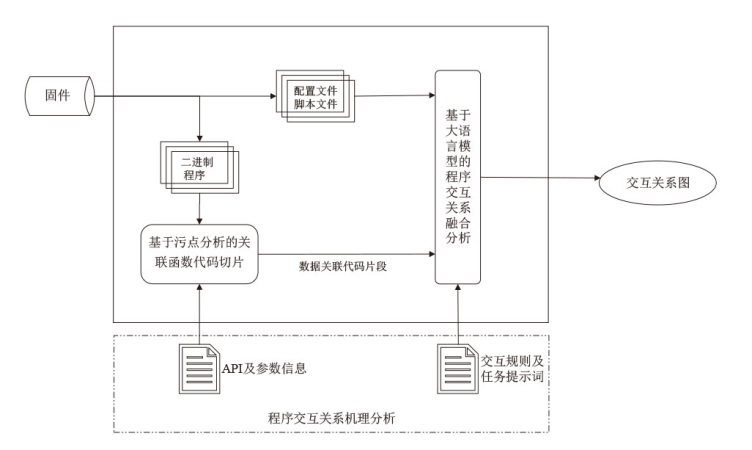
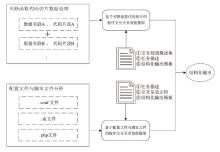
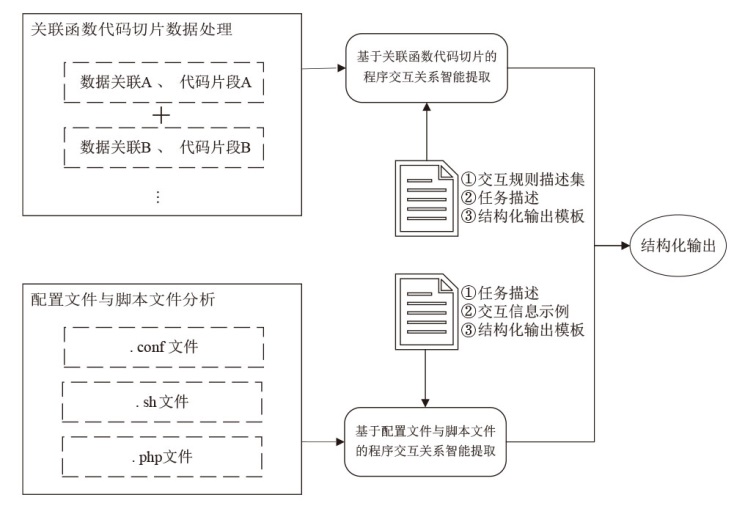
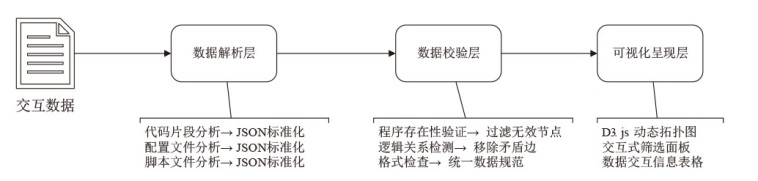
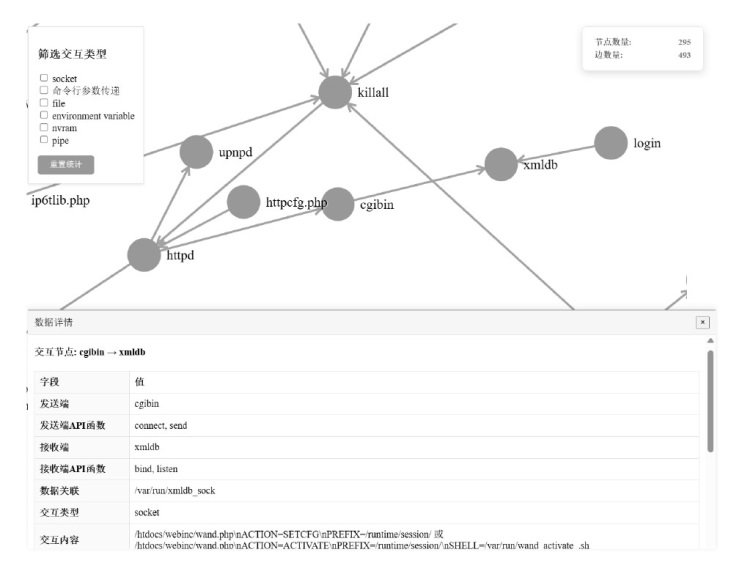
针对嵌入式设备固件程序间交互关系逆向分析自动化程度低、准确率不高、分析效率低等问题,文章提出一种基于污点分析与文本语义的固件程序交互关系智能逆向分析方法。该方法构建了基于污点分析的关联函数代码切片算法,结合大语言模型的语义理解能力,实现了二进制程序中交互信息的精准提取和关联代码片段的智能定位,此外,还设计了面向脚本文件和配置文件的专用交互信息提取方法,有效提升了方法处理非结构化文本数据的能力。实验结果表明,程序间交互关系逆向分析方法的检测准确率达93.2%,研究成果可为理解程序功能、实现通信控制、发现潜在漏洞等应用提供有效支撑。
中图分类号:
引用本文
王磊, 陈炯峄, 王剑, 冯袁. 基于污点分析与文本语义的固件程序交互关系智能逆向分析方法[J]. 信息网络安全, 2025, 25(9): 1385-1396.
WANG Lei, CHEN Jiongyi, WANG Jian, FENG Yuan. Intelligent Reverse Analysis Method of Firmware Program Interaction Relationships Based on Taint Analysis and Textual Semantics[J]. Netinfo Security, 2025, 25(9): 1385-1396.
表1
各交互类型的关键API函数
| 交互类型 | 关键API函数 | 其他关联API函数 | 数据关联 |
|---|---|---|---|
| 套接字 | bind、connect | sendto、send、sendmsg、 recvfrom、recv、recvmsg | IP地址和端口,或文件路径 |
| 共享内存 | shmat、shm_open | shmget、mmap | 共享内存段标识、文件路径 |
| 文件读写 | open、fopen | read、fread、fgets、 write、fwrite、fprintf | 文件路径 |
| 环境变量获取与设置 | getenv、setenv、putenv | — | 环境变量名 |
| NVRAM | nvram_get、acosNvramConfig_get、nvram_set、acosNvramConfig_set | — | NVRAM存储键 |
| 命名管道 | mkfifo | open、fopen、read、 write、fread、fwrite | 文件路径 |
| 命令行参数 传递 | — | — | 命令行参数 |
| [1] | IOT Business News. 5 Game-Changing IoT Trends to Watch in 2025[EB/OL]. (2025-03-12)[2025-05-06]. https://iotbusinessnews.com/2025/03/12/16089-5-game-changing-iot-trends-to-watch-in-2025/. |
| [2] | 360 Digital Security Group·Vulnerability Intelligence Service. (2025). 2024 Annual Cybersecurity Vulnerability Analysis Report[EB/OL]. (2025-02-10)[2025-05-06]. https://cdn.isc.360.com/isc-cxo/2024_Vulnerability_Report.pdf. |
| 360数字安全集团·漏洞情报服务. (2025). 2024年度网络安全漏洞分报告[EB/OL]. (2025-02-10)[2025-05-06]. https://cdn.isc.360.com/isc-cxo/2024_Vulnerability_Report.pdf. | |
| [3] | JIAO Yongsheng, SHU Hui. Reversing of Interprocess Communication Based on TEMU[J]. Application Research of Computers, 2013, 30(7): 5-10. |
| 焦永生, 舒辉. 基于TEMU的进程间通信过程逆向[J]. 计算机应用研究, 2013, 30(7): 5-10. | |
| [4] | HENDERSON A, YAN L K, HU X, et al. DECAF: A Platform-Neutral Whole-System Dynamic Binary Analysis Platform[J]. IEEE Transactions on Software Engineering, 2017, 43(2): 164-184. |
| [5] | LIWY7Z. Taint Aalysis Technology[EB/OL]. (2022-03-03)[2025-05-06]. https://blog.csdn.net/weixin_44442186/article/details/123263226. |
| LIWY7Z. 污点分析技术[EB/OL]. (2022-03-03)[2025-05-06]. https://blog.csdn.net/weixin_44442186/article/details/123263226. | |
| [6] | REDINI N, MACHIRY A, WANG R, et al. Karonte: Detecting Insecure Multi-Binary Interactions in Embedded Firmware[C]// IEEE. 2020 IEEE Symposium on Security and Privacy. New York: IEEE, 2020: 1544-1561. |
| [7] | WU Yuhao, WANG Jinwen, WANG Yujie, et al. Your Firmware Has Arrived: A Study of Firmware Update Vulnerabilities[C]// USENIX. 33rd USENIX Security Symposium. Berkeley: USENIX, 2024: 5627-5644. |
| [8] | LI Wen, JIANG Ming, LUO Xiapu, et al. POLYCRUISE: A Cross-Language Dynamic Information Flow Analysis[C]// USENIX. 31st USENIX Security Symposium. Berkeley: USENIX, 2022: 2513-2530. |
| [9] | CHEN Libo, WANG Yanhao, LINGHU Jiaqi, et al. SaTC: Shared-Keyword Aware Taint Checking for Detecting Bugs in Embedded Systems[J]. IEEE Transactions on Dependable and Secure Computing, 2024, 21(4): 2421-2433. |
| [10] | CHEN Libo, WANG Yanhao, CAI Quanpu, et al. Sharing More and Checking Less: Leveraging Common Input Keywords to Detect Bugs in Embedded Systems[C]// USENIX. 30th USENIX Security Symposium. Berkeley: USENIX, 2021: 303-319. |
| [11] | ALHANAHNAH M, STEVENS C, CHEN B, et al. IoTCom: Dissecting Interaction Threats in IoT Systems[J]. IEEE Transactions on Software Engineering, 2023, 49(4): 1523-1539. |
| [12] | WANG Rui, WANG Xiaofeng, ZHANG Kehuan, et al. Towards Automatic Reverse Engineering of Software Security Configurations[C]// ACM. The 15th ACM Conference on Computer and Communications Security. New York: ACM, 2008: 245-256. |
| [13] | XIAO Yuting, CHEN Jiongyi, HU Yupeng, et al. FIRMRES: Exposing Broken Device-Cloud Access Control in IoT through Static Firmware Analysis[C]// IEEE. The 2024 54th Annual IEEE/IFIP International Conference on Dependable Systems and Networks. New York: IEEE, 2024: 495-506. |
| [14] | LI Xixing, WEI Qiang, WU Zehui, et al. Finding Taint-Style Vulnerabilities in Lua Application of IoT Firmware with Progressive Static Analysis[EB/OL]. (2023-08-28) [2025-05-06]. https://www.mdpi.com/2076-3417/13/17/9710. |
| [15] | LIU Puzhuo, SUN Chengnian, ZHENG Yaowen, et al. LLM-Powered Static Binary Taint Analysis[J]. ACM Transactions on Software Engineering and Methodology, 2025, 34(3): 1-36. |
| [16] | LIU Hangtian, ZHENG Lei, GAN Shuitao, et al. EAGLEYE: Exposing Hidden Web Interfaces in IoT Devices via Routing Analysis[EB/OL]. (2025-02-24)[2025-05-06]. https://dx.doi.org/10.14722/ndss.2025.240399. |
| [17] | CHEN Yi, YAO Yepeng, WANG Xiaofeng, et al. Bookworm Game: Automatic Discovery of LTE Vulnerabilities through Documentation Analysis[C]// IEEE. The 2021 IEEE Symposium on Security and Privacy. New York: IEEE, 2021: 1770-1787. |
| [18] | TIAN Junfeng, XING Wenjing, LI Zhen. BVDetector: A Program Slice-Based Binary Code Vulnerability Intelligent Detection System[EB/OL]. (2020-02-20)[2025-05-06]. https://www.sciencedirect.com/science/article/pii/S0950584920300392. |
| [19] | LEMOS R, HEINRICH T, MAZIERO C A, et al. Is It Safe? Identifying Malicious Apps through the Use of Metadata and Inter-Process Communication[C]// IEEE. The 2022 IEEE International Systems Conference SysCon. New York: IEEE, 2022: 1-8. |
| [20] | LI Meijian, WANG Yongjun, XIE Peidai, et al. Reverse Analysis of Secure Communication Protocol Based on Taint Analysis[EB/OL]. (2014-05-22)[2025-05-06]. https://ieeexplore.ieee.org/document/6992222. |
