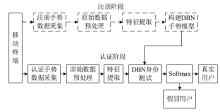
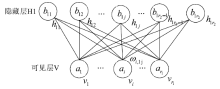
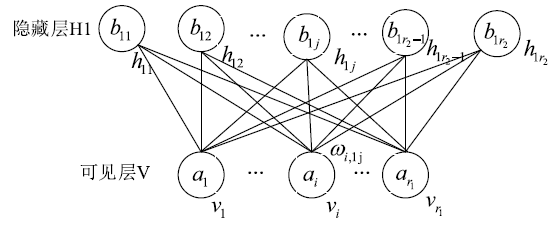
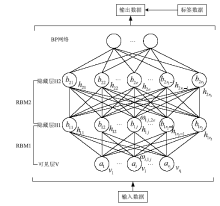
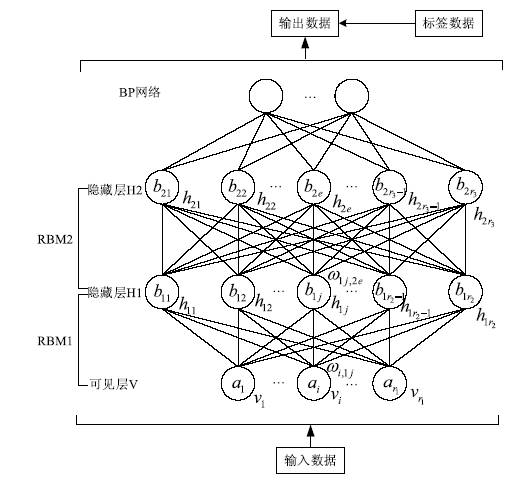
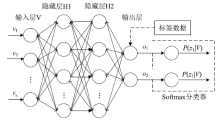
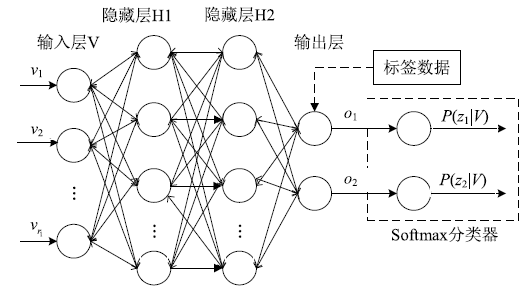
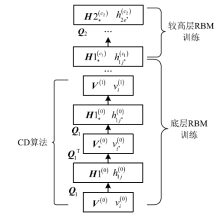
| [1] |
MENG Yuxin, WONG D S, SCHLEGEL R, et al.Touch Gestures Based Biometric Authentication Scheme for Touchscreen Mobile Phones[C]//Springer. 2012 International Conference on Information Security and Cryptology, November 28-30, 2012, Beijing, China. Heidelberg: Springer, 2012: 331-350.
|
| [2] |
LIU Qiang, WANG Mimi, ZHAO Peihai, et al.A Behavioral Authentication Method for Mobile Gesture Against Resilient User Posture[C]//IEEE. 3rd International Conference on Systems and Informatics, November 19-21, 2016, Shanghai, China. New Jersey: 2017: 324-331.
|
| [3] |
LIN Xiaofeng, FANG Mu, LI Qiang, et al.A Design and Implementation of Windows Login Based on Fingerprint Identification[J]. Netinfo Security, 2016, 16(9): 130-133.
|
|
林晓锋,房牧,李强,等.一种基于指纹识别的Windows系统登录方法设计与实现[J].信息网络安全,2016,16(9):130-133.
|
| [4] |
CHEN Shaokang, MAU S, HARANDI M T, et al.Face Recognition from Still Images to Video Sequences: A Local-Feature-Based Framework[J]. EURASIP Journal on Image & Video Processing, 2011(1): 1-14.
|
| [5] |
HUANG Jiaju, HOU Daqing, SCHUCKERS S, et al. Benchmarking Keystroke Authentication Algorithms[EB/OL]., 2017-12-1.
|
| [6] |
WANG Kaijie, YANG Tianqi.Gait Recognition Method Based on Column Mass Vector and Support Vector Machine[J]. Computer Engineering & Applications. 2015, 51(7): 169-173.
|
|
王开杰,杨天奇.基于列质量向量和SVM的步态识[J].计算机工程与应用,2015,51(7):169-173.
