信息网络安全 ›› 2017, Vol. 17 ›› Issue (9): 21-25.doi: 10.3969/j.issn.1671-1122.2017.09.005
一种跨指令架构二进制漏洞搜索技术研究
- 国防科技大学网络工程系, 湖南长沙 410073
Research on Cross-architecture Vulnerabilities Searching in Binary Executables
Weiyang XU( ), Yao LI, Yong TANG, Baosheng WANG
), Yao LI, Yong TANG, Baosheng WANG
- Department of Network Engineering, National University of Defense Technology, Changsha Hunan 410073, China
摘要:
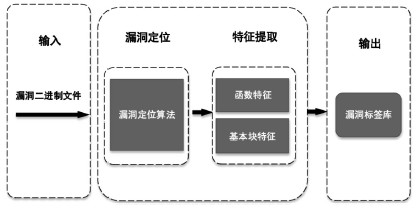
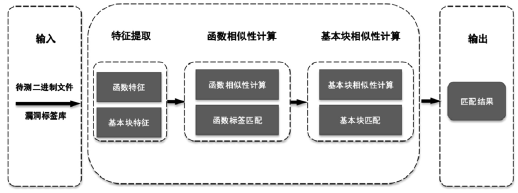
计算机软件技术不断发展过程中,漏洞的出现无法避免,快速识别漏洞是保护计算机系统的关键。现有识别漏洞的方法多数是基于源代码的,即使基于二进制层面的方法也只是在单一指令架构上完成。针对以上问题,文章提出一种高效搜索二进制代码漏洞的方法。将不同指令架构的汇编代码规范化,提取漏洞特征与二进制文件特征,通过特征匹配算法找出二进制文件中存在漏洞之处。实验表明,该方法能够准确找到样例中存在的已知漏洞,如OpenSSL库中的Heartbleed漏洞、BusyBox中的提权漏洞以及路由器固件中存在的后门。
中图分类号: