信息网络安全 ›› 2025, Vol. 25 ›› Issue (7): 1111-1125.doi: 10.3969/j.issn.1671-1122.2025.07.010
新型可组合的认证分布式数据结构模型研究
- 东北大学软件学院,沈阳 110169
-
收稿日期:2025-05-20出版日期:2025-07-10发布日期:2025-08-07 -
通讯作者:徐剑 E-mail:xuj@mail.neu.edu.cn -
作者简介:高扬(1980—),男,辽宁,实验师,博士,主要研究方向为网络与信息安全、人工智能与机器学习|张琪(1997—),男,辽宁,硕士研究生,主要研究方向为隐私计算|王琛(1996—),女,辽宁,博士研究生,主要研究方向为隐私计算|徐剑(1978—),男,辽宁,教授,博士,主要研究方向为网络与信息安全、隐私计算 -
基金资助:国家自然科学基金(62372096)
Research on New Composable Authenticated Distributed Data Structure Model
GAO Yang, ZHANG Qi, WANG Chen, XU Jian( )
)
- Software College of Northeastern University, Shenyang 110169, China
-
Received:2025-05-20Online:2025-07-10Published:2025-08-07 -
Contact:XU Jian E-mail:xuj@mail.neu.edu.cn
摘要:
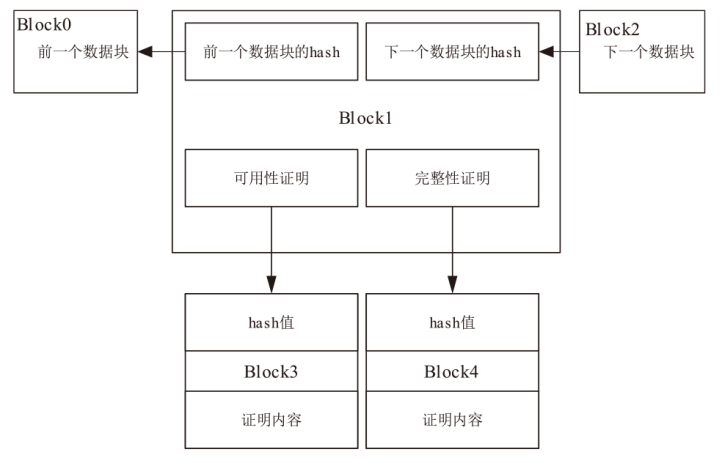
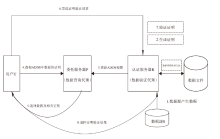
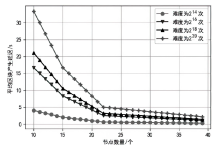
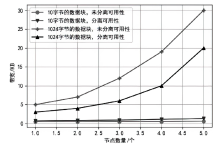
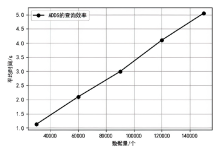
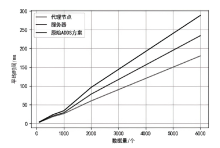
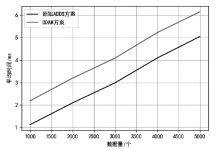
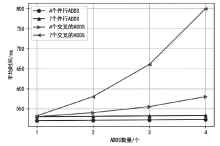
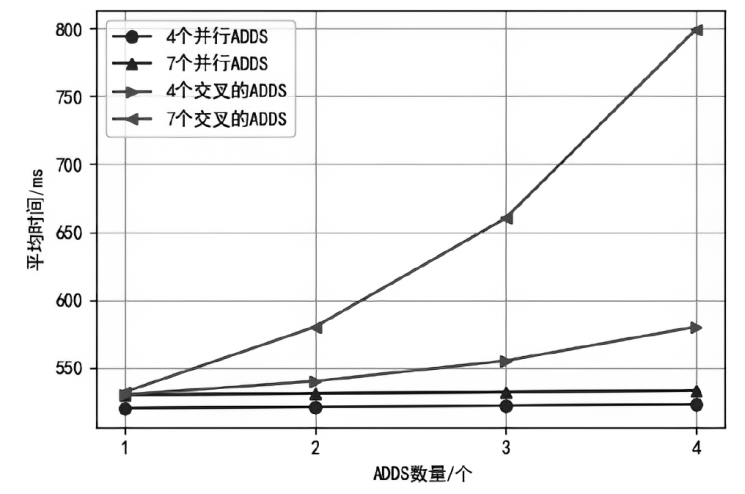
认证分布式数据结构(ADDSM)模型是认证数据结构(ADS)模型的扩展,用于解决ADS模型缺乏可组合性、无法支持复杂的数据组合运算等问题。然而,ADDSM模型存在理论描述不完整、缺少数据持久化解决方案以及机密性保护缺失等问题。为此,文章构建了新型可组合的认证分布式数据结构(NC-ADDSM)。首先,文章对模型进行了完整的理论描述,包括模型的形式化定义、属性描述和安全性定义;然后,设计了初始化、数据插入、数据查询、数据验证、数据持久化等算法,用于构建NC-ADDSM;最后,设计了支持数据更新和数据查询与验证的通信协议,确保只有拥有解密密钥的实体才能获取明文数据。理论分析和实验结果表明,文章所提出的NC-ADDSM在保证安全性的同时,具有较高的执行效率。
中图分类号:
引用本文
高扬, 张琪, 王琛, 徐剑. 新型可组合的认证分布式数据结构模型研究[J]. 信息网络安全, 2025, 25(7): 1111-1125.
GAO Yang, ZHANG Qi, WANG Chen, XU Jian. Research on New Composable Authenticated Distributed Data Structure Model[J]. Netinfo Security, 2025, 25(7): 1111-1125.
| [1] | SANAZ T B, ALPTEKIN K, ÖZNUR Ö. Integrita: A BFT Distributed Storage System[J]. Future Generation Computer Systems, 2025, 166: 1-29. |
| [2] | CHEN Yuanliang, MA Fuchen, ZHOU Yuanhang, et al. Survey on Dynamic Testing Technologies for Distributed Systems[J]. Journal of Software, 2025, 36(7): 2964-3002. |
| 陈元亮, 马福辰, 周远航, 等. 分布式系统动态测试技术研究综述[J]. 软件学报, 2025, 36(7): 2964-3002. | |
| [3] | The National People’s Congress Standing Committee. Data Security Law of the People’s Republic of China[EB/OL]. (2021-06-21) [2025-05-18]. http://www.npc.gov.cn/c2/c30834/202106/t20210610311888.html. |
| 全国人大常委会. 中华人民共和国数据安全法[EB/OL]. (2021-06- 21)[2025-05-18]. http://www.npc.gov.cn/c2/c30834/202106/t20210610311888.html. | |
| [4] | WU Haotian, LI Zecheng, SONG Rui, et al. Enabling Privacy-Preserving and Efficient Authenticated Graph Queries on Blockchain-Assisted Clouds[J]. IEEE Transactions on Knowledge and Data Engineering, 2023, 35(9): 9728-9742. |
| [5] | LIU Jianghua, HOU Jingyu, YANG Wenjie, et al. Leakage-Free Dissemination of Authenticated Tree-Structured Data with Multi-Party Control[J]. IEEE Transactions on Computers, 2021, 70(7): 1120-1131. |
| [6] | SHEFF I, WANG Xinwen, NI Haobin, et al. Charlotte: Composable Authenticated Distributed Data Structures, Technical Report[EB/OL]. (2019-05-09) [2025-05-10]. https://arxiv.org/pdf/1905.03888. |
| [7] | TAMASSIA R. Authenticated Data Structures[C]// Springer. European Symposium on Algorithms. Heidelberg: Springer, 2003: 2-5. |
| [8] | CHOI J A, BEILLAHI S M, SINGH S F, et al. LMPT: A Novel Authenticated Data Structure to Eliminate Storage Bottlenecks for High Performance Blockchains[J]. IEEE Transactions on Network and Service Management, 2024, 21(2): 1333-1343. |
| [9] | YIN Bo, ZENG Weilong, ZHANG Peng, et al. EAQ: Enabling Authenticated Complex Query Services in Sustainable-Storage Blockchain[J]. IEEE Transactions on Sustainable Computing, 2023, 8(3): 435-447. |
| [10] | YANG Haining, FENG Dengguo, QIN Jing. Efficient Verifiable Unbounded-Size Database from Authenticated Matrix Commitment[J]. IEEE Transactions on Dependable and Secure Computing, 2023, 20(5): 3873-3889. |
| [11] | LIANG Yihuai, LI Yan, SHIN B S. Dynamic Authenticated Keyword Search in Hybrid-Storage Blockchain[J]. Future Generation Computer Systems, 2024, 155: 53-65. |
| [12] | TONG Qiang, LONG Yin, LIU Yulong, et al. Append-Only Authenticated Data Sets Based on RSA Accumulators for Transparent Log System[EB/OL]. (2025-04-21) [2025-05-11]. https://doi.org/10.1016/j.csi.2025.103978. |
| [13] | LIU Dongxiao, HUANG Cheng, XUE Liang, et al. Authenticated and Prunable Dictionary for Blockchain-Based VNF Management[J]. IEEE Transactions on Wireless Communications, 2022, 21(11): 9312-9324. |
| [14] |
MO Ruo, MA Jianfeng, LIU Ximeng, et al. Multi-Authority ABS Supporting Dendritic Access Structure[J]. Journal on Communications, 2017, 38(7): 96-104.
doi: 10.11959/j.issn.1000-436x.2017150 |
|
莫若, 马建峰, 刘西蒙, 等. 支持树形访问结构的多权威基于属性的签名方案[J]. 通信学报, 2017, 38(7): 96-104.
doi: 10.11959/j.issn.1000-436x.2017150 |
|
| [15] | WANG Qiang, WANG Cong, LI Jin, et al. Enabling Public Verifiability and Data Dynamics for Storage Security in Cloud Computing[C]// Springer. European Symposium on Research in Computer Security. Heidelberg: Springer, 2009: 355-370. |
| [16] | ZHU Yan, AHN G J, HU Hongxin, et al. Dynamic Audit Services for Outsourced Storages in Clouds[J]. IEEE Transactions on Services Computing, 2013, 6(2): 227-238. |
| [17] | ERWAY C C, KÜPÇÜ A, PAPAMANTHOU C, et al. Dynamic Provable Data Possession[J]. ACM Transactions on Information and System Security (TISSEC), 2015, 17(4): 1-29. |
| [18] | NAKAMOTO S. Bitcoin: A Peer-to-Peer Electronic Cash System[EB/OL]. (2008-10-31) [2025-05-10]. https://bitcoin.org/bitcoin.pdf. |
| [19] | YUAN Yong, WANG Feiyue. Blockchain: The State of the Art and Future Trends[J]. Acta Automatica Sinica, 2016, 42(4): 481-494. |
| 袁勇, 王飞跃. 区块链技术发展现状与展望[J]. 自动化学报, 2016, 42(4): 481-494. | |
| [20] | LI Fang, LI Zhuoran, ZHAO He. Research on the Progress in Cross-Chain Technology of Blockchains[J]. Journal of Software, 2019, 30(6): 1649-1660. |
| 李芳, 李卓然, 赵赫. 区块链跨链技术进展研究[J]. 软件学报, 2019, 30(6): 1649-1660. | |
| [21] | ZHANG Ce, XU Cheng, XU Jianliang, et al. GEM2-Tree: A Gas-Efficient Structure for Authenticated Range Queries in Blockchain[C]// IEEE. IEEE 35th International Conference on Data Engineering. New York: IEEE, 2019: 842-853. |
| [22] | LI Chenxing, BEILLAHI S M, YANG Guang, et al. LVMT: An Efficient Authenticated Storage for Blockchain[J]. ACM Transactions on Storage, 2024, 20(3): 1-34. |
| [1] | 孙钰, 熊高剑, 刘潇, 李燕. 基于可信执行环境的安全推理研究进展[J]. 信息网络安全, 2024, 24(12): 1799-1818. |
| [2] | 杨丽, 朱凌波, 于越明, 苗银宾. 联邦学习与攻防对抗综述[J]. 信息网络安全, 2023, 23(12): 69-90. |
| [3] | 沈卓炜, 高鹏, 许心宇. 基于安全协商的DDS安全通信中间件设计[J]. 信息网络安全, 2021, 21(6): 19-25. |
| [4] | 吴奕, 仲盛. 区块链共识算法Raft研究[J]. 信息网络安全, 2021, 21(6): 36-44. |
| [5] | 尤玮婧, 刘丽敏, 马悦, 韩东. 基于安全硬件的云端数据机密性验证方案[J]. 信息网络安全, 2020, 20(12): 1-8. |
| [6] | 韩菊茹, 杨秩, 纪兆轩, 马存庆. 基于微信小程序的文件加密系统设计与实现[J]. 信息网络安全, 2019, 19(9): 81-85. |
| [7] | 郑敏, 王虹, 刘洪, 谭冲. 区块链共识算法研究综述[J]. 信息网络安全, 2019, 19(7): 8-24. |
| [8] | 胡荣磊, 李文敬, 蒋华, 张昕然. 基于离散对数的无证书聚合签密方案[J]. 信息网络安全, 2019, 19(7): 42-49. |
| [9] | 刘敬浩, 平鉴川, 付晓梅. 一种基于区块链的分布式公钥管理方案研究[J]. 信息网络安全, 2018, 18(8): 25-33. |
| [10] | 程冬梅, 严彪, 文辉, 孙利民. 基于规则匹配的分布式工控入侵检测系统设计与实现[J]. 信息网络安全, 2017, 17(7): 45-51. |
| [11] | 于泳. 密码技术在分布式系统中的应用研究[J]. , 2011, 11(5): 0-0. |
| [12] | 毕连城. 等级保护中关键数据保护的几点考虑[J]. , 2007, 7(12): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||