|
| [7] |
LI Daofeng, ZHANG Xiaoping, ZHONG Cheng, et al.Hierarchical Identity Based Signature Scheme from Hardness of Lattice LWE Problem[J]. Journal of Chinese Computer Systems, 2016, 37(1): 96-99.
|
|
李道丰,张小萍,钟诚,等.格LWE 难题下分层的基于身份的签名方案[J].小型微型计算机系统,2016,37(1):96-99.
|
| [8] |
LIU Weibo, WANG Zidong, LIU Xiaohui, et al. A Survey of Deep Neural Network Architectures and Their Applications[EB/OL].2018-7-11.
|
| [9] |
LI Hongling, ZOU Jianxin.Research of SQL Injection Detection Based on SVM and Text Feature Extraction[J]. Netinfo Security, 2017, 17(12): 40-46.
|
|
李红灵,邹建鑫.基于SVM和文本特征向量提取的SQL注入检测研究[J].信息网络安全,2017,17(12):40-46.
|
| [10] |
LI Dongjie, LI Yangyang, LI Junxiang, et al.Gesture Recognition Based on BP Neural Network Improved by Chaotic Genetic Algorithm[J]. International Journal of Automation and Computing. 2018, 15(3): 1-10.
|
| [11] |
DAI Yukun, ZHOU Zhiheng, CHEN Xi, et al. A Novel Method for Simultaneous Gesture Segmentation and Recognition Based on HMM[EB/OL]., 2018-7-12.
|
| [12] |
MIAO Yunqi, WANG Linna, XIE Chunyu, et al.Gesture Recognition Based on Deep Belief Networks[C]//Springer. 12th Chinese Conference on Biometric Recognition, October 28-29, 2017, Beijing, China. Heidelberg: Springer, 2017: 439-446.
|
| [13] |
DU Yongping, YAO Changqing, HUO Shuhua, et al.A New Item-based Deep Network Structure Using a Restricted Boltzmann Machine for Collaborative Filtering[J]. Frontiers of Information Technology & Electronic Engineering, 2017, 18(5): 658-666.
|
| [14] |
LI Fu, SUN Ziwen.Continuous Hidden Markov Model for Hand Gesture Recognition[J]. Journal of Chinese Computer Systems, 2018, 39(3): 474-477.
|
|
李富,孙子文.手势识别身份认证的连续隐马尔可夫模型[J].小型微型计算机系统,2018,39(3):474-477.
|
| [15] |
CHEN Luefeng, ZHOU Mengtian, SU Wanjuan, et al. Softmax Regression Based Deep Sparse Autoencoder Network for Facial Emotion Recognition in Human-robot Interaction[EB/OL]. , 2018-7-12.
|
| [16] |
RZECKI K, PŁAWIAK P, NIEDŹWIECKI M, et al. Person Recognition Based on Touch Screen Gestures Using Computational Intelligence Methods[EB/OL]. , 2018-7-12.
|
| [17] |
JAIN A, KANHANGAD V.Exploring Orientation and Accelerometer Sensor Data for Personal Authentication in Smartphones Using Touchscreen Gestures[J]. Pattern Recognition Letters, 2015, 68(P2): 351-360.
|
| [18] |
DIAZ M M, J FIERREZ, GALBALLY J. Graphical Password-based User Authentication With Free-form Doodles[J]. IEEE Transactions on Human-Machine Systems, 2016, 46(4): 607-614.
|
| [19] |
SHAHZAD M, LIU A X, SAMUEL A.Secure Unlocking of Mobile Touch Screen Devices by Simple Gestures: You Can See It But You Can Not Do It[C]//ACM. 19th International Conference on Mobile Computing & Networking, September 30-October 4, 2013, Miami, Florida, USA. New York: ACM, 2013: 39-50.
|
| [20] |
YAO Luying, HUO Zhiyong.Stereo Matching Algorithm Based on Steady-state Matching Probability and Edge-aware Disparity Propagation[J]. Journal of Nanjing University of Posts and Telecommunications(Natural Science Edition), 2016, 36(2): 124-130.
|
|
姚璐莹,霍智勇.基于稳态匹配概率和边缘感知视差传播的立体匹配算法研究[J].南京邮电大学学报(自然科学版),2016,36(2):124-130.
|