| [21] | JI Yang, LEE S, DOWING E, et al. RAIN: Refinable Attack Investigation with On-demand Inter-Process Information Flow Tracking[C]// ACM. The 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 311-326. |
| [22] | COLE E. Static Taint Analysis of Binary Executables Using Architecture-Neutral Intermediate Representation[R]. St. Louis: Washington University in St. Louis, WUCSE-2019-1177, 2019. |
| [23] | LIU N F, LIN K, HEWITT J, et al. Lost in the Middle: How Language Models Use Long Contexts[J]. Transactions of the Association for Computational Linguistics, 2024, 12: 157-173. |
| [1] | 胡雨翠, 高浩天, 张杰, 于航, 杨斌, 范雪俭. 车联网安全自动化漏洞利用方法研究[J]. 信息网络安全, 2025, 25(9): 1348-1356. |
| [2] | 刘会, 朱正道, 王淞鹤, 武永成, 黄林荃. 基于深度语义挖掘的大语言模型越狱检测方法研究[J]. 信息网络安全, 2025, 25(9): 1377-1384. |
| [3] | 张燕怡, 阮树骅, 郑涛. REST API设计安全性检测研究[J]. 信息网络安全, 2025, 25(8): 1313-1325. |
| [4] | 陈平, 骆明宇. 云边端内核竞态漏洞大模型分析方法研究[J]. 信息网络安全, 2025, 25(7): 1007-1020. |
| [5] | 酆薇, 肖文名, 田征, 梁中军, 姜滨. 基于大语言模型的气象数据语义智能识别算法研究[J]. 信息网络安全, 2025, 25(7): 1163-1171. |
| [6] | 张学旺, 卢荟, 谢昊飞. 基于节点中心性和大模型的漏洞检测数据增强方法[J]. 信息网络安全, 2025, 25(4): 550-563. |
| [7] | 顾欢欢, 李千目, 刘臻, 王方圆, 姜宇. 基于虚假演示的隐藏后门提示攻击方法研究[J]. 信息网络安全, 2025, 25(4): 619-629. |
| [8] | 解梦飞, 傅建明, 姚人懿. 基于LLM的多媒体原生库模糊测试研究[J]. 信息网络安全, 2025, 25(3): 403-414. |
| [9] | 秦中元, 王田田, 刘伟强, 张群芳. 大语言模型水印技术研究进展[J]. 信息网络安全, 2025, 25(2): 177-193. |
| [10] | 王鹃, 张勃显, 张志杰, 谢海宁, 付金涛, 王洋. 基于模糊测试的Java反序列化漏洞挖掘[J]. 信息网络安全, 2025, 25(1): 1-12. |
| [11] | 焦诗琴, 张贵杨, 李国旗. 一种聚焦于提示的大语言模型隐私评估和混淆方法[J]. 信息网络安全, 2024, 24(9): 1396-1408. |
| [12] | 陈昊然, 刘宇, 陈平. 基于大语言模型的内生安全异构体生成方法[J]. 信息网络安全, 2024, 24(8): 1231-1240. |
| [13] | 项慧, 薛鋆豪, 郝玲昕. 基于语言特征集成学习的大语言模型生成文本检测[J]. 信息网络安全, 2024, 24(7): 1098-1109. |
| [14] | 郭祥鑫, 林璟锵, 贾世杰, 李光正. 针对大语言模型生成的密码应用代码安全性分析[J]. 信息网络安全, 2024, 24(6): 917-925. |
| [15] | 张长琳, 仝鑫, 佟晖, 杨莹. 面向网络安全领域的大语言模型技术综述[J]. 信息网络安全, 2024, 24(5): 778-793. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||